Block encryption method based on parity cellular automaton
A block encryption and automaton technology, applied in the field of information security, can solve problems such as security and efficiency defects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
[0034] Such as figure 1Shown, in conjunction with a specific embodiment introduction realizes the technical scheme of the present invention, comprises the following steps:
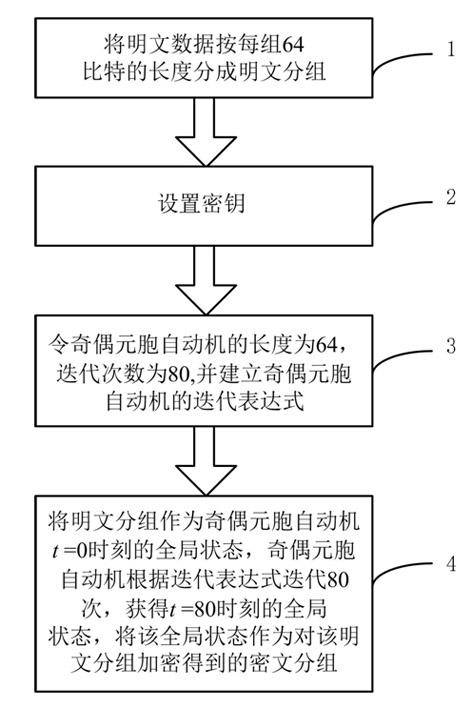
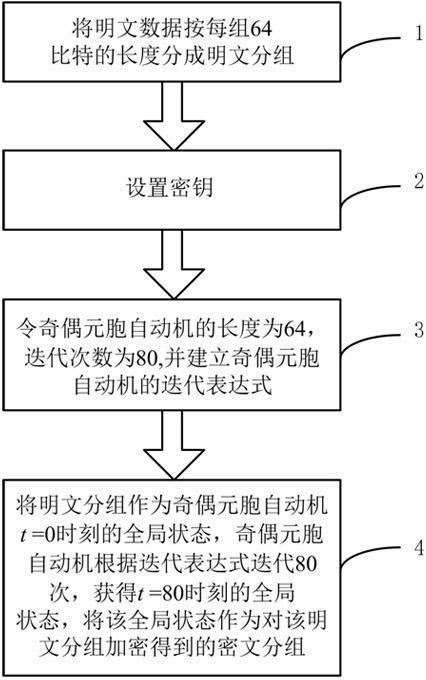
[0035] Step 1: divide the plaintext data into plaintext groups according to the length of each group of 64 bits;
[0036] Step 2: Set the key, key 1 is an 8-bit binary sequence a 0 a 1 a 2 a 3 here (k=0, 1, 2, 3) represents a k The value of is reversed, the key 2 is a string of 80-bit binary random sequence r 1 r 2 r 3 ,...,r 80 ;
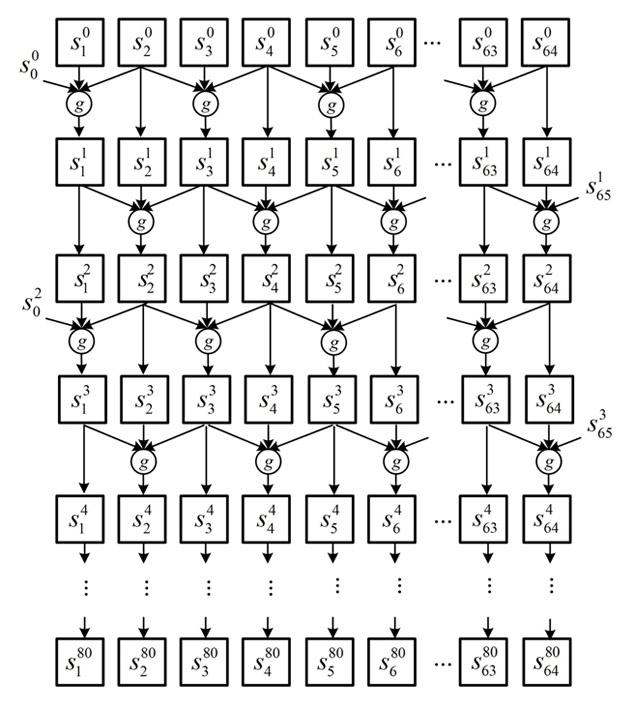
[0037] Step 3: Let the length of the odd-even cellular automaton be 64, the number of iterations of the odd-even cellular automaton be 80, and establish the iteration expression of the odd-even cellular automaton:
[0038] When time t is even, s i t + ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com