Network data security management method and equipment
A network data and security management technology, applied in the field of network data security management, can solve the problems of filter leakage, illegal content deception, sensitive data filtering and early warning, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
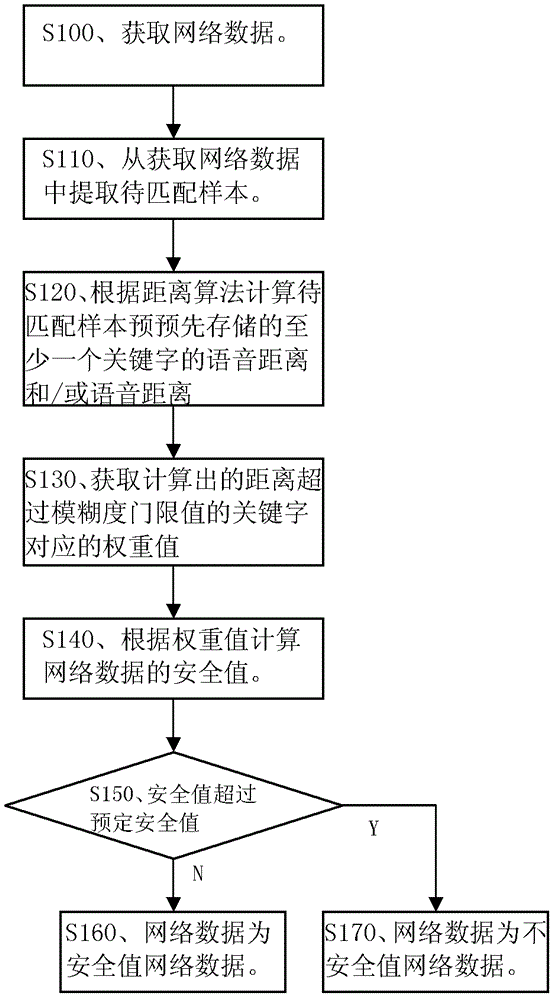
[0027] Embodiment 1. Network data security management method. The procedure of this method is as follows figure 1 shown.
[0028] figure 1 The specific process of the network data security management method shown in includes the following steps:
[0029] S100. Obtain network data.
[0030] Specifically, the present invention can intercept network data flowing through the node at a certain node in the network and needs to continue to be transmitted in the network. The node can be the source node or intermediate node of the network data transmission path. For example, the node can Network devices such as switches, routers, or servers. The network data may be all payloads carried in a data packet, or may be part of payloads carried in a data packet. The present invention does not limit the specific location of the network device for acquiring network data, the specific form of the network device, and the like.
[0031] S110. Extract samples to be matched from the acquired n...
Embodiment 2
[0053] Embodiment 2, a network data security management method.
[0054] The flow of this method is basically the same as that of the first embodiment above, except that an additional step of judging the frequency of occurrence is required. In order to realize this judgment step, the corresponding relationship information also includes the field of the keyword occurrence frequency probability threshold value, and it is also necessary to calculate the matching samples whose distance calculated by S120 exceeds the ambiguity threshold value in the full text of the network data. If the frequency of occurrence does not exceed the keyword occurrence frequency probability threshold value corresponding to the matching sample, the network data is determined to be safe network data; otherwise, the network data is determined to be unsafe network data.
[0055] The newly added judging step in the second embodiment should be after S120, and the newly added judging step may not be performed...
Embodiment 3
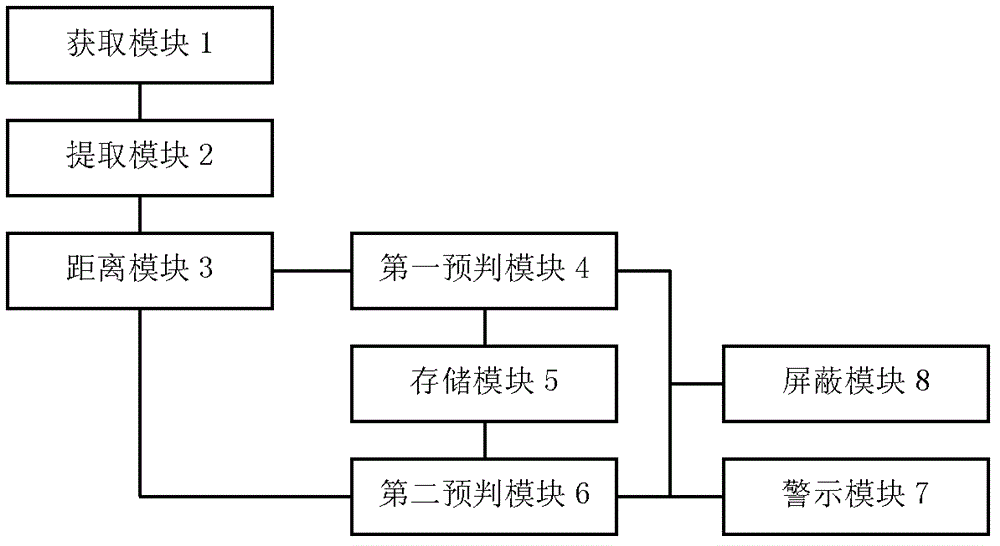
[0056] Embodiment 3, network data security management equipment. The structure of the device is attached as figure 2 shown.
[0057] figure 2 The network data security management device shown in specifically includes: an acquisition module 1 , an extraction module 2 , a distance module 3 , and a first prediction module 4 . Optionally, the device may further include: at least one of a storage module 5 , a second prediction module 6 , a warning module 7 , and a shielding module 8 .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com