Method and device for identifying phishing website
A phishing website and identification method technology, which is applied in the Internet field, can solve the problems of missed website judgment, poor identification flexibility, and low phishing identification accuracy, and achieve the effects of improving robustness, solving poor flexibility, and improving judgment accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
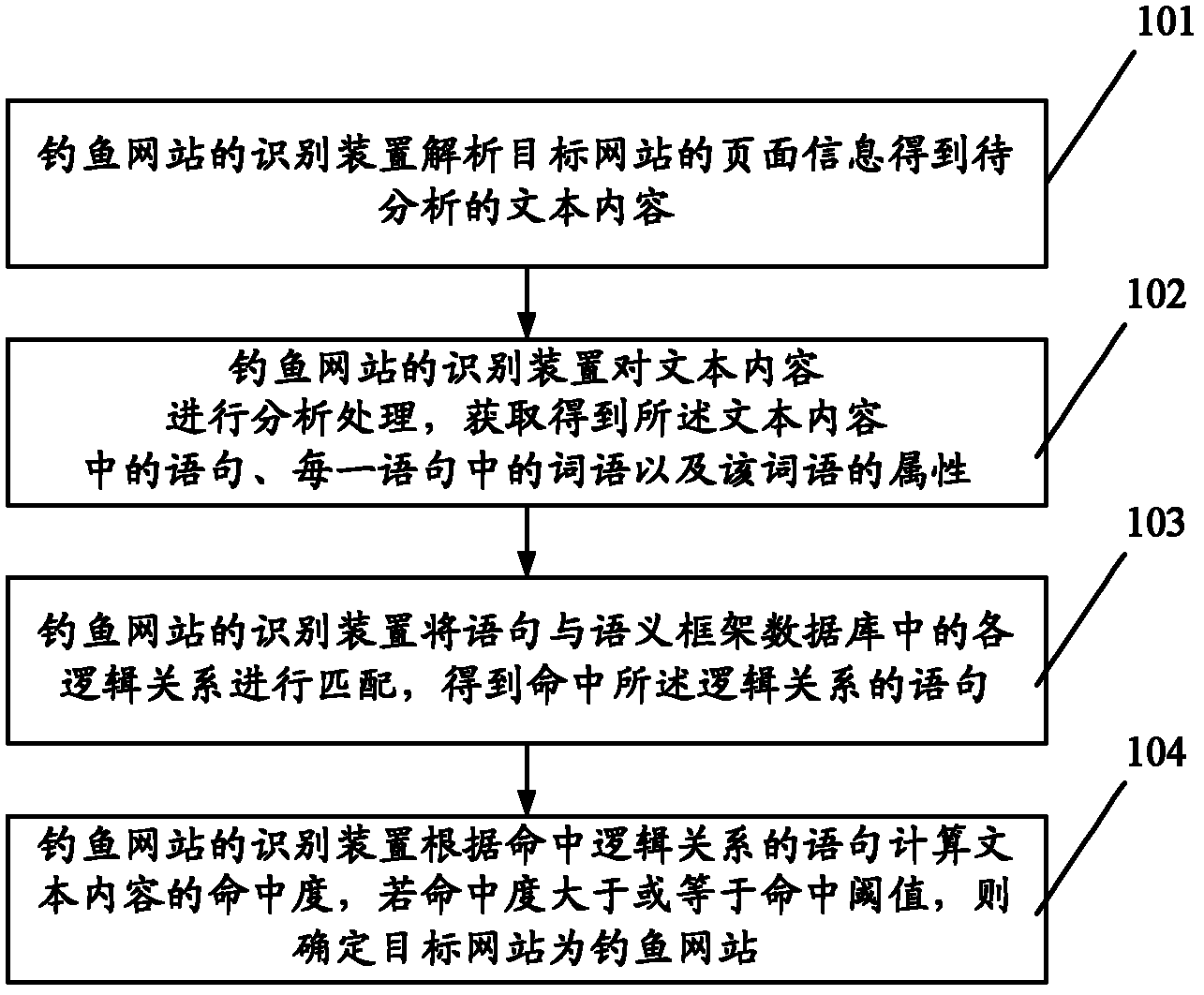
[0030] figure 2 It is a schematic flow diagram of an embodiment of a method for identifying a phishing website in the present invention, such as figure 2 As shown, the method may include the following steps:
