Access control list conversion system, and method and program therefor
一种访问控制表、访问控制的技术,应用在存储器系统、仪器、计算等方向,能够解决损害可维护性等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
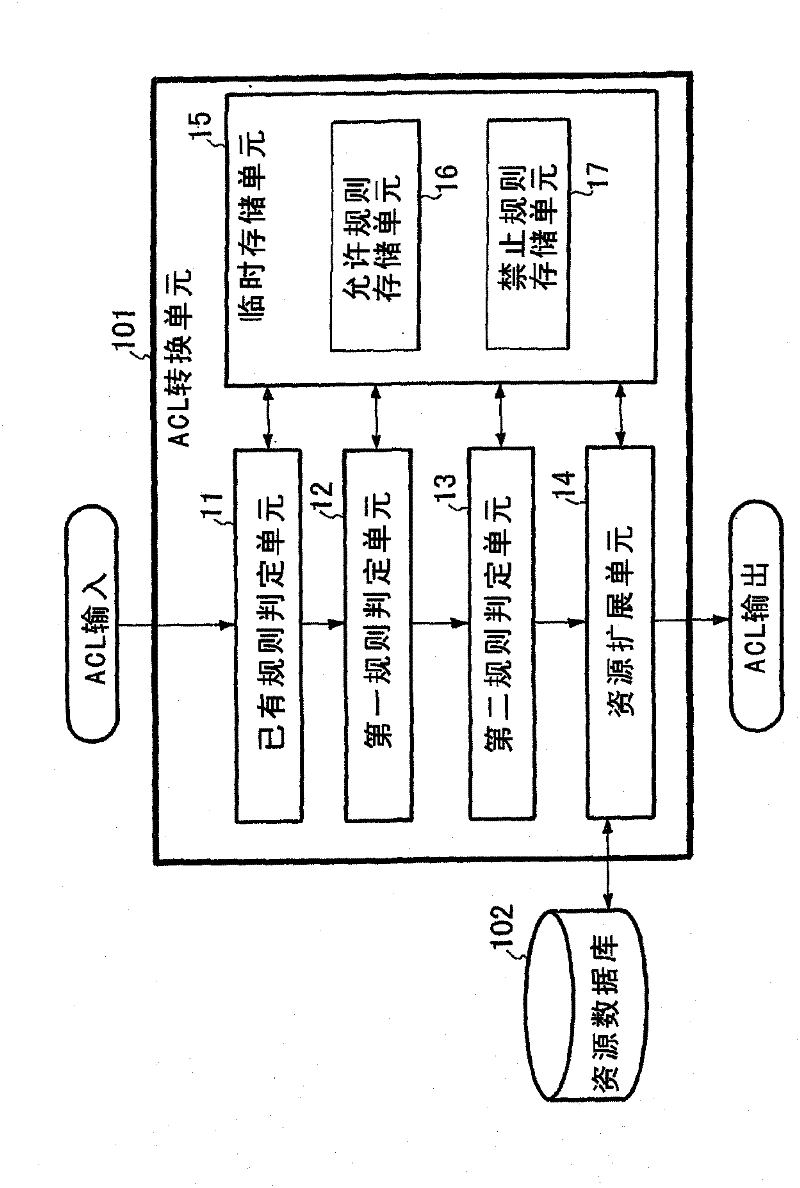
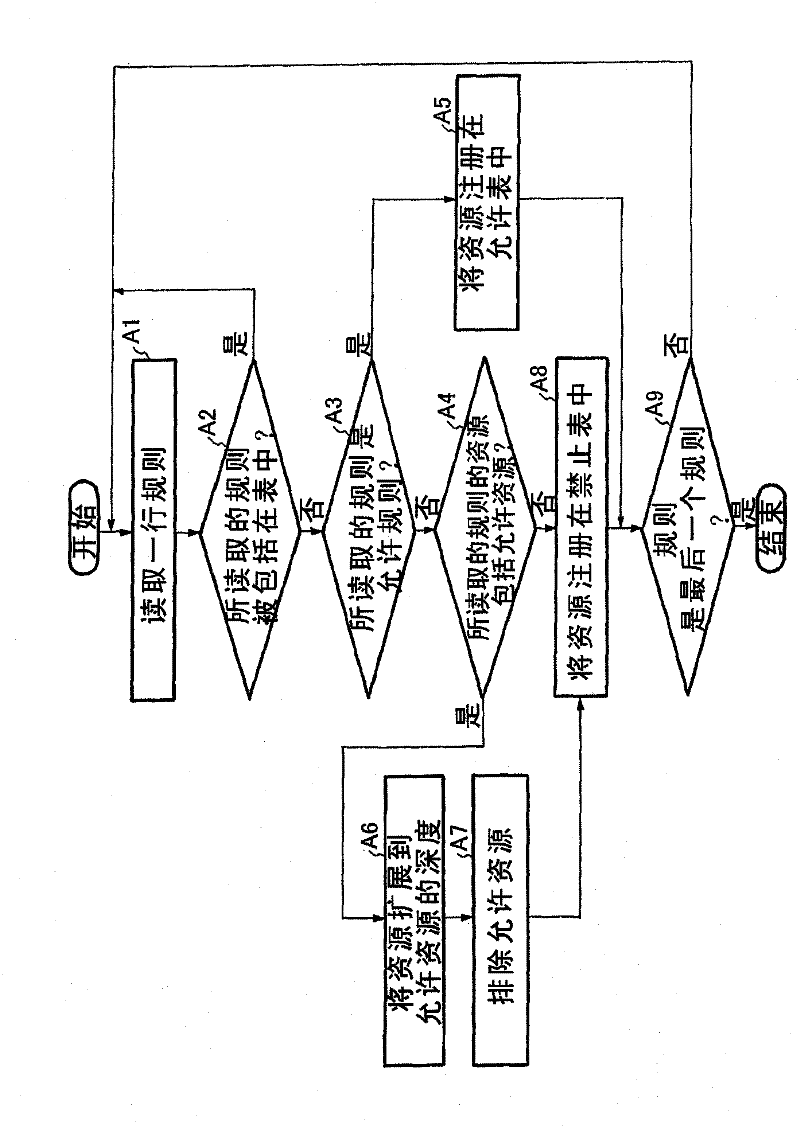
[0047] figure 1 is a block diagram showing an example of the structure of the access control list generation / conversion system according to the first embodiment of the invention.
[0048] refer to figure 1 , the first embodiment of the invention includes an ACL conversion unit 101 and a resource database 102 .
[0049] The resource database 102 systematically stores all the latest information (from high-level concepts to low-level concepts) of resources to be controlled by access control lists (ACLs).
[0050] In the invention, the access control list is configured to include one or more access control rules, each access control rule being a set of: the access target resource to be accessed, the access actor user to access the access target resource, and the defined It specifies whether to allow or prohibit the access actor user's access to the access target resource. "Access actor user" is, for example, information capable of specifying a user (such as "Yamada") who access...
no. 2 example
[0074] Next, an access control list differential allocation system according to another embodiment of the invention will be described in detail with reference to the drawings.
[0075] In this embodiment, an access control list (ACL) is widely managed, the access control list is updated for an updated policy, and the difference before and after the update of the access control list is distributed to each control target machine.
