Frequent subgraph mining based abnormal intrusion detection method
A technology of frequent subgraphs and intrusion detection, which is applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve the problems of difficulty in obtaining variable-length feature patterns, difficult trade-offs, etc., so as to reduce the dependence on training data and improve the The effect of discriminating ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
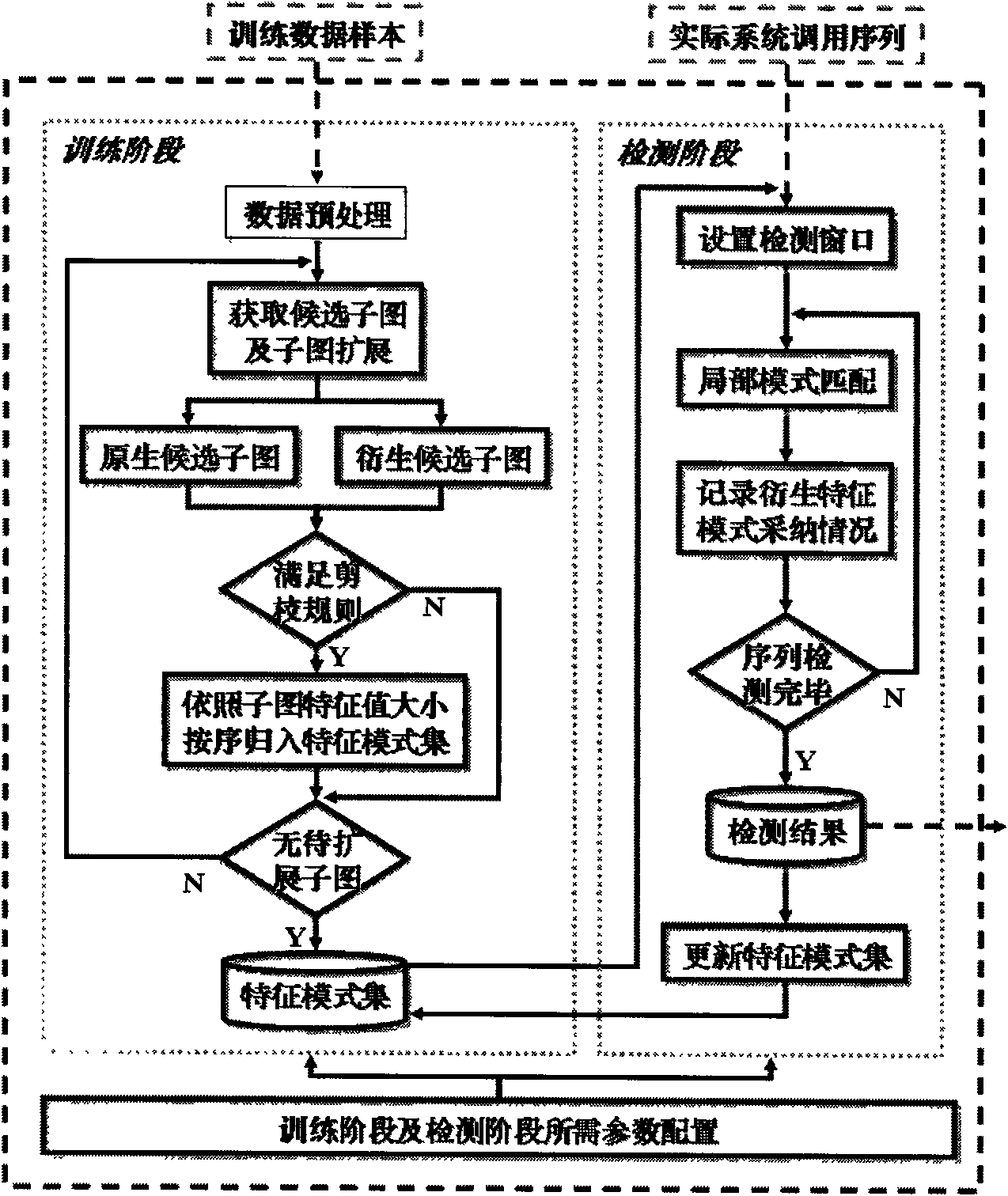
[0050] The detection model and basic idea of the present invention:
[0051] The traditional intrusion detection method based on the system call sequence, whether it is the initial research on the call sequence, or the introduction of mathematical models such as hidden Markov or artificial immunity, the core idea has basically not changed, and it is an enumeration matching method. . The enumeration matching method divides the original system call sequence in various preset forms, and finally takes the sequence fragments that meet the requirements—called short system call sequences—as the most basic data processing unit and classifies them into feature pattern set. Therefore, although the technical means used in the construction of the intrusion detection model have their own characteristics, the feature patterns obtained by most traditional methods have inevitable limitations, that is, they only reflect the local characteristics of a certain trained system call sequence. ....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com