Proactive audit system and method
An active and subsystem technology, applied in the field of network security, can solve problems such as data content omission, difficulty in analyzing the content of user data packets, and inability to detect leaking behaviors, etc., to achieve the effect of comprehensive auditing and risk reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
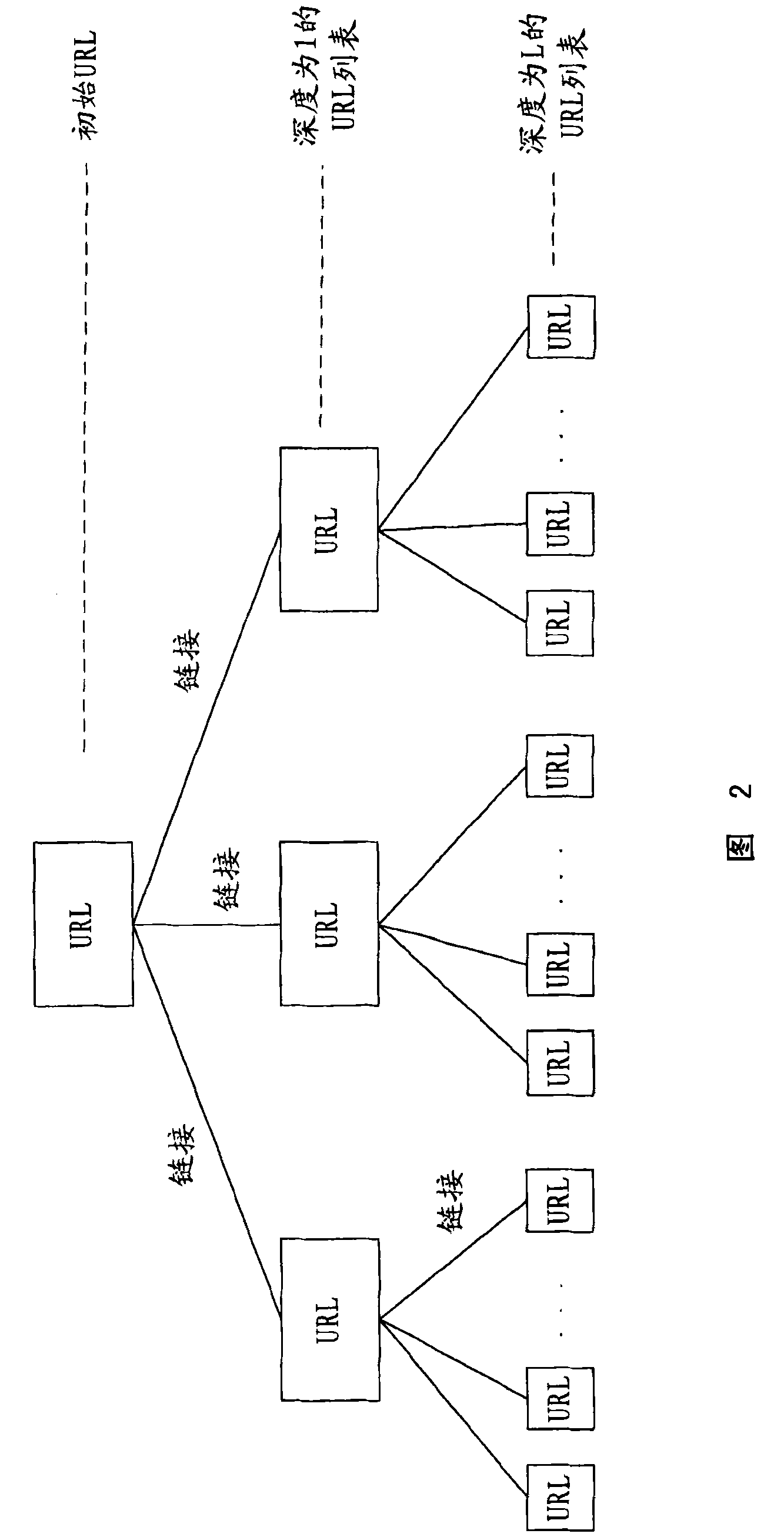
[0021] Before describing the specific embodiments of the present invention, the term URL, which is often used in the technical field, is firstly outlined, that is, a Uniform Resource Locator, which is an identification of a webpage existing on the Internet. As long as the URL is input in the web browser, the content of the webpage pointed to by the URL can be displayed in the web browser. Since there is a one-to-one correspondence between the URL and the content of the web page pointed to by the URL, the two can be used interchangeably hereinafter. For example, a URL containing illegal content means that the webpage pointed to by the URL contains illegal content.
