Control system, security check method and embedded system
A technology for embedded systems and control systems, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as scalability limitations of embedded systems, and achieve the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] In order to make the above and other objects, features and advantages of the present invention more comprehensible, preferred embodiments are exemplified below and described in detail with accompanying drawings.
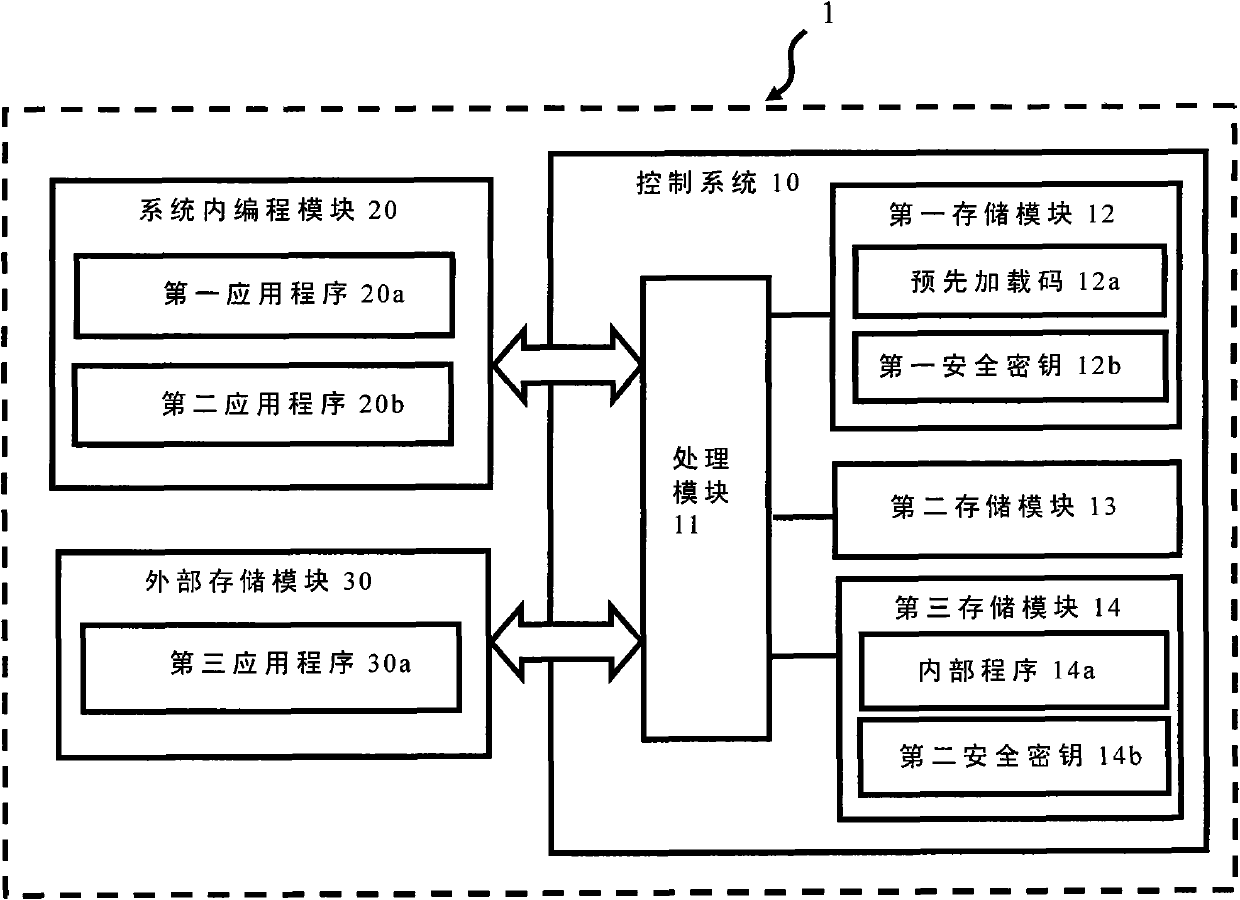
[0018] Please refer to figure 1 , figure 1 It is a structural diagram of the embedded system of the present invention.
[0019] The embedded system 1 of the present invention includes a control system 10 , an In System Programming (ISP) module 20 and an external storage module 30 , which are electrically connected to each other. The control system 10 is structured using a System On Chip (SOC), a Multi-chip Package (MCP) or a System In Package (SIP), but the present invention does not This is not the limit. The control system 10 includes a processing module 11 , a first storage module 12 , a second storage module 13 and a third storage module 14 , which are electrically connected to each other. If the control system 10 is a SoC, the processing module 11 , t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com