Negotiation control method based on SIP security policy grade in IMS network
A security policy and control method technology, applied in security devices, electrical components, wireless communications, etc., can solve problems such as not providing service levels, not fully considering network security requirements and negotiation mechanisms, and incompatible security configurations of different operators , to achieve the effect of reducing resource overhead and satisfying service quality assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
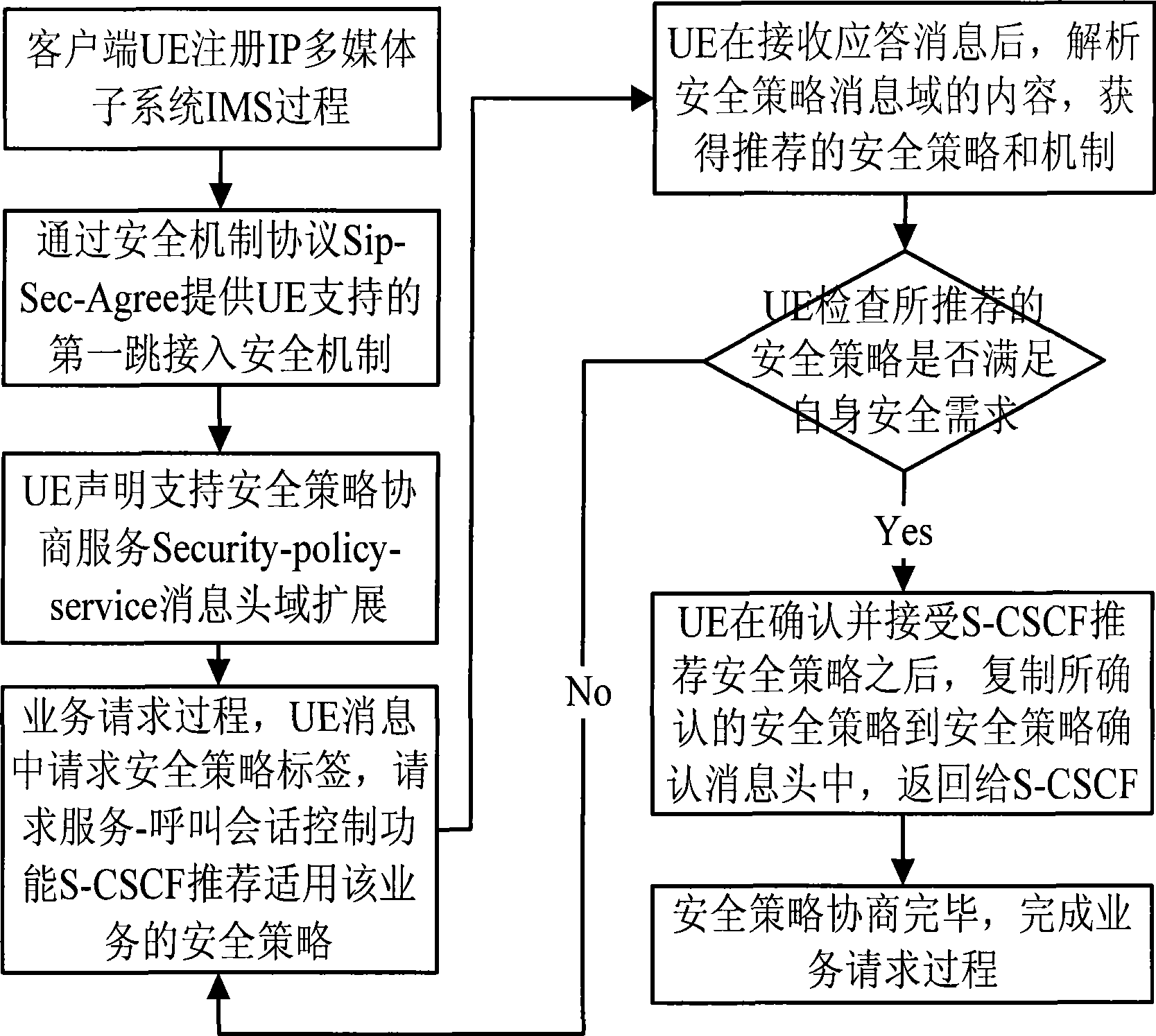
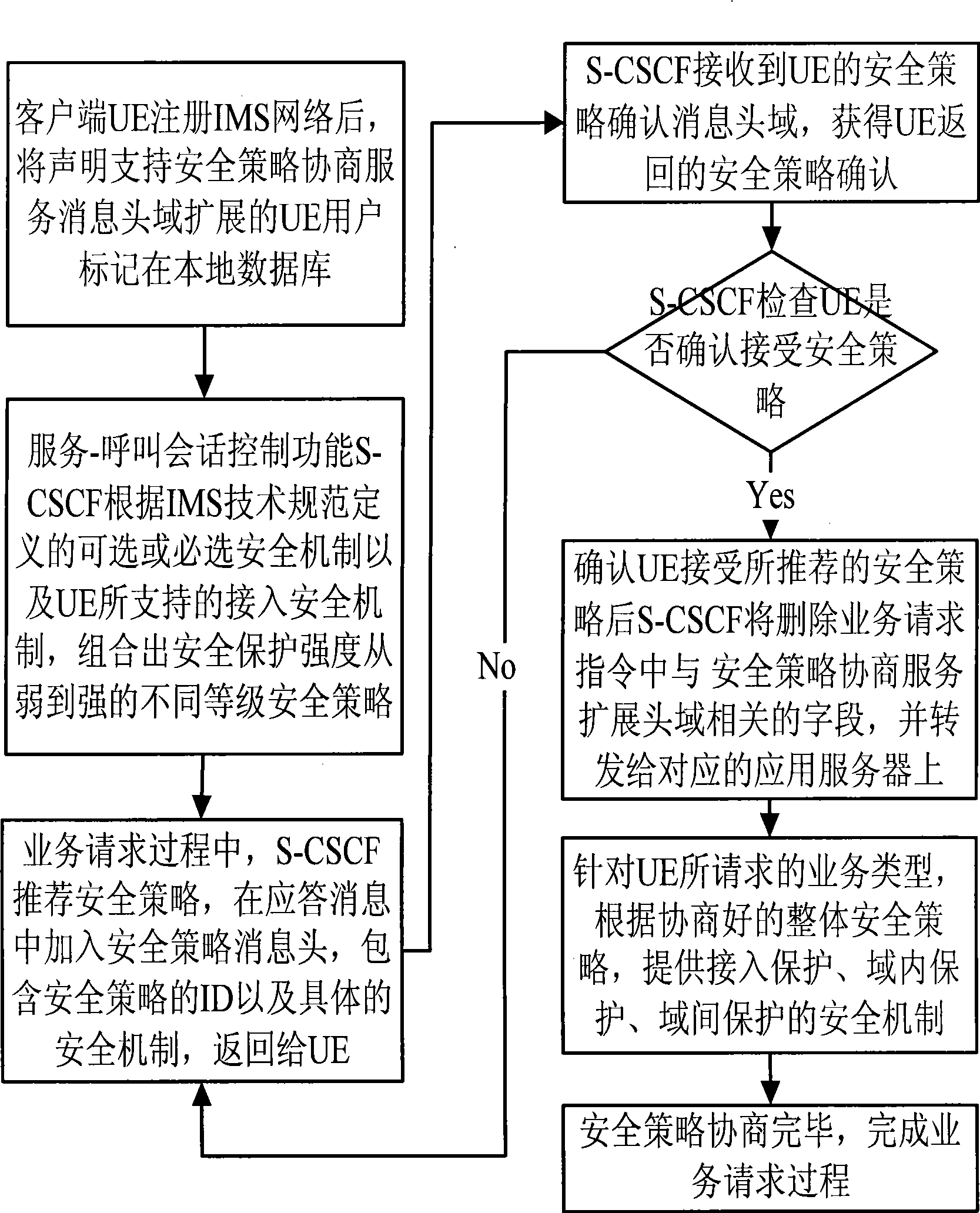
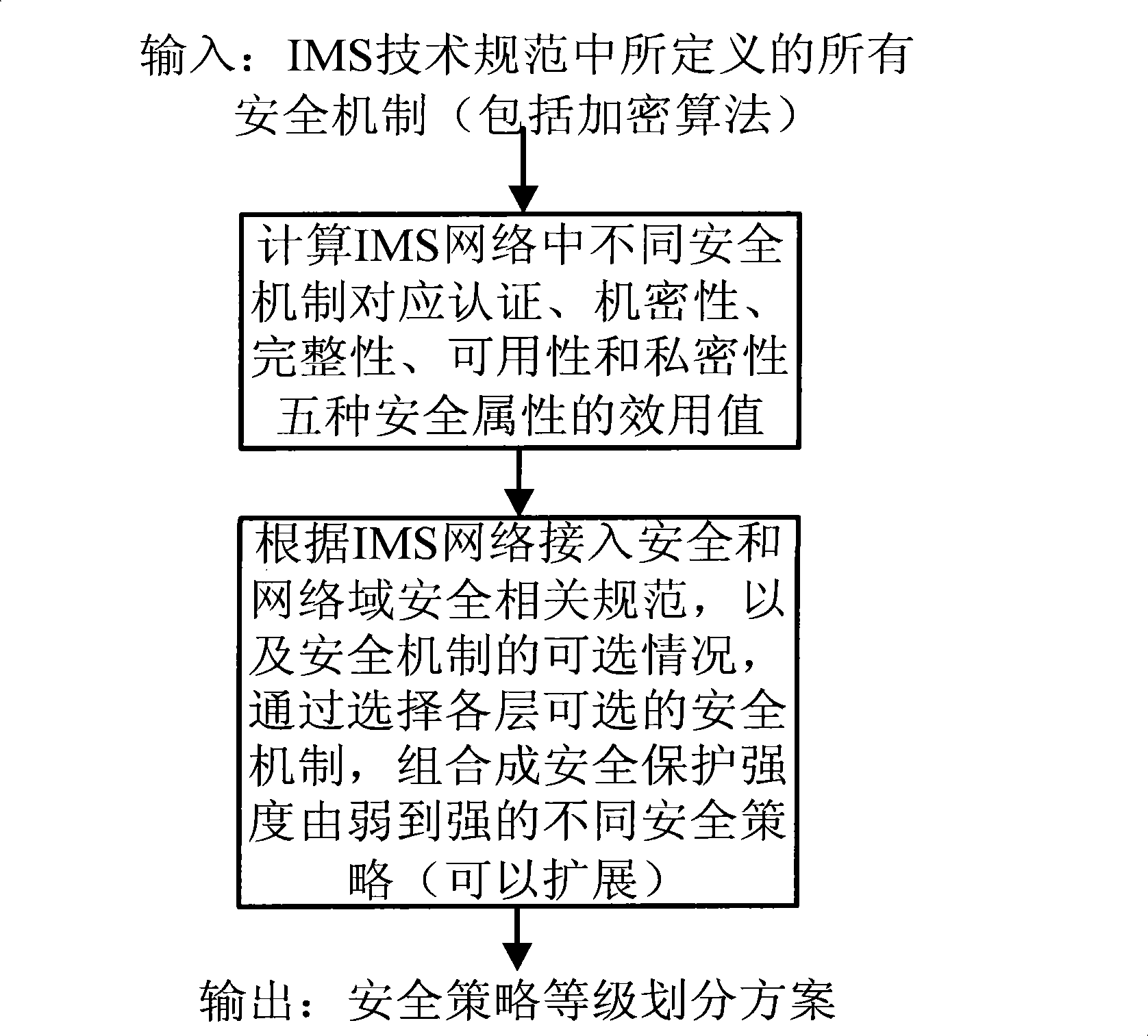
[0048] The present invention is a security policy negotiation and control method in an IMS network. The interactive entity involved in the present invention is mainly based on the SIP message format between the user equipment UE as the client and the service-call session control function S-CSCF in the IMS network. security policy negotiation control.
[0049] The present invention defines a new SIP extended message domain: security policy negotiation service Security-policy-service, which is used for the security policy negotiation process between the S-CSCF and the UE. During the registration process, the S-CSCF provides a default security policy for the UE. And check whether the UE supports the extension of the present invention; in the service request signaling, negotiate a security policy that meets the security requirements of the service requested by the user through the Security policy service.
[0050] For the flow chart of UE security policy negotiation, see figure 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com