Remote voice identification authentication system and method
An identity authentication and authentication system technology, applied in the field of identity authentication methods, can solve problems such as low user acceptance and increase user operation burden, and achieve the effect of improving security and high user acceptance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
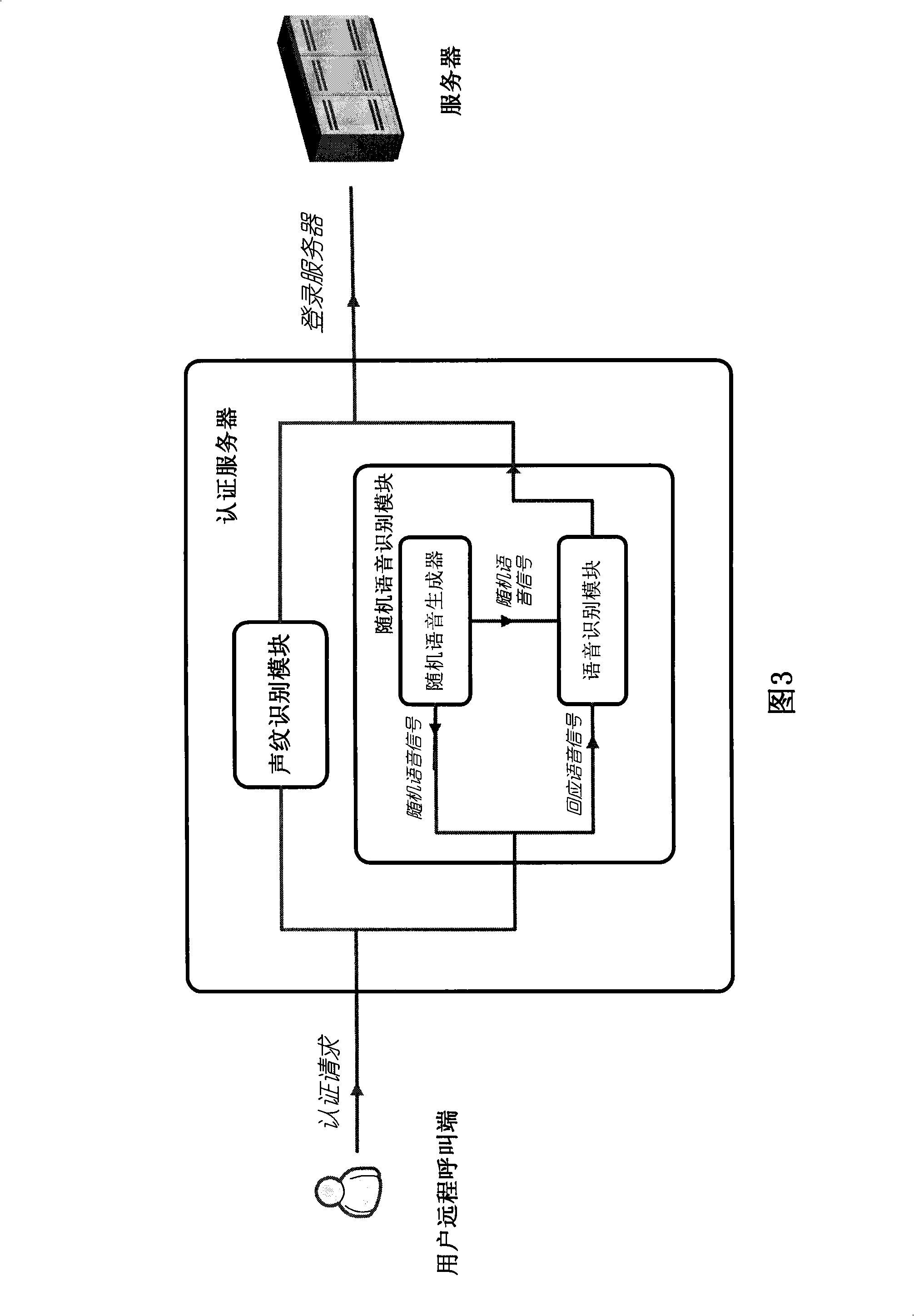
[0063] As shown in Figure 3, the random speech recognition module includes a random speech generator and a speech recognition module. The random speech generator is used to generate a random speech signal that requires the user to repeat. The speech recognition module is a module that uses speech recognition technology to recognize the speech signal that the user responds to. By comparing the user response voice signal recognized by the voice recognition module with the random voice signal generated by the random voice generator, it is judged whether the user has passed the voice authentication.
[0064] Here, there are many specific implementation forms that can be used as a random speech generator. In this embodiment, an IVR system (Interactive Voice Response, interactive voice response system) is used for implementation.
Embodiment 2
[0066] like Figure 4 As shown, the random speech recognition module is realized by the artificial speech server. The so-called artificial voice server is to manually provide identity authentication services to users who apply for identity authentication. The service personnel of the artificial voice server can ask random questions to the user applying for identity authentication, and judge the authenticity of the user according to the answer made by the user. Moreover, during the conversation between the user and the service personnel, the voice information sent by the user can be simultaneously authenticated by the voiceprint recognition module. In this way, the user can complete the identity authentication without knowing it, which improves the acceptance of the user.
[0067] Here, although the artificial voice server is used for voice recognition, certain human resource costs will be increased. However, this method, as a solution with high user acceptance, is also an i...
Embodiment 3
[0069] As shown in Figure 5, the random speech recognition module includes a random speech generator, a speech recognition module and an artificial speech server. Among them, the random speech generator, the speech recognition module and the artificial speech server have been introduced in Embodiment 1 and Embodiment 2, and will not be repeated here.
[0070] In this embodiment, the artificial voice server serves as a supplement to the random voice generator and the voice recognition module. When the user fails to authenticate through the random voice generator and the voice recognition module, he can choose to authenticate through the artificial voice server. In this way, on the one hand, a large amount of human resource costs caused by the artificial voice server can be saved, and on the other hand, remedial measures are provided for authentication failures of the random voice generator and the voice recognition module.
[0071] The authentication method of this remote voic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com