Protection method and device for point-to-multipoint pseudowires (P2MP PW)
A pseudowire and multi-point technology, applied in the field of communication, to achieve the effect of improving stability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
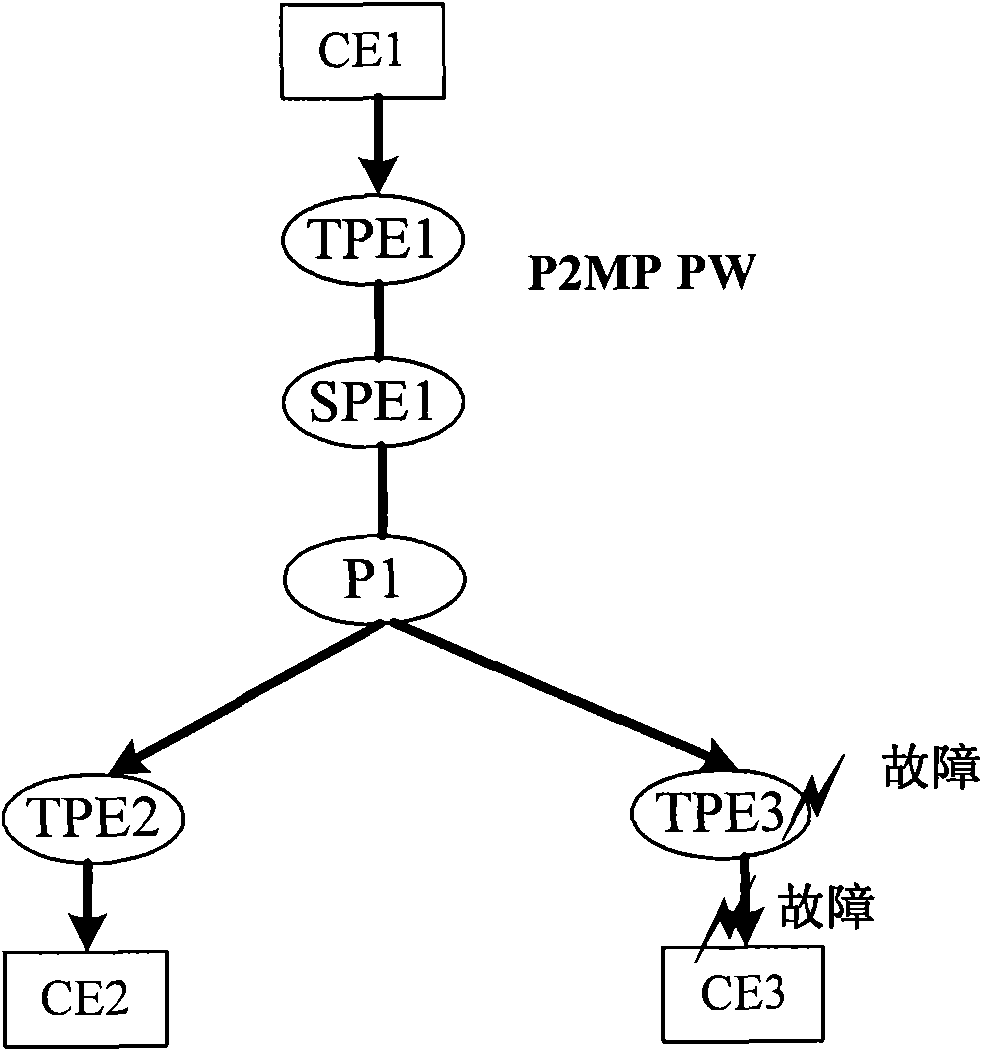
[0118] In this example, the protection of a single-segment P2MP PW is involved. For a single-segment P2MP PW, the ingress PE node is the switching node and also the upstream PE node of the egress PE.
