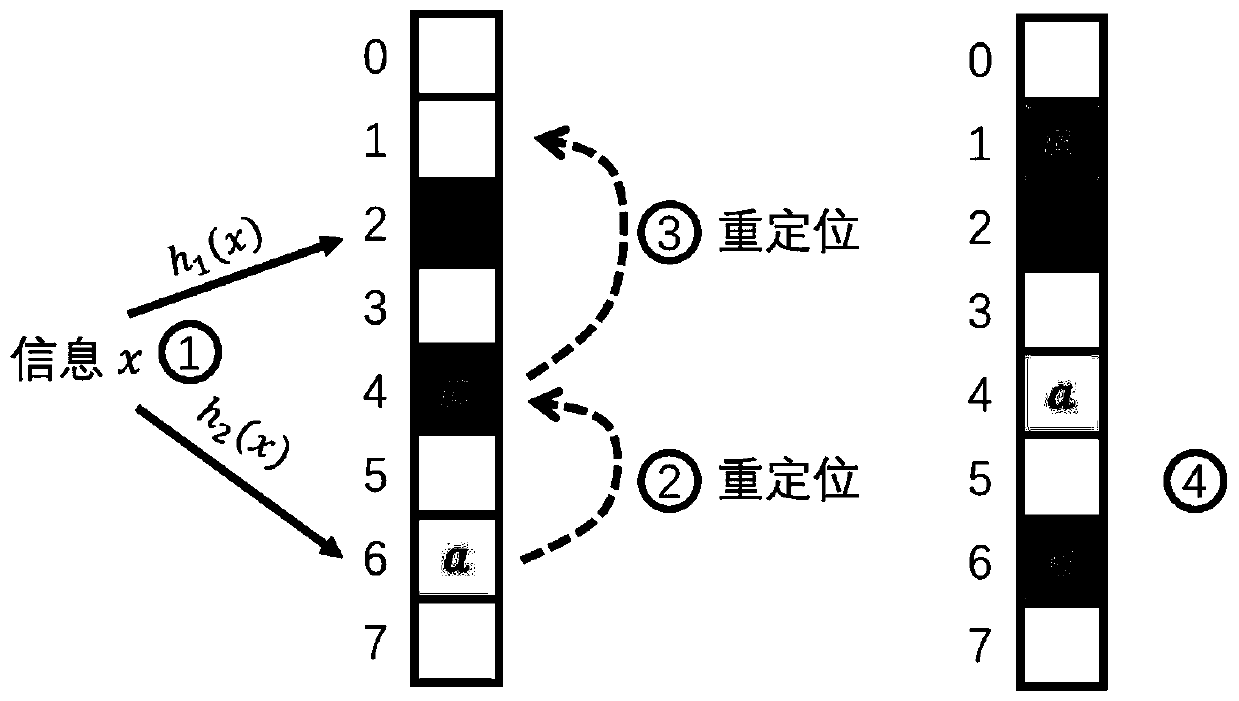
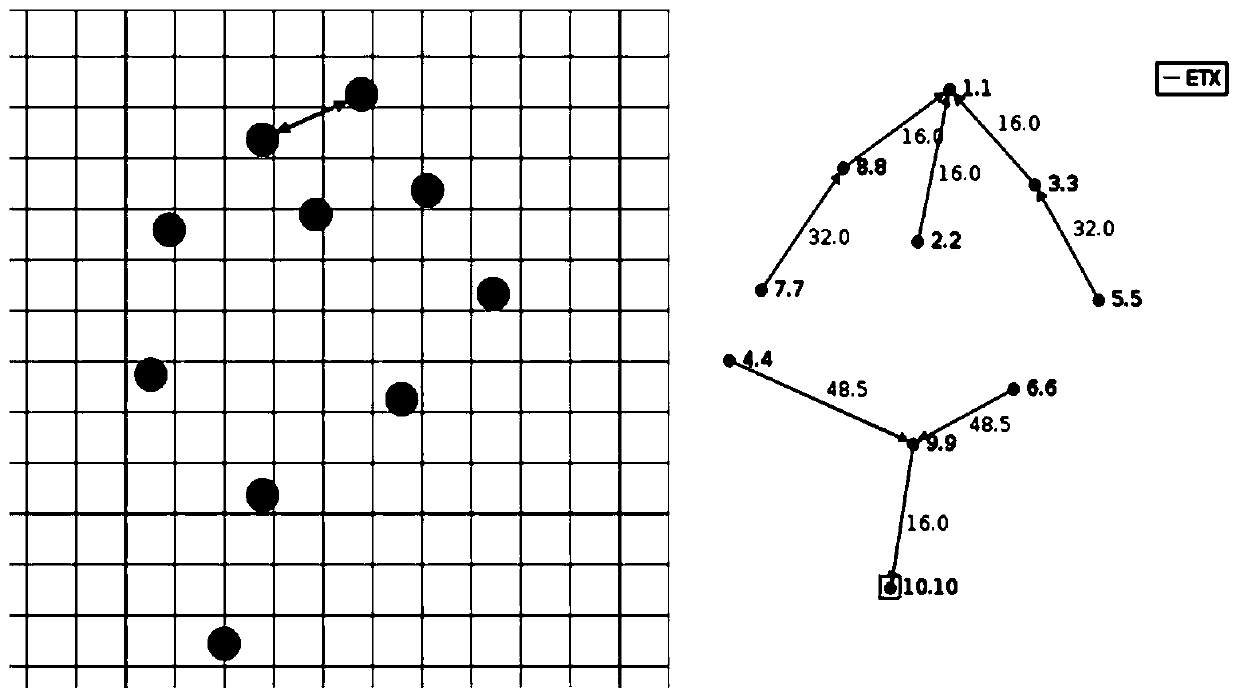
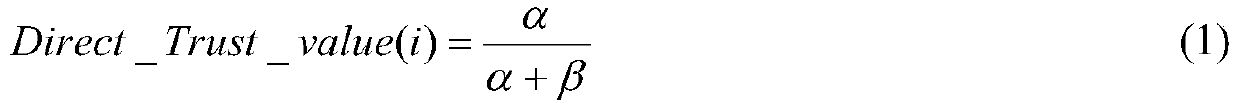Patents
Literature
30 results about "Packet drop attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
