Method for determining inquiry answer type bidirectional identification and business
An identity verification, question-and-answer technology, applied to transmission systems, instruments, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
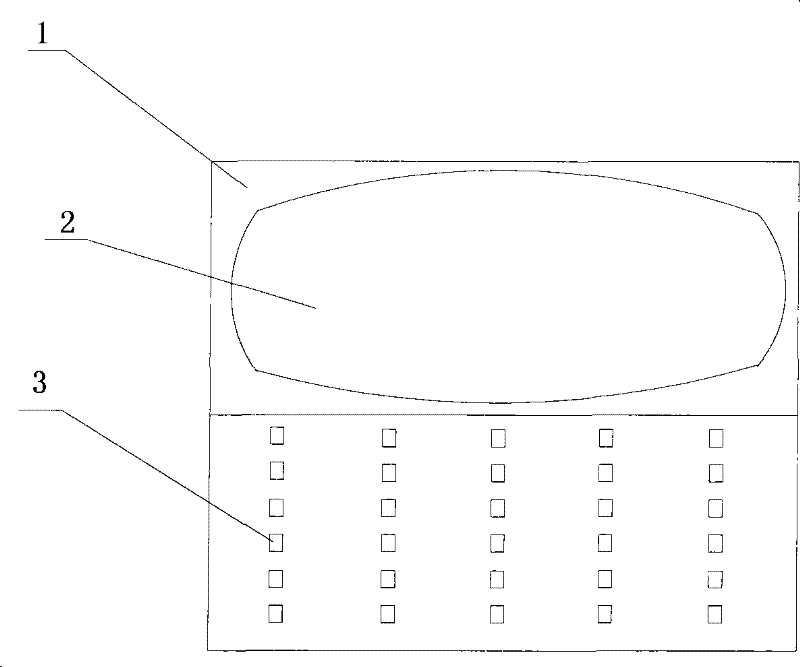
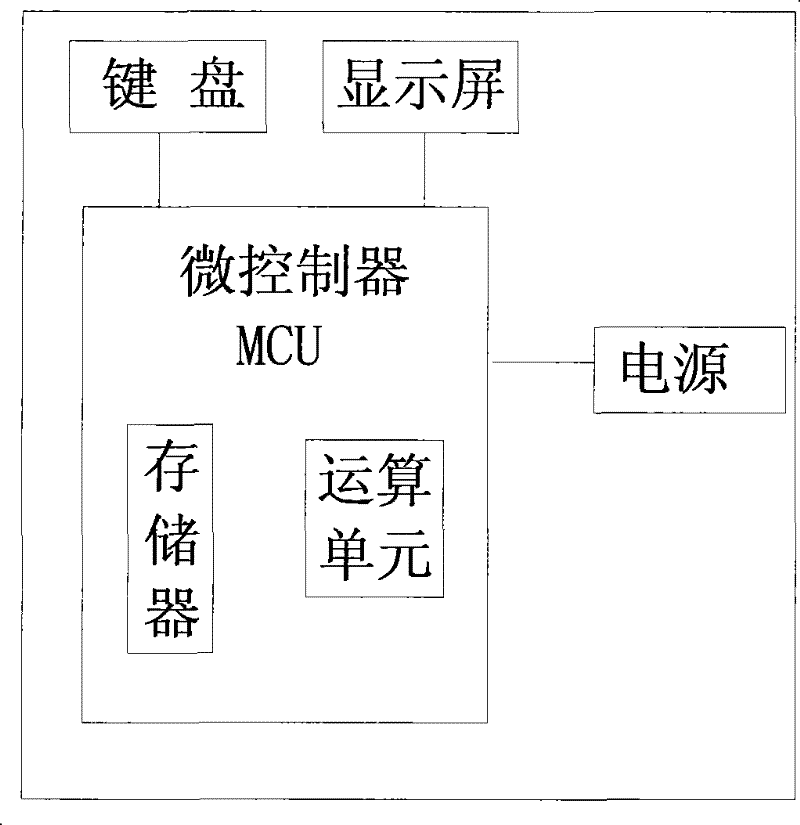
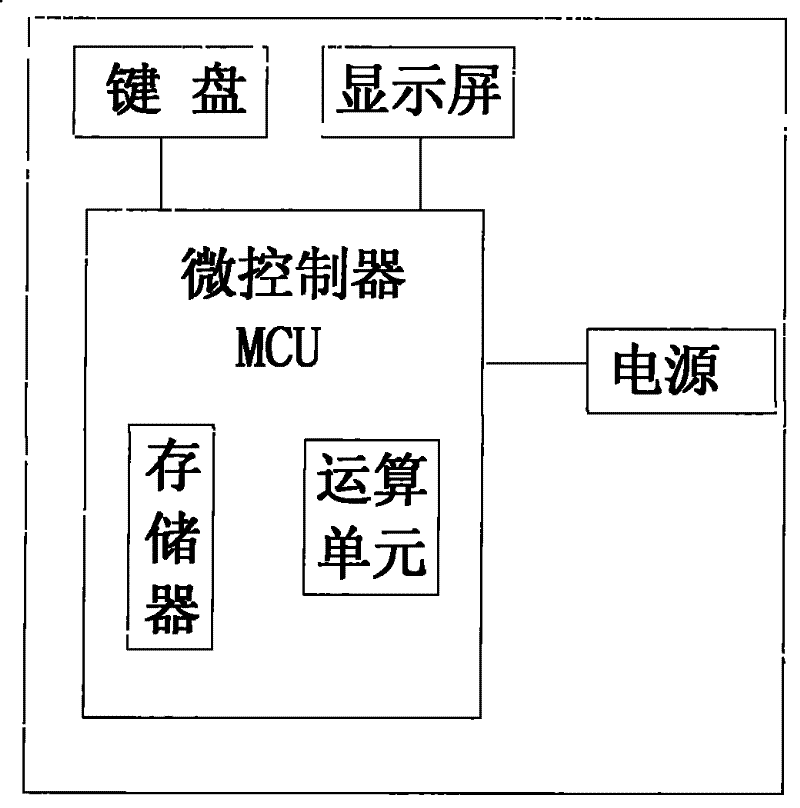
[0082] The encryption device 1 includes a keyboard 3, a display screen 2, a microcontroller MCU, and a power supply. The keyboard 3, the display screen 2, and the power supply are respectively connected to the microcontroller MCU, and the microcontroller MCU has a built-in memory and arithmetic unit.
[0083] The two-way authentication method for both parties in a transaction using the encryption device 1 described above, the authentication method includes identity confirmation, and identity confirmation includes the following steps:
[0084] (a) Customer service providers distribute independent encryption devices to dedicated customers;
[0085] (b) The user connects to the server via the Internet or telephone and enters the customer account K;
[0086] (c) The server retrieves the server password Mo and the encryption algorithm Fo indicating the identity of the server according to the customer account K;
[0087] (d) The server generates a random number N, calculates the encryption re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com