Method and device for defending against denial-of-service attacks
A denial of service attack and attack feature technology, applied in secure communication devices, computer security devices, instruments, etc., can solve problems such as denial of service attacks, inability to fully detect and block abnormal traffic attacks, and lack of effective integration of technologies. achieve the effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
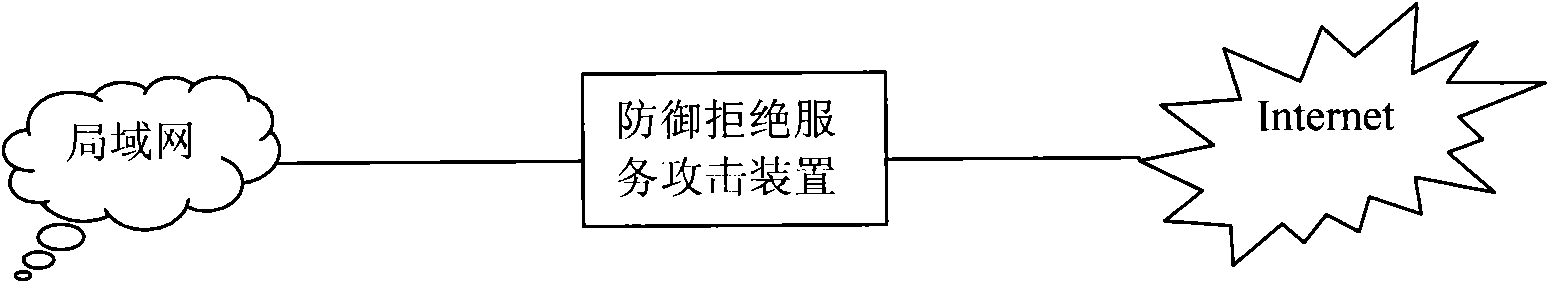
[0048] The core of the method of the present invention is to overcome the shortcomings of the prior art, and provide a device for defending against denial of service attacks in a TCP / IP network, so that the denial of service attacks can be effectively detected and blocked, so as to ensure the security of network applications and provide A secure network application environment for network users.
