VoIP voice encryption protection method, node and system
A technology of voice encryption and encryption algorithm, applied in transmission system and key distribution, can solve the problems of inability to meet the characteristics of VoIP calls, inability to ensure the security of user session information, and inability to meet legal monitoring requirements, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
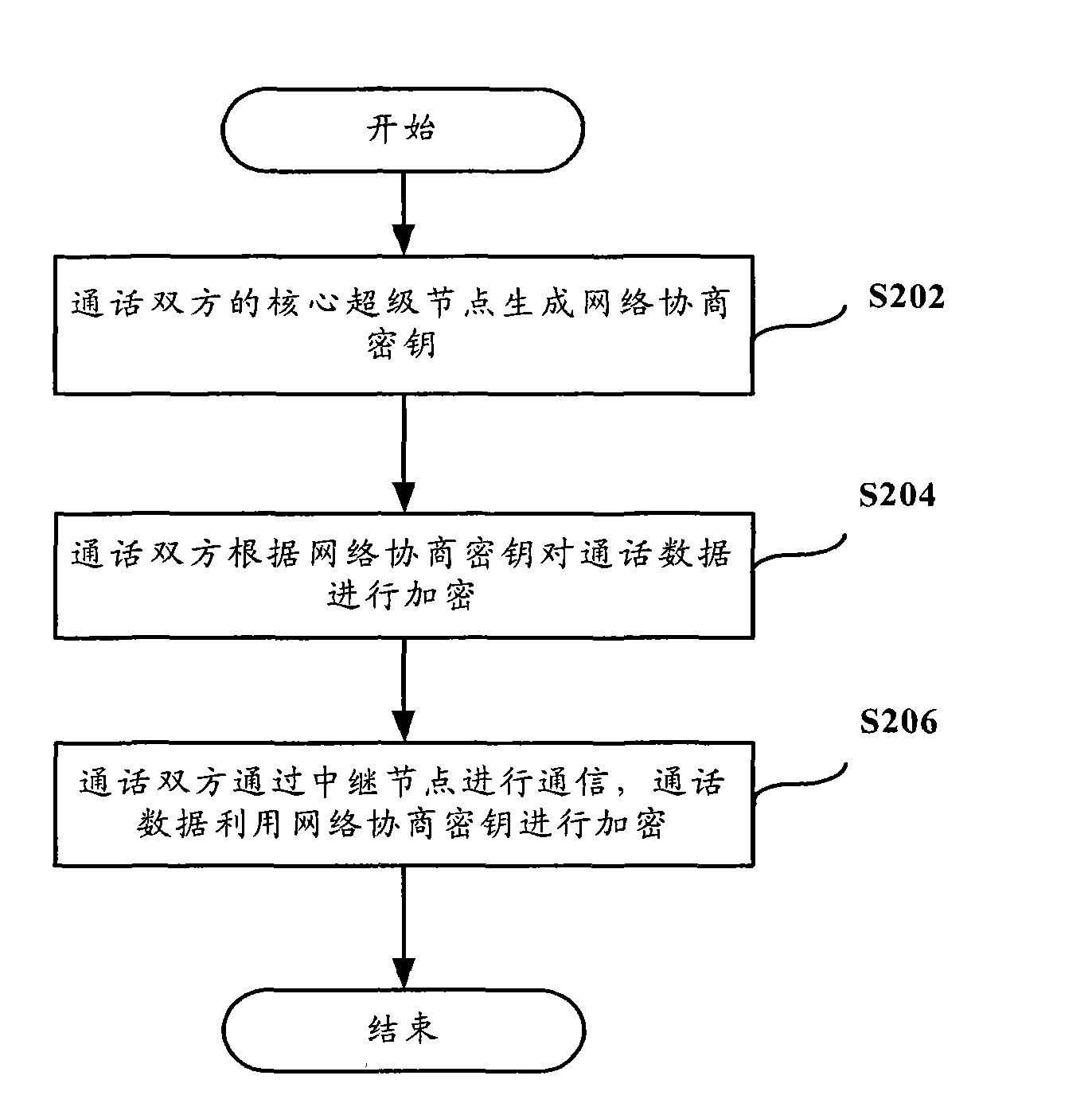
