Method for collaboratively resisting overlay layer DDoS attack in P2P network
A P2P network and overlay technology, applied in the field of P2P network security, can solve problems such as query message flooding attacks, inability to respond to connection requests, and exhaustion of TCP connection resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
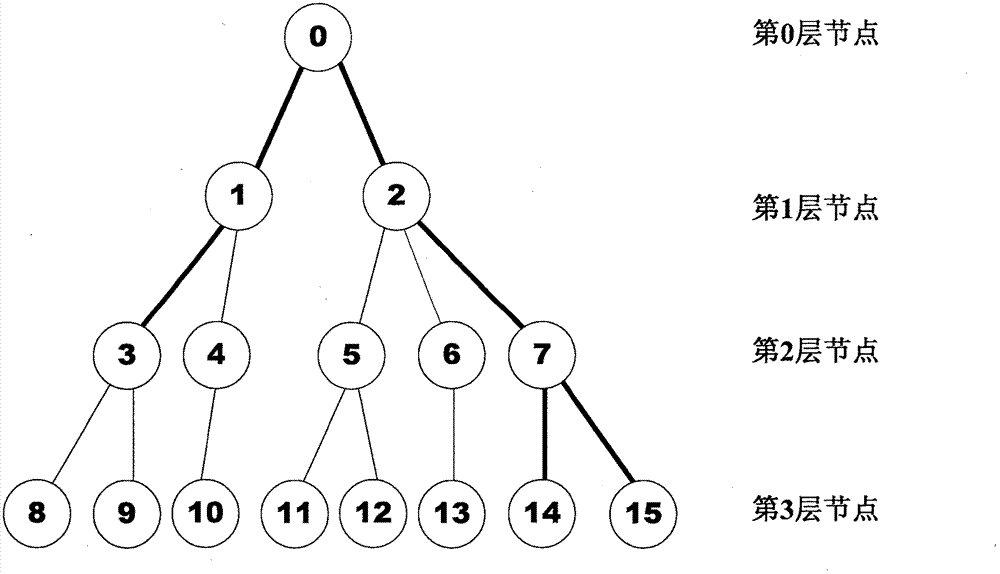
[0047] In structured P2P networks such as Chord, Pastry, Tapestry, CAN, Kademlia, etc., the message routing process with a certain node as the destination node presents a tree-like feature with the node as the root node. With the increase of message routing hops, Messages will continue to converge and finally reach the destination node. The embodiments of the present invention are not aimed at a specific network, but are applicable to all DHT-based structured P2P networks.
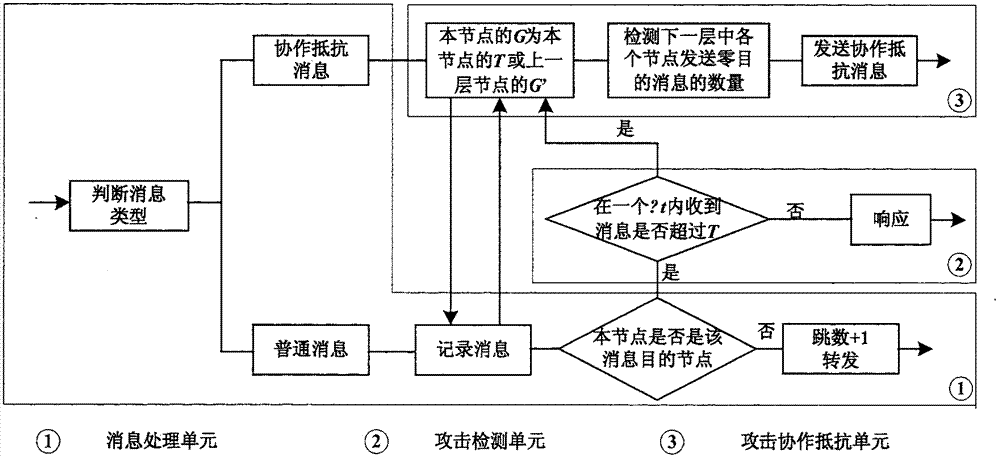
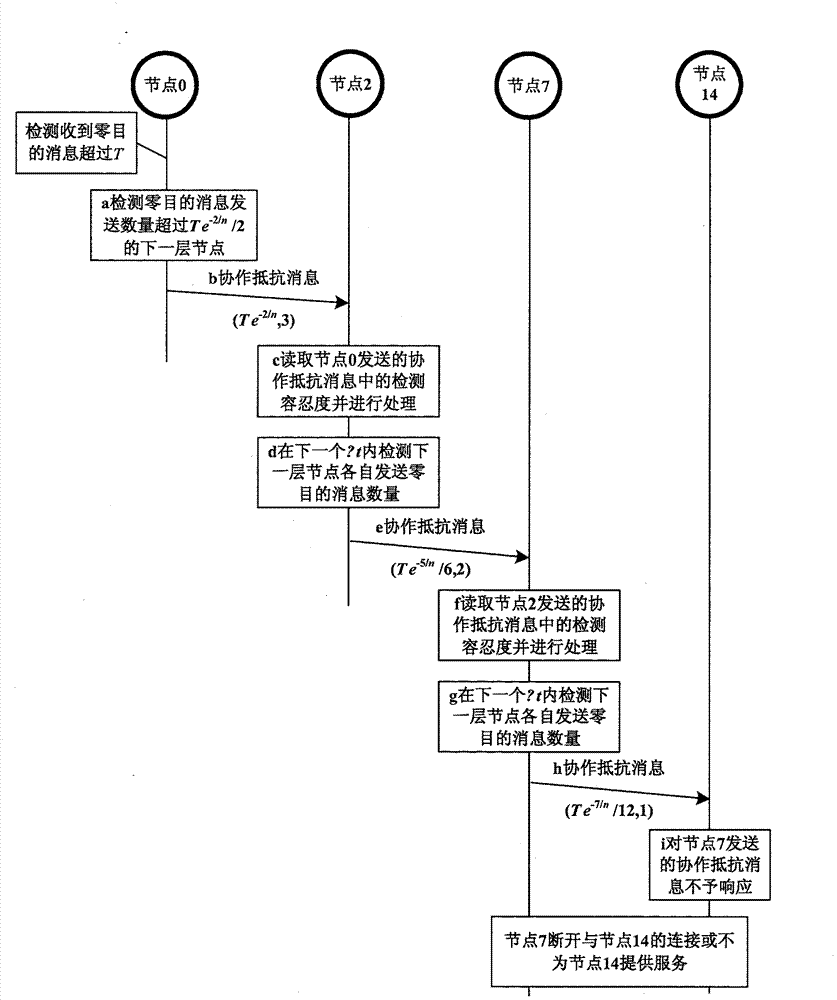
[0048] figure 1 It is a schematic diagram of the P2P network structure of the present invention. The maximum number of nodes allowed by the structured P2P network is n, and the number of currently online nodes is 16. Among them, nodes 3, 14, and 15 send a large number of query messages to node 0. If node 0 detects that the number of zero-purpose messages exceeds its attack tolerance Θ in a Δt, it is considered to have suffered a DDoS attack, and node 0 is recorded as the 0th layer node. For the convenien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com