Fast-flux botnet detection method and system in high-speed network
A botnet and high-speed network technology, applied in the field of Fast-Flux botnet detection under high-speed networks, can solve the problems of high false alarm rate, low detection accuracy, and low processing efficiency, so as to avoid false negatives, high detection accuracy, The effect of improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
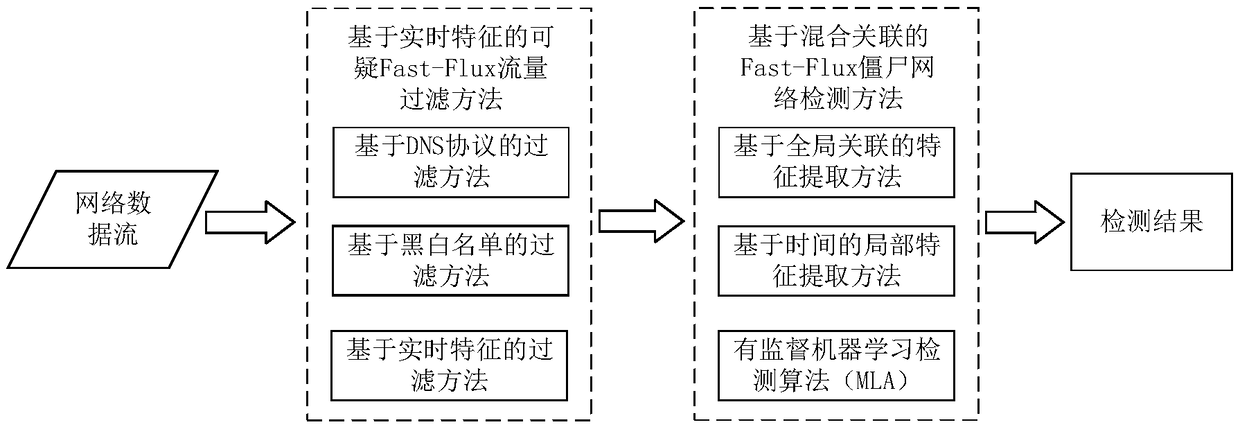
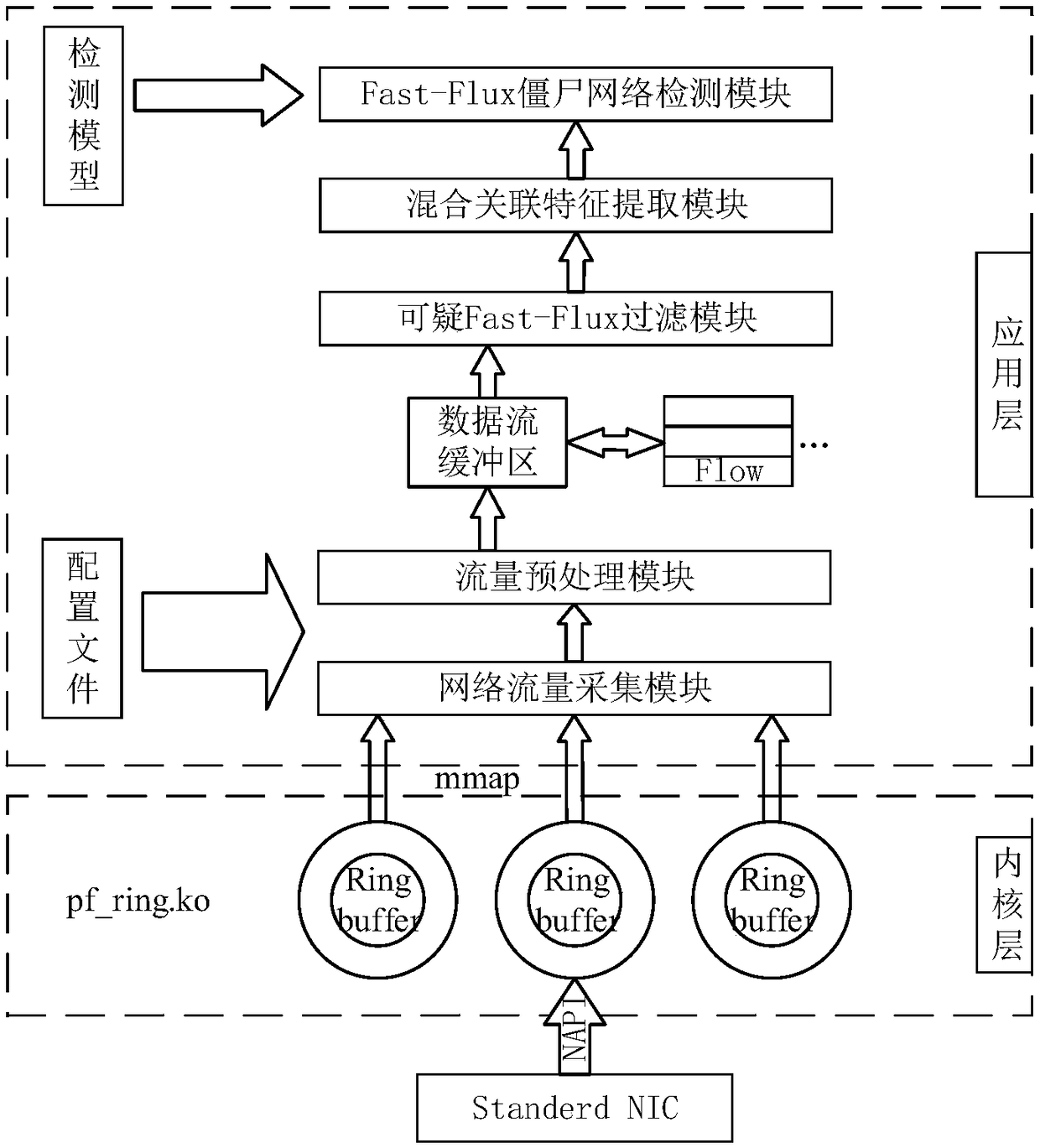
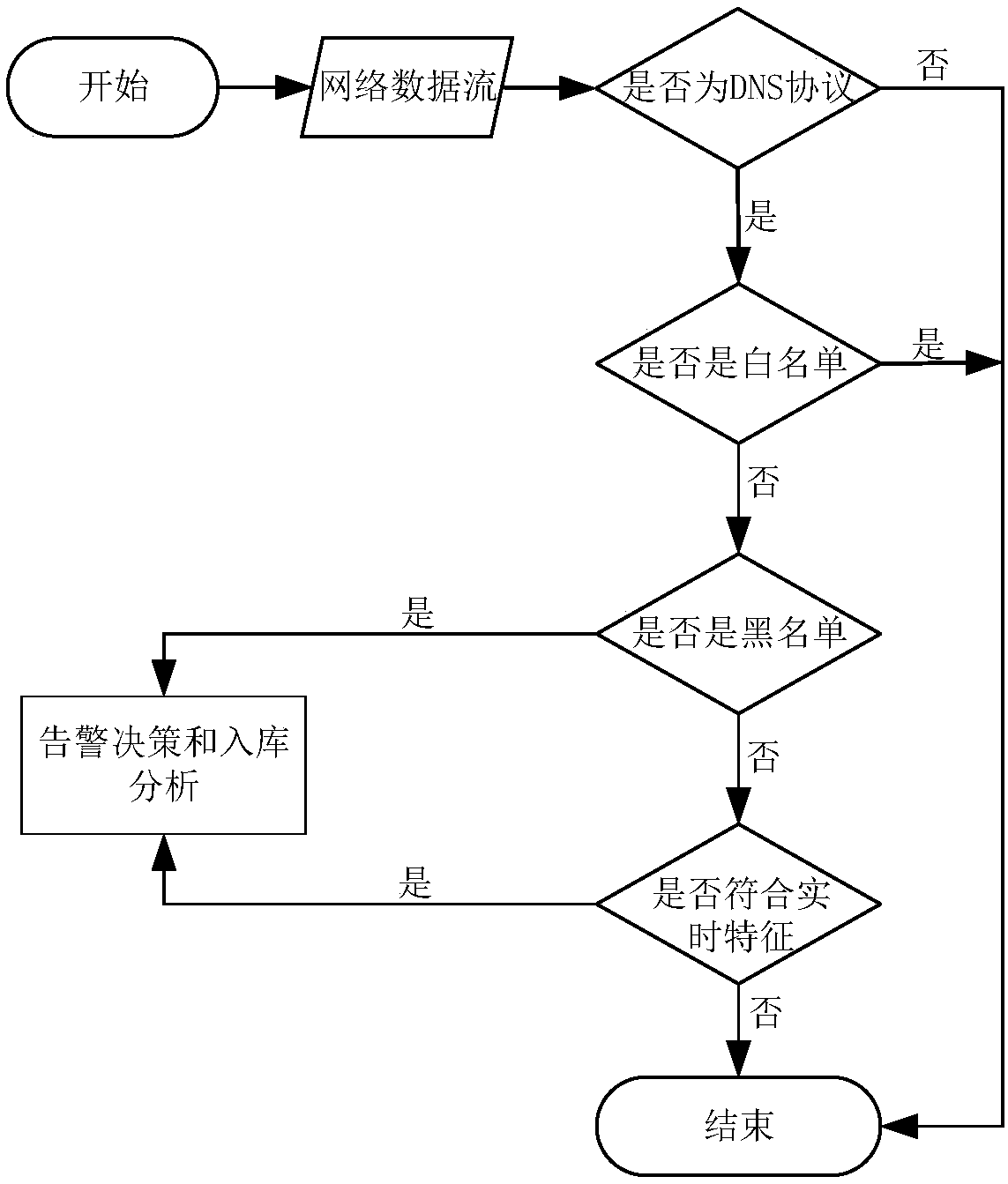
[0081] The current research on Fast-Flux botnets has begun to take shape, but there is currently no relatively mature detection system for the detection of Fast-Flux botnets under large data set traffic. Most of the research on the FastFlux botnet at home and abroad is based on collecting a list of malicious domain names, then using the dig tool to find the characteristics of malicious domain names offline, and then training the feature vectors through learning algorithms to detect Fast-Flux botnets, which does not guarantee the real online The detection rate in the environment achieves the same result, especially in high-speed networks.
[0082] In a high-speed network, taking a 10Gbps network as an example, even if the network utilization rate is only 30% under normal circumstances, 500M data traffic will be generated in one second. Assuming that the average size of each data packet is 512Byte, the data packet will also There are 1 million. Once the data packet processing pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com