A digital signature method and device
A digital signature and quantity technology, applied in the field of information security, can solve the problems of online banking security threats, the inability to guarantee the security of the online banking system, and the low security of digital signature methods, so as to improve security and reduce losses.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0074] Embodiment 1 of the present invention provides a digital signature method, see figure 1 , including the following steps:
[0075] Step 101, the host obtains the data input by the user, encapsulates the message according to the data, and sends the encapsulated message to the USBKey.
[0076] Wherein, the data input by the user may include instructions and / or parameters, and the instructions include query instructions, payment instructions, and transfer instructions, etc.; the parameters include account number, account name, and transfer amount, etc. The business system in the host adds content to the message by calling the functions provided by the controls in the host according to the data input by the user, and encapsulates the content, keywords corresponding to the content, and content length information into information segments in the message. When it is necessary to add content to the message multiple times, the information segments need to be arranged according t...
Embodiment 2
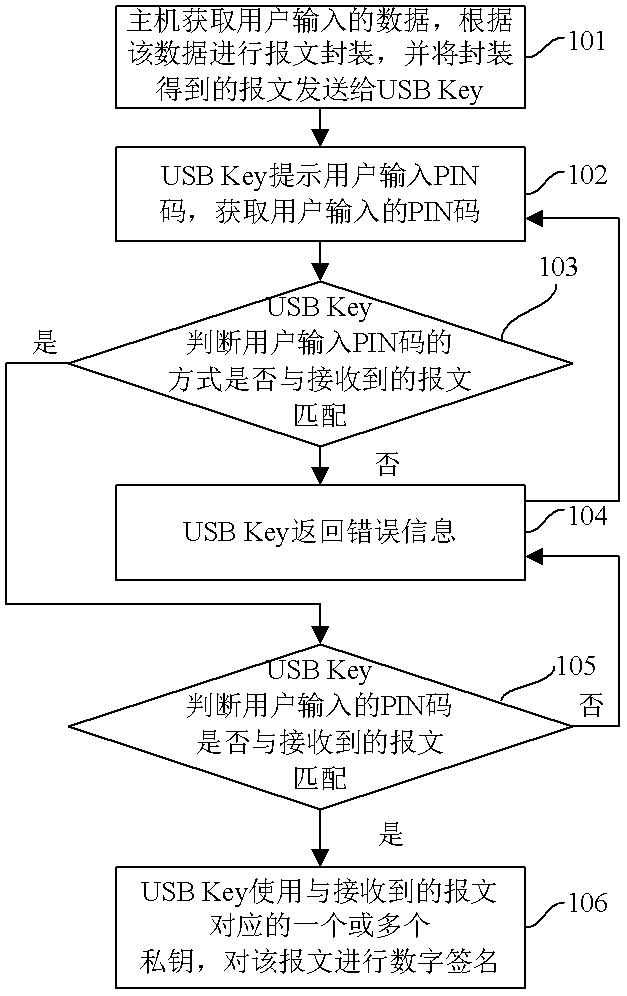
[0108] Embodiment 2 of the present invention provides a digital signature method, which is applied to a system including a host computer and a USBKey, see image 3 , including the following steps:
[0109] Step 201, the host obtains the data input by the user, encapsulates the message according to the data, and sends the encapsulated message to the USBKey.
[0110] Wherein, the data input by the user may include instructions and / or parameters.
[0111] Step 202, the USBKey sends prompt information to the host according to the received message.
[0112] Step 203, the host prompts the user to input a PIN code according to the received prompt information, obtains the PIN code input by the user, and sends the PIN code to the USBKey.
[0113] It should be noted that the above step 202 is a preferred step of this embodiment. In other embodiments of the present invention, the USBKey may not send prompt information to the host. After the host obtains the data input by the user, it ...
Embodiment 3
[0128] Embodiment 3 of the present invention provides a digital signature method, see Figure 4 , including the following steps:
[0129] In step 301, the USBKey receives a message from a host.
[0130] In step 302, the USBKey prompts the user to input a PIN code, and obtains the PIN code entered by the user.
[0131] Step 303 , the USBKey judges whether the PIN code set stored by itself contains the PIN code input by the user, and if so, executes step 304 ; otherwise, executes step 305 .
[0132] Step 304 , the USBKey judges whether the PIN code input by the user is the same as the PIN code used in the last authentication, and if they are the same, execute step 305 ; otherwise, execute step 308 .
[0133] In step 305, the USBKey returns authentication failure information, and adds 1 to the number of authentication failures.
[0134] Wherein, the initial value of the authentication failure times is 0.
[0135] In step 306, the USBKey judges whether the number of authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com