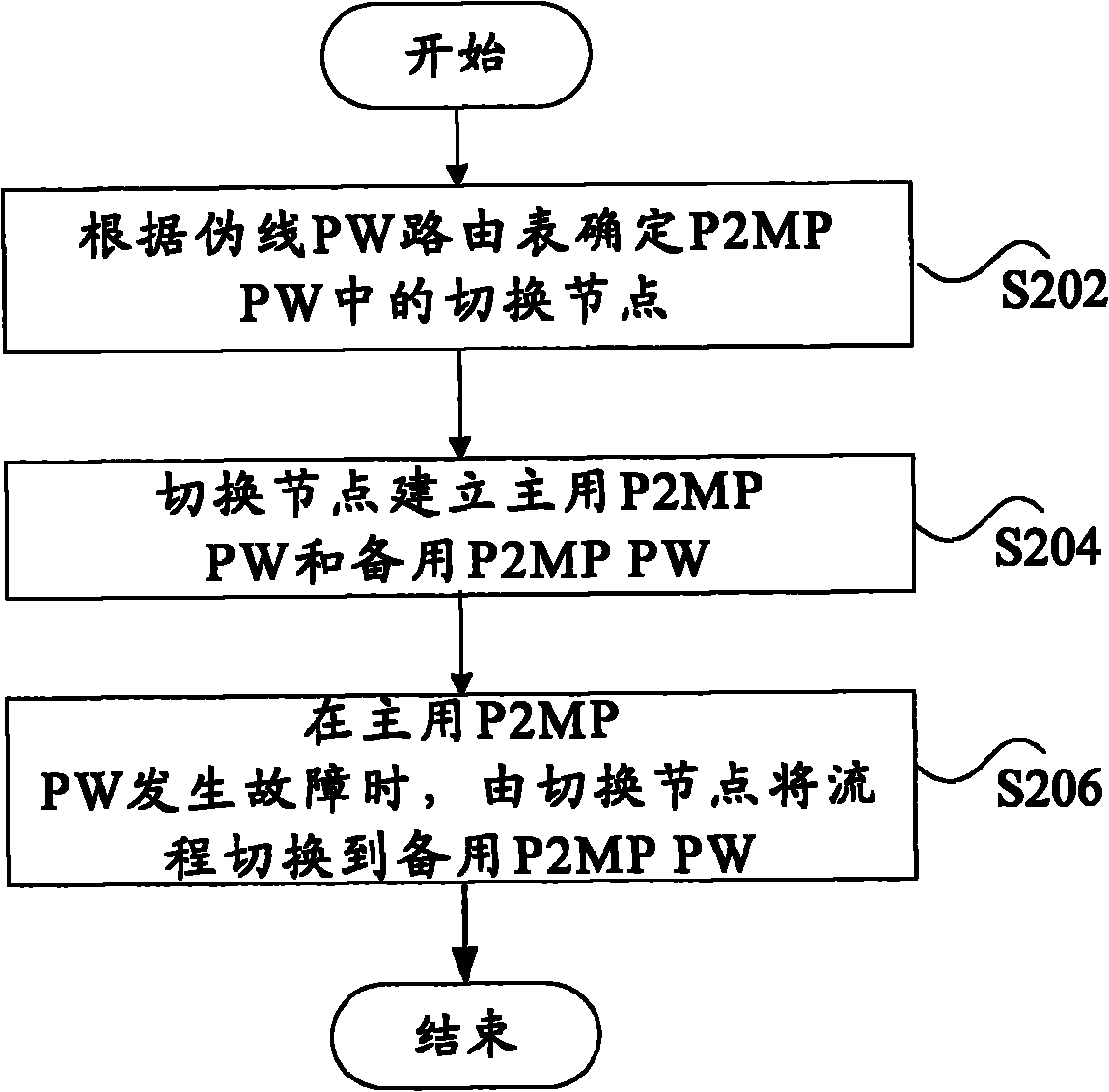
[0119] Figure 11 It is a flow chart of the implementation method of the egress PE protection of P2MP SS-PW in Example 1 according to the embodiment of the present invention, such as Figure 11 As shown, the method includes the following steps S1101 to S1108:
[0120] Step S1101, the egress node configures AII and Priority.
[0121] The NLRI field in the MP_REACH_NLRI and MP_UNREACH_NLRI attributes in BGP UPDATE messages needs to be extended to carry a two-bit priority. Among them, 00 has the highest priority, and the following are 01, 10, and 11 in sequence; see Table 1 for the extension of the NLRI field.
[0122] Dual-homing egress nodes are configured with the same AII but different priorities.
[0123] for Figure 5 In the shown P2MP SS-PW protection network, PE1 is con...
example 2
[0143] This example involves the protection of multi-segment P2MP MS-PW. The upstream node of the egress PE is the switching node. Figure 7 It is a schematic diagram of P2MP MS-PW egress PE protection in Example 2 according to the embodiment of the present invention.
[0144] Figure 12 It is a flow chart of the implementation method of the egress PE protection of the P2MP MS-PW in Example 2 according to the embodiment of the present invention, such as Figure 12 As shown, the method includes the following steps S1201 to S1209:
[0145] Step S1201, the egress node configures AII and Priority.
[0146] It is necessary to expand the NLRI fields in the MP_REACH_NLRI and MP_UNREACH_NLRI attributes in BGP UPDATE messages to carry two bits of priority. Among them, 00 has the highest priority, and the following are 01, 10, and 11 in sequence; for the extension of the NLRI field, see Table 1 .
[0147] Dual-homing egress nodes are configured with the same AII but different prioriti...
example 3
[0168] In this example, the protection of multi-segment P2MP MS-PW is involved, and its network structure is shown in Figure 9 , Figure 9 It is a schematic diagram of P2MP MS-PW egress PE protection in Example 3 according to the embodiment of the present invention.
