Method and device for positioning cross-site scripting attack source
A technology of cross-site scripting attack and positioning method, which is applied in the field of cross-site scripting attack source positioning method and device field, can solve the problem of inability to accurately locate the source of cross-site scripting scripting attack, and achieve the effect of convenient traceability and security emergency response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
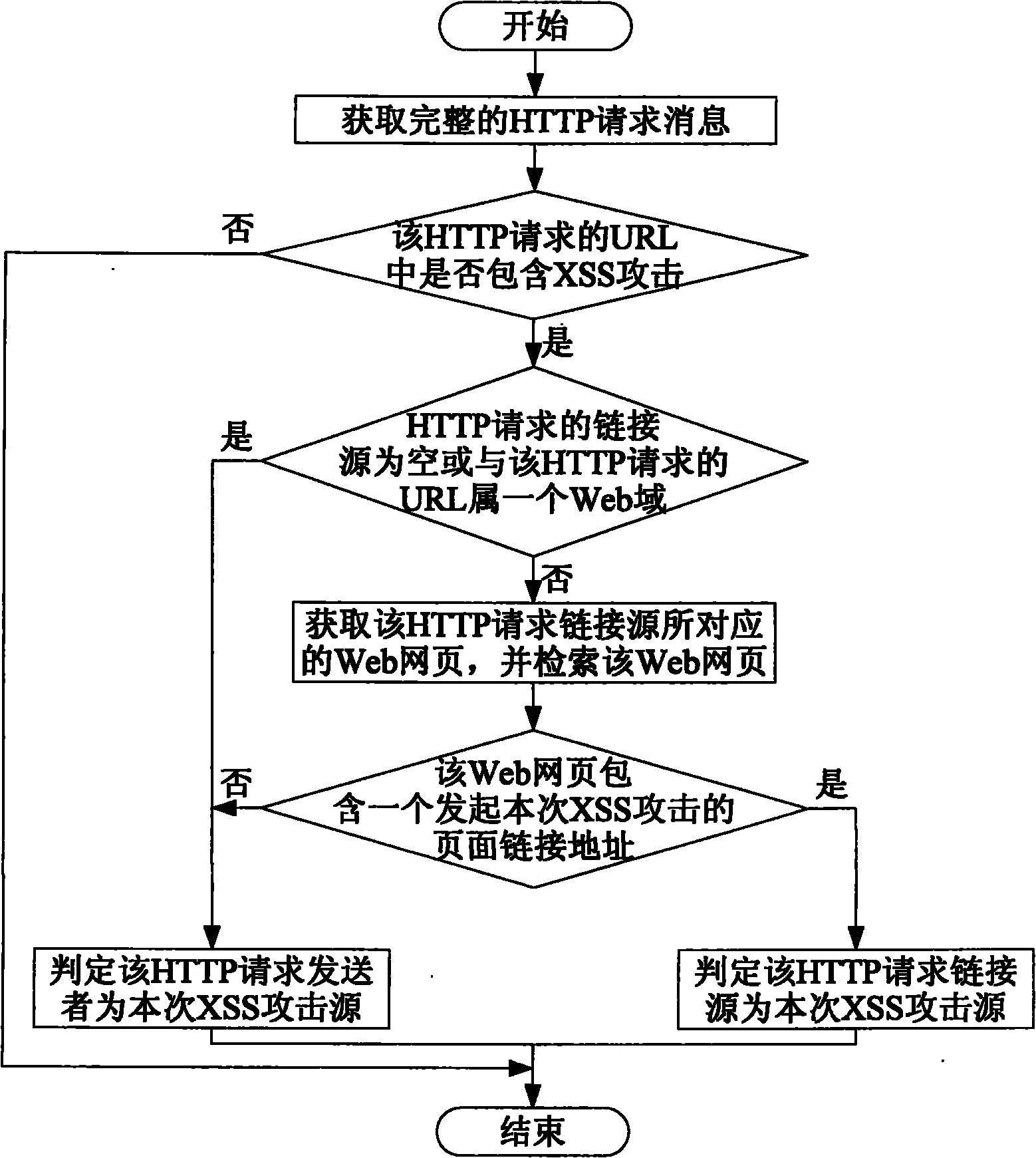
[0062] The first embodiment is a method for locating the source of a cross-site scripting attack, including the following steps:
[0063] A. Obtain the complete HTTP request message, check whether the HTTP request contains an XSS attack, if an XSS attack is found, perform step B, otherwise end;
