Authentication method and apparatus for wireless radio frequency recognition system
An authentication method and radio frequency technology, applied in the field of communication, can solve the problems of asynchronous data update, no dynamic ID refresh mechanism, legal tags cannot pass authentication, etc., to achieve the effect of ensuring anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] In the following, the embodiments of the present invention will be further described with reference to the drawings and examples.
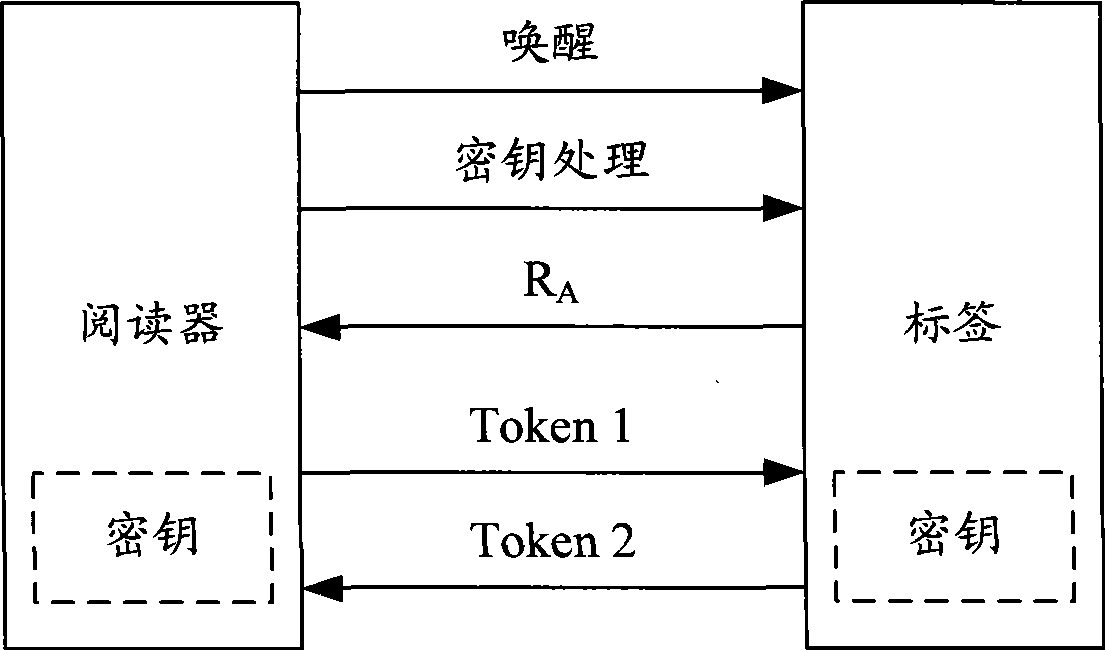
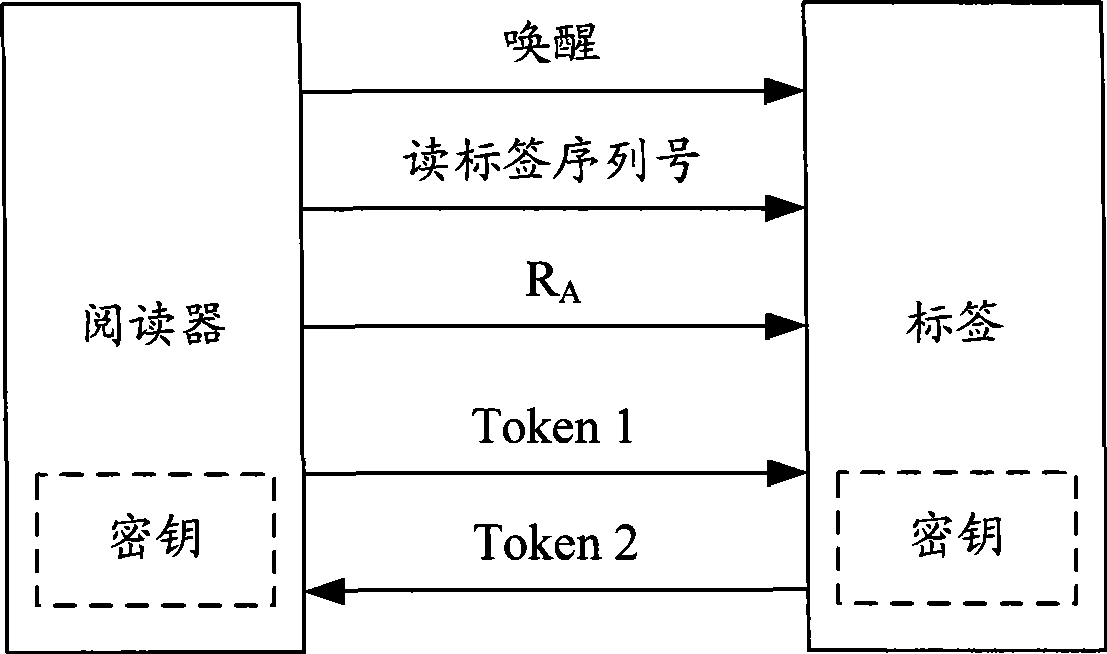
[0072] The embodiment of the present invention provides an authentication method, which ensures the anonymity of the tag by updating the ID in each authentication, and