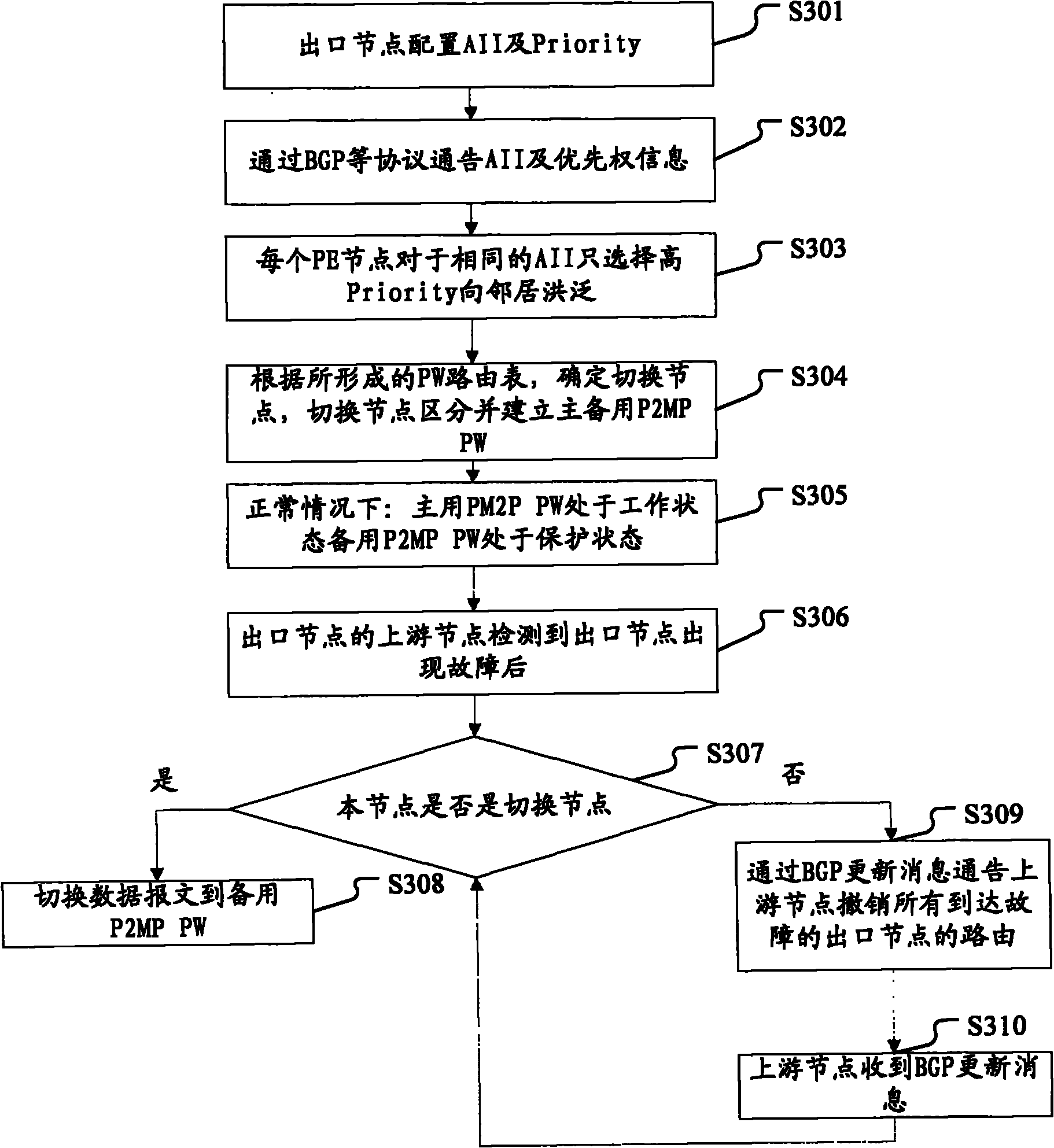
[0169] Figure 13 It is a flow chart of the implementation method of the egress PE protection of the P2MP MS-PW in Example 3 according to the embodiment of the present invention, such as Figure 13 As shown, the method includes the following steps S1301 to S1311:
[0170] In step S1301, the egress node configures AII and Priority.
[0171] The NLRI fields in the MP_REACH_NLRI and MP_UNREACH_NLRI attributes in BGP UPDATE messages need to be extended so that they carry a two-bit priority, 00 has the highest priority, and the following are 01, 10, and 11 in sequence; see Table 1 for the extension of the NLRI field.
[0172] Dual-homing egress nodes are configured with the same AII but different priorities.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com