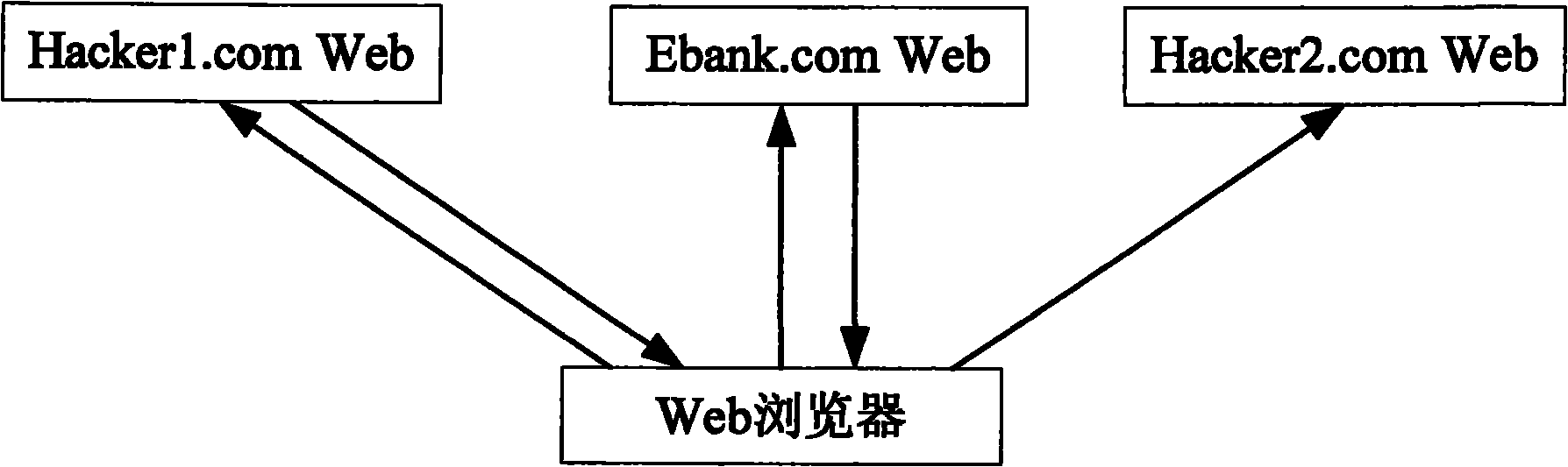
[0064] B. Analyze the link source of the HTTP request, and when it is found that the link source of the HTTP request is empty, or the link source and the URL of the HTTP request belong to the same Web domain, it is determined that the sender of the HTTP request is this XSS Attack the source and end, otherwise continue to step C;
[0065] C. Obtain the Web page corresponding to the HTTP request link source, and retrieve the Web page. When it is found that the Web page contains a page link address that initiated the XSS attack, it is determined that the HTTP request link source is the source of the XSS attack Otherwise, it is determined that the HTTP request sender is the source of the XSS ...
