Method for identifying security classification of electronic file
An electronic file, classified technology, applied in electrical components, digital data protection, transmission systems, etc., can solve the problem that electronic files are easily tampered with illegally, the management of classified files cannot be guaranteed, the content of classified files and the integrity of classified parts cannot be guaranteed, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Hereinafter, the present invention will be described in detail through a specific embodiment in conjunction with the accompanying drawings.
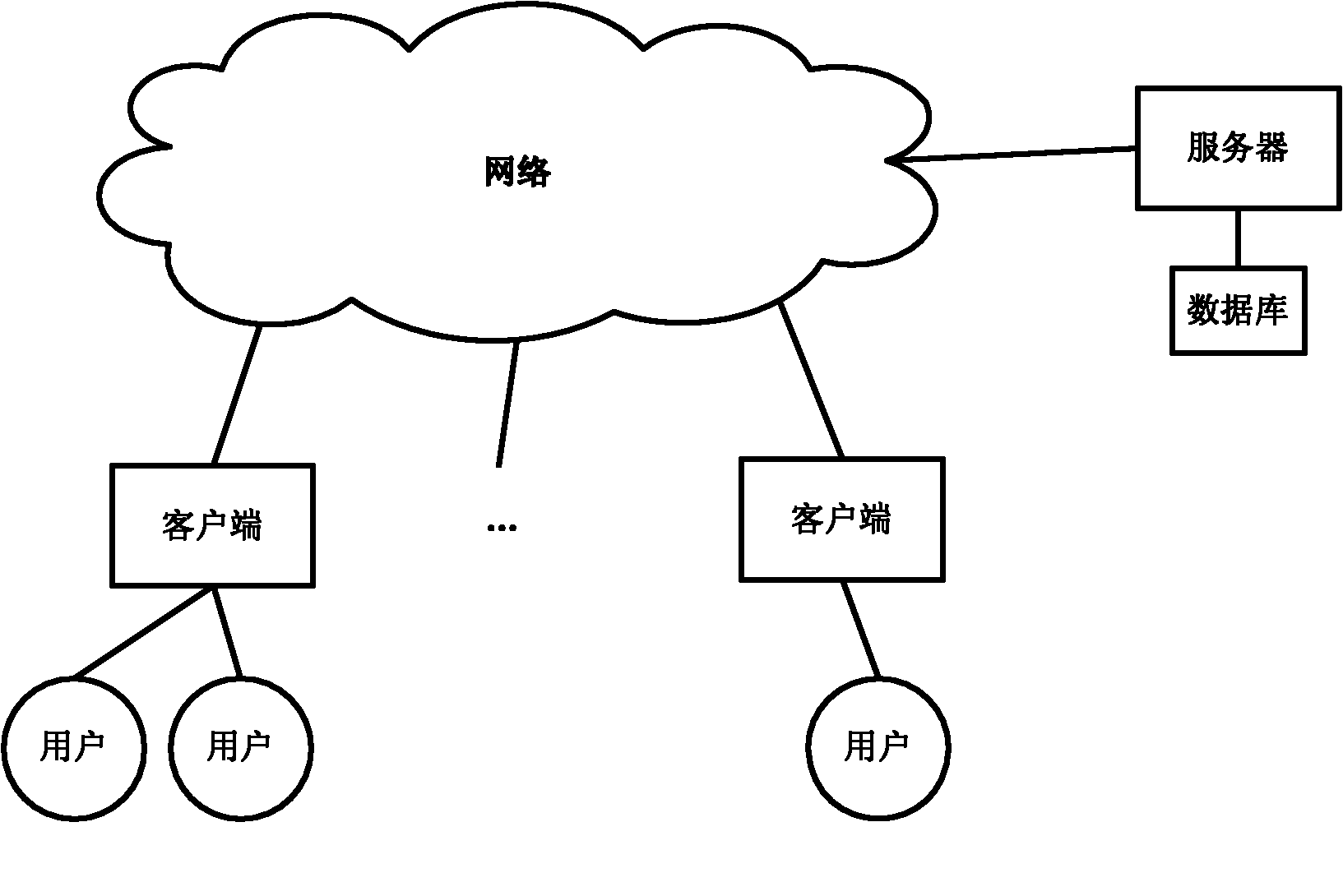
[0027] In this embodiment, the present invention is described in detail by taking the electronic document management system based on the confidentiality identification method of the present invention used by a certain unit as an example. Such as image 3 As shown, the system includes a server (the server is equipped with a secret level management center (software) and a database), and multiple clients for users to use.
