Application service access authentication method and application service access authentication agent
A technology for application services and authentication, applied in the field of communications, can solve problems such as unfavorable development of telecom value-added services, restricting the openness of telecom business capabilities, major security risks and performance pressures, etc., to reduce performance burden, expand scope, and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
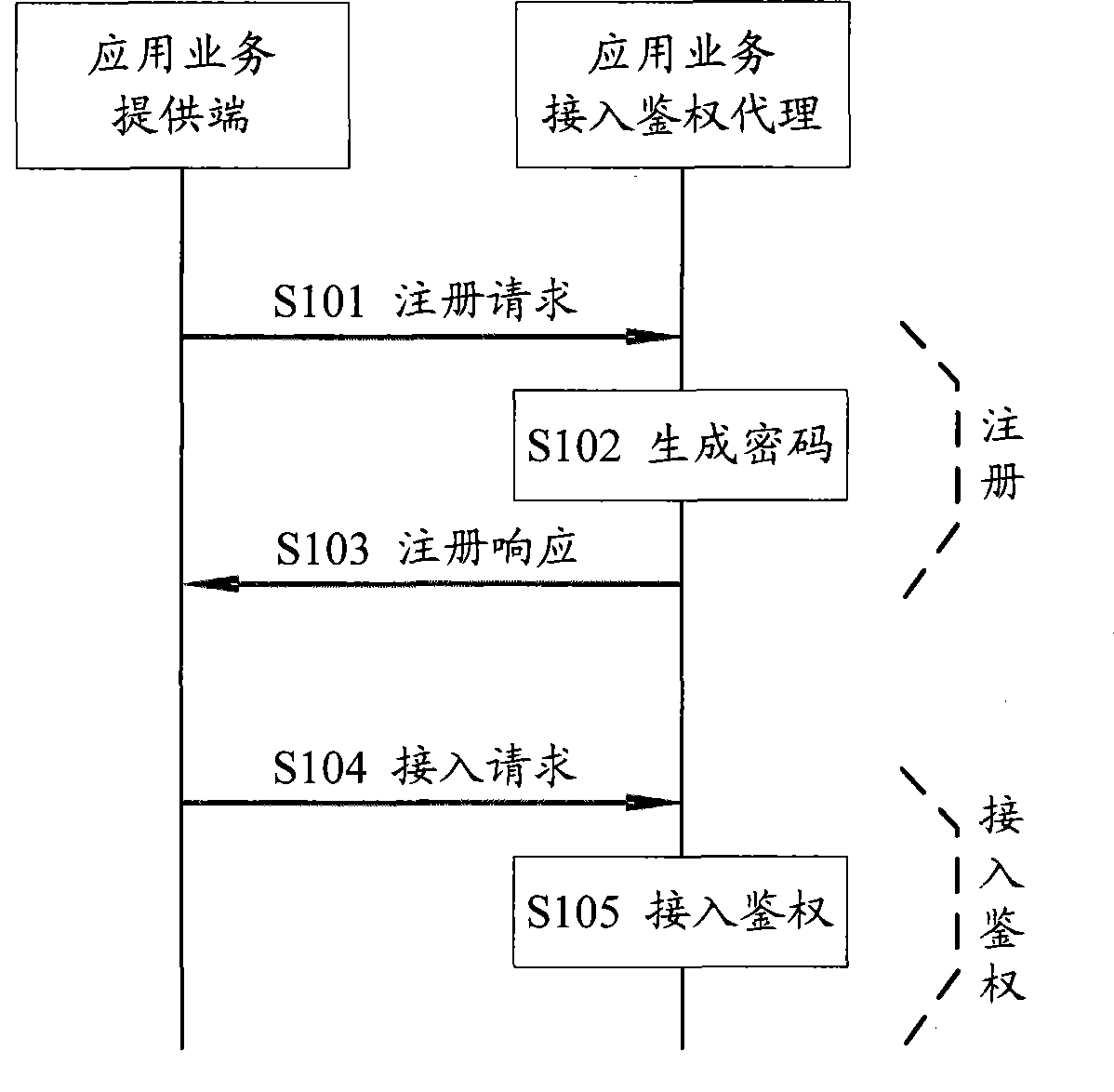
[0022] First, the application service access authentication method in the embodiment of the present invention is described:
[0023] After registering the application service and obtaining the password of the application service, the method includes:
[0024] Receive the access request sent by the provider of the registered application service, the access request carries the password of the application service, and perform access authentication on the application service according to the password of the application service.
[0025] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0026] figure 1 Shown is the flow chart of the method provided by the embodiment of the present invention, which specifically includes the following steps:
[0027] S101. The application service provider sends an application service registration request to the application service access authentication agent, where the registrati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com