Identity authentication method and device
A technology of identity authentication and user identity authentication, which is applied in the direction of instruments, induction recording carriers, character and pattern recognition, etc., can solve the problems of certificates and IC cards being easily used and counterfeited, insufficient storage space, etc., so as to facilitate promotion and improve The effect of safety and simple structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
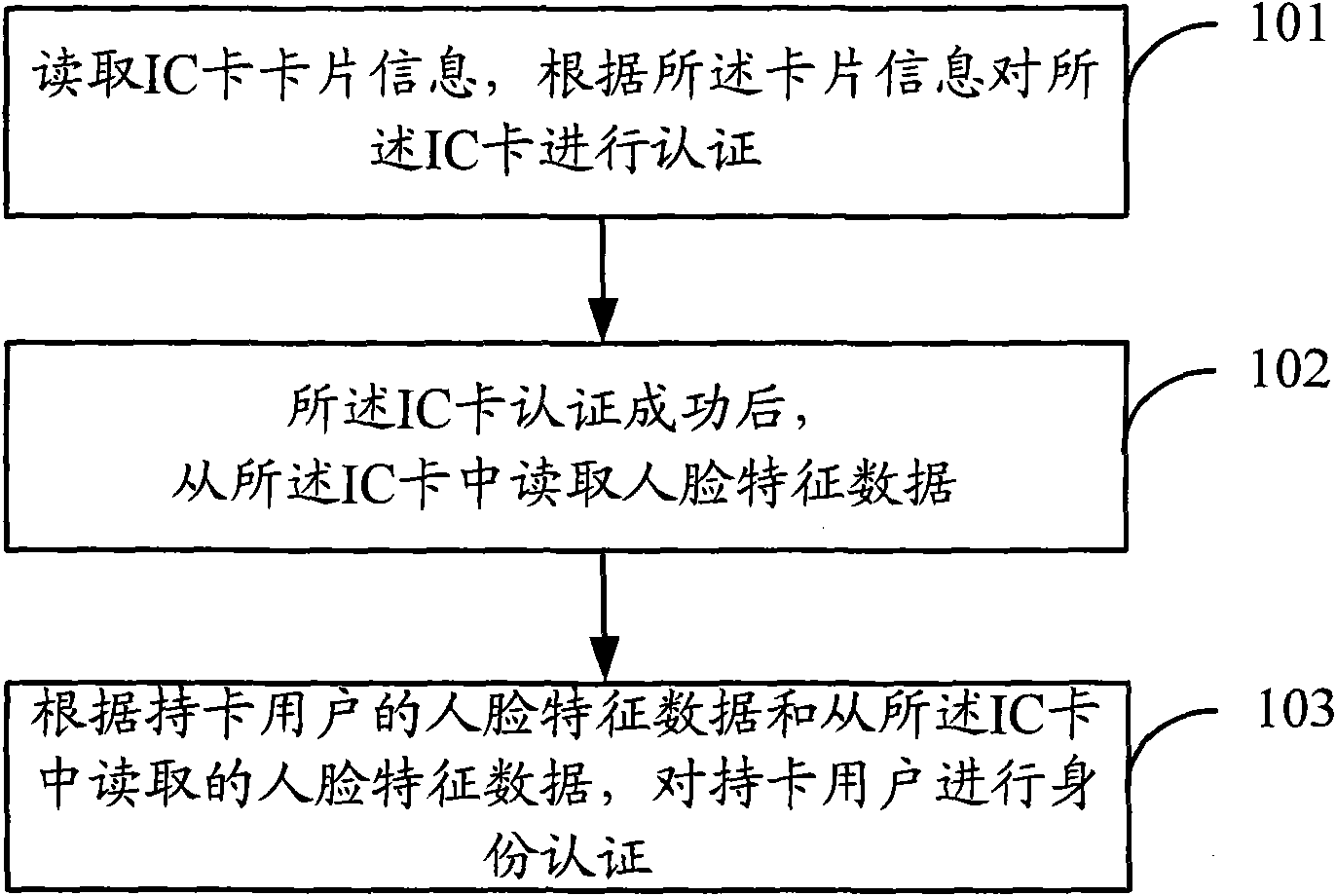
[0043] Such as figure 1 As shown, in the embodiment of the present invention, the flow of the identity authentication method may include:
[0044] Step 101, read the card information of the IC card, and authenticate the IC card according to the card information.
[0045] Step 102. When the IC card is successfully authenticated, read facial feature data from the IC card.
[0046] Step 103: Perform identity authentication on the card user according to the face feature data of the card user and the face feature data read from the IC card.
[0047] Depend on figure 1 As can be seen from the flow shown, the IC card needs to be pre-written with card information and face feature data.
[0048] The card information of the IC card, as the basic information of the user, can be stored in a memory as the card's authorization identification, so as to facilitate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com