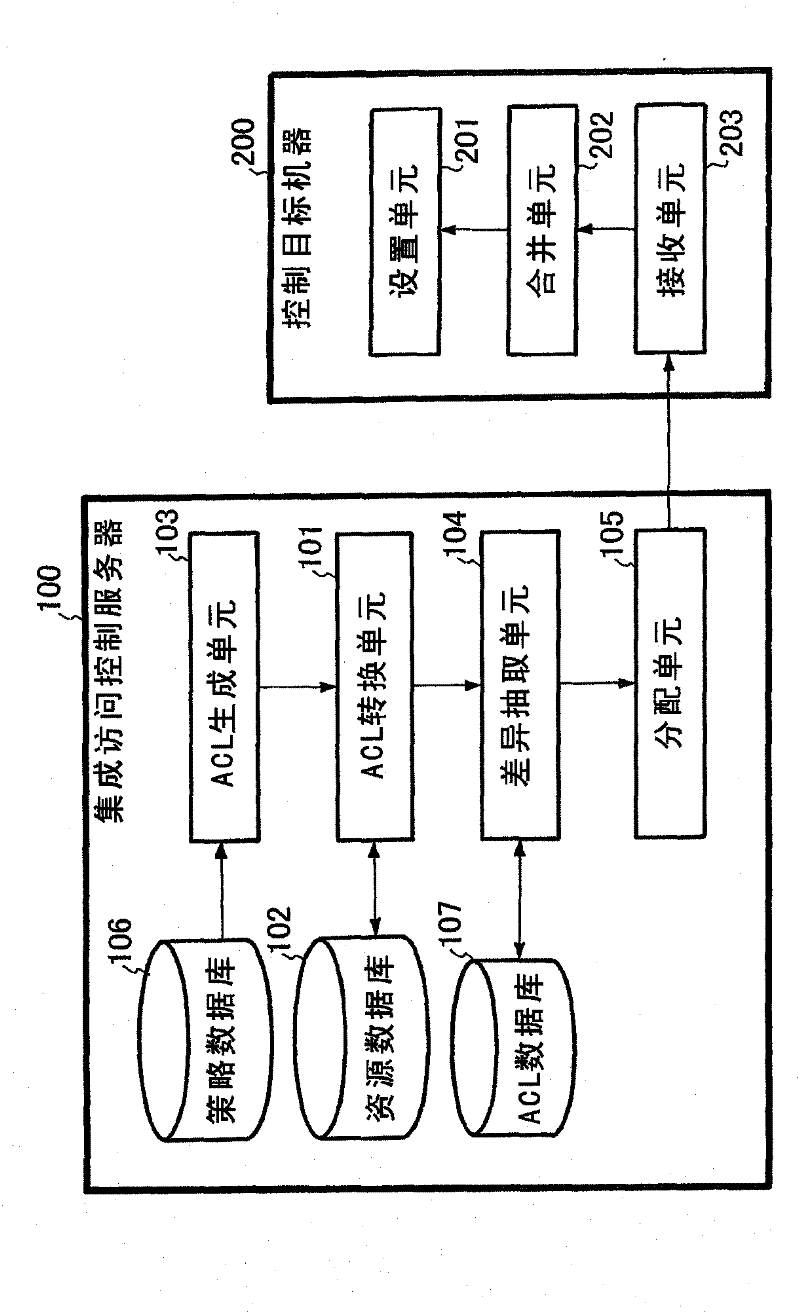
[0076] refer to image 3 , this embodiment includes an integrated access control server 100 and a control target machine 200. image 3 is a block diagram showing an example of the structure of the access control list differential allocation system according to the second embodiment of the invention.
[0077] The integrated access control server 100 includes a policy database 106 , a resource database 102 , an ACL database 107 , an ACL generating unit 103 , an ACL converting unit 101 , a difference extracting unit 104 , and an allocating unit 105 . P...
no. 3 example
[0086] Next, an access control list consistency ensuring differential allocation system according to another embodiment of the invention will be described in detail with reference to the drawings.
[0087] In this embodiment, an example of ensuring consistency in distribution of differences between access control lists is described. Figure 4 is a block diagram showing a structural example of an access control list differential assignment consistency ensuring system according to the third embodiment of the invention.
[0088] refer to Figure 4 , in this embodiment, the integrated access control server 100' also includes a signature unit 108 and a control target machine 200', compared with the second embodiment, it also includes a signature verification unit 204.
[0089] In the integrated access control server 100', the difference information extracted by the difference extraction unit 104 is supplied to the signature unit 108. The signature unit 108 adds the private key di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com