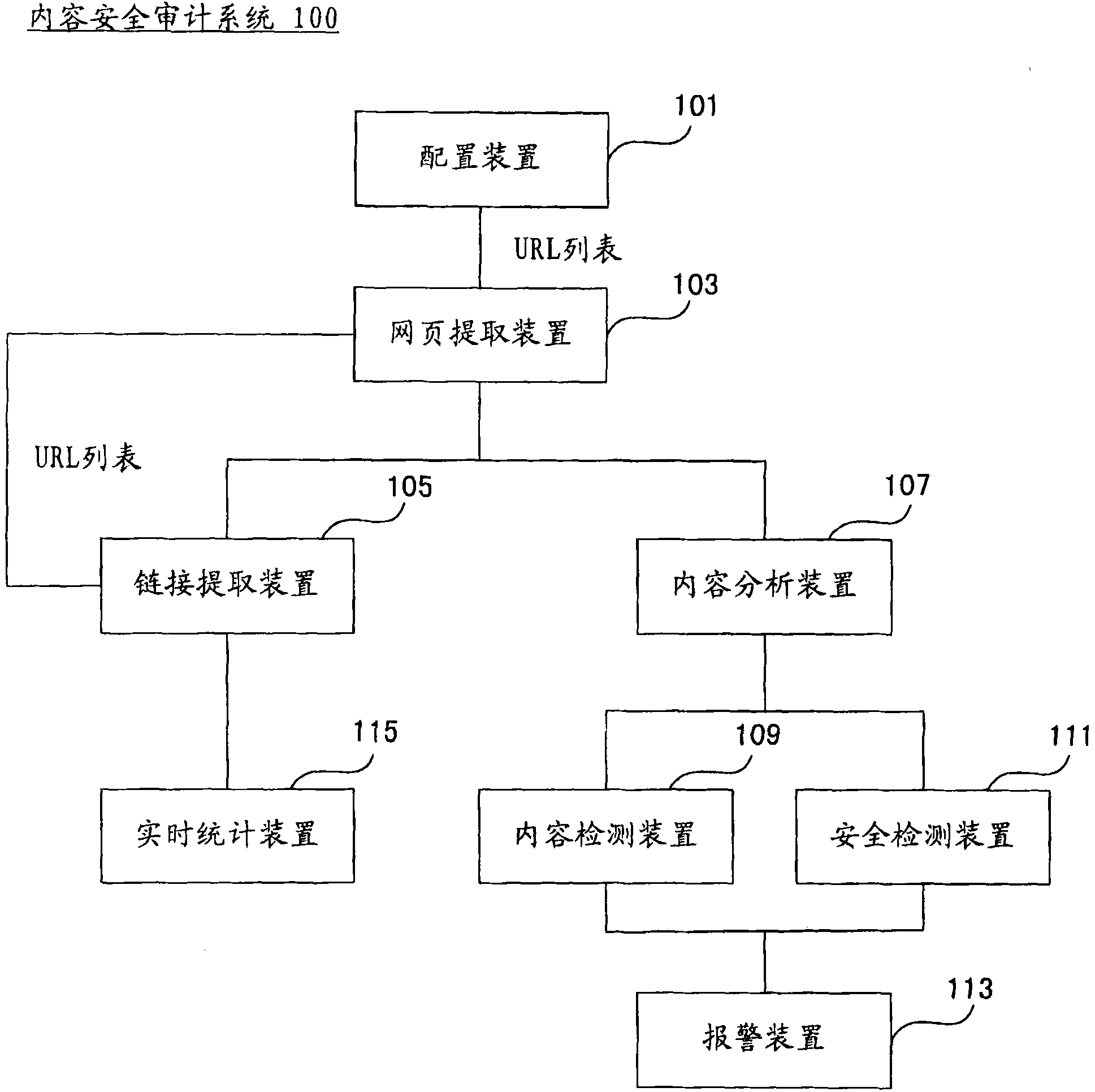
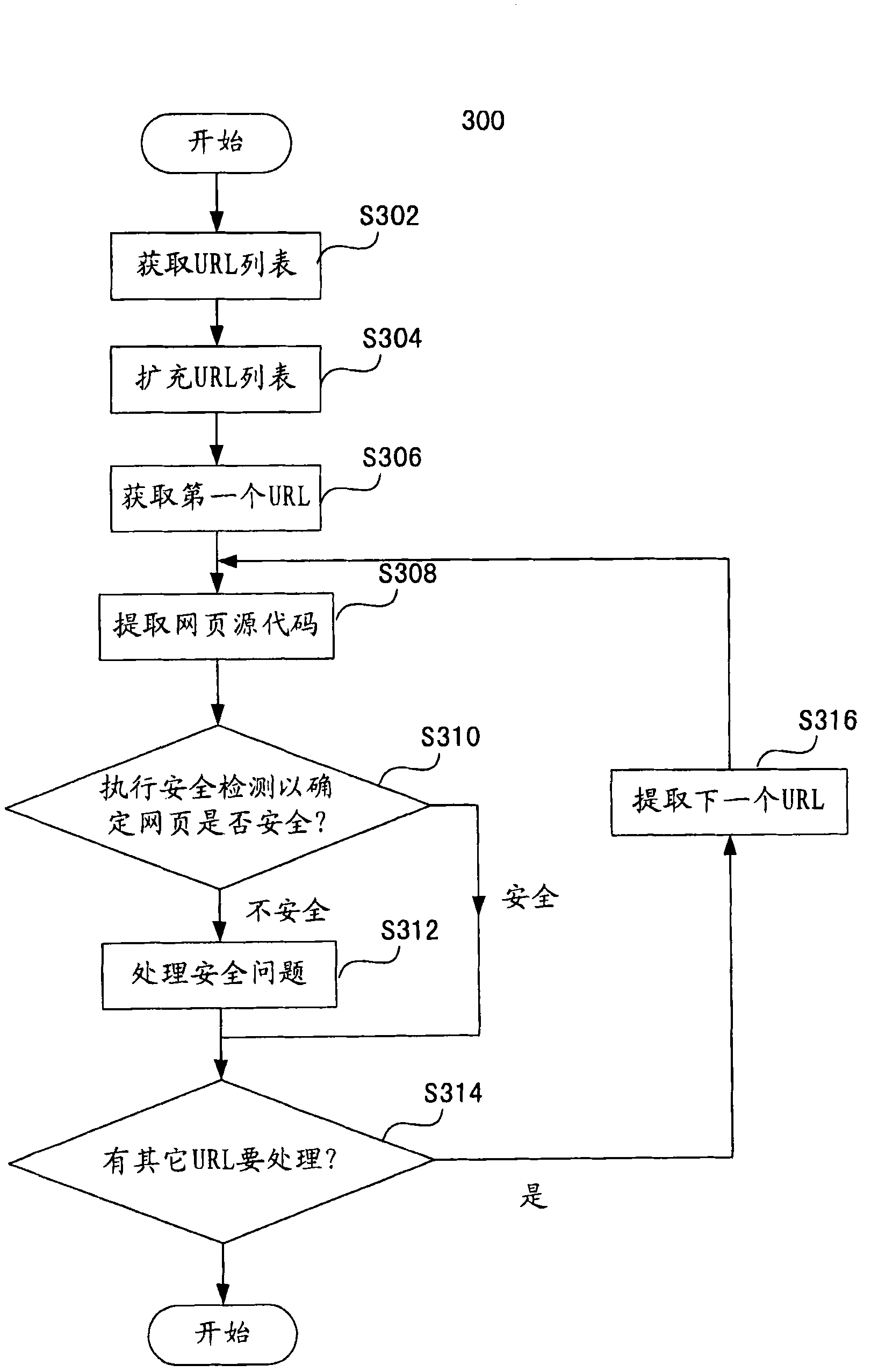
[0022] figure 1 A structural block diagram of the content security audit system 100 according to the embodiment of the present invention is illustrated. The configuration means 101 obtains a URL list designated to be actively audited, and provides the URL list to the web page extraction means 103 . For each URL i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com