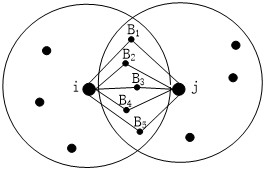
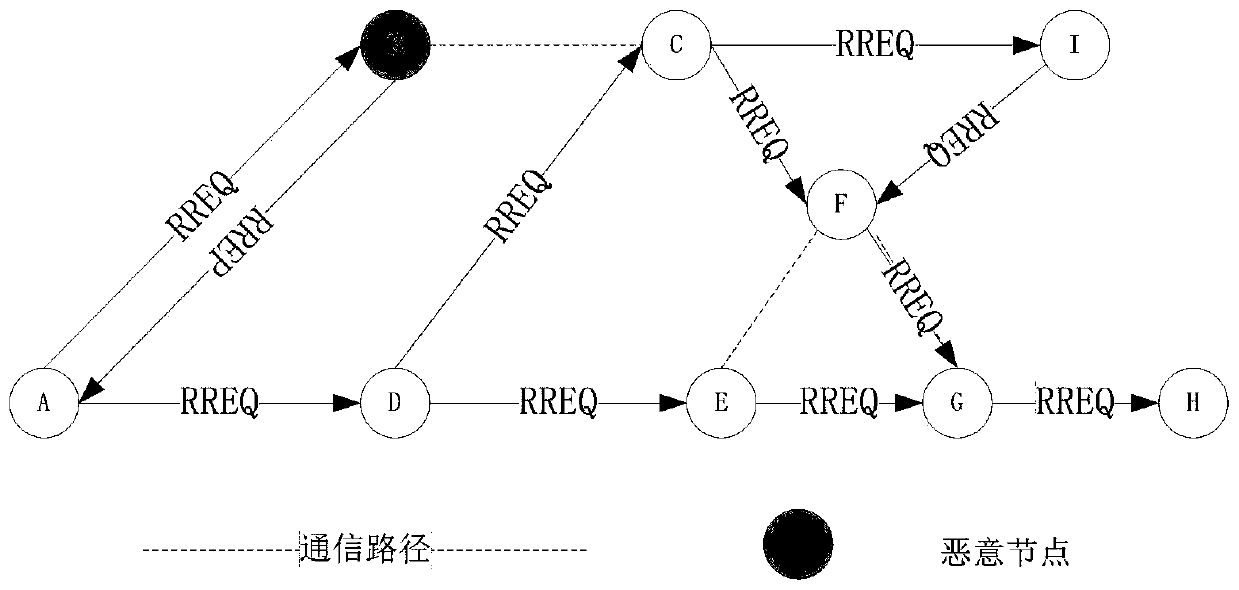
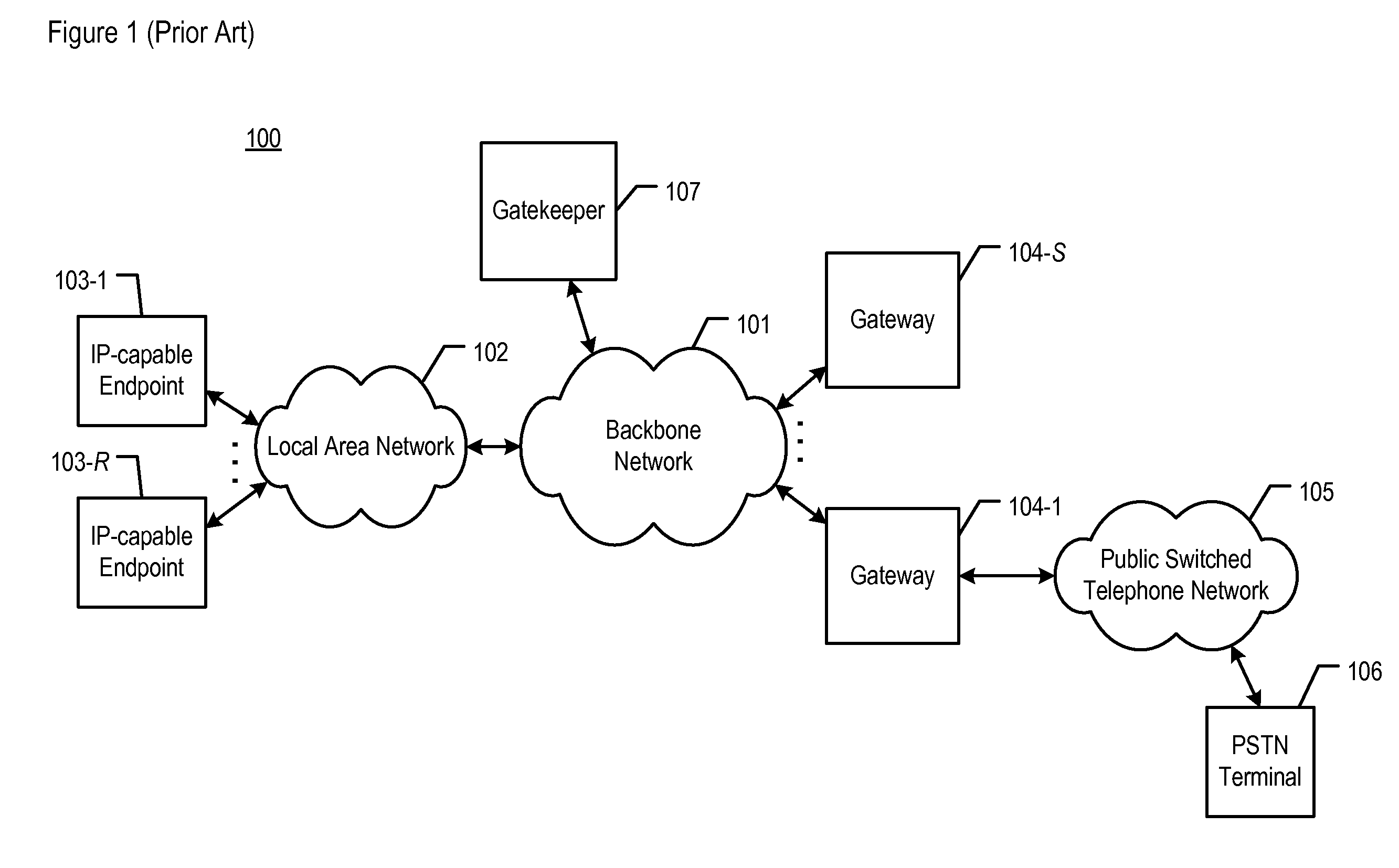
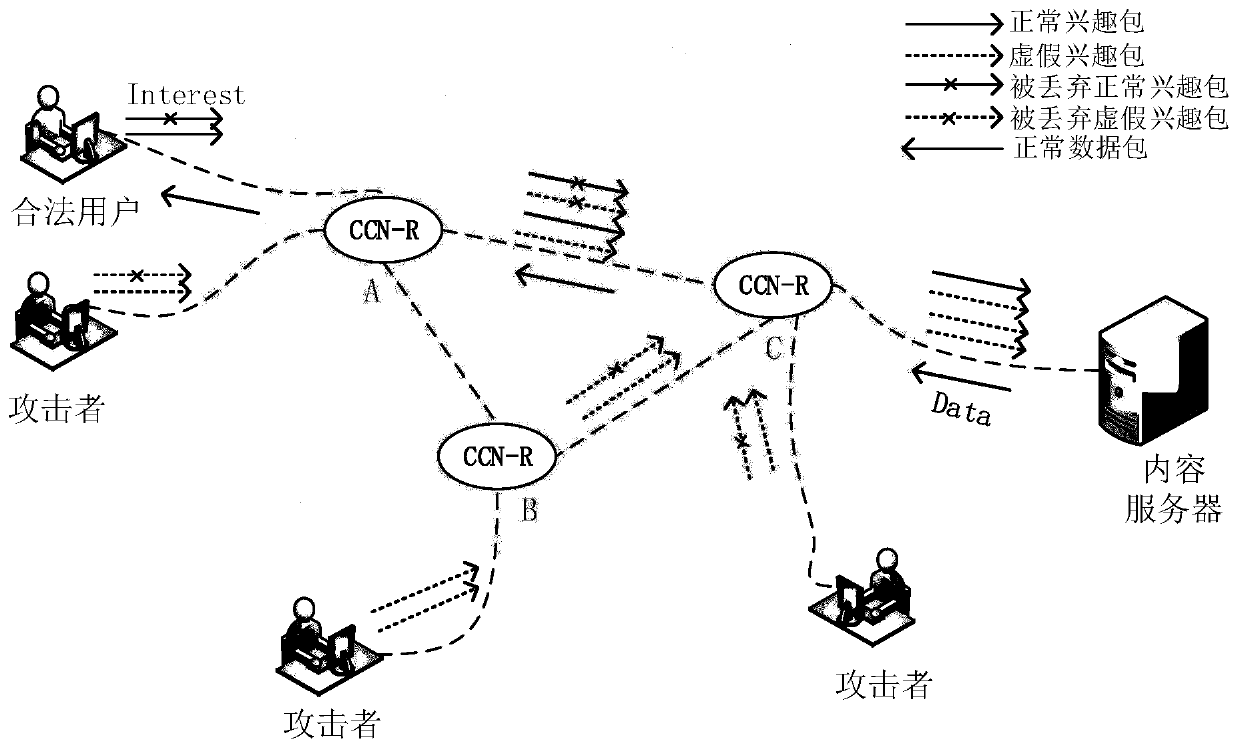
In computer networking, a packet drop attack or blackhole attack is a type of denial-of-service attack in which a router that is supposed to relay packets instead discards them. This usually occurs from a router becoming compromised from a number of different causes. One cause mentioned in research is through a denial-of-service attack on the router using a known DDoS tool. Because packets are routinely dropped from a lossy network, the packet drop attack is very hard to detect and prevent.
