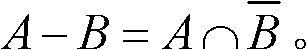Hypergraph-model-based multicast key management method
A technology of multicast key and management method, applied in the field of centralized key management scheme
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] Below in conjunction with example the present invention will be further described.
[0047] (1) Establishment phase
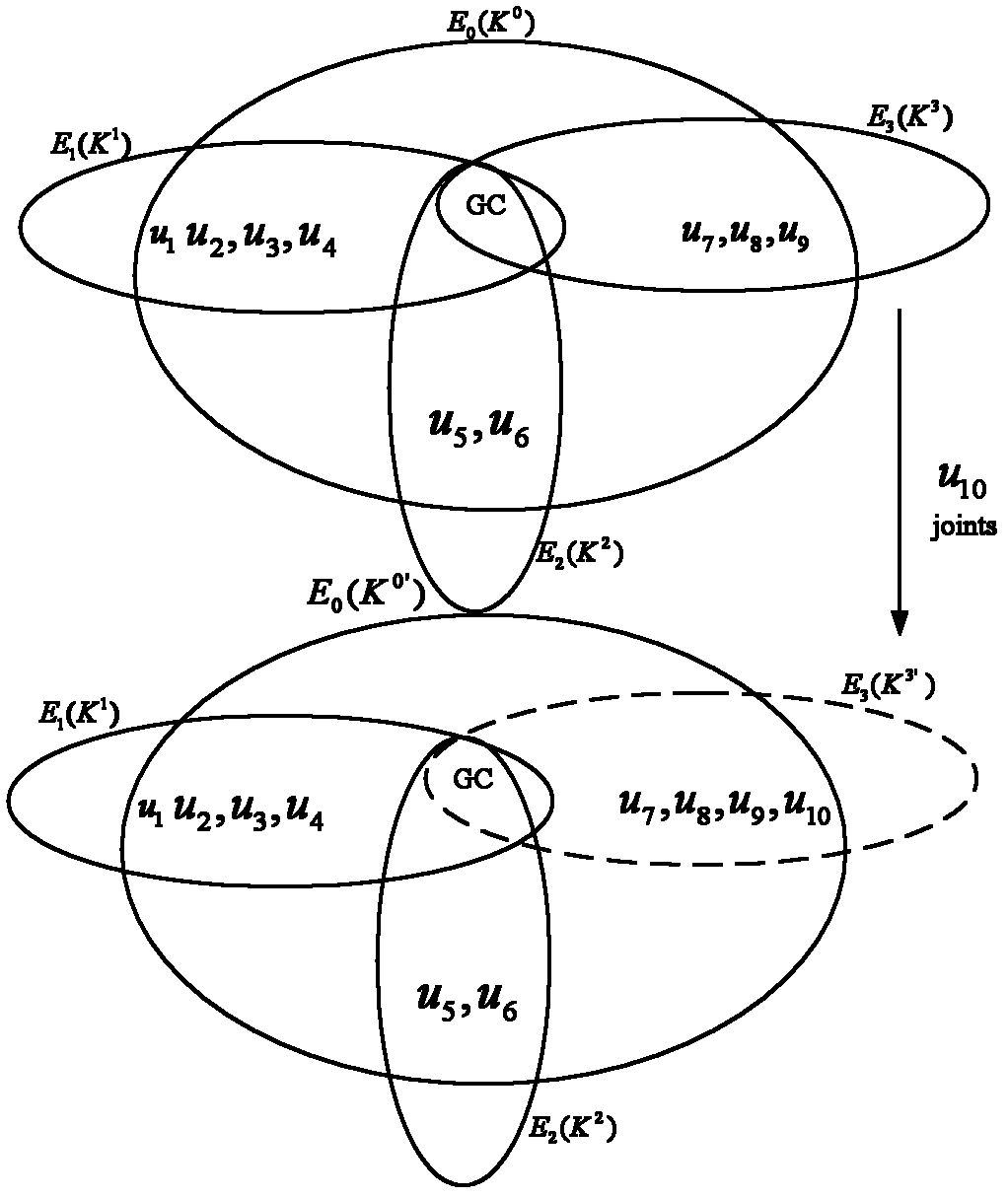
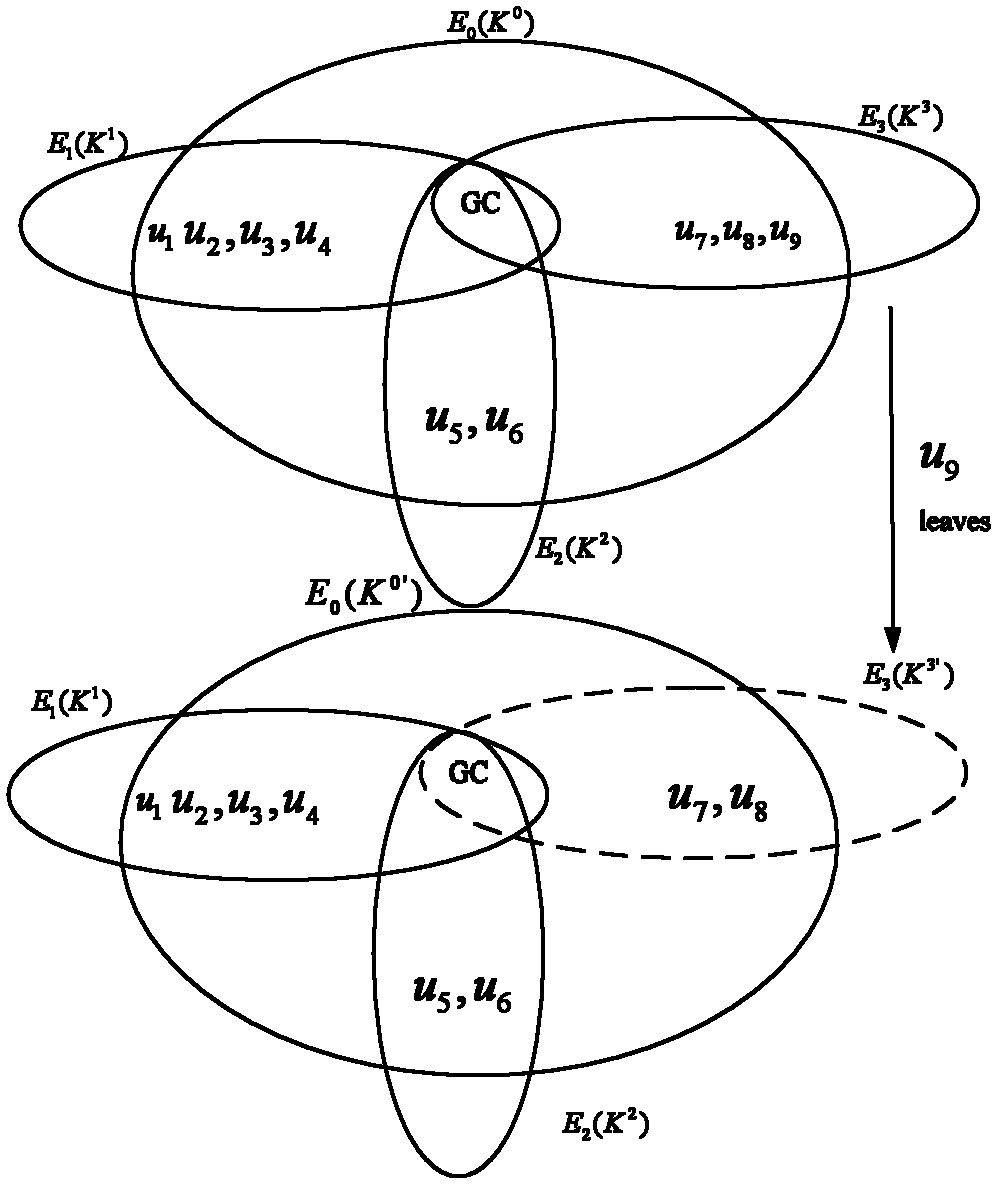
[0048] There is a trusted group control center GC responsible for group access control and key management, and the GC distributes keys for group members and maintains the relationship between member keys. First, the GC builds a key hypergraph. Members of the security group are GC, u 1 , u 2 , u 3 , u 4 , u 5 , u 6 , u 7 , u 8 , u 9 Corresponding to the vertices of the key hypergraph, the hyperedge E 1 (K 1 )={u 1 , u 2 , u 3 , u 4},E 2 (K 2 )={u 5 , u 6},E 3 (K 3 )={u 7 , u 8 , u 9} represents a set of group members, and these members share the subgroup key K 1 , K 2 , K 3 . Given a key hypergraph H, the set of hyperedges (secure subgroups) intersects in pairs at the vertex GC. GC randomly selects a key K 0 , as the master key of the security group, and securely distribute the master key to all members. Group members are au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com