USB equipment security and secrecy auditing system and auditing method
A technology of security, confidentiality and equipment, applied in the field of information security, it can solve problems such as loopholes in the protection effect, and achieve the effects of accurate audit results, improved protection effect, and strong versatility and universality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
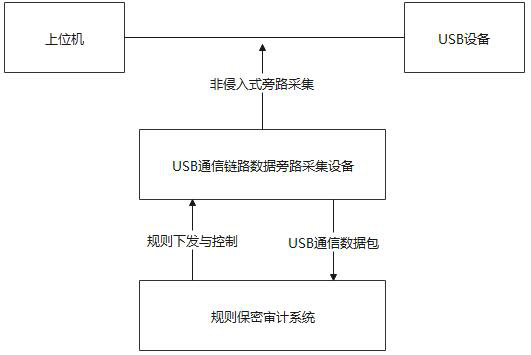
[0036] This embodiment discloses a USB device security and confidentiality audit system. The system is separately set up outside the USB device and the host computer. It is applicable to any operating system and can avoid the problem of malicious programs (or USB devices) bypassing the audit. like figure 1 As shown, the USB device security and confidentiality audit system includes a USB communication link data bypass acquisition device and a rule security audit system, and the USB communication link data bypass acquisition device is used for non-intrusive bypass acquisition of USB devices and a host computer. related data between, and filter the data according to the pre-set filtering rules. The rule security audit system is used to analyze and process the filtered data, and conduct a comprehensive audit of the USB device according to the set rules.
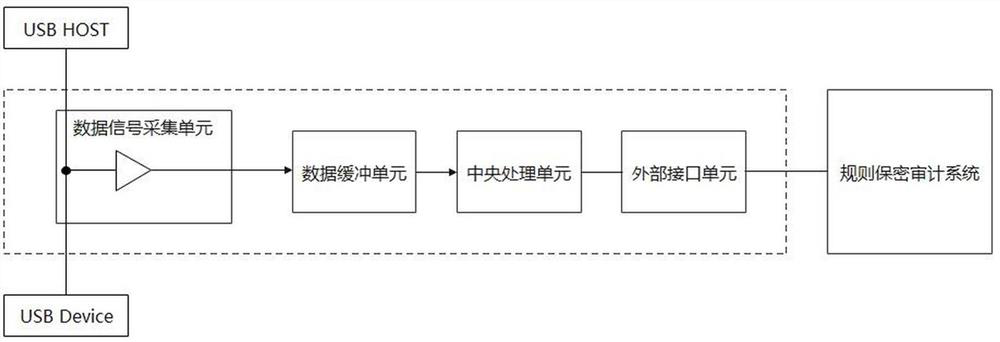
[0037] Specifically, as figure 2 As shown, the USB communication link data bypass acquisition equipment includes a data sign...
Embodiment 2
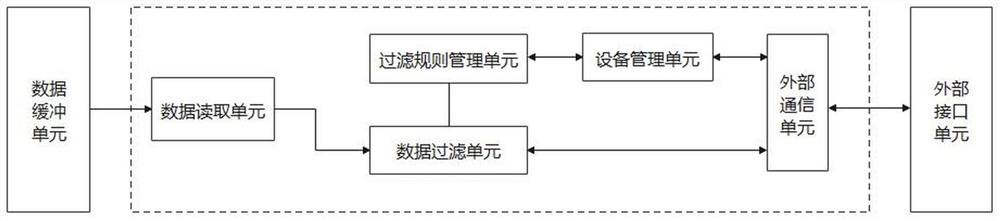
[0042] On the basis of Embodiment 1, this embodiment further limits the central processing unit. like image 3 As shown, the central processing unit includes a data reading unit, a data filtering unit, a filtering rule management unit, a device management unit and an external communication unit, and the data reading unit, the data filtering unit and the external communication unit are sequentially connected to the data buffer unit and the external communication unit. Between the external interface units, one end of the filtering rule management unit is connected to the data filtering unit, and the other end is connected to the external communication unit through the hardware management unit. Among them, the device management unit is responsible for reporting the information and status of the device itself to the rule security audit system, and receives the filtering rules distributed by the rule security audit system; the filtering rule management unit is responsible for the s...
Embodiment 3
[0044] On the basis of Embodiment 1 or Embodiment 2, in this embodiment, a data storage unit is also set in the rule security audit system, and the data storage unit is respectively connected with the hardware management unit, the rule management unit and the security security audit unit, and is used for Store security events or non-security events for later viewing and statistical analysis.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com