Embodiment 2
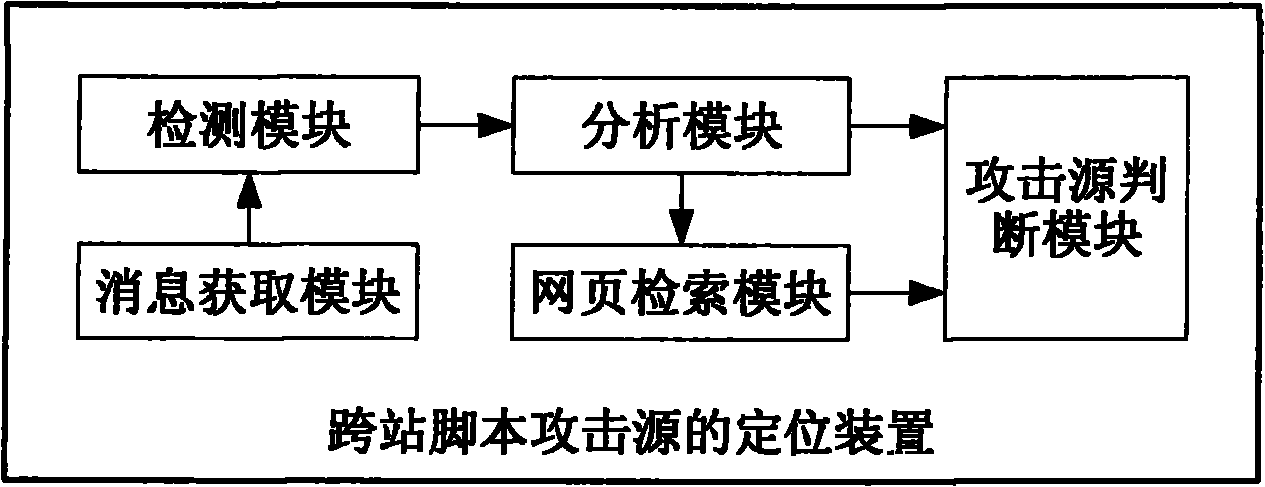
[0113]实施例二,一种跨站脚本攻击源的定位装置,包括:消息获取模块、检测模块、分析模块、网页检索模块及攻击源判断模块。
[0114]所述消息获取模块用于获取完整的HTTP请求消息,发送给所述检测模块;
[0115]所述检测模块用于检查所收到的HTTP请求中是否包含XSS攻击,如果发现XSS攻击,则将所述HTTP请求发送给所述分析模块,否则不进行处理;
[0116]分析模块用于分析所收到的HTTP请求的链接源,当发现该HTTP请求的链接源为空,或者所述链接源与该HTTP请求的URL同属于一个Web域时,发送消息给所述攻击源判断模块;否则将所述HTTP请求发送给所述网页检索模块;
[0117]所述网页检索模块用于获取所收到的HTTP请求链接源所对应的Web网页,并检索该Web网页,当发现该Web网页包含一个发起本次XSS攻击的页面链接地址,则发送表示"包含”的消息给所述攻击源判断模块,否则发送表示"不包含”的消息给所述攻击源判断模块;
[0118]所述攻击源判断模块用于当收到所述分析模块发送的消息时,判定该HTTP请求的发送者为本次XSS攻击源;以及当收到所述网页检索模块发送的表示"包含”的消息时判定所述HTTP请求链接源为本次XSS攻击源,当收到所述网页检索模块发送的表示"不包含”的消息时判定该HTTP请求发送者为本次XSS攻击源。
[0119]本实施例中,所述检测模块具体包括:
[0120]提取子模块,用于从HTTP请求中提取用户输入数据;
[0121]解码子模块,用于对用户输入的数据解码;
[0122]注入脚本提取子模块,用于对解码后的用户输入数据执行文档对象模型结构分析,将解码后的用户输入数据转换为一个文档对象模型树;从所述文档对象模型树中提取注入脚本;
[0123]判断子模块,用于从注入脚本中提取XSS攻击行为特征;如果能提取到,则判断为发现XSS攻击;否则不进行处理。
[0124]各子模块的具体实现细节同实施例一中相应部分的方法一致,这里不再赘述。
[0125]本实施例中,所述分析模块所分析的HTTP请求的链接源是指该HTTP请求的上一链接页面,包含在HTTP请求的Referer协议字段中。
[0126]本实施例中,所述分析模块通过比较HTTP请求链接源中的Web域名与HTTP请求Host协议字段中的Web域名是否一致来判断该HTTP请求链接源和该HTTP请求URL是否属于...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com