stores the (ID, P_key) pair of the tag on the reader side, and the reader side only Update the (ID, P_key) part that is inconsistent with the content sent by the tag. Therefore, while ensuring anonymity, even if there are multiple abnormal situations that cause the tag to not be updated, the tag used in the last communication is still stored in the reader's form, so the tag can still be normal with the trusted reader. Communication.
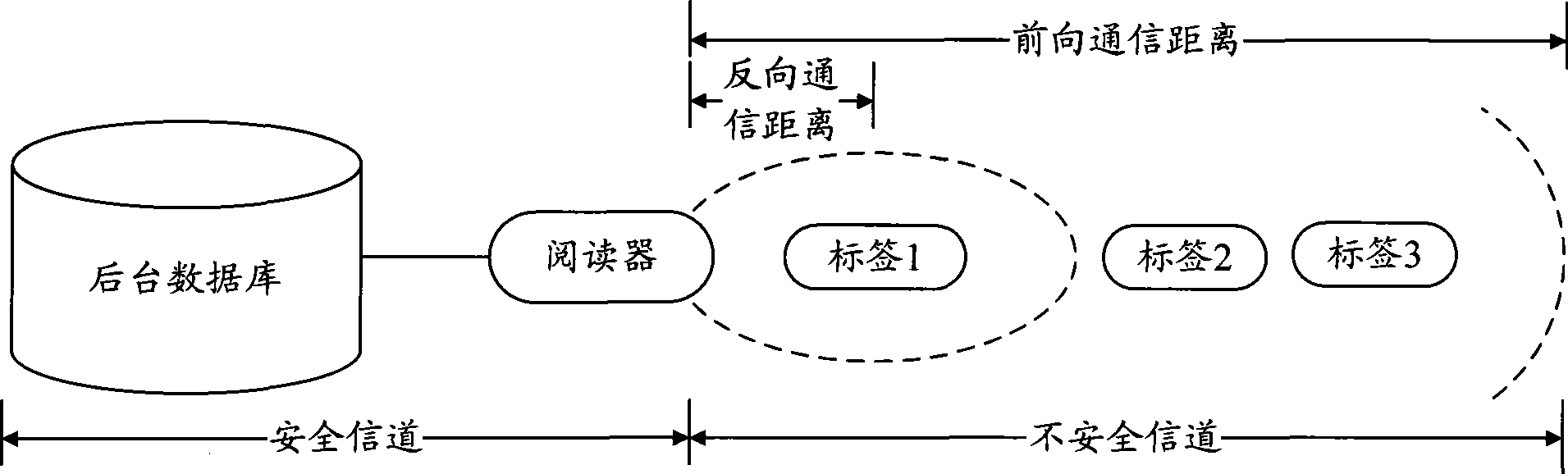
[0073] The embodiment of the present invention is used for the authentication between the reader and the tag in the RFID system, and mainly solves the communication security problem between the reader and the tag, that is, the air interface part. Fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com