Key management and recovery method for encrypted digital certificate
A technology of key recovery and encryption certificate, applied in key distribution, can solve the problems of lack of flexibility, taking a long time, and the private key of digital certificate cannot be recovered, and achieves the advantages of simple key management system, simplified implementation, and superiority outstanding effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
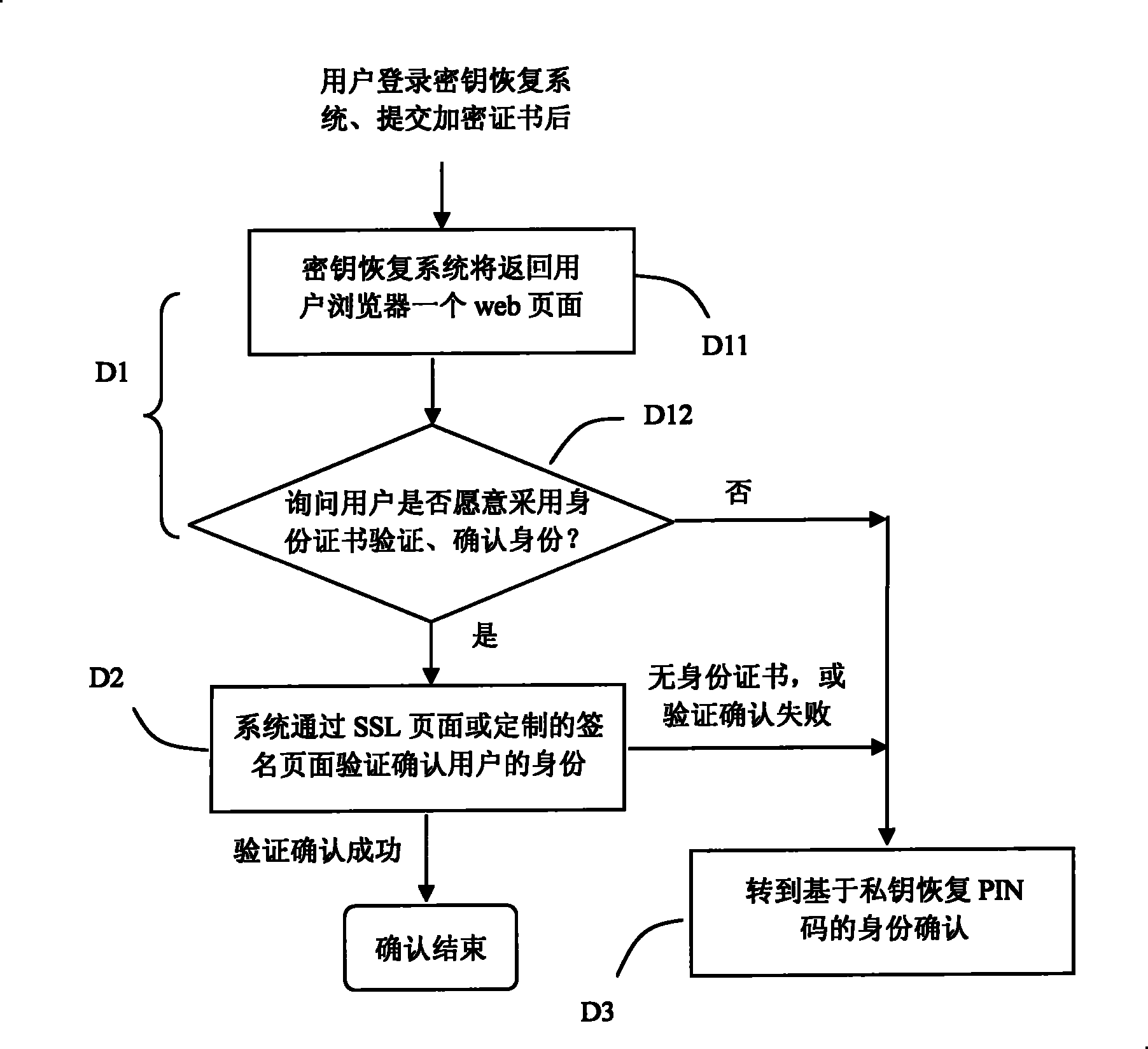
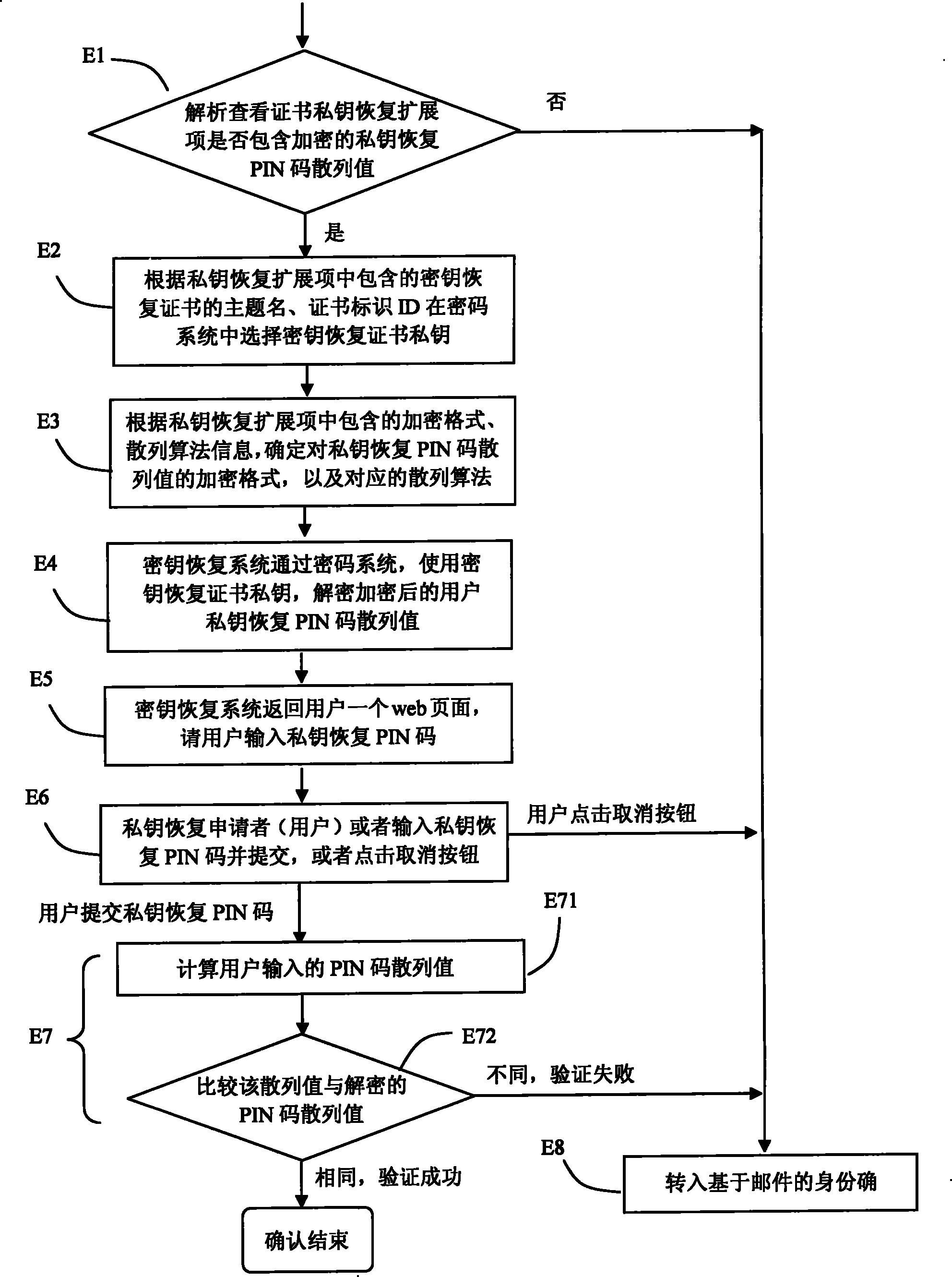
[0054] The present invention will be described in further detail below in conjunction with the accompanying drawings.