[0031] Step 101, the identification device of the phishing website analyzes the page information of the target website to be visited by the user to obtain the text content to be analyzed;
[0032] For example, the analysis and filtering interface module in the device for identifying phishing websites may perform the above analysis work. Wherein, the method for obtaining the page information of the target website may be as follows:
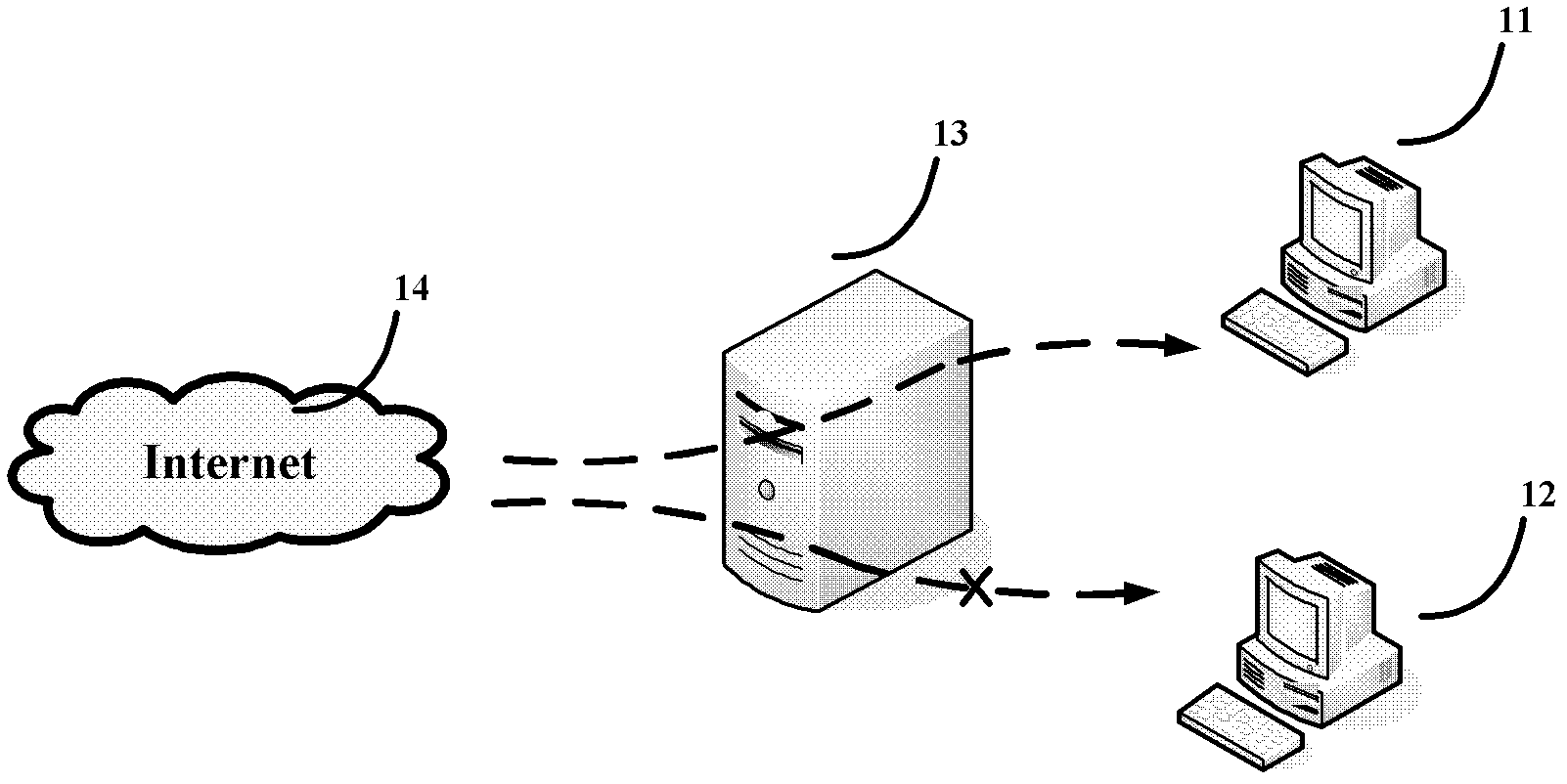
[0033] The analysis and filtering interface module can receive a phishing identification request instruction from an upper layer module or device. The upper module or device, for example, can be set in figure 1 In the server 13, it can be an upper-level user program, a gateway-side monitoring program, or an anti-phishing interface of ot...
