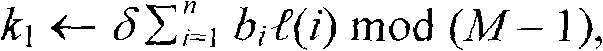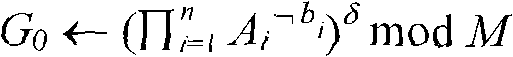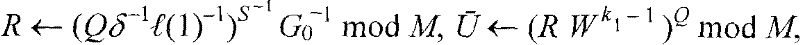Digital signature method based on multivariable array problem and super logarithm problem
A digital signature and super-logarithmic technology, which is applied to the public key of secure communication, user identity/authority verification, etc., can solve the problems of large security parameters, reduced signature efficiency, waste of storage space, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0108] The characteristic of the public-key digital signature method based on the multivariate permutation problem and the super-logarithm problem is that it allows each user to obtain two keys, one key can be made public, and one key can only be privately owned. In this way, there is no need to worry about the secret key being leaked during the transfer process. When it is agreed that the communication parties transmit information on the Internet, the sender uses his own private key to digitally sign the file or message, and the receiver uses the sender's public key to verify it after receiving the file and signature code.
[0109] Each user can obtain two keys from the designated CA digital certificate center. The CA center is an institution that registers users, generates, distributes and manages keys. Its main function is to use the key generation method to generate a pair of public key and private key of the user.
[0110]This digital signature method can be implemented...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com