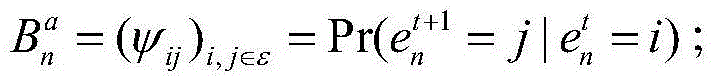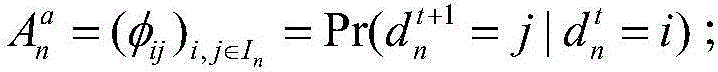Method for realizing layered key management in wireless mobile communication network
A technology of mobile communication network and key management, which is applied in the field of hierarchical key management in wireless mobile communication networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] In order to understand the technical content of the present invention more clearly, the following examples are given in detail.
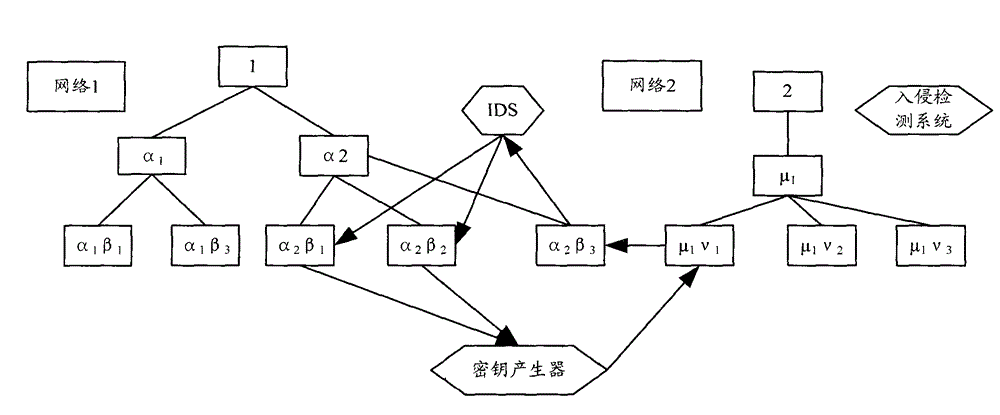
[0061] see figure 1 As shown, the method for implementing hierarchical key management in the wireless mobile communication network includes the following steps:
[0062] (1) Establish a corresponding system model according to the state of each node in the wireless mobile communication network, including the following steps:
[0063] (a) Establish the security state model of each node in the wireless mobile communication network, specifically:
[0064] Construct the I corresponding to each node according to the following formula n A Markov chain of one-step transition probability matrices for states:
[0065] A n a = ( φ ij ) i , j ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com