Method for providing file security information and security information processing system
A technology for security information and files, applied in the Internet field to reduce the time of file scanning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
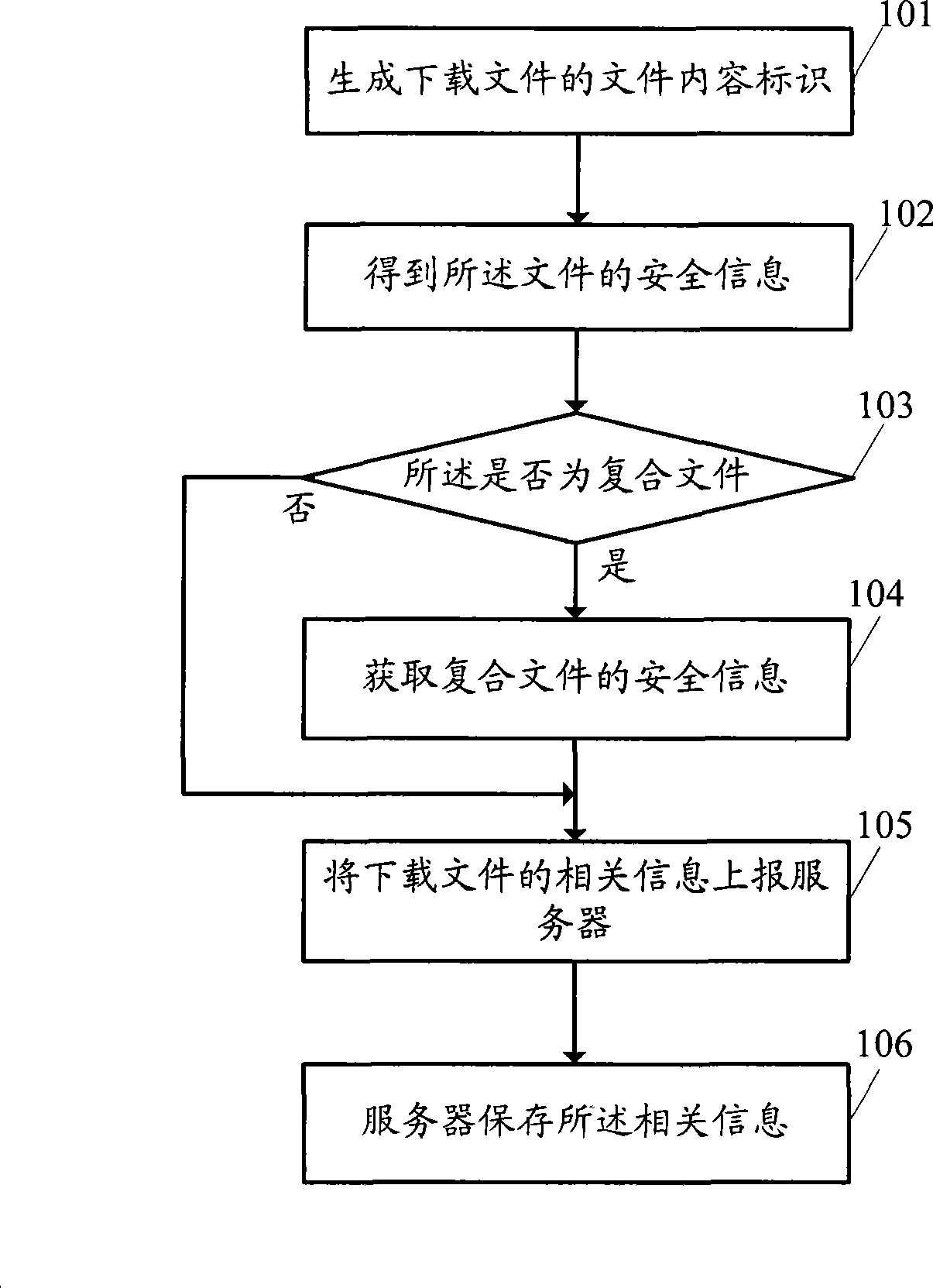
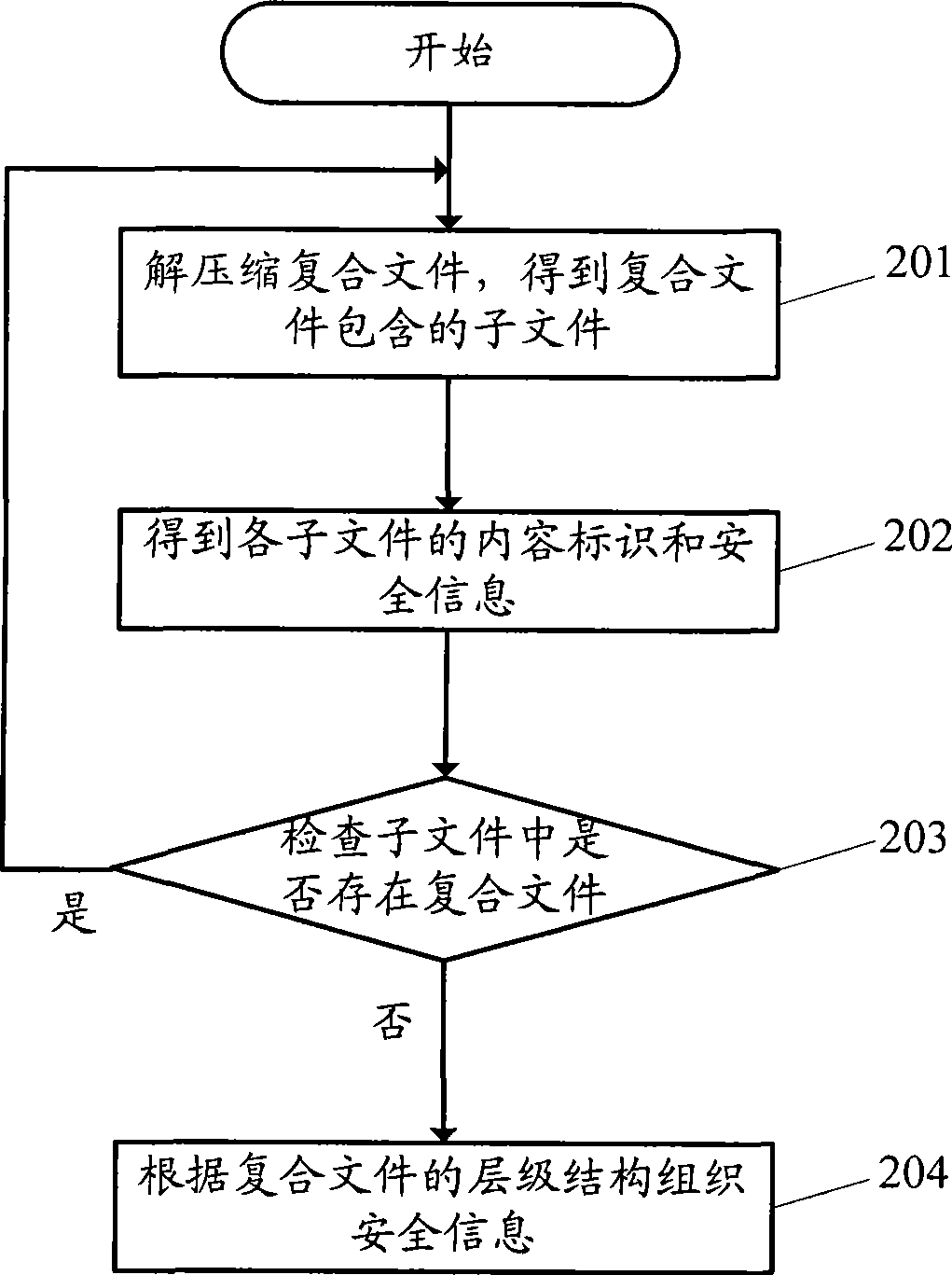
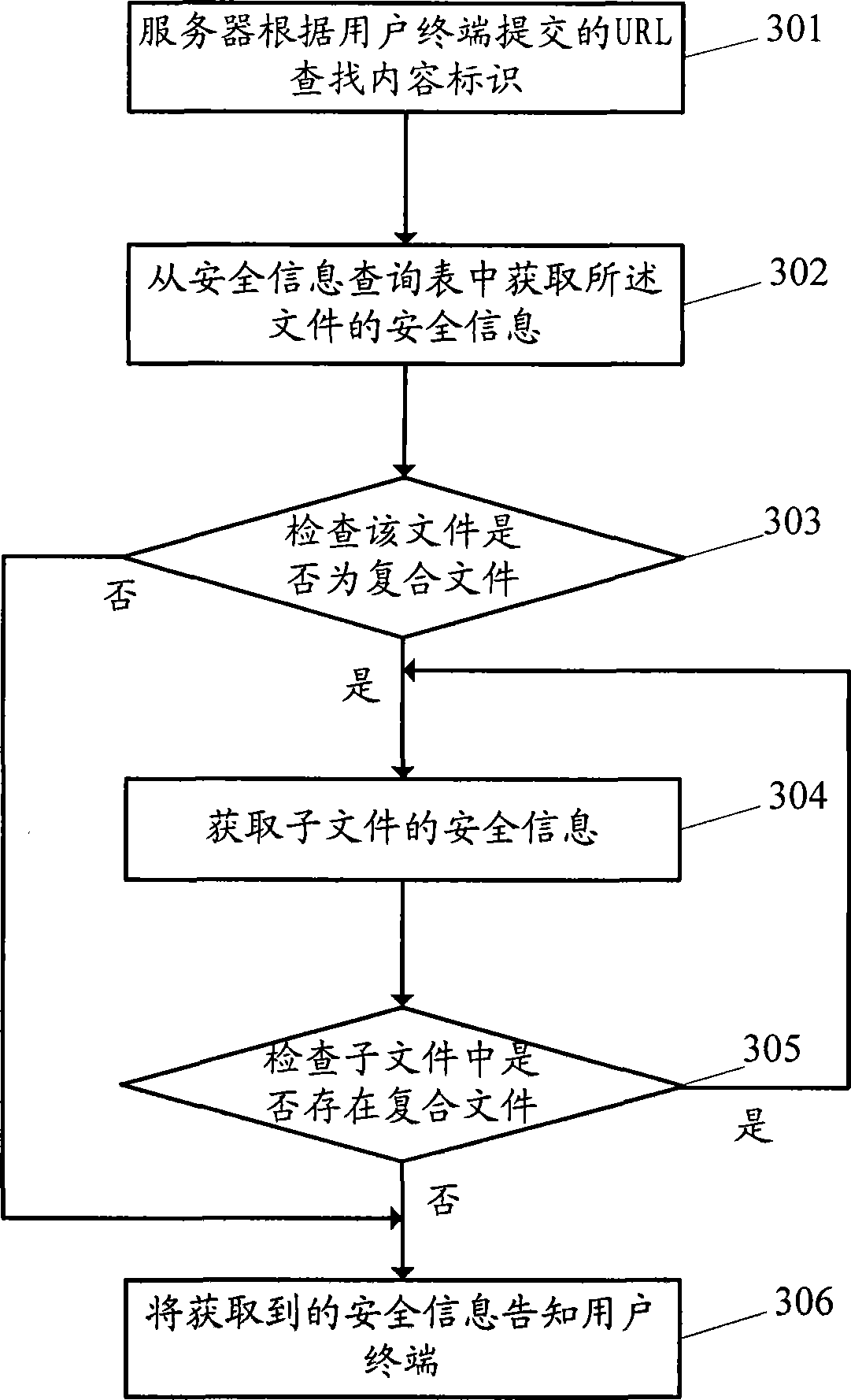
[0054]An embodiment of the present invention provides a method for downloading a file, which includes: when a user end initiates a file download, first submitting a Uniform Resource Locator (URL) to a server. The server looks up the content identification of the file corresponding to the URL in the mapping table according to the URL, then judges whether the file is a compound file according to the content identification, if not, obtains the security information of the file through the content identification, and if so, obtains the security information of the file from The content identifiers of the subfiles included in the file are obtained from the subfile mapping table, and the security information of all subfiles is obtained through the obtained content identifiers, and the files are downloaded according to the security information.
[0055] Such as figure 1 As shown, the embodiment of the present invention is a method for reporting security information, which specifically ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com