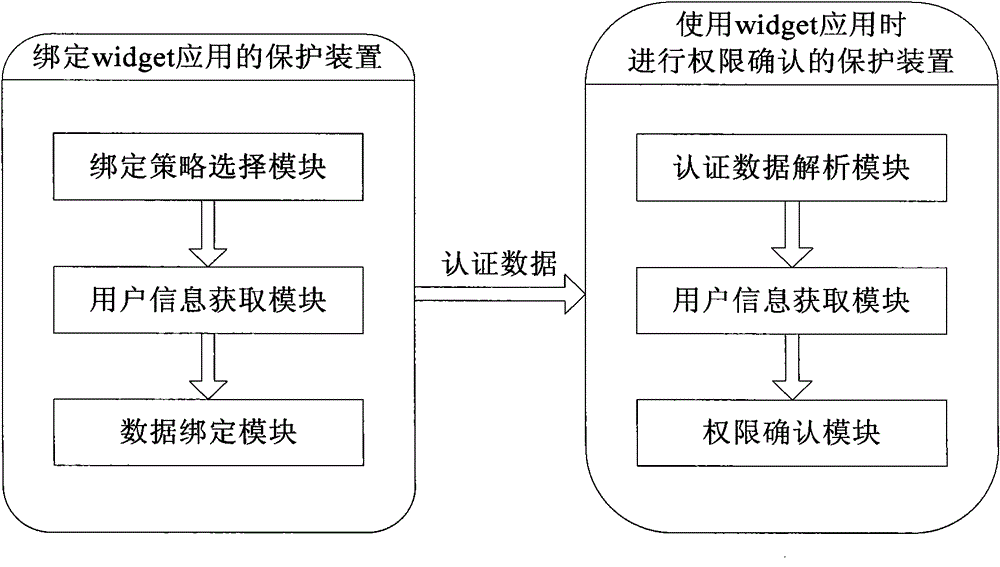
A widget application protection method and device
A user and algorithm technology, applied in the field of mobile Internet, to achieve the effect of improving user experience and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
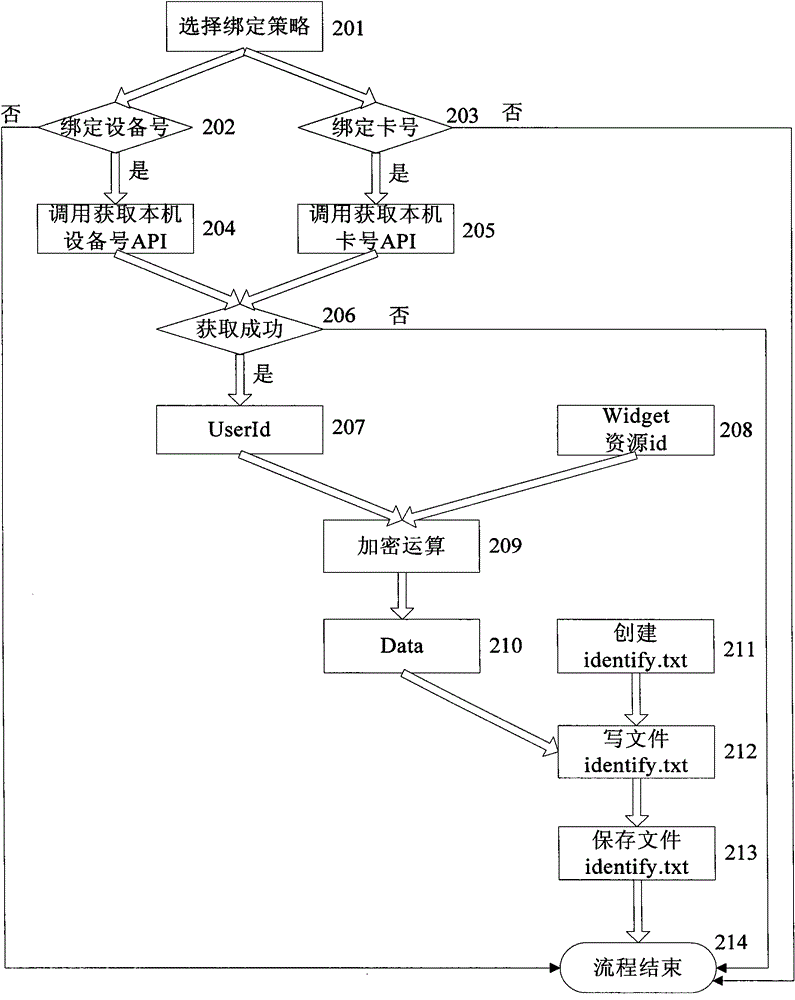
[0052] Such as figure 2 As shown, the terminal A binding user identity process includes the following steps:
[0053] Step 1: Choose a binding usage strategy for a widget application user; including the following steps:
[0054] Step 201, the user first selects a binding policy for a widget application through the corresponding menu on terminal A, and the terminal determines that the user chooses to bind with the device, then executes step 202, and if it judges that the user chooses to bind with the SIM card, then executes step 203, If the user does not choose, the process ends;
[0055] Step 202, start the process of binding with the device, and execute step 204;
[0056] Step 203, start the process of binding with the card number, and execute step 205;
[0057] If the selected binding strategy is 1) bind the device number of terminal A, the widget application downloaded, installed and running on terminal A can only be used on terminal A, and terminal B cannot continue to...