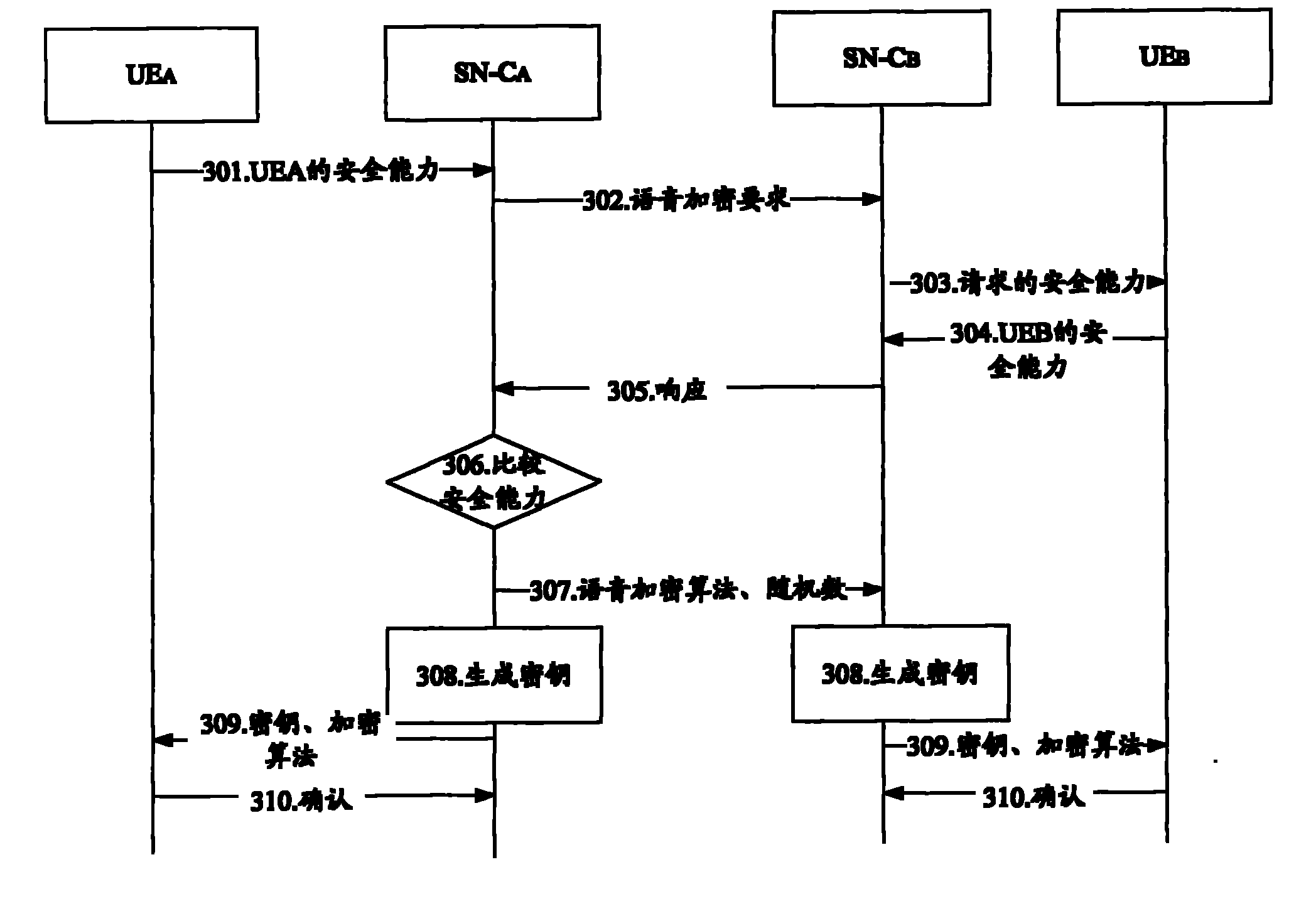
[0024] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
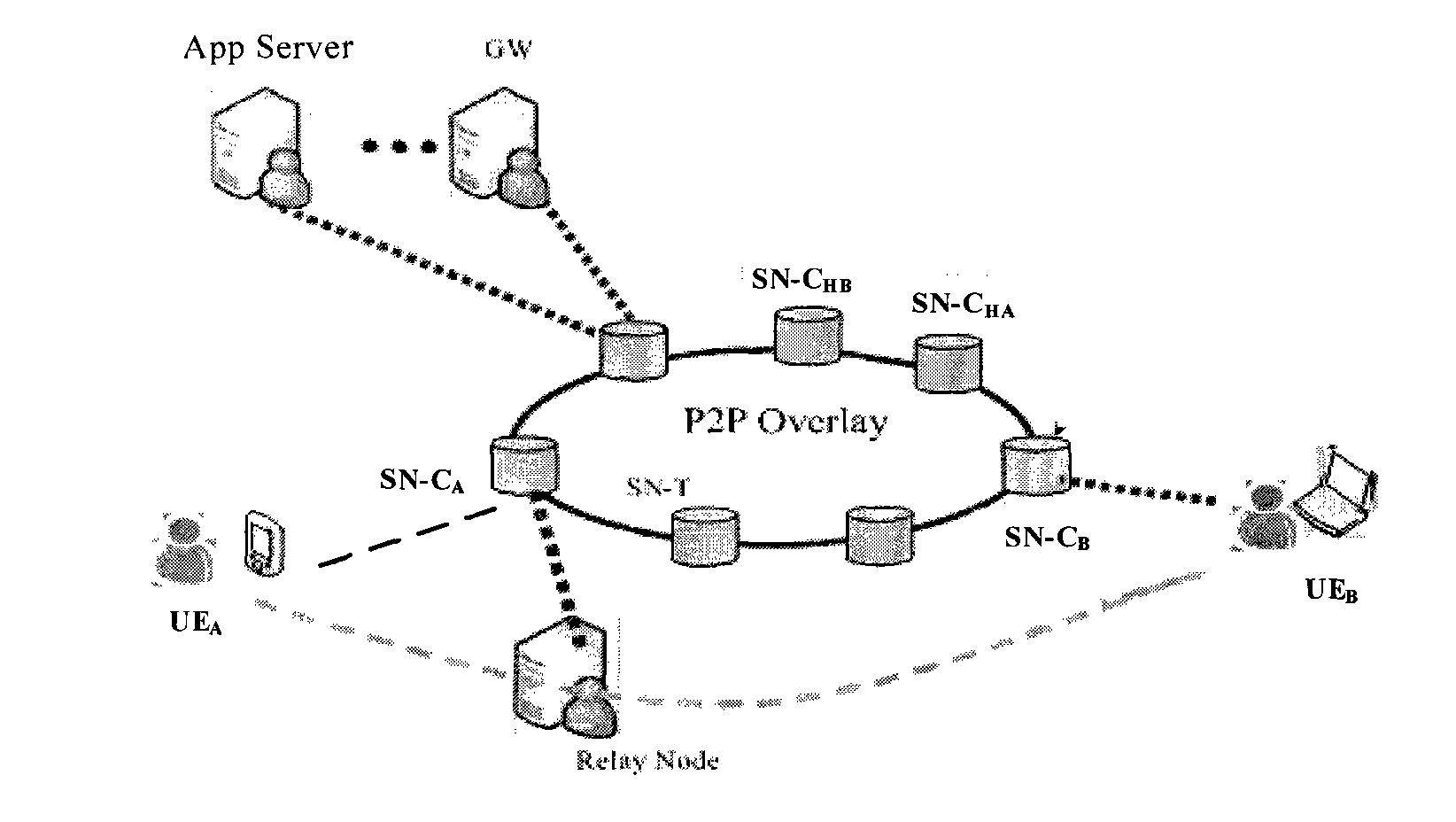
[0025] figure 1 It is a schematic diagram of an embodiment of a DSN network application scenario for VoIP voice encryption protection according to the present invention. Such as figure 1 shown, where SN-C A 、SN-C B ,...,SN-C HA 、SN-C HB They are all core super nodes (Super Node Core, referred to as SN-C). As a terminal node connected to the core network composed of SN-C, UE periodically reports its own status information to the super node (SN) to realize resource sharing between terminal nodes; some terminals can also implement Network Address Translation (Network Address Translation, referred to as NAT) server function, selected by SN-C to provide traversal s...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap