Method and equipment for obtaining attack message
An attack packet and acquisition method technology, applied in the field of attack packet acquisition, can solve the problems that the distance cannot be guaranteed for the attack packet to pass through the IDS device, the network performance is affected, and the IDS device is expensive.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] As described in the background, the existing attack packet capture technology has problems such as high cost of capture equipment and impact on network performance.
[0057] Based on the above problems, the present invention proposes a method for obtaining attack packets, which accurately and efficiently records the packets that attack the network equipment without affecting the processing performance of the network equipment itself and without reducing the overall performance of the network. .
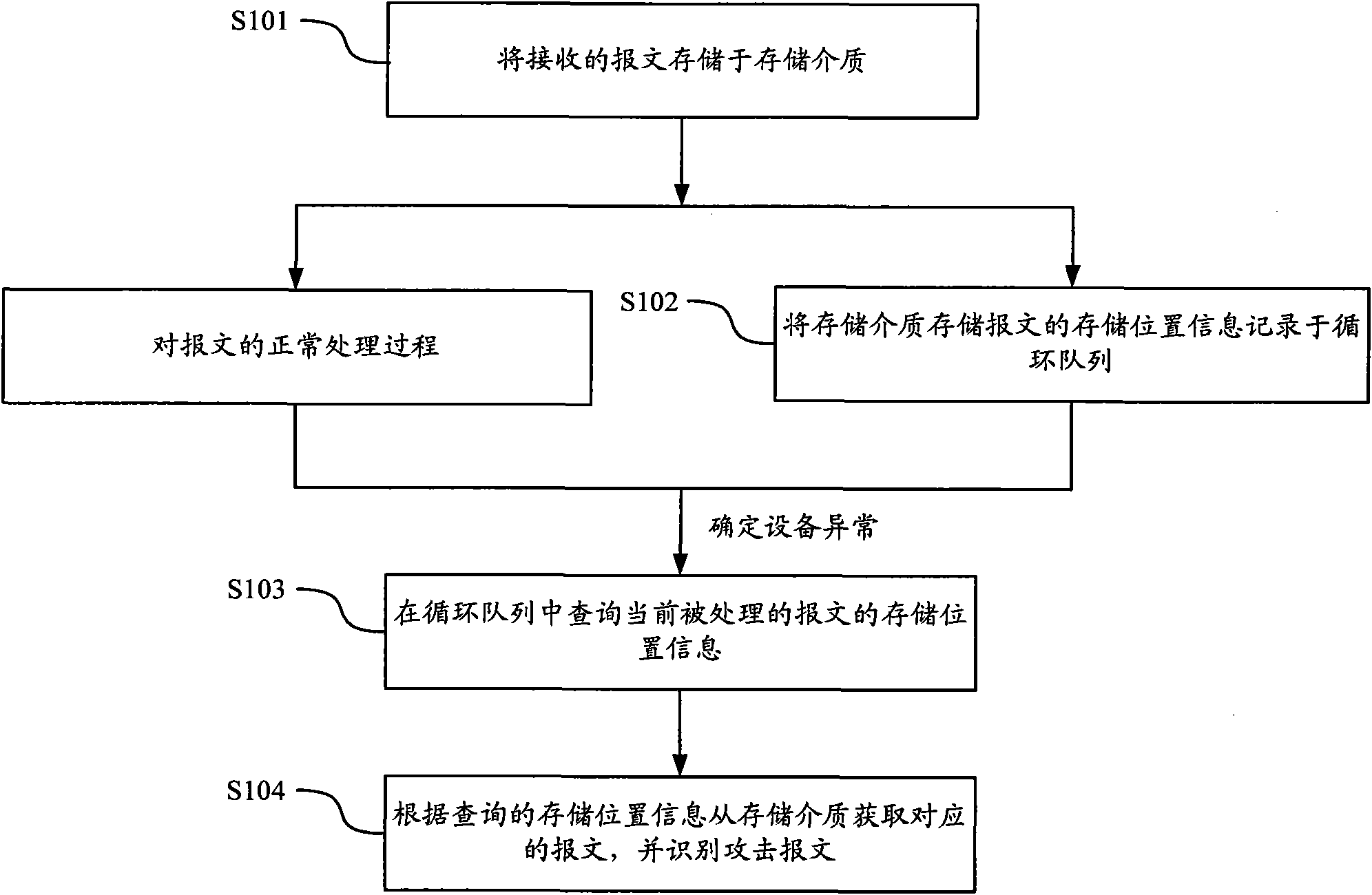
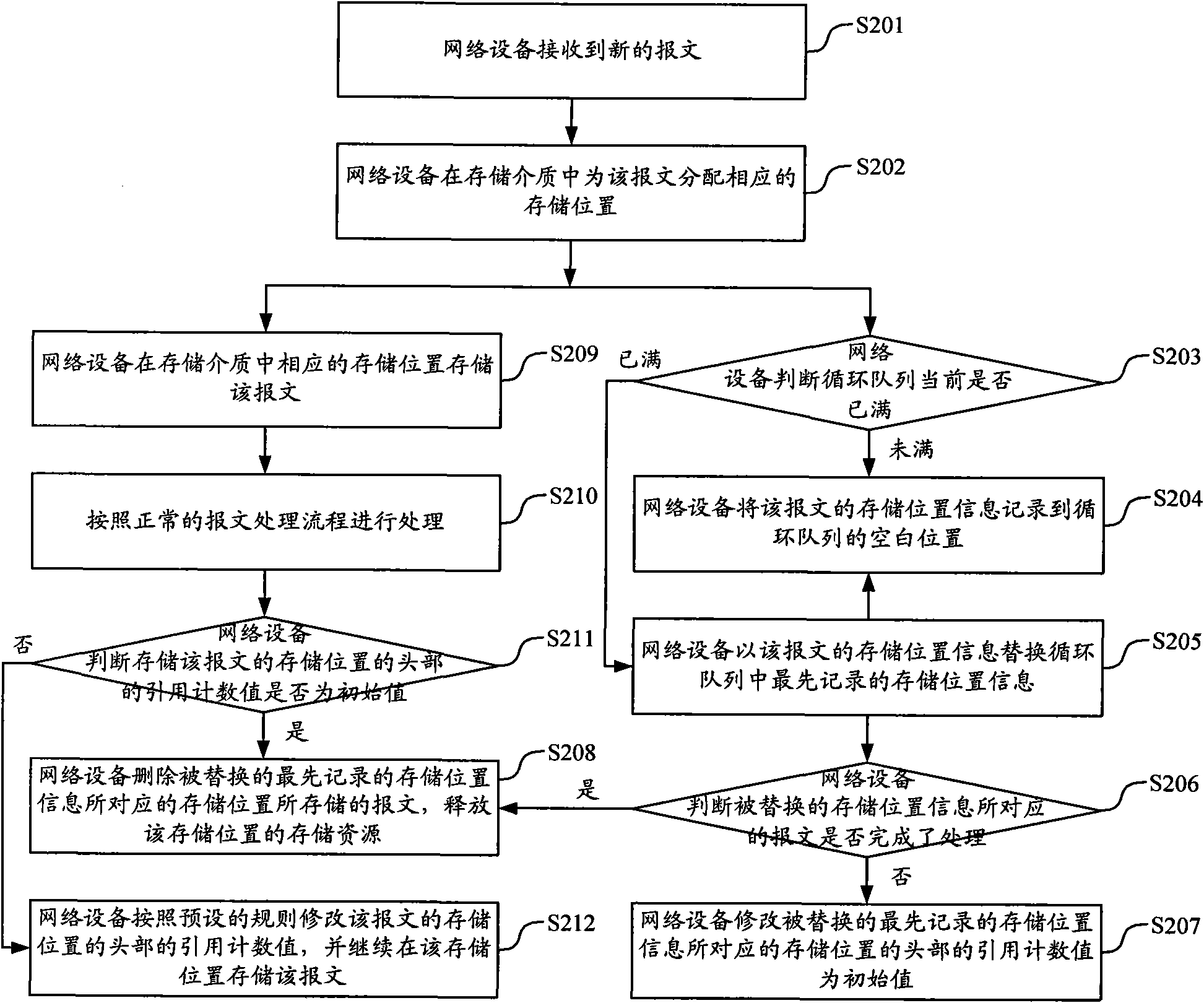
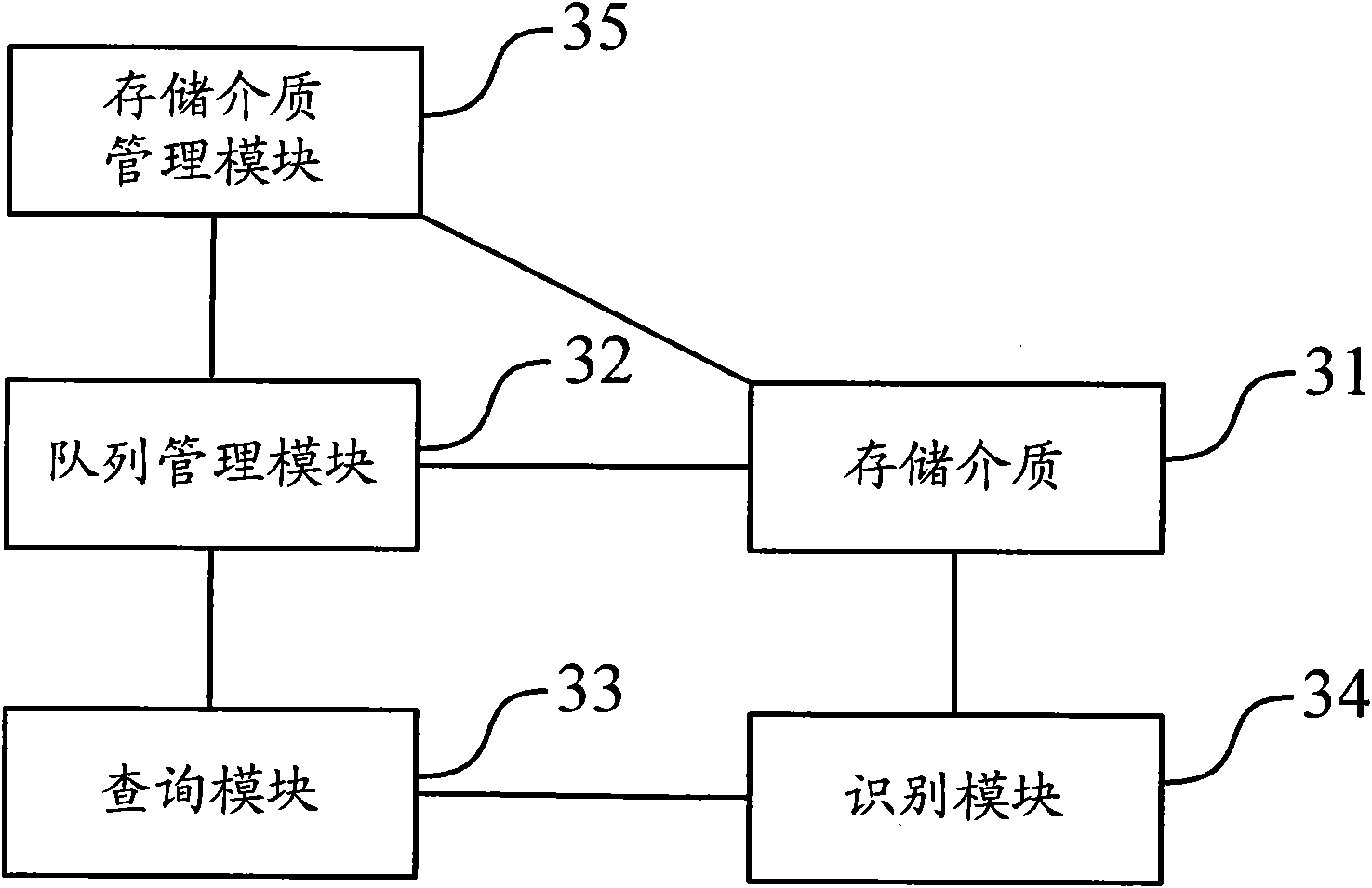
[0058] like figure 1As shown, it is a schematic flow chart of a method for obtaining attack messages proposed by the present invention. The method establishes a circular queue in the network device to record the storage of the recently received preset number of messages in the storage medium. location information, and save the message corresponding to the storage location information recorded in the circular queue in the storage medium, that is, as long as the storage location...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com