Security-marker-based access control method and related system
A security mark and access control technology, applied in transmission systems, electrical components, etc., can solve problems such as the inability to manage the unified management of subject access control, and the inability to adapt to the development needs of building a security mark protection level information system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The embodiment of the present invention provides an access control method based on a security mark, which is used to apply MAC technology to the middleware layer, so that the access control of the subject can be managed uniformly at the middleware layer, and at the same time, it is adapted to the construction of security mark protection level information. system development needs. Embodiments of the present invention also provide related systems, which will be described in detail below.
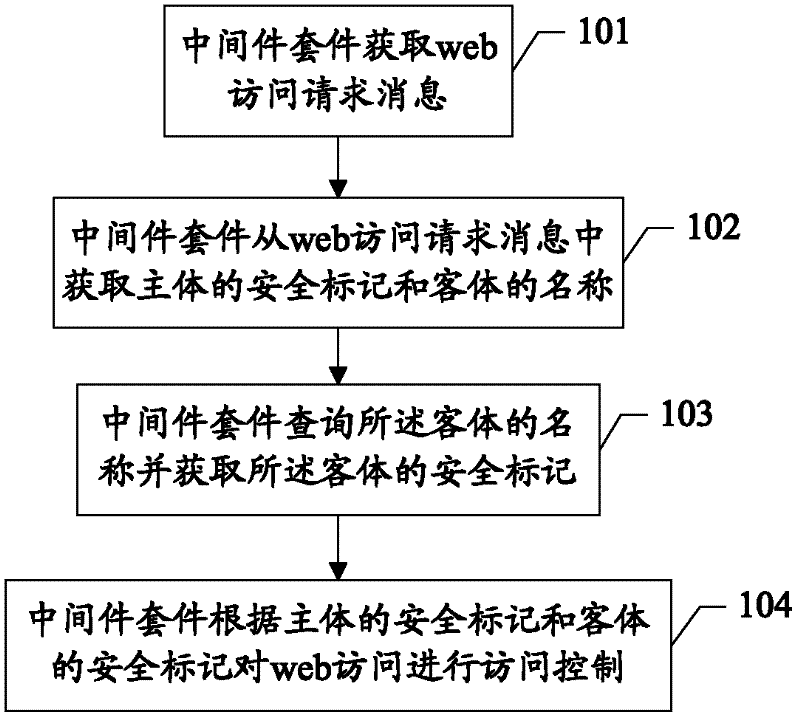
[0028] Please refer to figure 1 , mainly including steps:
[0029] 101. The middleware suite acquires a web access request message.
[0030] Wherein, before the subject accesses the object, it sends a web access request message to the middleware, and the middleware package can obtain the web access request message. The web access request message includes information such as the subject security mark and the name of the object.
[0031] 102. The middleware suite acquires the security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com