Generation method of embodiment for information safety evaluation
A security assessment and information security technology, applied in the field of information security, can solve problems such as poor application flexibility and scalability, inability to cover assessment items, and complicated work, so as to improve data collection efficiency and assessment and analysis results, improve automation management level, Enhance the effect of standardization and consistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] Embodiment 1. A method for generating an implementation use case for information security assessment, the process is as follows figure 1 shown, including:
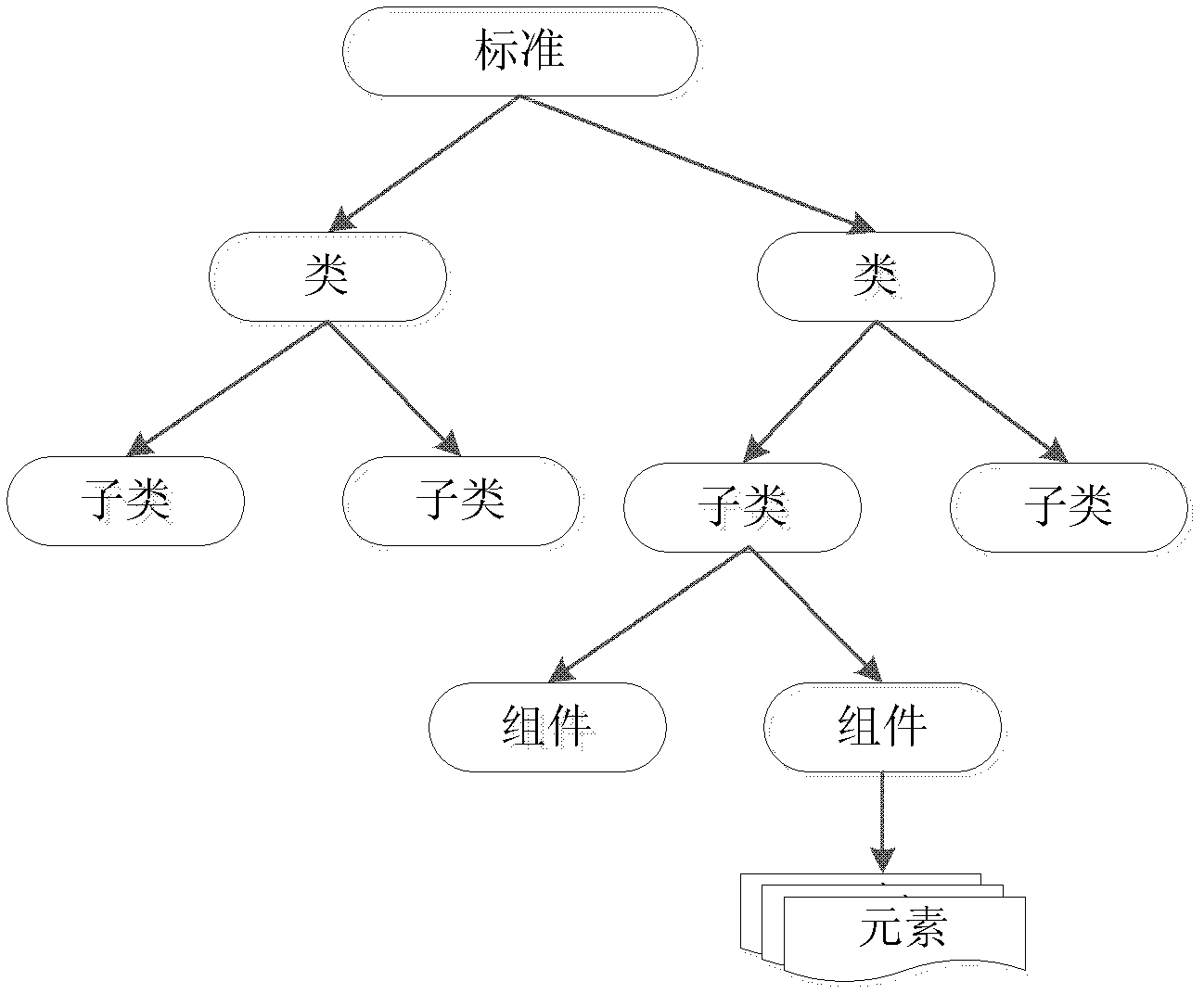
[0040] Preserving each evaluation standard, wherein each evaluation standard includes its corresponding safety evaluation content;