Wireless QoS by hardware packet sizing, data rate modulation, and transmit power controlling based on the accumulated packet drop rate
InactiveUS20070165526A1Improve data transfer rateLow data rateEnergy efficient ICTFrequency-division multiplex detailsTransmitted powerData rate
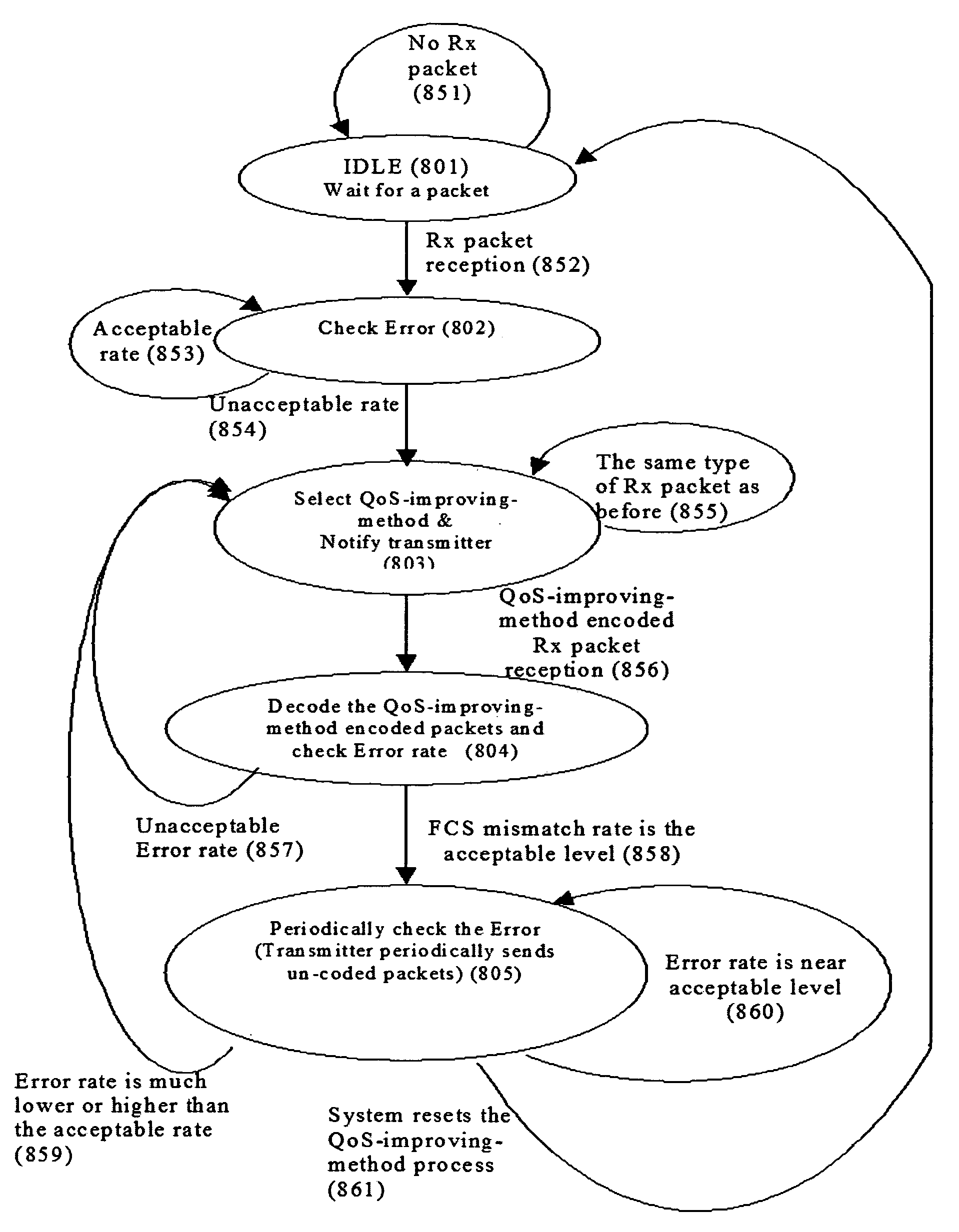
