Double-host security computer based on satellite system
A security and security, satellite system technology, applied in the direction of transmission system, electrical components, etc., can solve the problems of the integrated security computer security security function is not perfect, leaking, affecting the computer running speed and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
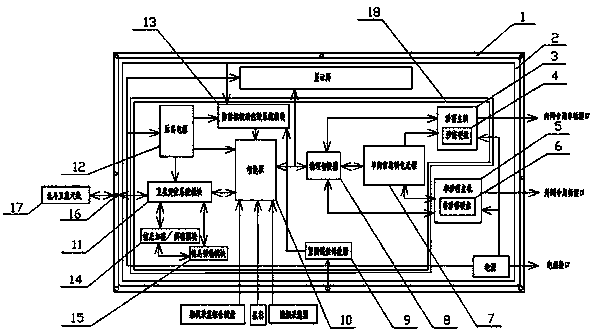
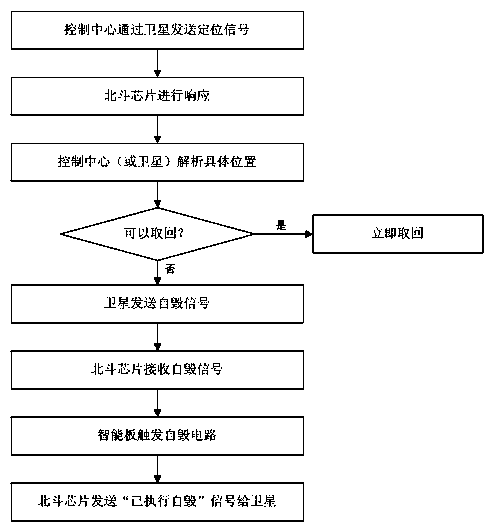
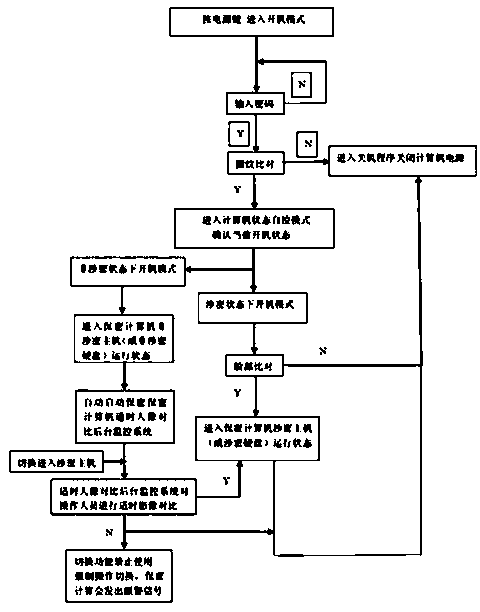
[0042] A kind of dual-host security computer based on satellite system, such as Figures 1 to 6As shown: including the mainframe and the casing 1, there are two mainframes, which are classified host 3 and non-secretized host 5 (named classified host 3 and non-secretized host 5, of course, it can also be named the first host 3 and the second host 5), the confidential host 3 and the non-secret host 5 are respectively connected with a physical switch 8, and the physical switch 8 is connected with a smart board 10, and the smart board 10 is interconnected and data transmission through the PCI-E bus control components . The secret-involved host 3 includes a first motherboard, a first CPU, a first RAM, a first sound card, a first network card and a first graphics card, and the secret-involved host 3 is connected with a secret-involved hard disk 4, which is a solid-state hard disk. The secret-related host 5 includes a second motherboard, a second CPU, a second RAM, a second sound ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com