A black hole attack detection method in clustered self-organizing network
A self-organizing network, black hole attack technology, applied in network topology, electrical components, wireless communication and other directions, can solve problems such as less research on mutual cooperation and cooperation, not considering multiple malicious nodes, and difficult to effectively overcome, etc. The effect of defense and treatment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
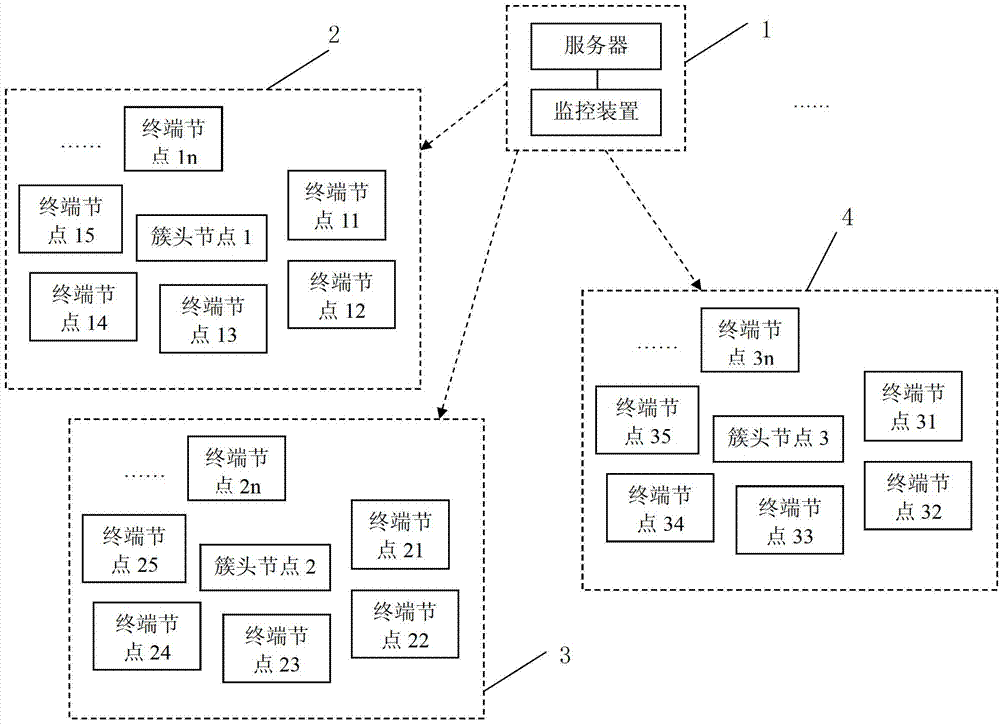
[0045] Such as figure 1 As shown, the self-organizing network includes one or more base stations 1, and each base station 1 has one or more cluster head areas within the coverage area. The figure shows the first cluster head area 2, the second cluster head area 3 and In the third cluster head area 4, there is one cluster head node and one or more terminal nodes in the cluster head area. For example, the first cluster head area 2 includes terminal node 11 to terminal node 1n, a total of n terminal nodes.
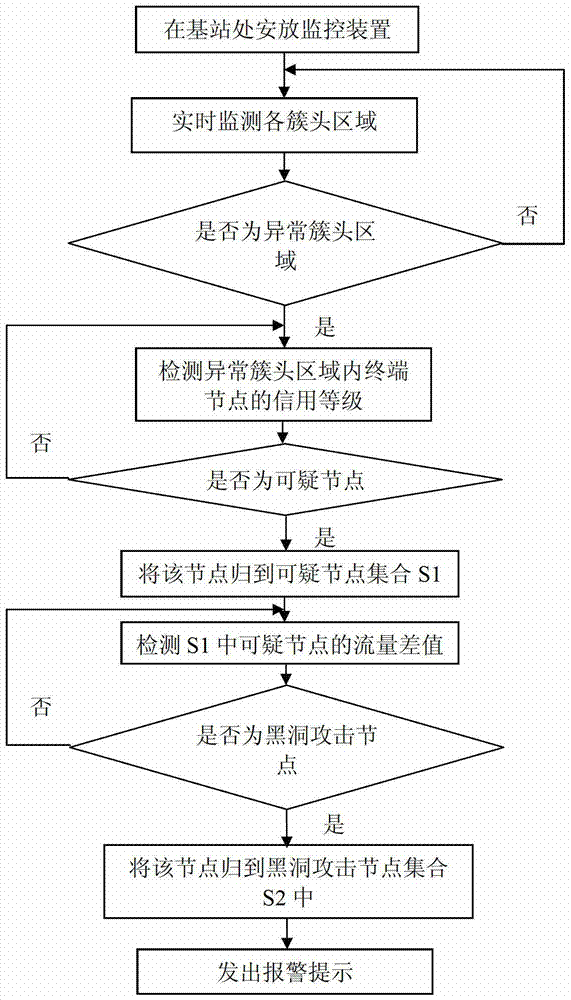
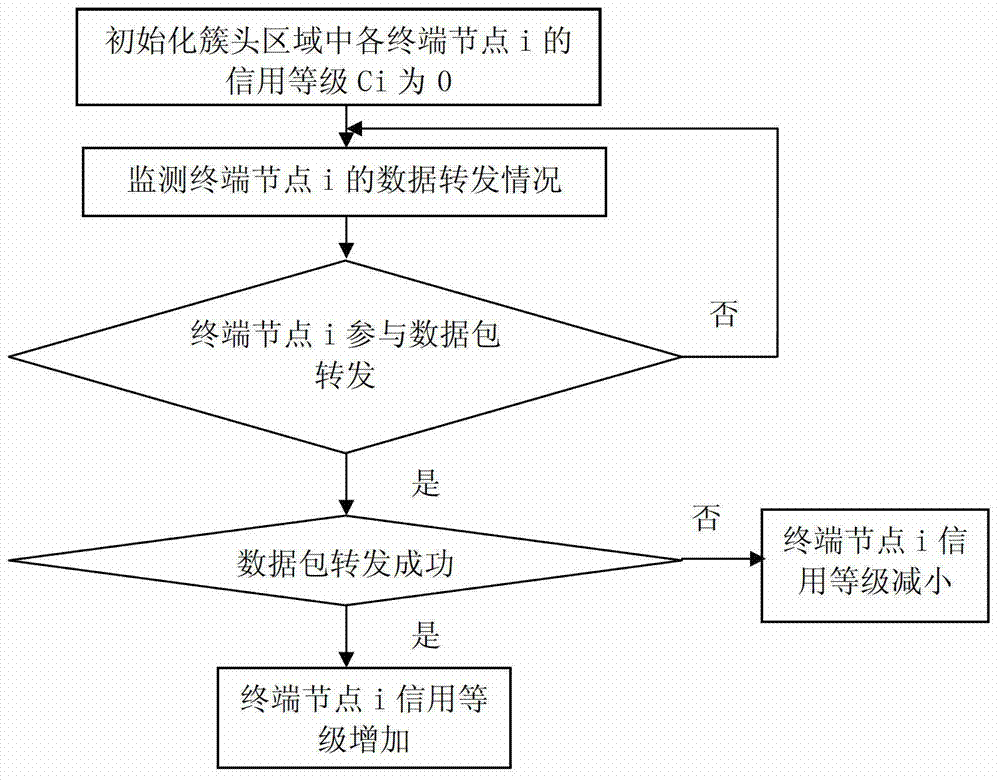
[0046] Such as figure 2 As shown, a black hole attack detection method in a clustered self-organizing network according to the present invention, the method comprises the following steps:
[0047] Step 1: Instal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com