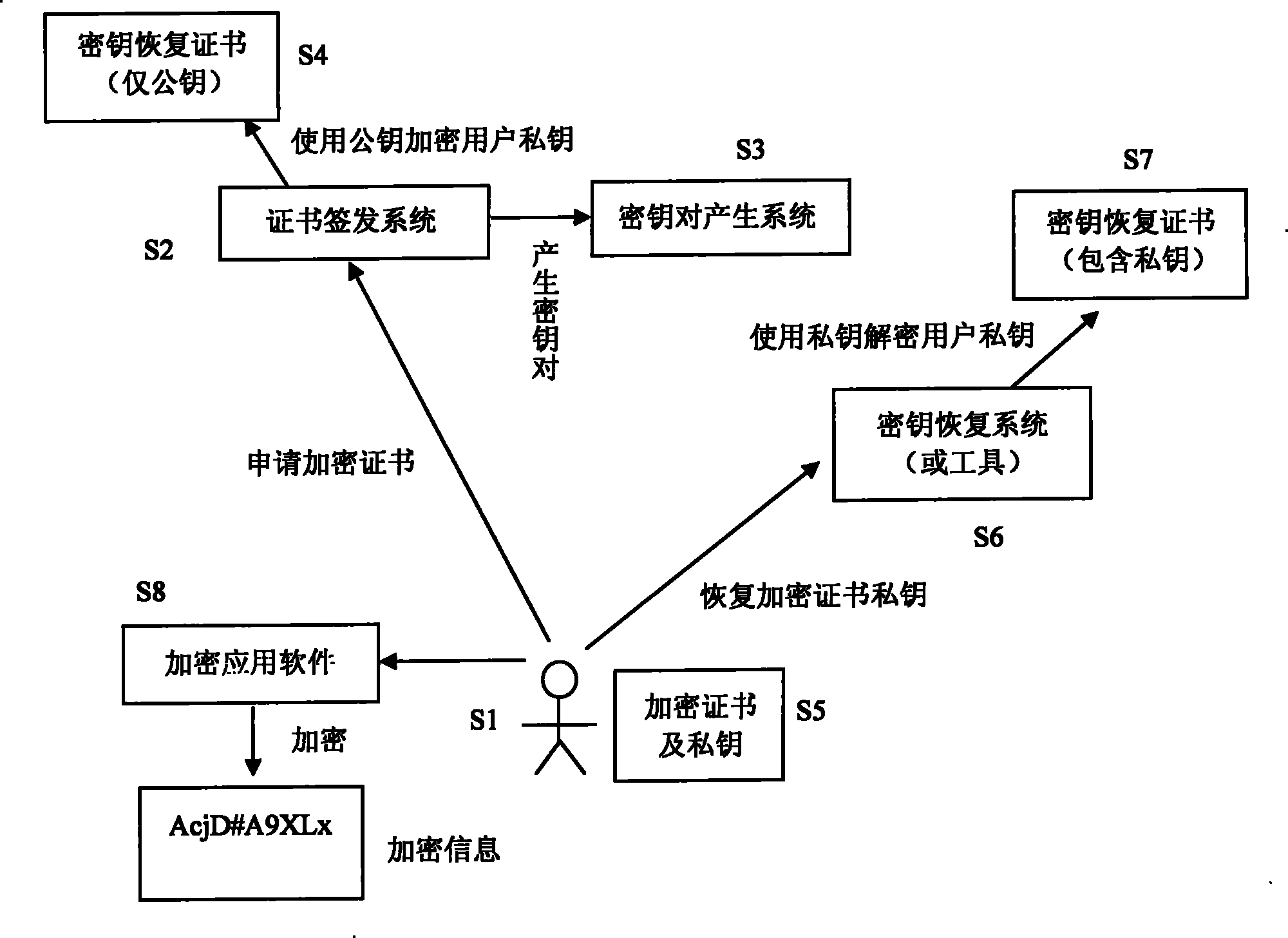
[0055] The present invention includes ( figure 1 ):
[0056] Certificate user S1: the owner of the encryption certificate and the user of the private key;
[0057] Certificate issuance system (CA system) S2: used to issue user encryption certificates;
[0058] Key pair generation system S3: used to generate user encryption certificate key pairs;
[0059] Key recovery certificate S4 (not including the private key): used to encrypt the private key of the user's encryption certificate;
[0060] User encryption certificate and private key S5: users use it to encrypt and decrypt information;
[0061] Key recovery system (or tool) S6: used to recover the private key of the user's encryption certificate;
[0062] Key recovery certificate and private key S7: used to decrypt the encrypted user certificate private key and private key recovery PIN code;
[0063] E...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com