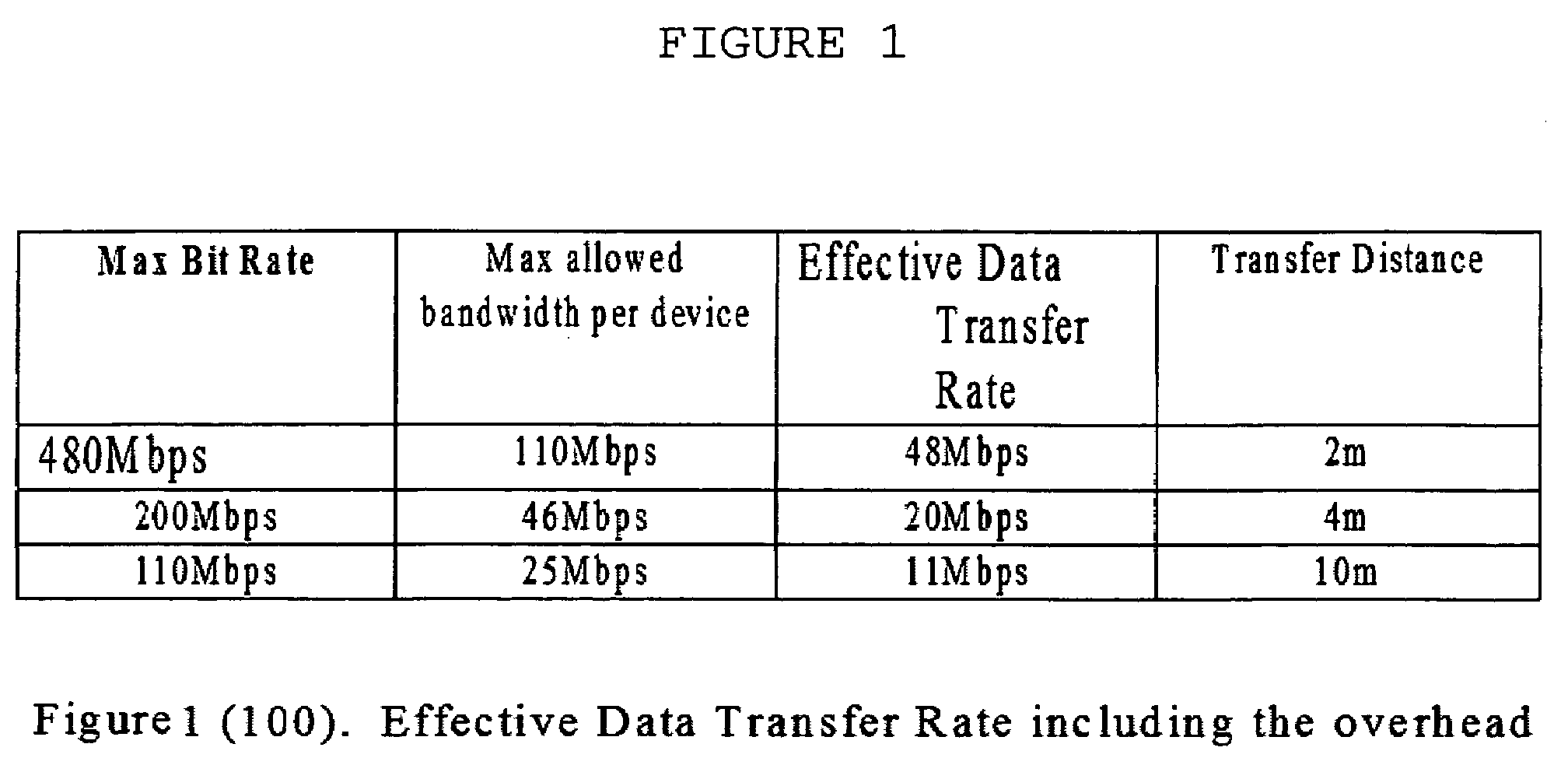
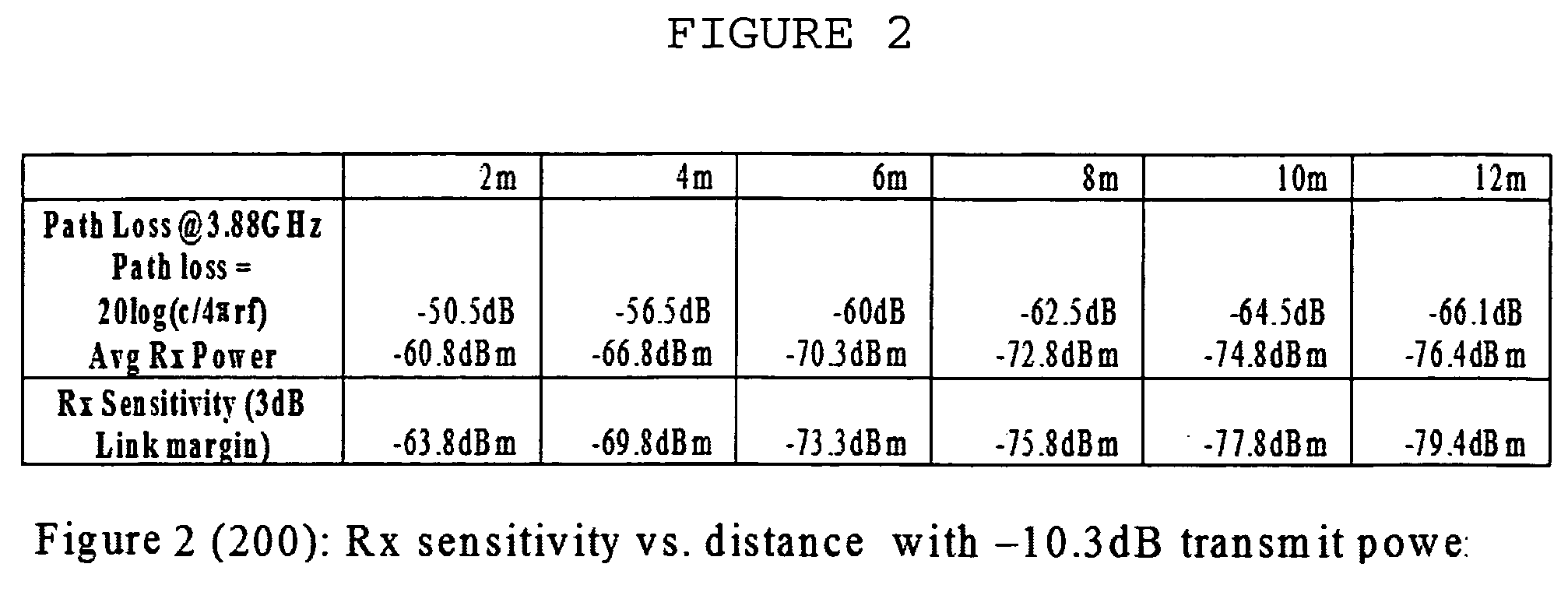
Two methods to improve the QoS. These methods can be applied individually or together. The first method is a packet sizing method, which is based on the Bit Error rate as well as the packet drop rate. The second method is a data transmit rate modulation method. The proposed methods in this invention, unlike the packet size reduction method that is in the WiMedia specification, enables the MAC to reduce and increase the packet size and the data transmit rate by working with the upper layer controller to maximize the data transfer rate, the transmitter power, and to minimize the packet drop rate.
