A tag data anti-theft method based on EPC protocol, electronic tag and reader
A technology of electronic tags and tag data, which is applied in the direction of collaborative devices, instruments, and record carriers used by machines, which can solve problems such as the inability to guarantee the security of tag data, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
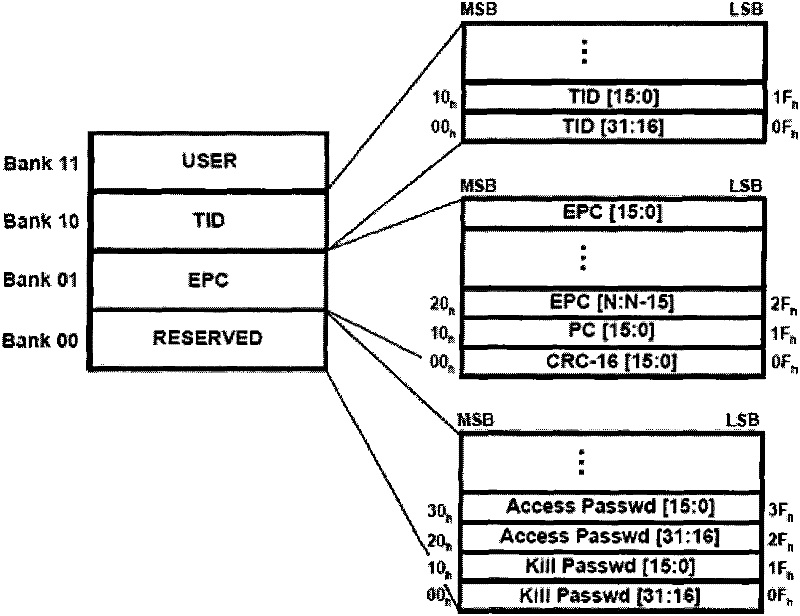
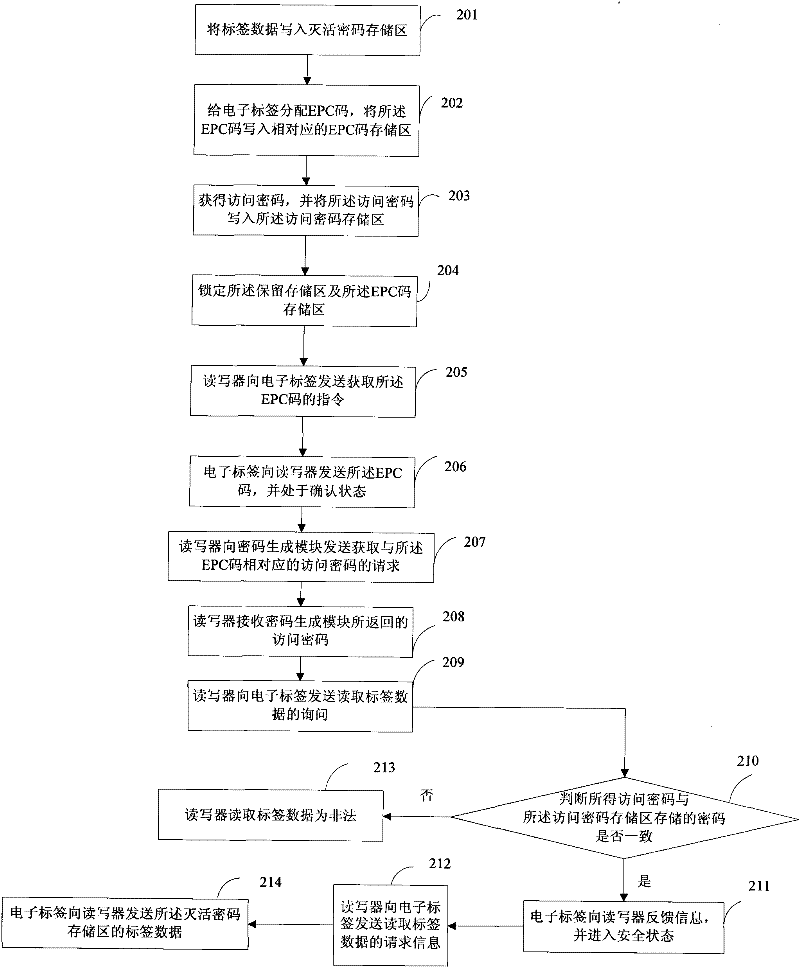
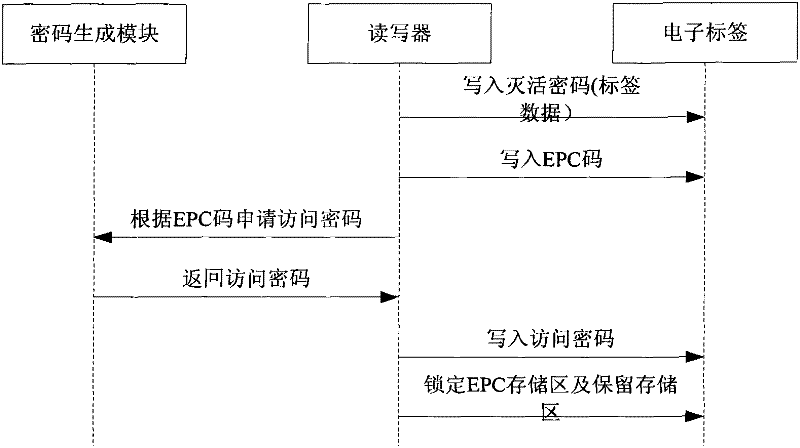
[0065] Such as figure 2 As shown, it is a flow chart of the tag data anti-theft method based on the EPC protocol according to the embodiment of the present invention. In this embodiment, both the reader-writer and the electronic tag comply with the EPC protocol. Wherein, the storage area of the electronic tag based on the EPC protocol includes an EPC storage area, a TID storage area, a reserved storage area, and a user storage area; wherein, the reserved storage area includes an inactivation password storage area and an access password storage area. In this embodiment, the TID codes in the TID storage areas of all electronic tags are set to a uniform value. First, in step 201, the tag data is written into the inactivation password storage area, wherein the tag data is the data that the user needs to encrypt and can only read through authorization, and the reader / writer writes the tag data into the inactivation password storage area. Password storage area. Then in step 20...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com