Virtual local area network (VLAN)-based transparent interconnection of lots of links (TRILL) traffic priority scheduling method
A technology of prioritizing scheduling and traffic, applied in the field of communication, can solve the problems of lack of hierarchy of Layer 2 MAC addresses, waste of investment, exhaustion of MAC address space, etc., to achieve the effect of quality of service assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
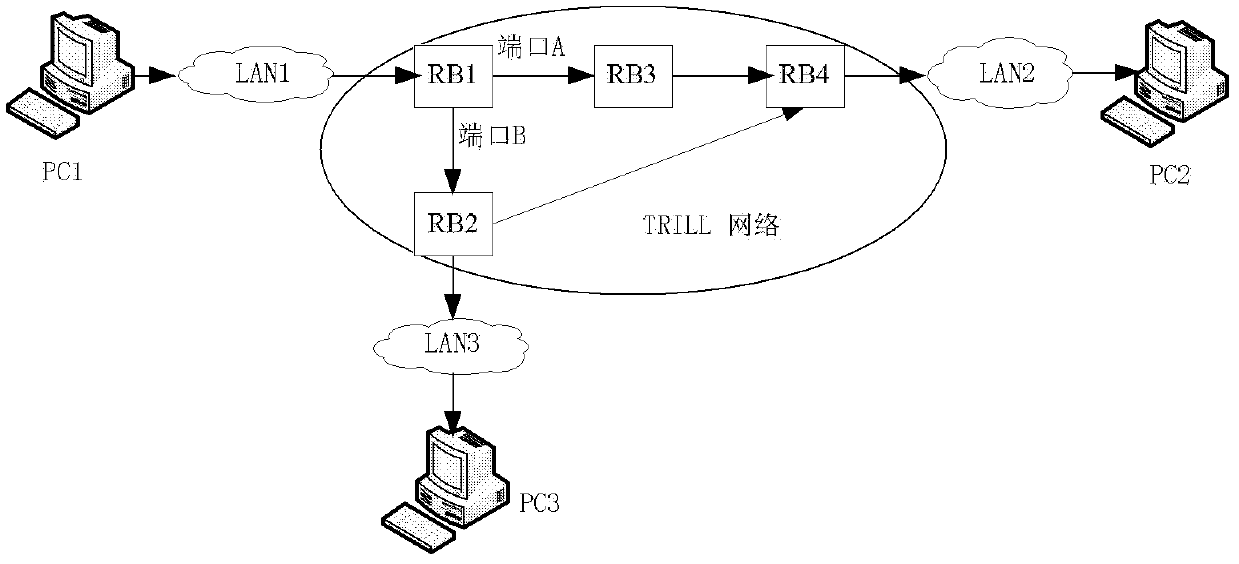
[0022] Such as figure 1 As shown, a schematic diagram of the TRILL network connection structure of four sub-switches is given: each switch uses RB instead, figure 1 PC1, PC2 and PC3 are client devices, PC1 is connected to LAN1, PC2 is connected to LAN2, PC3 is connected to LAN3, edge switch RB1 is TRILL network edge device, intermediate switch RB3 is TRILL network transmission device; the port of RB1 A is connected to the switch RB3, and port B is connected to the edge switch RB2; RB2 and RB3 are connected to the TRILL network edge device RB4, where RB2 can be used as an edge device or as a transmission device.
[0023] Port A and port B on the edge switch RB1 are two paths in the TRILL network. The links connected from port A and port B not only transmit the traffic generated by RB1, but also back up each other at the same time.
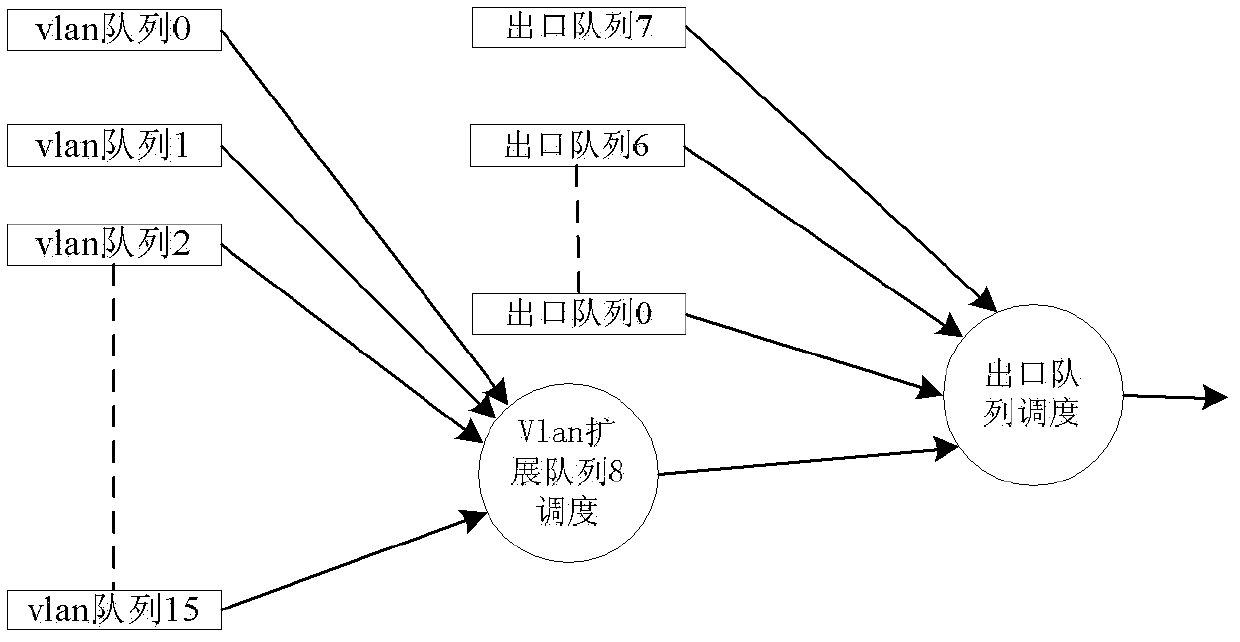
[0024] TRILL traffic data forwarding priority negotiation process between RB1 and RB4 is as follows: figure 2 As shown, RB1 sends a HELLO messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com