[0041] Form assessment use case templates for different industry types and business types respectively; said assessment use case templates include the security assessment content corresponding to each assessment standard included in the industry type and business type, and the corresponding test methods for each security assessment content;
[0042] Select the corresponding evaluation use case template according to the business type and industry type of the project to be evaluated, and construct the evaluation use case instance of the project to be evaluated;
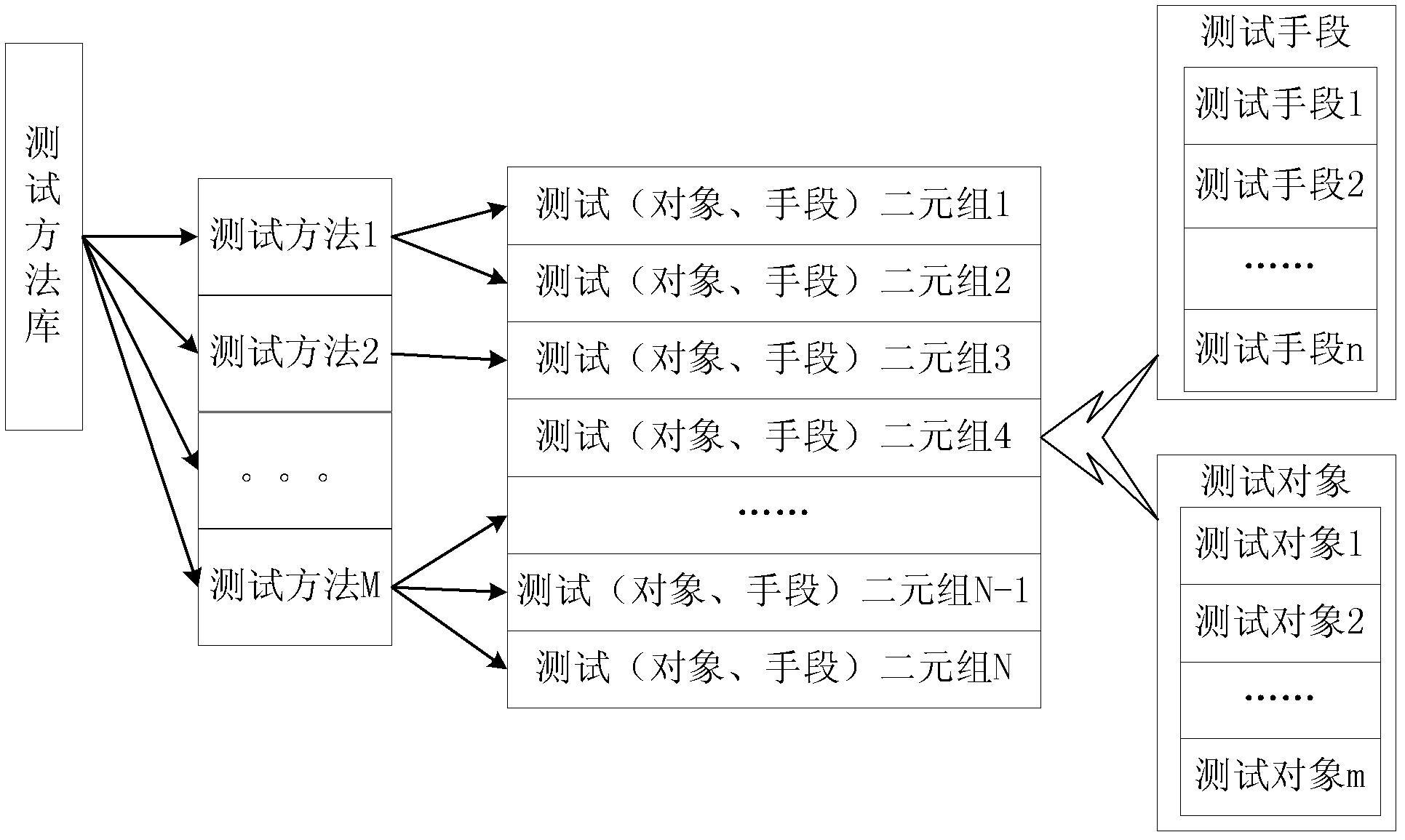
[0043] A test method is selected according to the evaluation use case instance of the project to be evaluated and the test ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com