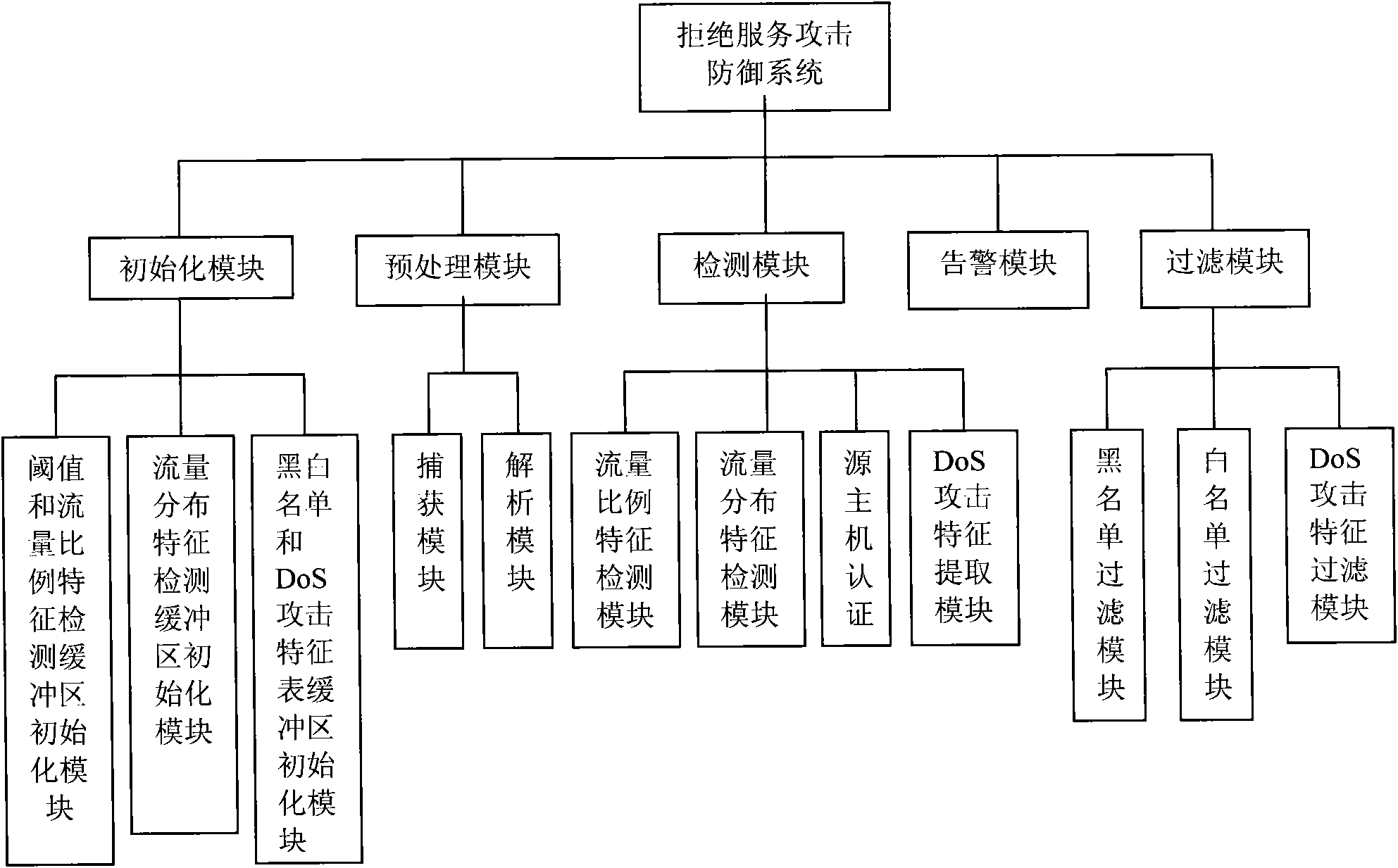
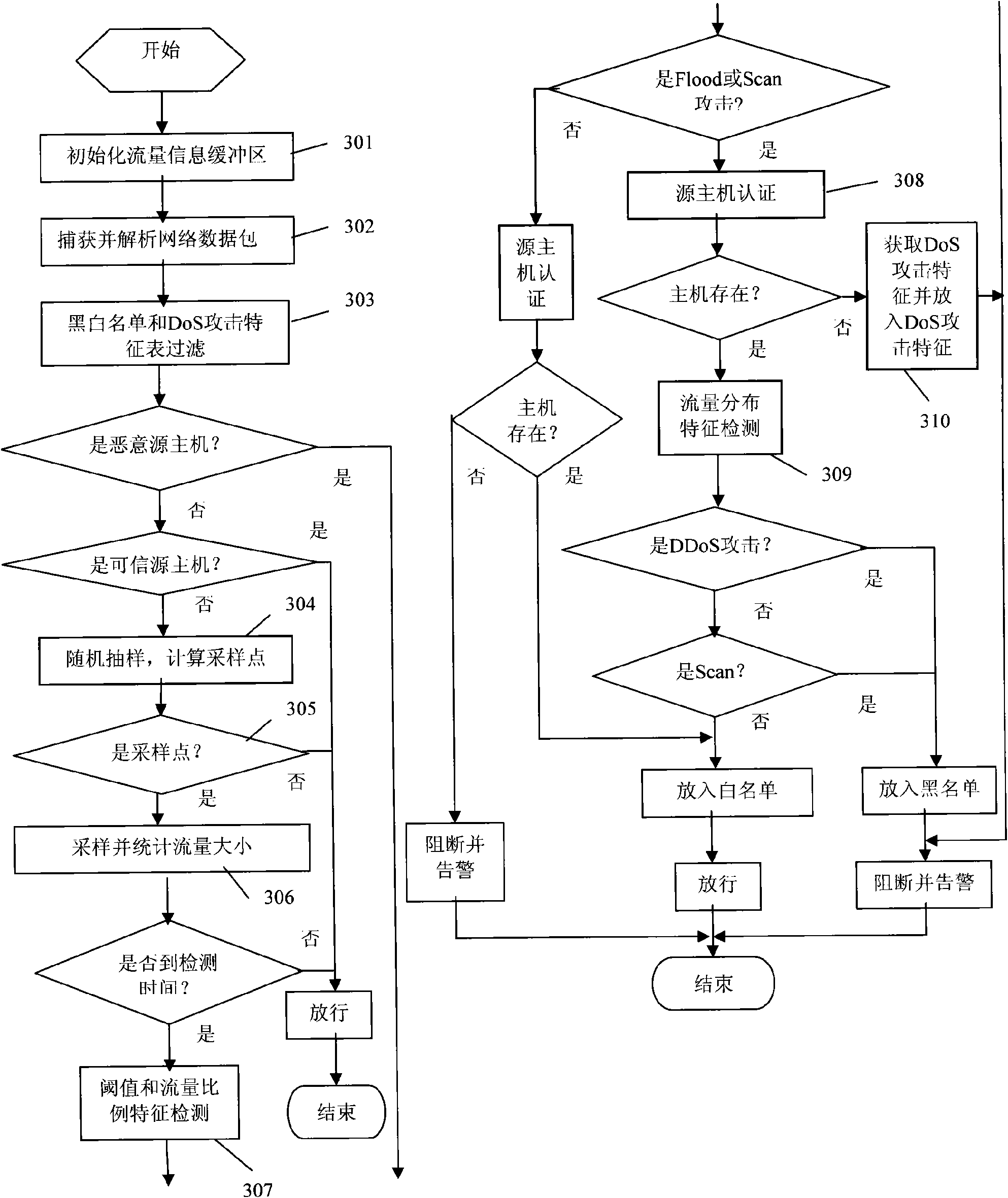
[0049] The general workflow for defending against denial of service attacks is:
[0050] The initialization stage includes initializing the threshold and traffic ratio feature detection buffer, initializing the traffic distribution feature detection buffer, initializing the black and white list buffer, and initializing the DoS attack feature table buffer;
[0051] Preprocessing stage, including capturing network packets and performing protocol analysis;
[0052] The detection stage includes detecting the threshold and traffic ratio characteristics, authenticating the identity of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com