A cloud environment distributed hash chain architecture and cloud data integrity verification method
A distributed hash and integrity verification technology, applied in the field of cloud computing and information security, can solve problems such as increasing the threat of data leakage to third parties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Embodiments of the invention are described in detail below, examples of which are illustrated in the accompanying drawings. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
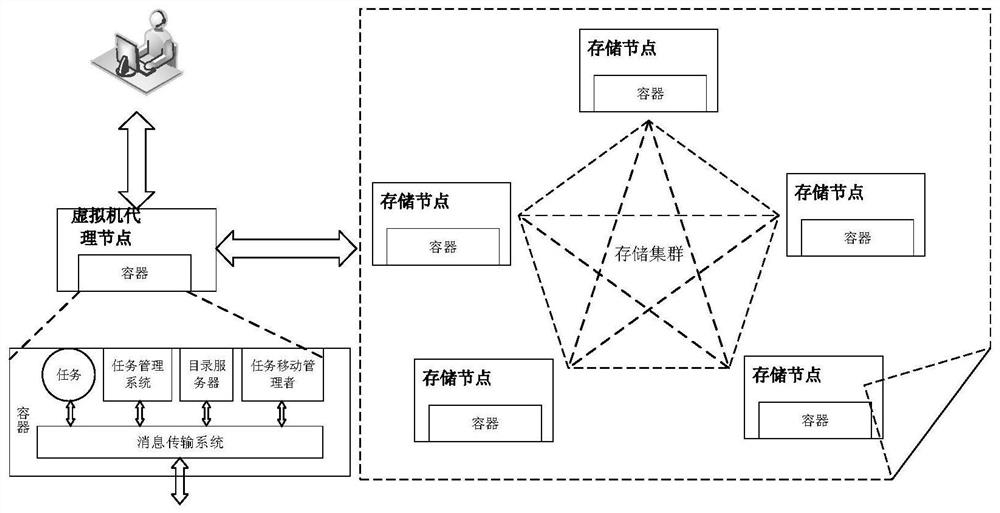
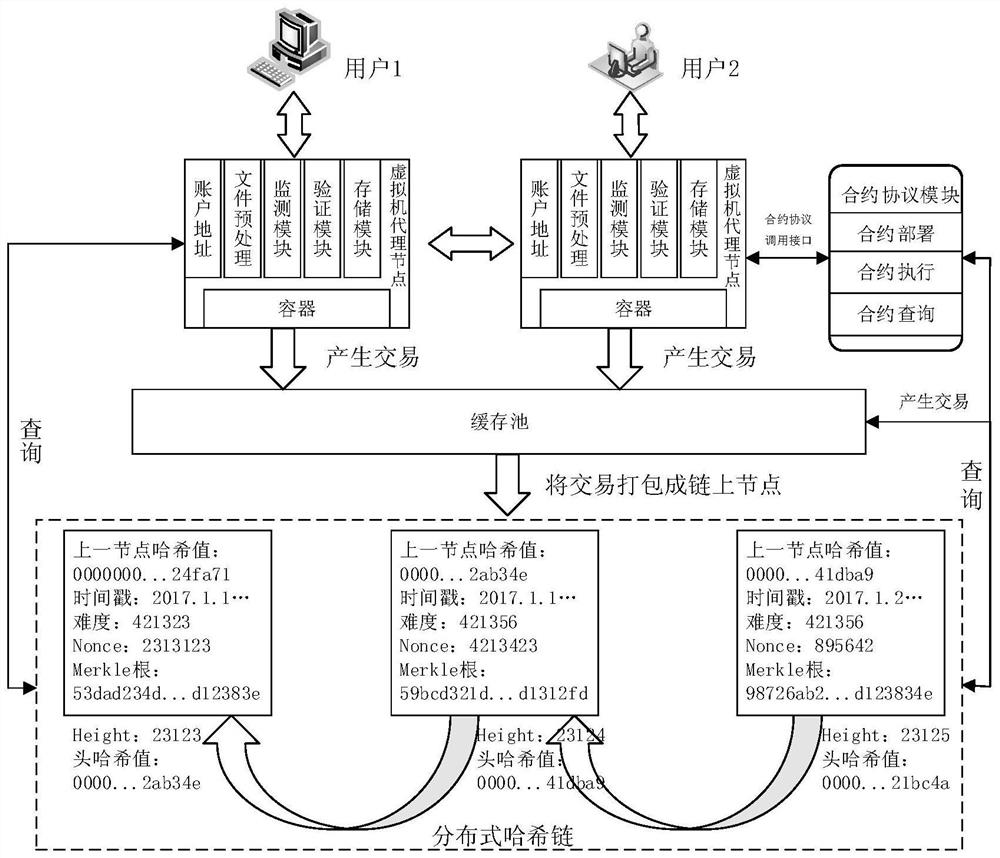
[0051] The present invention designs a cloud environment distributed hash chain architecture. The nodes involved are functionally divided into two categories: virtual machine proxy nodes and storage nodes. When a user submits a storage task, the virtual machine proxy node is responsible for file Perform preprocessing, select the appropriate storage node to save the data, and after all the storage is completed, the virtual machine agent node will return the result to the user.
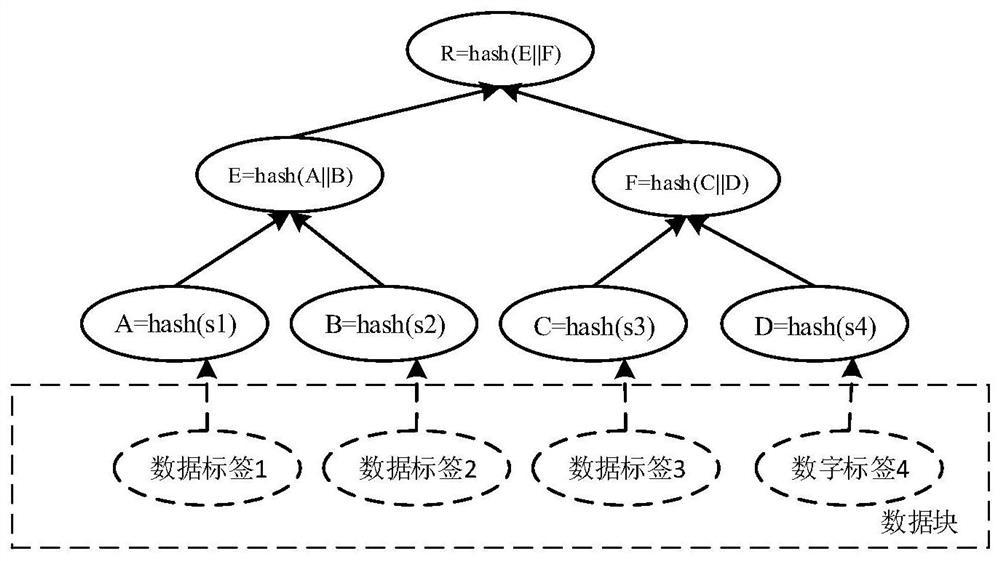
[0052] In order to apply to complex services in the cloud distributed environment and enhance the portability of the model, the present invention first runs a special container on the node to prep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com