Method and device for adding, searching for and deleting key in hash table
A hash table and hash sub-table technology, which is applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems that z2 and y1 cannot be guaranteed to be non-conflicting, and can not be guaranteed, so as to improve search performance and search process simplified effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
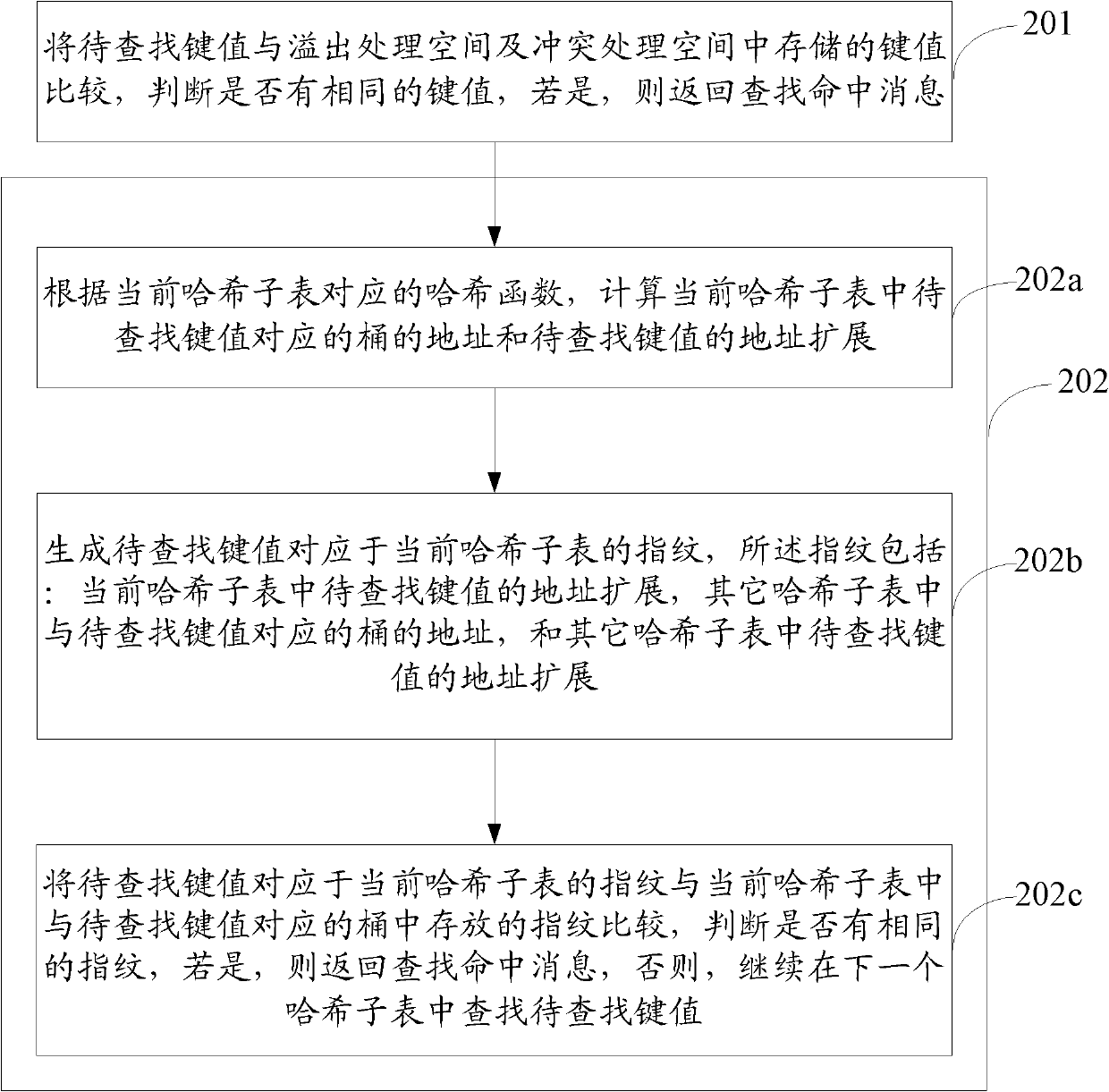
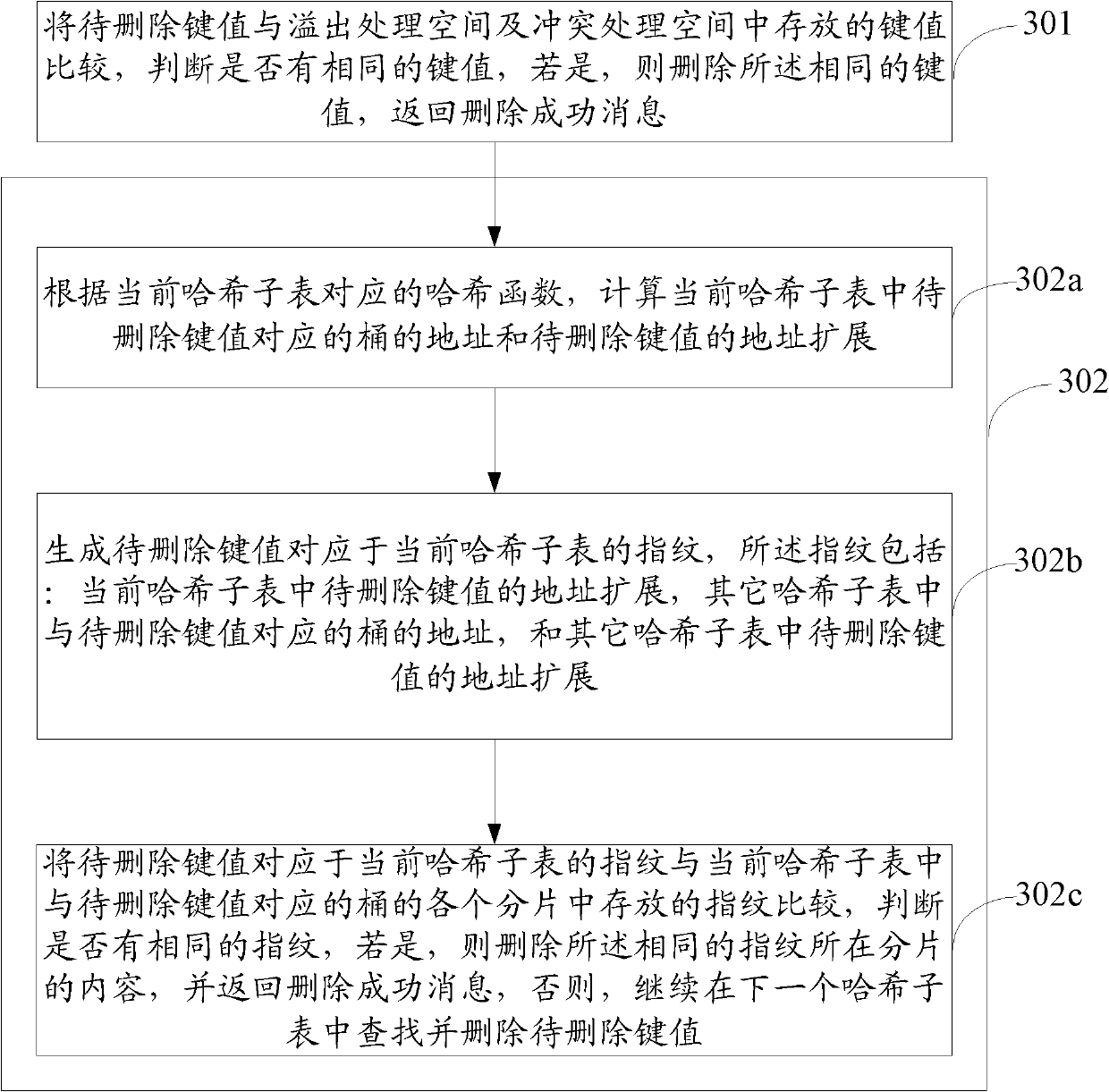
[0047] Embodiments of the present invention provide a method and device for adding, searching or deleting key values in a hash table. A detailed description will be given below in conjunction with the accompanying drawings.
[0048] Please refer to figure 1 , this embodiment provides a method for adding a key value in a hash table.
[0049] Before describing the method of this embodiment, the structure of the hash table in this embodiment will be described first. The hash table of this embodiment consists of the following parts:
[0050] At least two hash subtables are used to store the fingerprint and index corresponding to the key value, which is the address of the key value in the original key value table;
[0051] A conflict processing space is used to store key values that conflict with the stored key values in the hash subtable; an overflow processing space is used to store overflow key values; it should be noted that the conflict processing space and the overfl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com