Method for querying real MAC address corresponding to IP through IP by spanning networks
A technology of MAC address and IP address, applied in the field of computer information security auditing device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
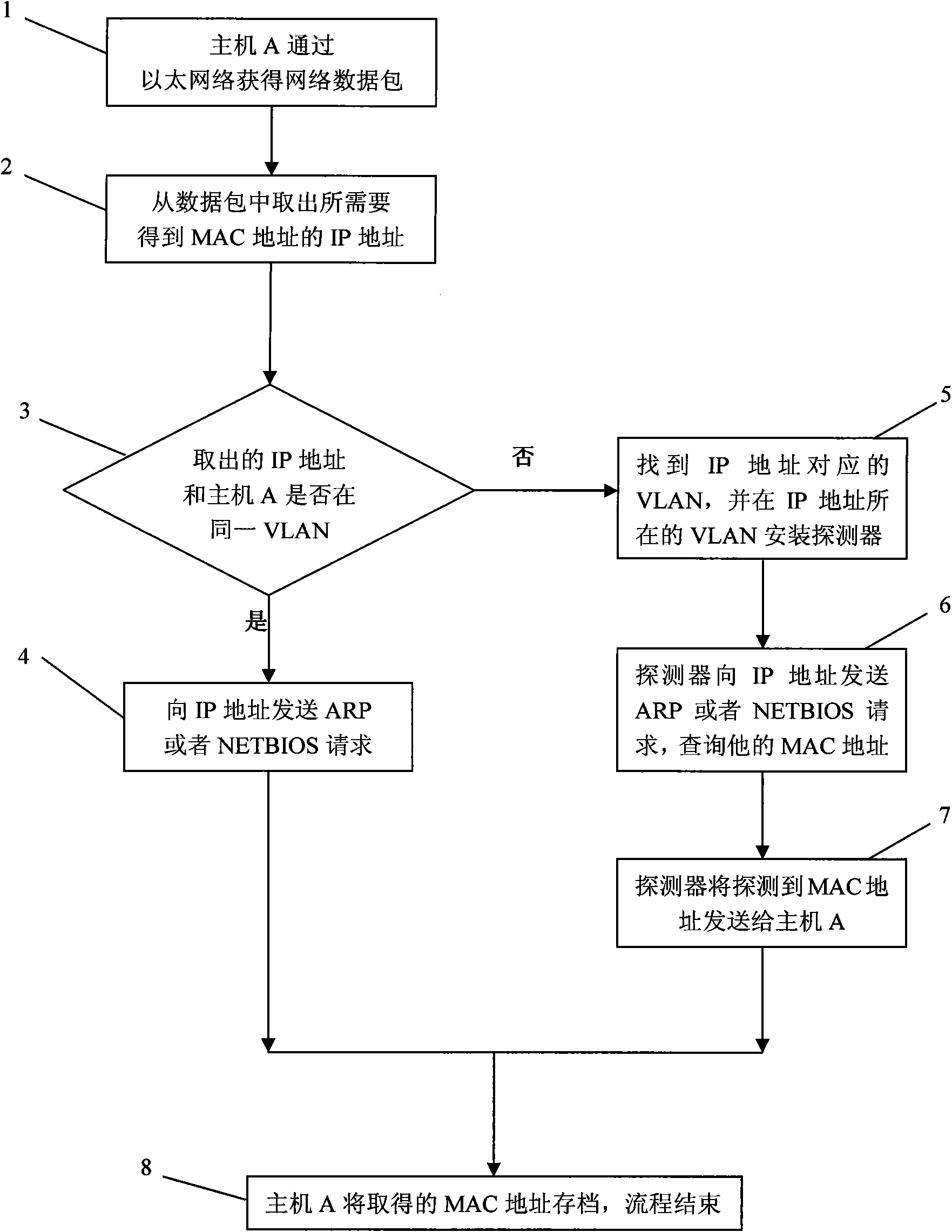
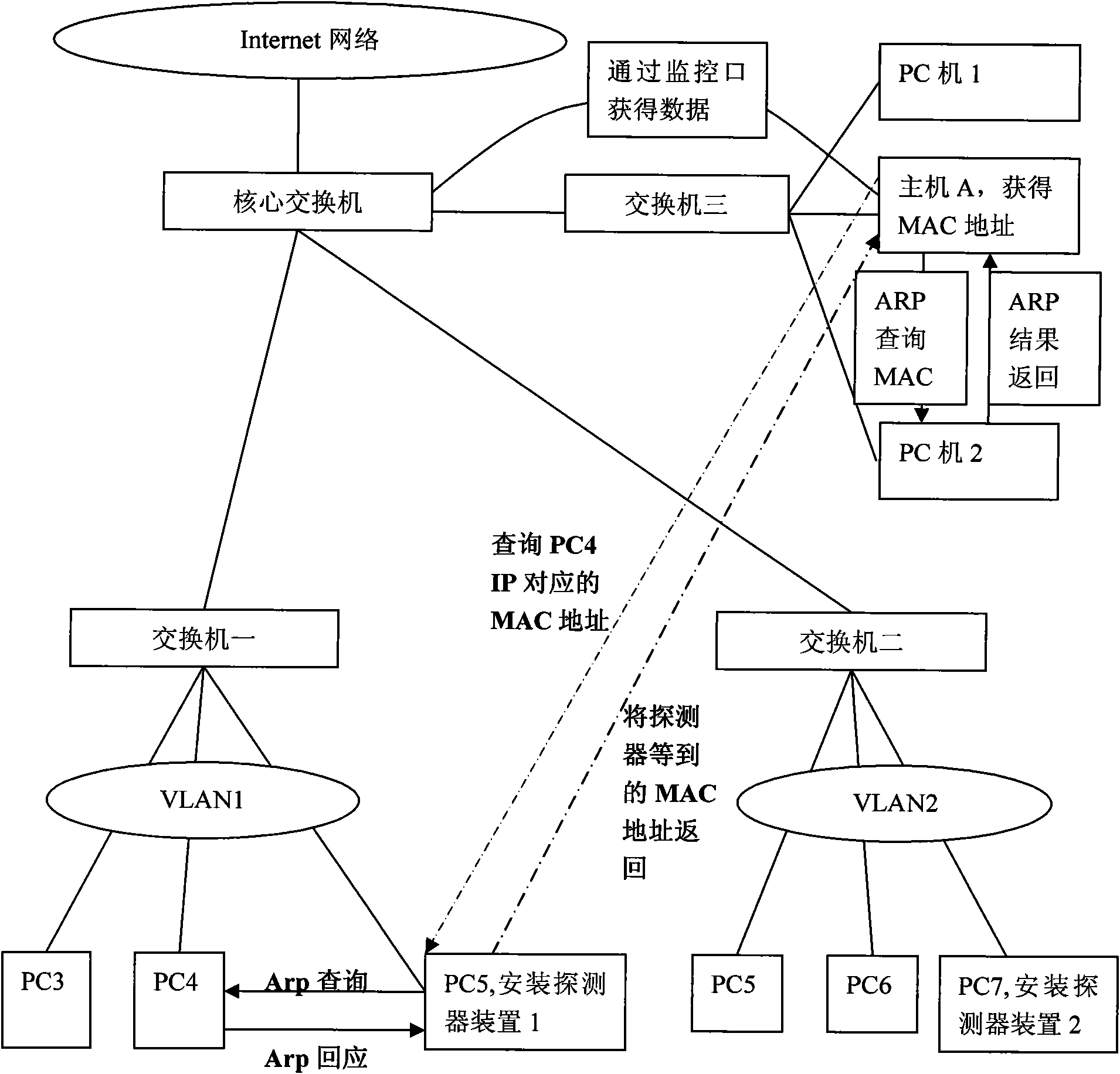
[0019] Such as figure 1 As shown, the method for querying the real MAC address corresponding to the IP address across the network through IP includes the steps of: obtaining a data packet through the network host A, and parsing the IP address from the data packet; querying the IP address corresponding to this IP address. Calculate the IP address and mask of the computer to see whether it is the data of the same VLAN; if the detection result is yes, then directly query the real MAC address through ARP or NETBIOS; to check whether it is, how to use NETBIOS or SNMP to see if it can be queried Corresponding to the MAC address, if the MAC address cannot be queried, then find one or more hosts B in the VLAN corresponding to the IP, and install a detection program; after the detection program is installed, query the real MAC address of the IP through ARP or NETBIOS, and get the query result , to send the data to host A.
[0020] Such as figure 1 Shown, computer information security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com