Attack detecting method and device
An attack detection and scenario technology, which is applied in the field of information management and can solve the problem that the correlation analysis method is not suitable for complex scenarios.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
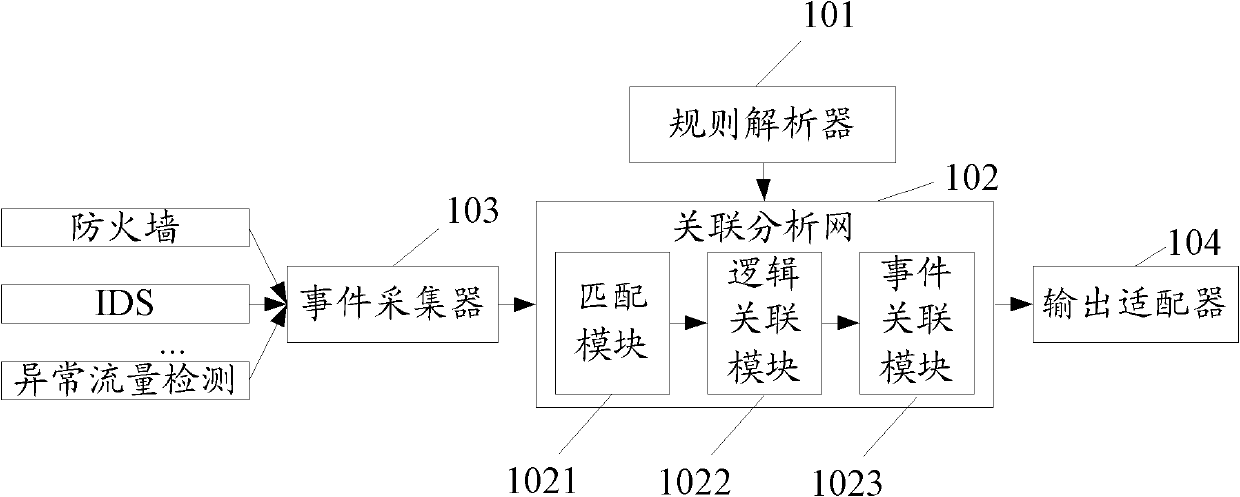
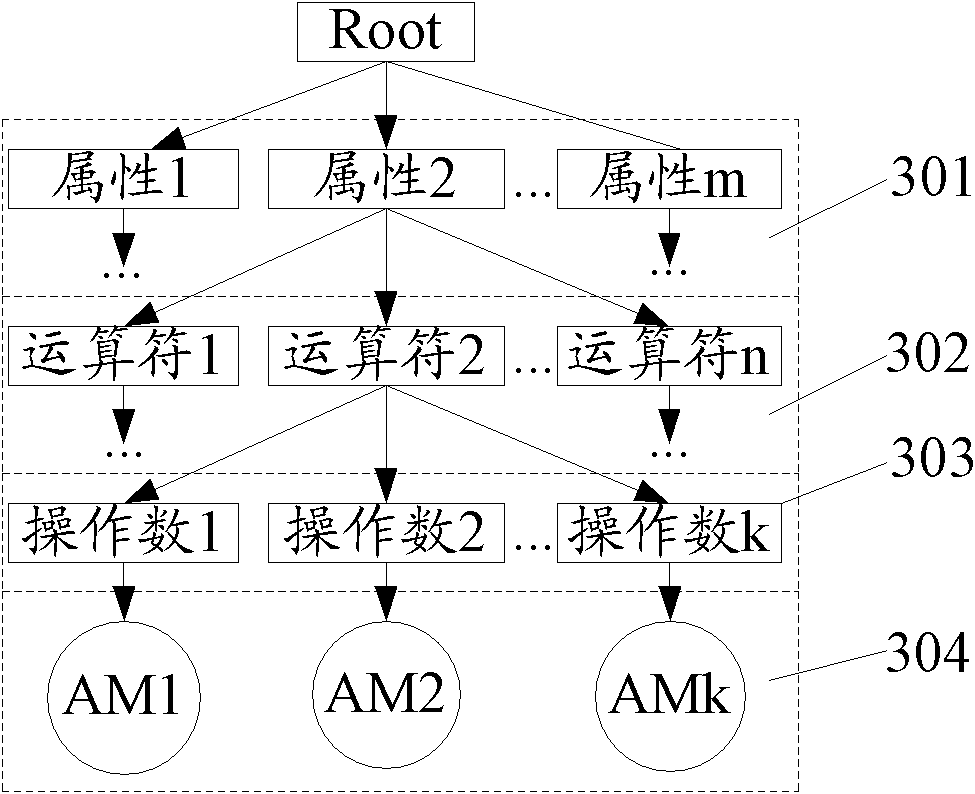
[0048] Most of the existing rule association analysis systems are based on finite state automata technology. In the case of a large number of rules, the number of states will be relatively large, which directly affects the calculation speed of the association analysis, and the system operation efficiency is seriously reduced.