[0028] Each part of the above-mentioned system is described below.
[0029] A server
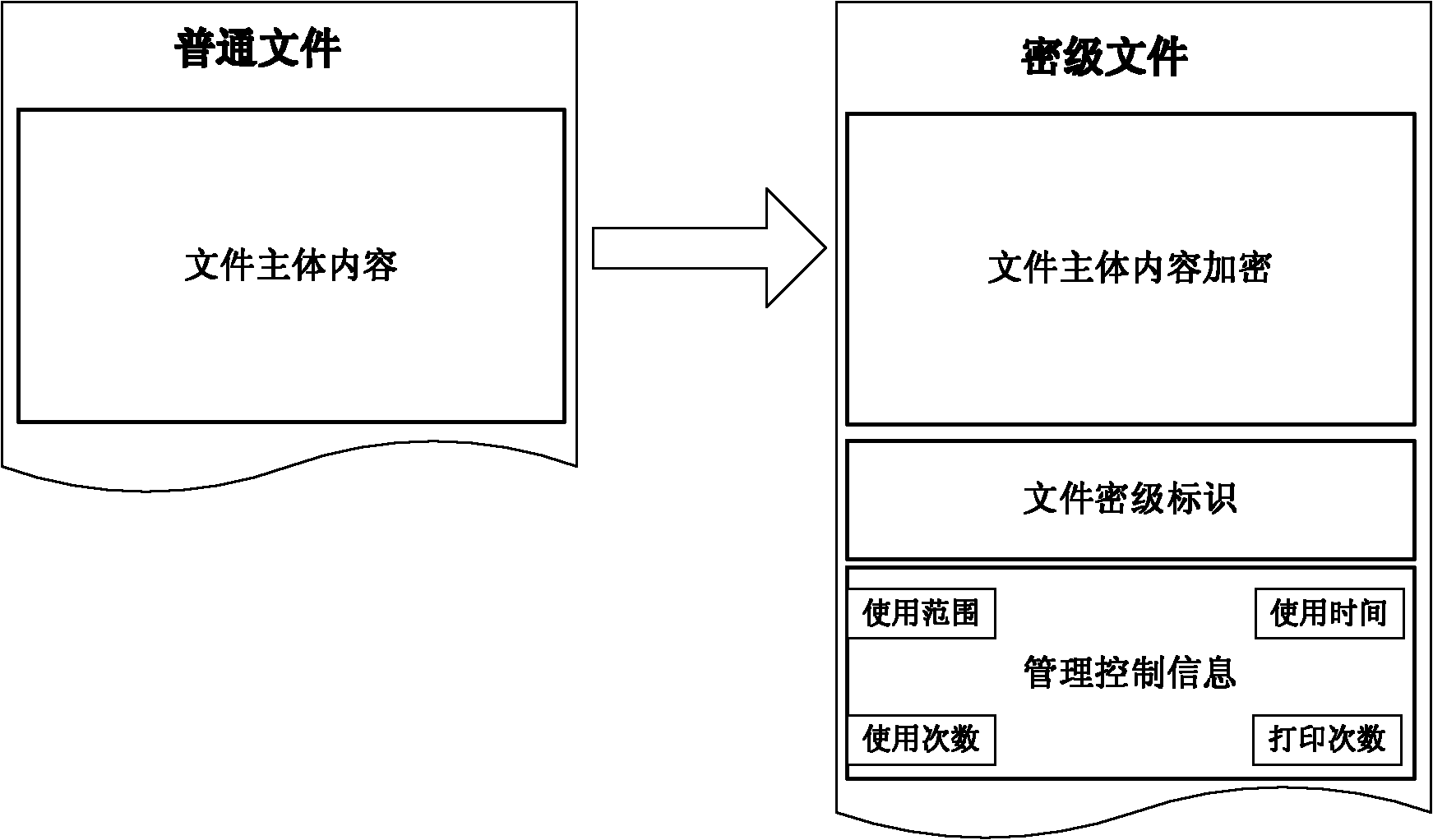
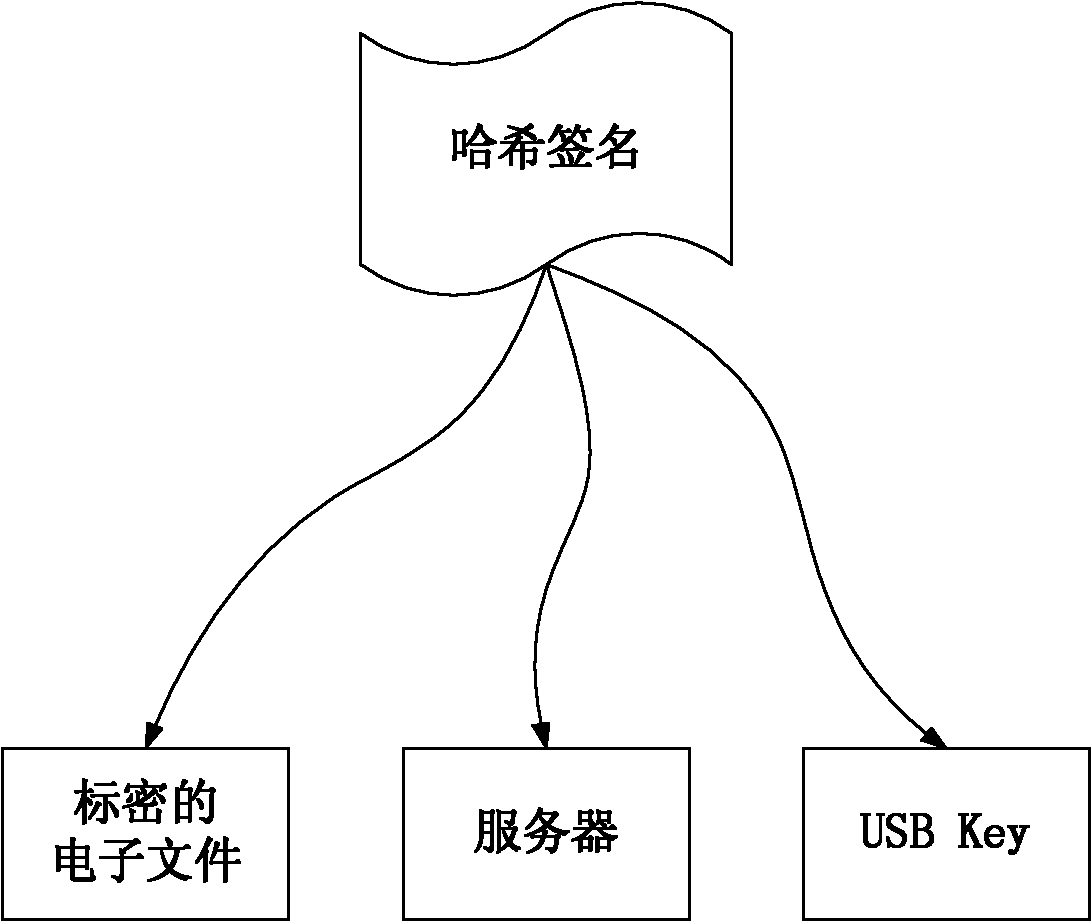
[0030] The server is used to store the corresponding terminal user information of the client, the unique identifier of the classified file, the management and control information of the classified file, and the hash value of the classified file. The server includes a database module, a registration module and an approval mana...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com