Software protecting method and software sale method based on same
A technology of software protection and software, applied in the direction of program/content distribution protection, marketing, instruments, etc., can solve the problems of parallel imports hitting the market, waste, unusable, etc., to achieve flexible sales of software, improve security, and maximize benefits Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
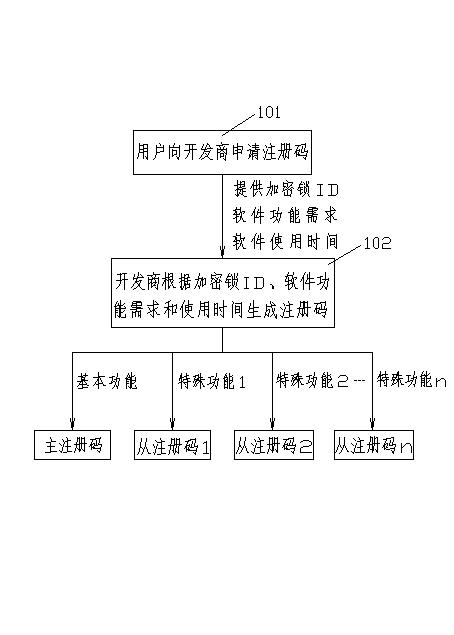
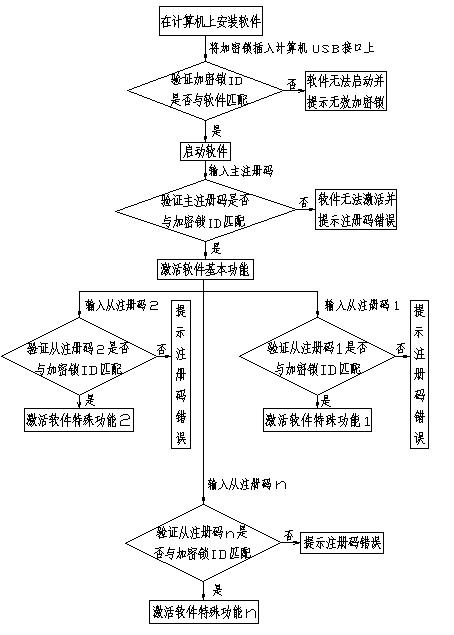
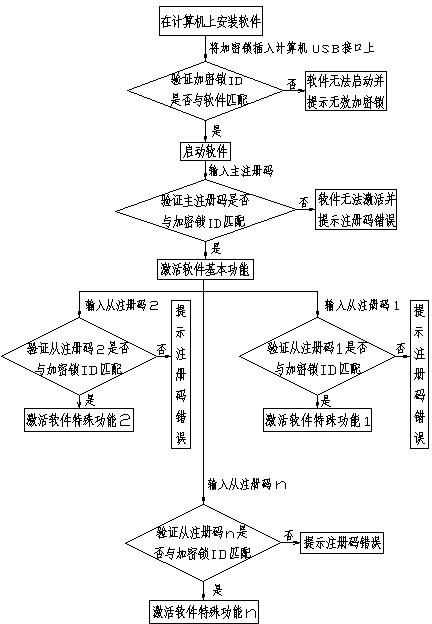
[0021] The software protection method of the present invention is described in detail below with the RIP software of ink-jet printer, and developer is when developing software, and the function of software is divided into basic function and special function, to basic function and special function encryption protection respectively, simultaneously to software The startup encryption of the software, the software starts using the hardware encryption method, such as a dongle, and the activation of the software function uses the software encryption method, such as the registration code (software serial number). When selling software, the developer will distribute the dongle containing the developer’s company ID and dongle ID to the user together with the RIP software; each set of RIP software corresponds to a dongle, and when the user gets the RIP software, install the RIP software on the computer At the same time, plug the encryption lock into the parallel interface, serial interfa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com