Embodiment 2
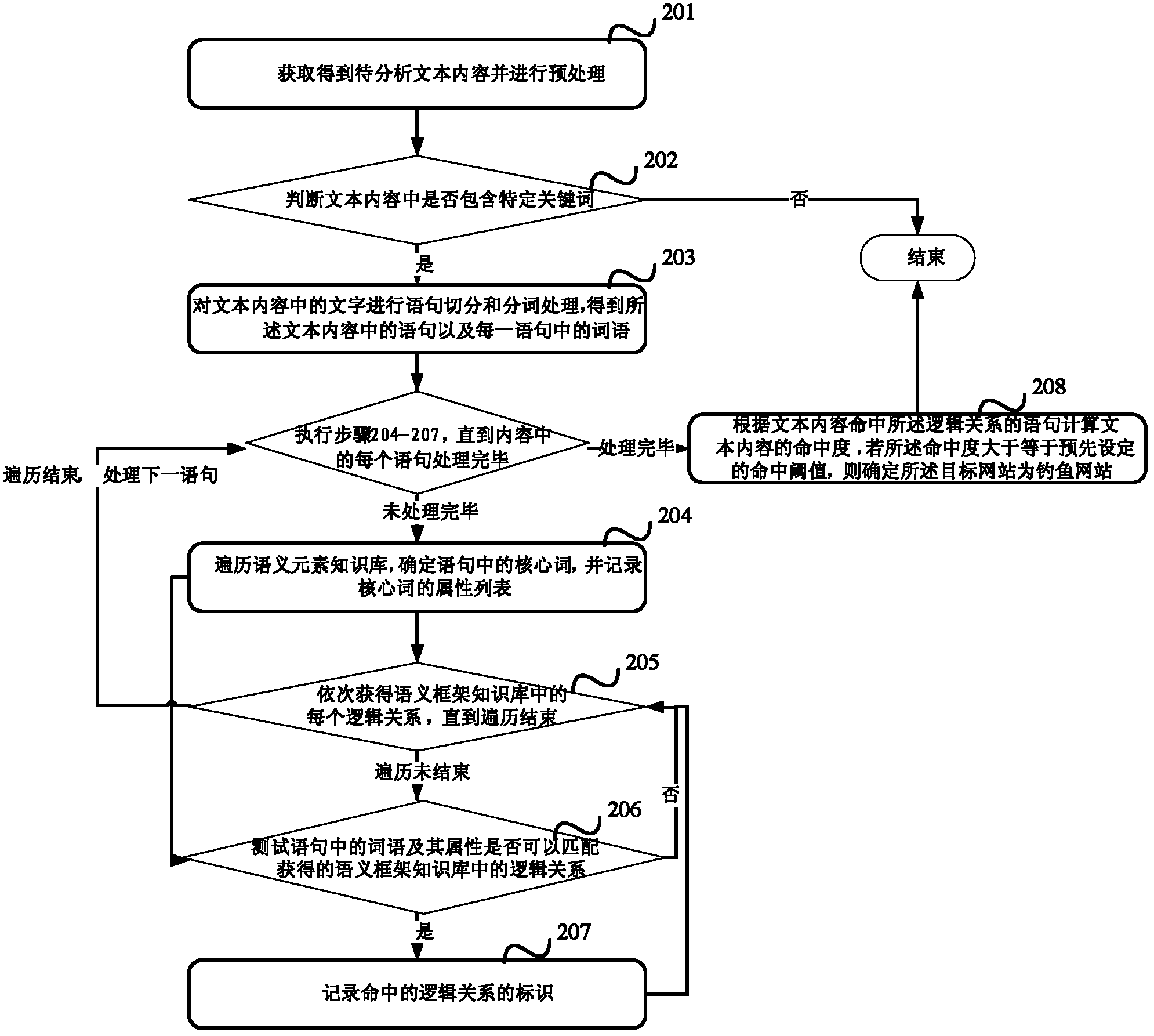
[0051] image 3 It is a schematic flowchart of Embodiment 2 of the method for identifying a phishing website of the present invention. This embodiment takes the identification of a winning website as an example to describe the method for identifying a phishing website of the present invention in detail.
[0052] Wherein, the following steps of the recognition method of this embodiment use the semantic element knowledge base and the semantic frame knowledge base. In order to make the following description of the method steps of the present embodiment clearer, the structures of the above two knowledge bases are first described as follows: see Figure 4 , Figure 4 It is a schematic diagram of the data structure in the semantic element knowledge base in Embodiment 2 of the identification method for phishing websites of the present invention.
[0053] Specifically, the semantic element knowledge base stores many words and attributes corresponding to the words, and the semantic f...
Embodiment 3
[0091] Image 6 It is a structural schematic diagram of Embodiment 1 of an identification device for phishing websites of the present invention. The identification device can execute the method described in any embodiment of the identification method for phishing websites of the present invention. This embodiment briefly introduces the structure of the device, and the specific working method can be See the description of the method examples.
[0092] Such as Image 6 As shown, the identification device of this embodiment may include: an analysis and filtering interface module 41, a semantic extraction module 42, a fishing identification module 43, a semantic element knowledge base 44 and a semantic frame knowledge base 45; the semantic extraction module 42 includes a semantic element analysis unit 421 and semantic frame matching unit 422 .
[0093] Wherein, the analysis and filtering interface module 41 is used to analyze the page information of the target website to be visi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com