Embodiment 2
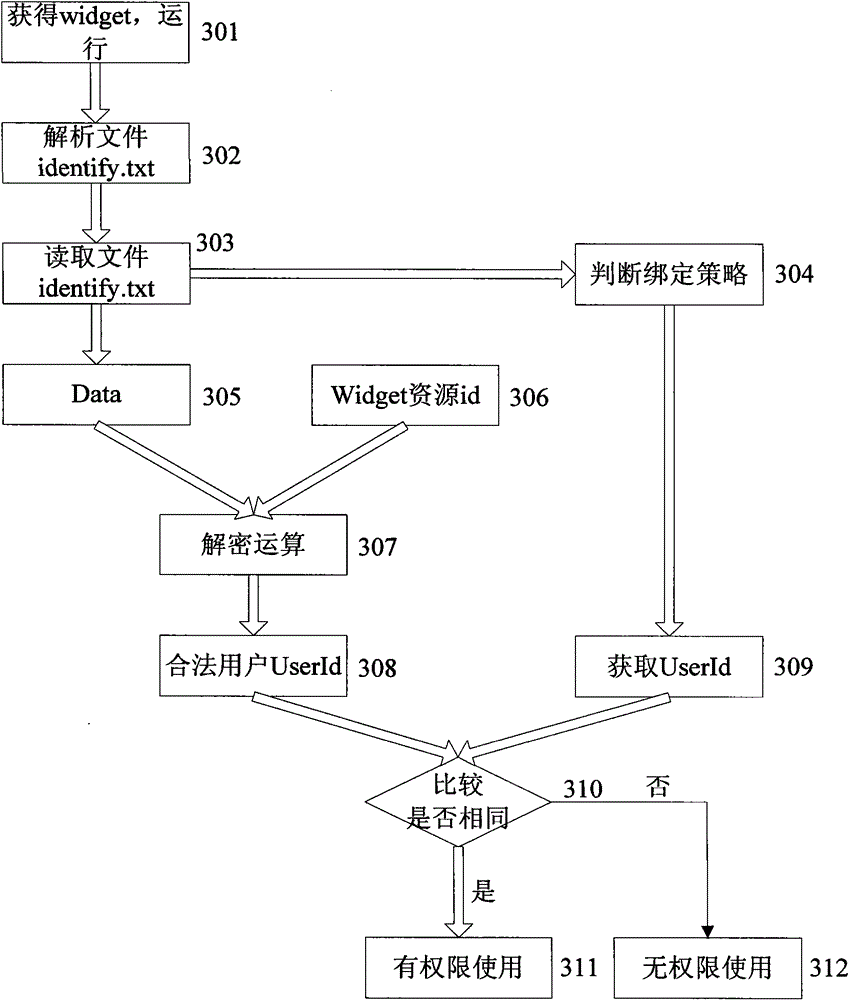
[0079] Such as image 3 As shown, the permission confirmation process when terminal B uses the widget application includes the following steps:
[0080] Step 1: After terminal B obtains the widget application from terminal A, when running the widget application, the widget engine first decrypts the UserId of the legal user from the Data; including the following steps:
[0081] Step 301, terminal B runs the widget application after obtaining the widget application from terminal A through some means;
[0082] Step 302, the widget engine parses the widget application resource package, and parses the identify.txt file therein;
[0083] Step 303, the widget engine reads the data stored in the file;
[0084] Step 304, according to the policy identifier, judge whether terminal A has adopted the device number binding policy or the card number binding policy, and execute step 309;
[0085] Step 305, read authentication data;
[0086] Step 306, read the id of the widget application;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com