Method and device for preventing network safety from desynchronizing
A network security and network technology, applied in the field of network security, can solve problems such as out of synchronization of network security parameters, failure of UE to access the network, etc., and achieve the effect of improving network availability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0083] Figure 7 It is Embodiment 1 of the present invention. In this embodiment, implementing the method for preventing network security out-of-sync provided by the embodiment of the present invention includes the following steps:
[0084] Step 701: the user terminal performs authentication and key agreement (AKA) on the original network (such as the EUTRAN network).
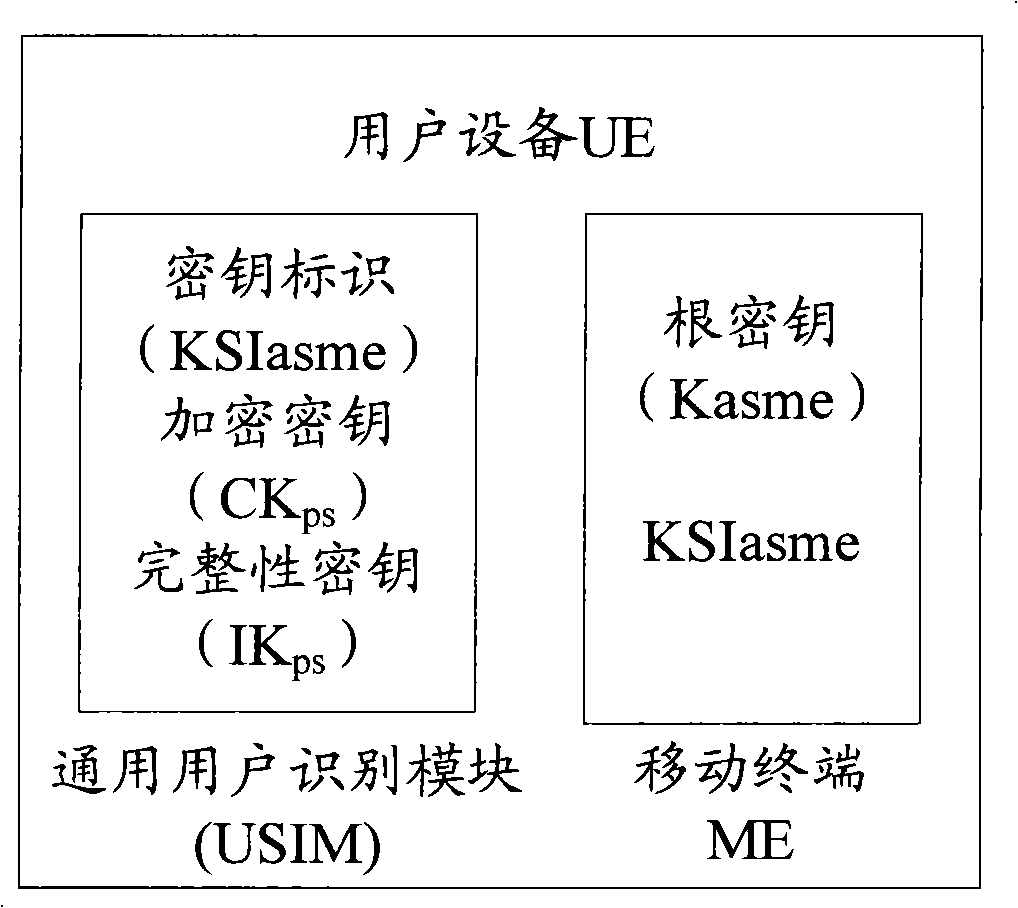
[0085] The original network mentioned above is the EUTRAN network, after the AKA process, the CK ps 、IK ps and the key identity of Kasme and Kasme KSIasme, CK ps 、IK ps, KSIasme is saved in USIM, and the same KSIasme as in USIM is saved in ME. It is the same as the prior art and will not be repeated here.
[0086] Step 702: Modify security parameters.
[0087] Preferably, after step 702, it also includes:
[0088] AKA is triggered again to generate new security parameter information.
[0089] In different embodiments, modifying security parameters may be implemented in different ways, and the embodiment...
Embodiment 2
[0090] Embodiment 2. In this embodiment, the modification of the security parameters is implemented by setting the security parameters of the USIM to an unavailable state. The unavailable state refers to making them unavailable by modifying the security parameters in the USIM. see Figure 8 , this embodiment specifically includes the following steps:
[0091] Step 801: the user terminal performs AKA on the original network.
[0092] Wherein the original network is an EUTRAN network, a UTRAN network or a GSM network.
[0093] When the UE is in the EUTRAN network, after the AKA process of the initial network, the CK is generated ps 、IK ps And the key identity of Kasme or KSI and Kasme KSIasme, CK ps 、IK ps And Kasme and KSIasme are saved in USIM, and the same KSIasme and Kasme in USIM are also saved in ME.
[0094] When the UE is in the UTRAN network, after the UTRAN AKA process, a CK is generated including ps 、IK ps And the key identity KSI, which is stored in the ME. ...
Embodiment 3
[0097] Embodiment 3, in this embodiment, the USIM is made unavailable by changing the value of START in the USIM, see Figure 9 , this embodiment specifically includes the following steps:
[0098] Step 901: the user terminal performs AKA on the original network.
[0099] Step 902: Set the START value of the USIM as a threshold value;
[0100] Or delete CK, IK;
[0101] Or set KSI to 111.
[0102] Figure 10 It is a corresponding signaling flowchart of an example provided by this embodiment. In this figure, the UE is in the EUTRAN network, and the specific steps are:
[0103] Step 1 to Step 2: UE is in the E-UTRAN network, and the UE sends a service request message to the MME through the eNB.
[0104] Step 3: There is no security parameter of the UE in the MME, the AKA process is triggered, and the UE and the MME generate the root key Kasme.
[0105] Step 4: On the UE side, the ME sets the START value in the USIM as the threshold.
[0106] When the START value of the US...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com