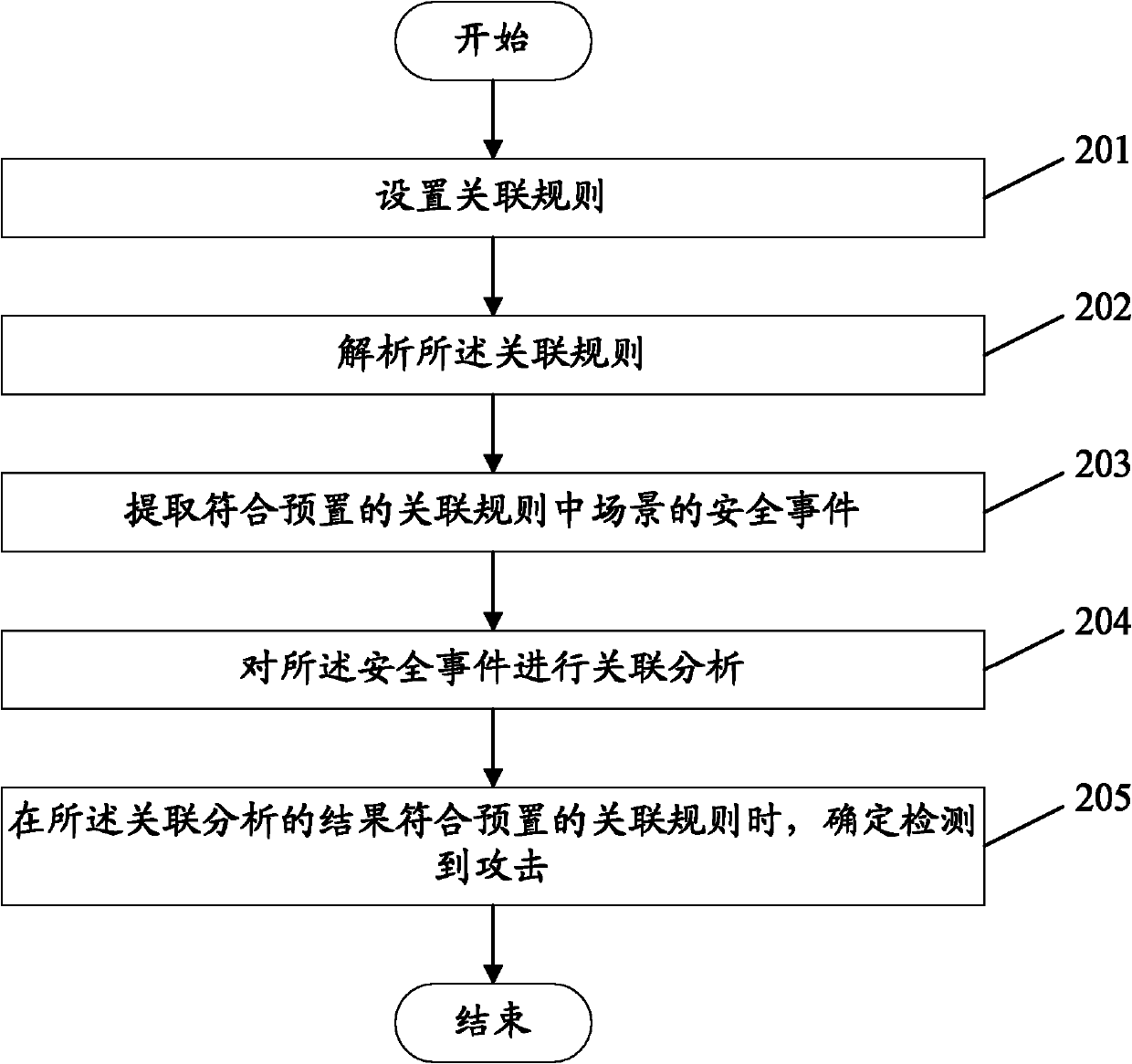
[0049] In order to solve the above problems, embodiments of the present invention provide an attack detection method and device. Using the attack detection method provided by the embodiment of the present invention, when looking for associated security events, the fast matching and association of associated security events among massive events can be realized according to set association rules. The technical solution provided by the invention can realize efficient matching and correlation analysis of security events in the case of complex correlation rules.
[0050] Embodiments of the present invention will be described in detail below in conjunction w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com