Authentication method, authentication system and relevant device
An authentication and equipment technology, applied in the field of communication, can solve the problem of not really reaching the security level of 128bit key length, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
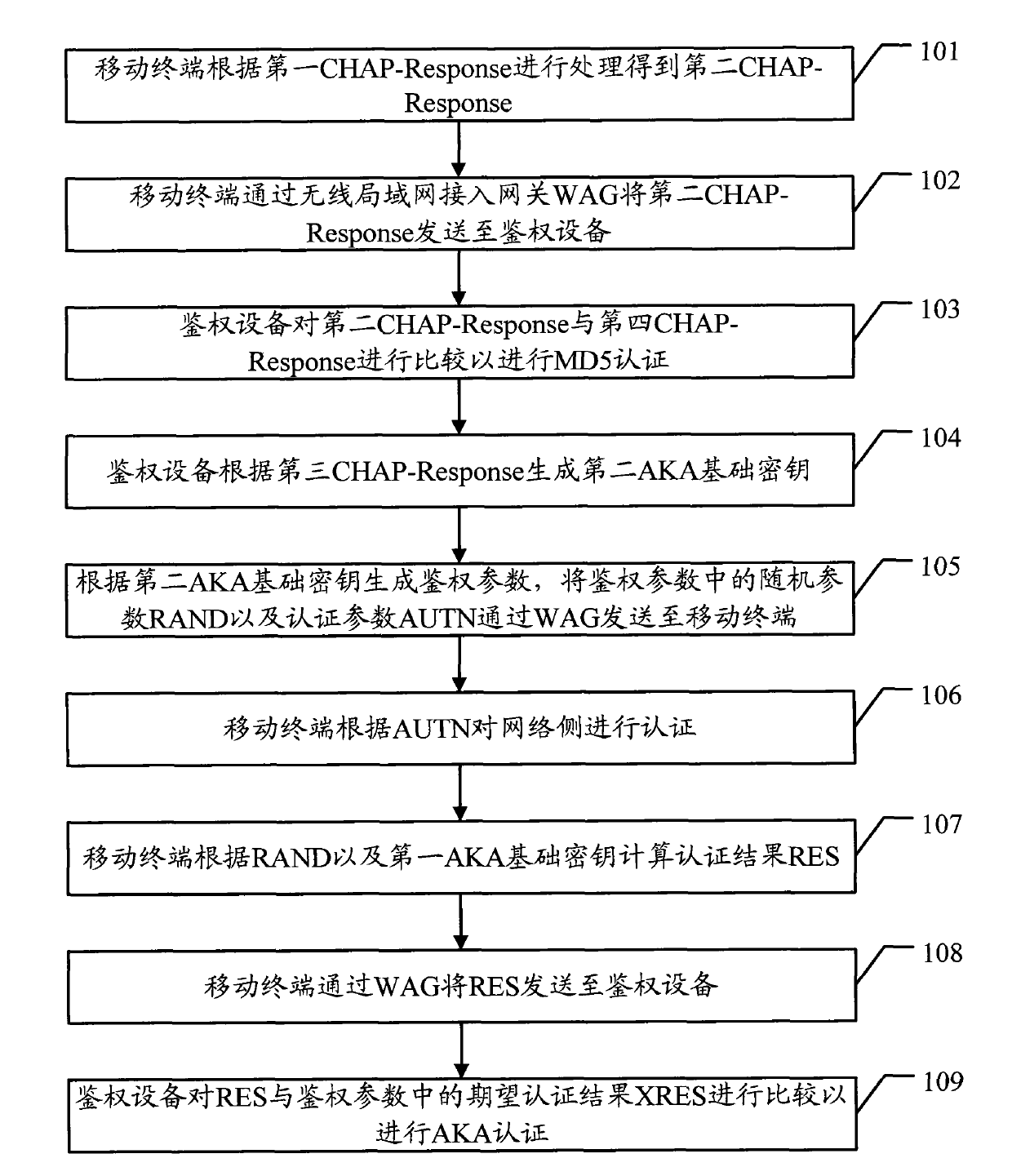
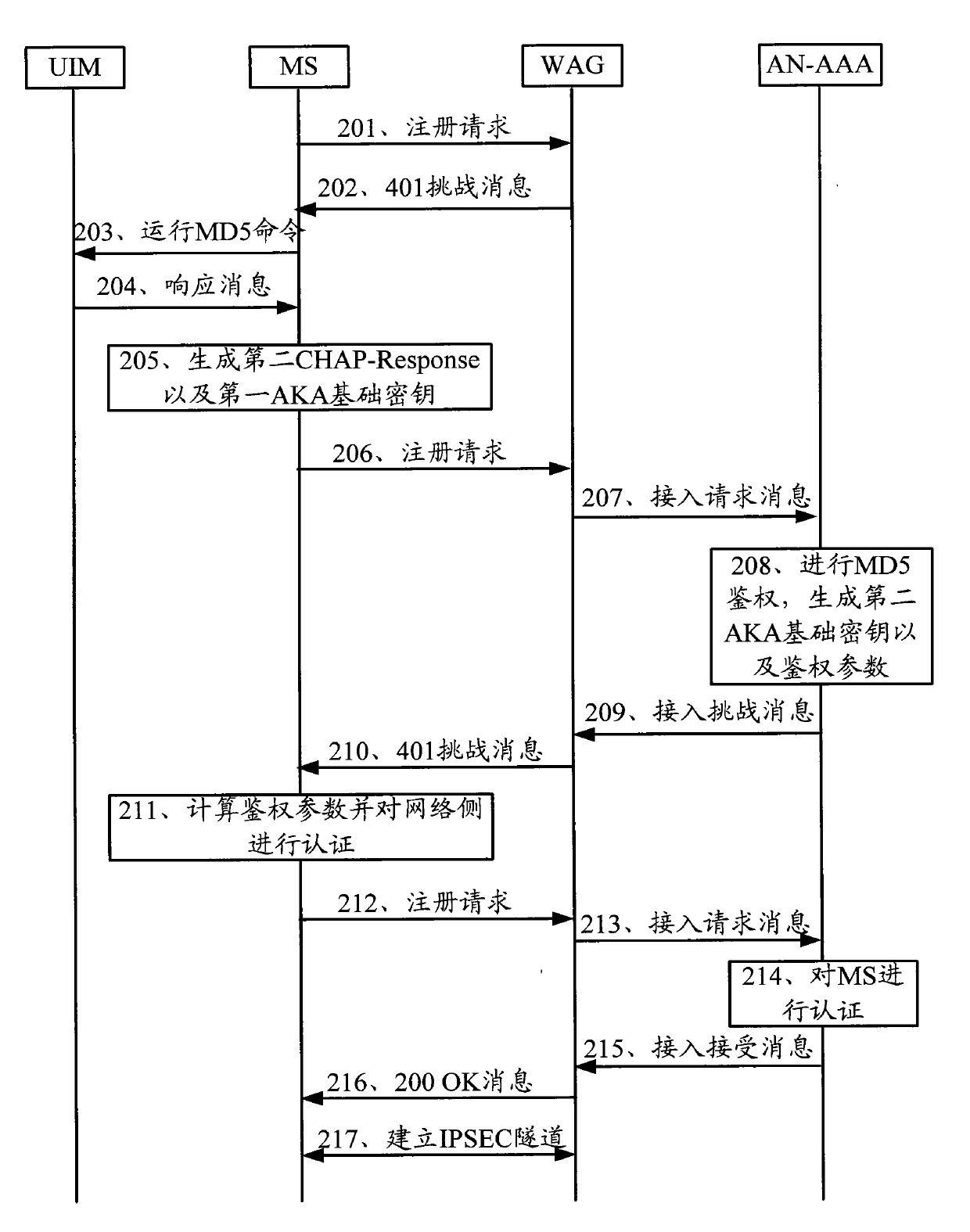
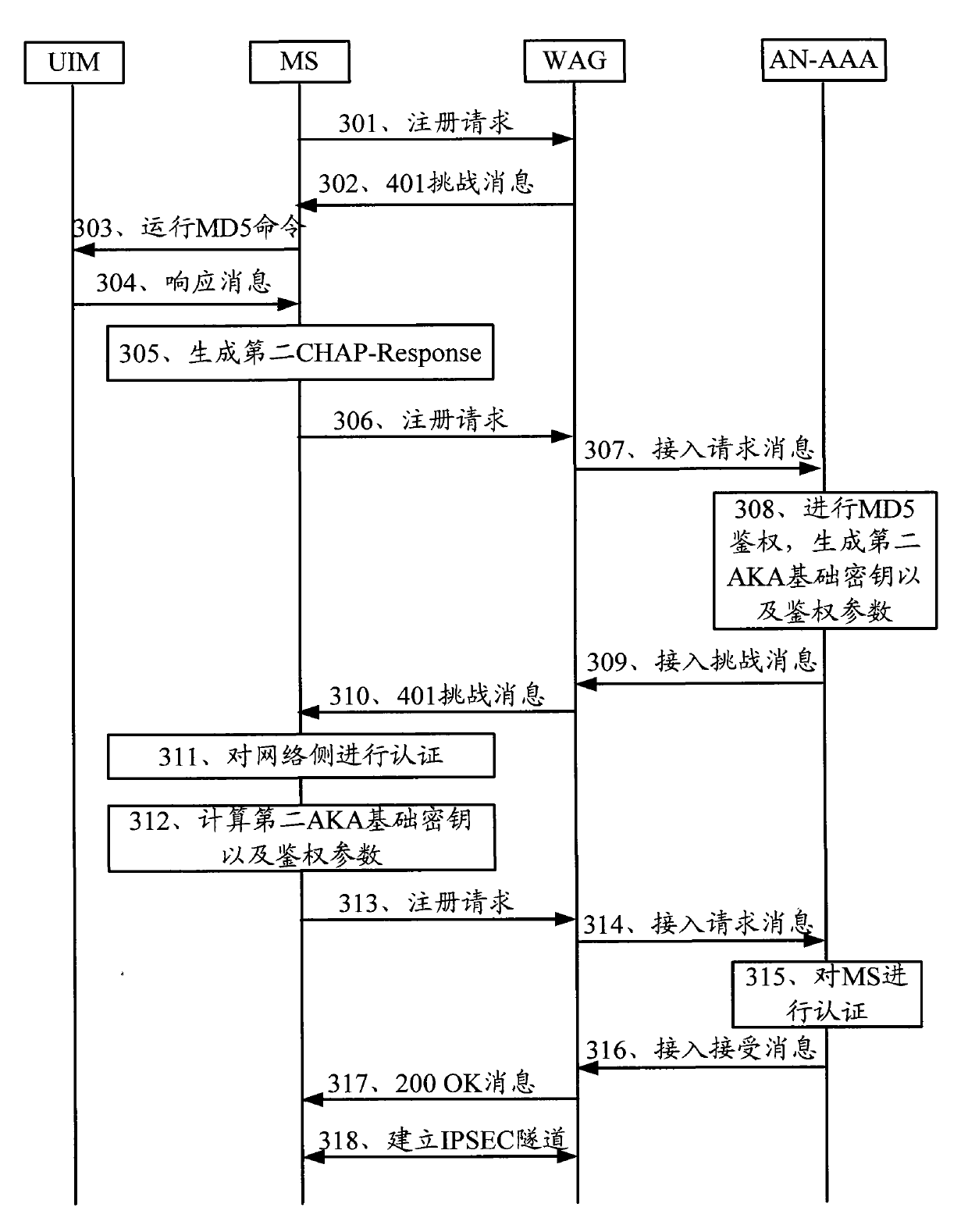
[0040] The embodiment of the present invention provides an authentication method, an authentication system and related equipment, which are used to improve the security of the MD5-based AKA authentication process.
[0041] see figure 1 , an embodiment of the authentication method in the embodiment of the present invention includes:
[0042] 101. The mobile terminal processes according to the first CHAP-Response to obtain a second CHAP-Response;
[0043] In this embodiment, when performing the MD5-based AKA authentication process, the mobile terminal can obtain the first CHAP-Response from the UIM, and the mobile terminal can process the first CHAP-Response to obtain the second CHAP-Response, The specific processing process will be described in detail in the subsequent embodiments.
[0044] It should be noted that the UIM can generate the first CHAP-Response by running the MD5 algorithm.
[0045] 102. The mobile terminal sends the second CHAP-Response to the authentication d...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap