Method and device for detecting and inhibiting Ethernet link storm
A storm, one-half technology, applied in the field of communication, can solve problems that do not meet the field environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] Embodiment 1 describes in detail a method for detecting and suppressing an Ethernet link storm proposed by this application.
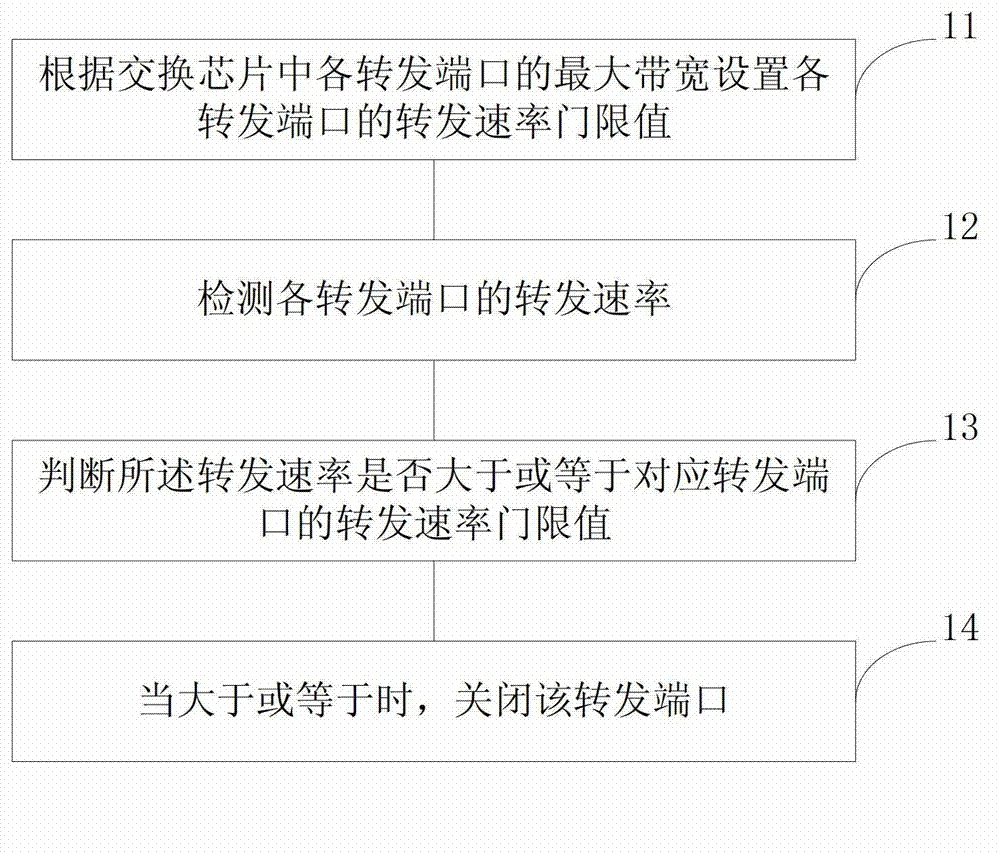
[0050] refer to figure 1 , which shows a flowchart of a method for detecting and suppressing an Ethernet link storm according to Embodiment 1 of the present application.
[0051] Step 11, setting the forwarding rate threshold value of each forwarding port according to the maximum bandwidth of each forwarding port in the switch chip;
[0052] During broadcast storms, the forwarding rate of data packets in the Ethernet link is much higher than that of transmitting normal business data, so the forwarding rate threshold can be set for each forwarding port according to the maximum bandwidth of each forwarding port in the switch chip to ensure The forwarding rate of each forwarding port under normal service will not reach the forwarding rate threshold.
[0053] For example, the maximum bandwidth of forwarding port A is 1000 Mbps, and the maximum ban...
Embodiment 2
[0068] Embodiment 2 introduces in detail a method for detecting and suppressing an Ethernet link storm proposed by this application.
[0069] refer to figure 2 , which shows a flowchart of a method for detecting and suppressing an Ethernet link storm described in Embodiment 2 of the present application.
[0070] Step 21, setting the forwarding rate threshold value of each forwarding port according to the maximum bandwidth of each forwarding port in the switch chip;
[0071] According to the maximum bandwidth of each forwarding port in the switch chip, a forwarding rate threshold is set for each forwarding port to ensure that the forwarding rate of each forwarding port will not reach the forwarding rate threshold under normal service.
[0072] Set the forwarding rate threshold value of each forwarding port in the switch chip to half of the maximum bandwidth of each forwarding port.
[0073] Since the packet forwarding rate of the Ethernet link during a broadcast storm is clo...
Embodiment 3
[0102] In the third embodiment, a method for detecting and suppressing an Ethernet link storm proposed in this application is introduced in detail.
[0103] refer to Figure 5 , which shows a flowchart of a method for detecting and suppressing an Ethernet link storm described in Embodiment 3 of the present application.
[0104] Step 31, setting the forwarding rate threshold value of the forwarding port;
[0105] Set the forwarding rate threshold of forwarding port A to 500 Mbps.
[0106] Step 32, detecting the forwarding rate of the forwarding port;
[0107]It is detected that the forwarding rate of forwarding port A at time T6 is 600 Mbps; the forwarding rate at time T7 is 300 Mbps.
[0108] Step 33, judging whether the forwarding rate exceeds the forwarding rate threshold;
[0109] Judging that the forwarding rate of forwarding port A of 600 Mbps at time T6 exceeds its forwarding rate threshold of 500 Mbps; judging that the forwarding rate of forwarding port A of 300 Mbp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com