Implementation method of ternary-equally recognizing credible network connecting architecture
A network connection and ternary peering technology, applied in the field of identifying trusted network connection architectures, can solve the problems of different TNC architecture implementation methods and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
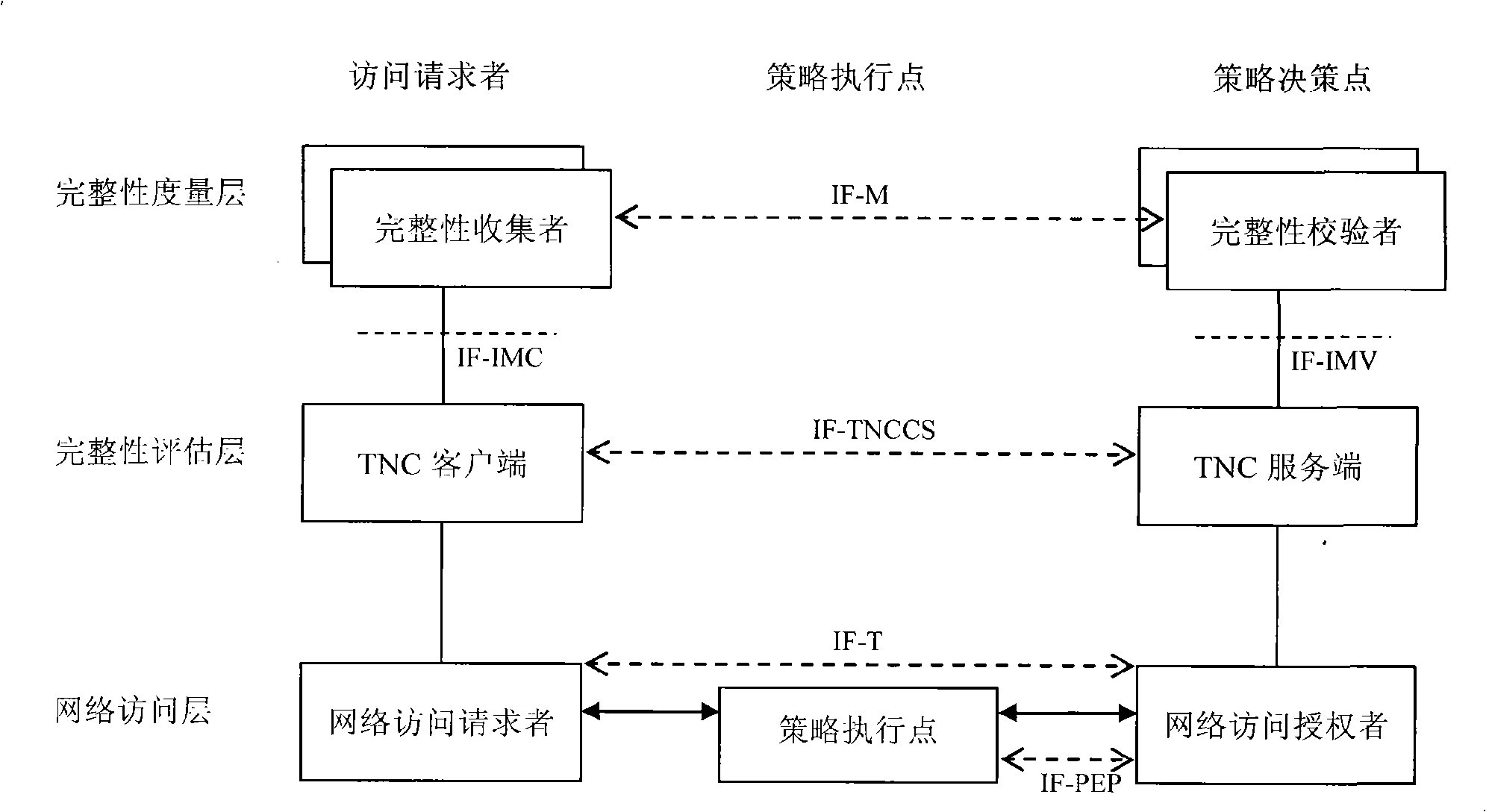
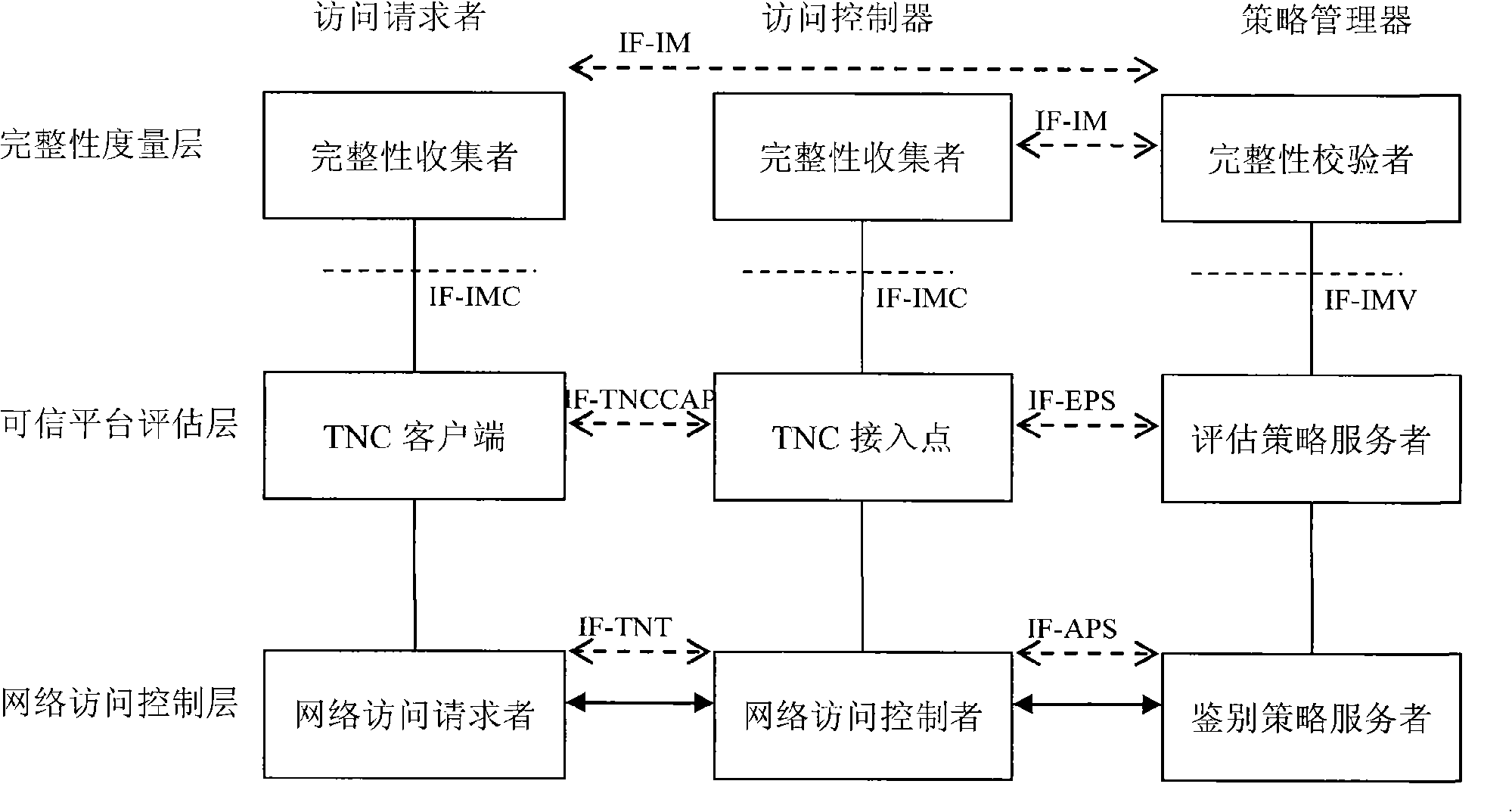
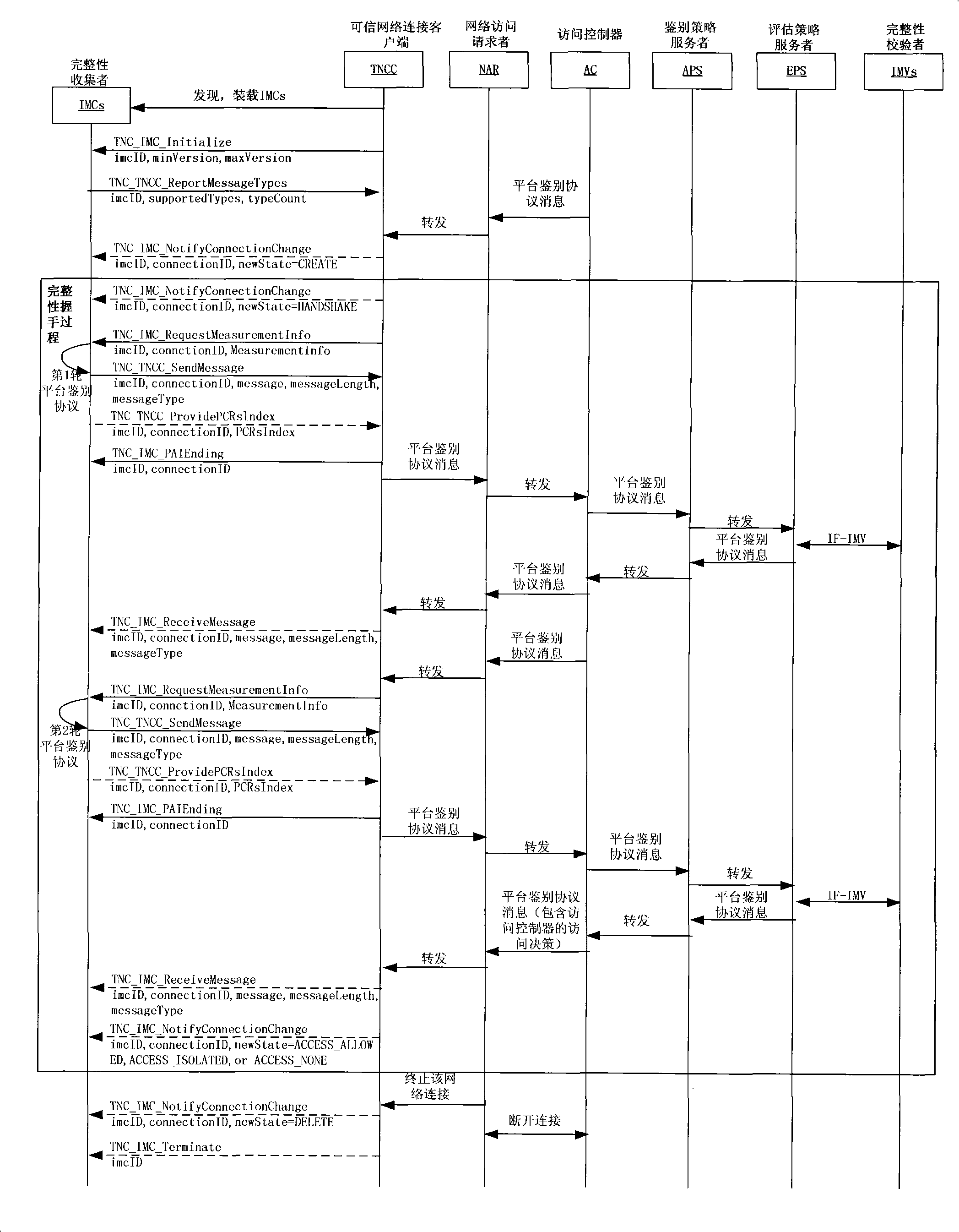
[0059] The present invention provides a method for implementing a trusted network connection framework for ternary peer-to-peer authentication. The method includes the following steps:
[0060] 1) Establish a trusted network connection architecture for ternary peer-to-peer authentication by defining an interface, and its specific implementation method is:
[0061] 1.1) The specific implementation method of IF-TNT and IF-APS:
[0062] The user authentication protocol defined in IF-TNT and IF-APS can use a ternary peer-to-peer authentication protocol based on symmetric keys and asymmetric keys, such as the WAI protocol in the Chinese wireless LAN standard.
[0063] The network transmission protocol defined in IF-TNT and IF-APS can be: the protocol data encapsulation packet can adopt the same or similar protocol data encapsulation packet as EAP, but the processing of the protocol data encapsulation packet is different from that of EAP, and the protocol data encapsulation packet ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com