Owner:LEE HYUN
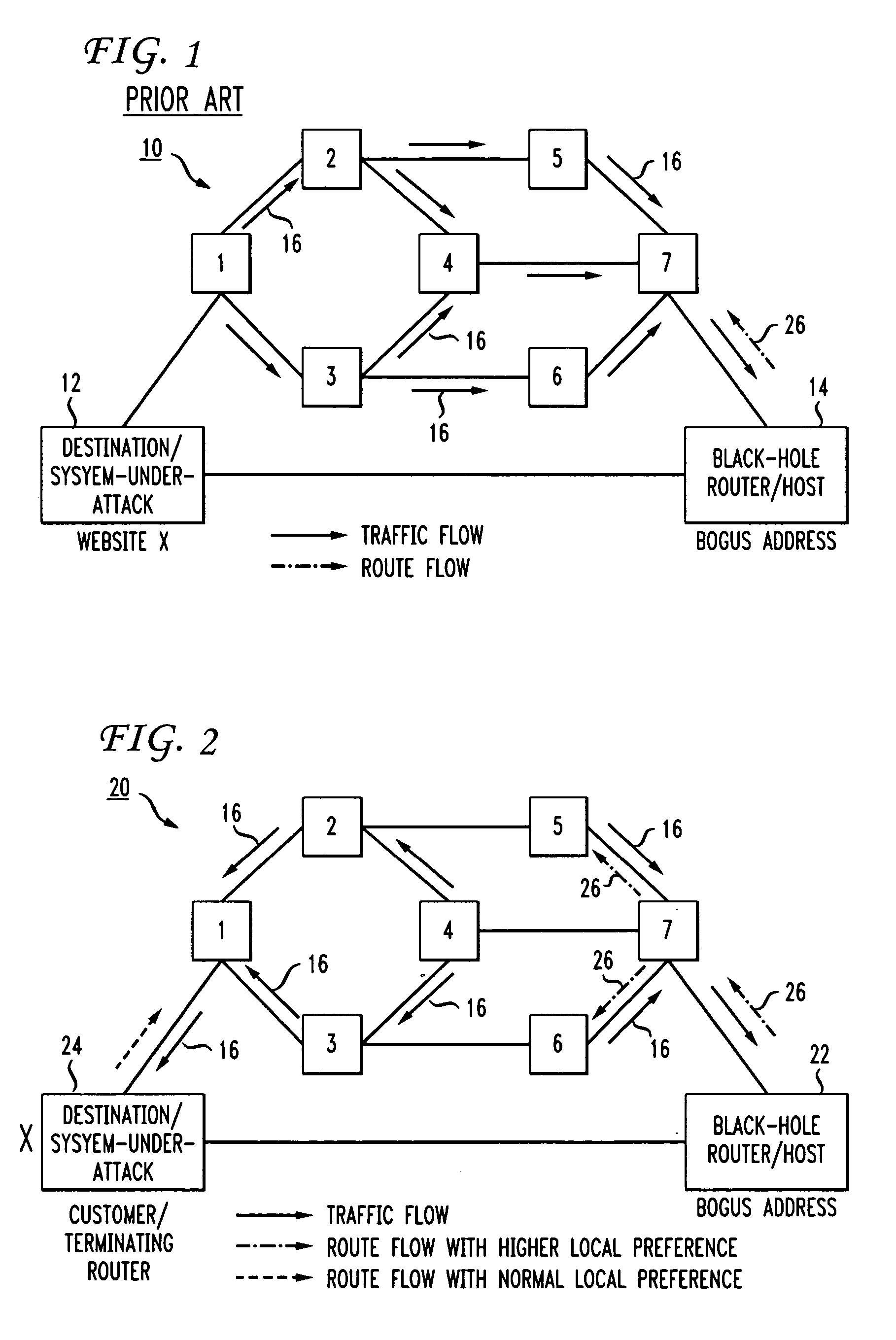
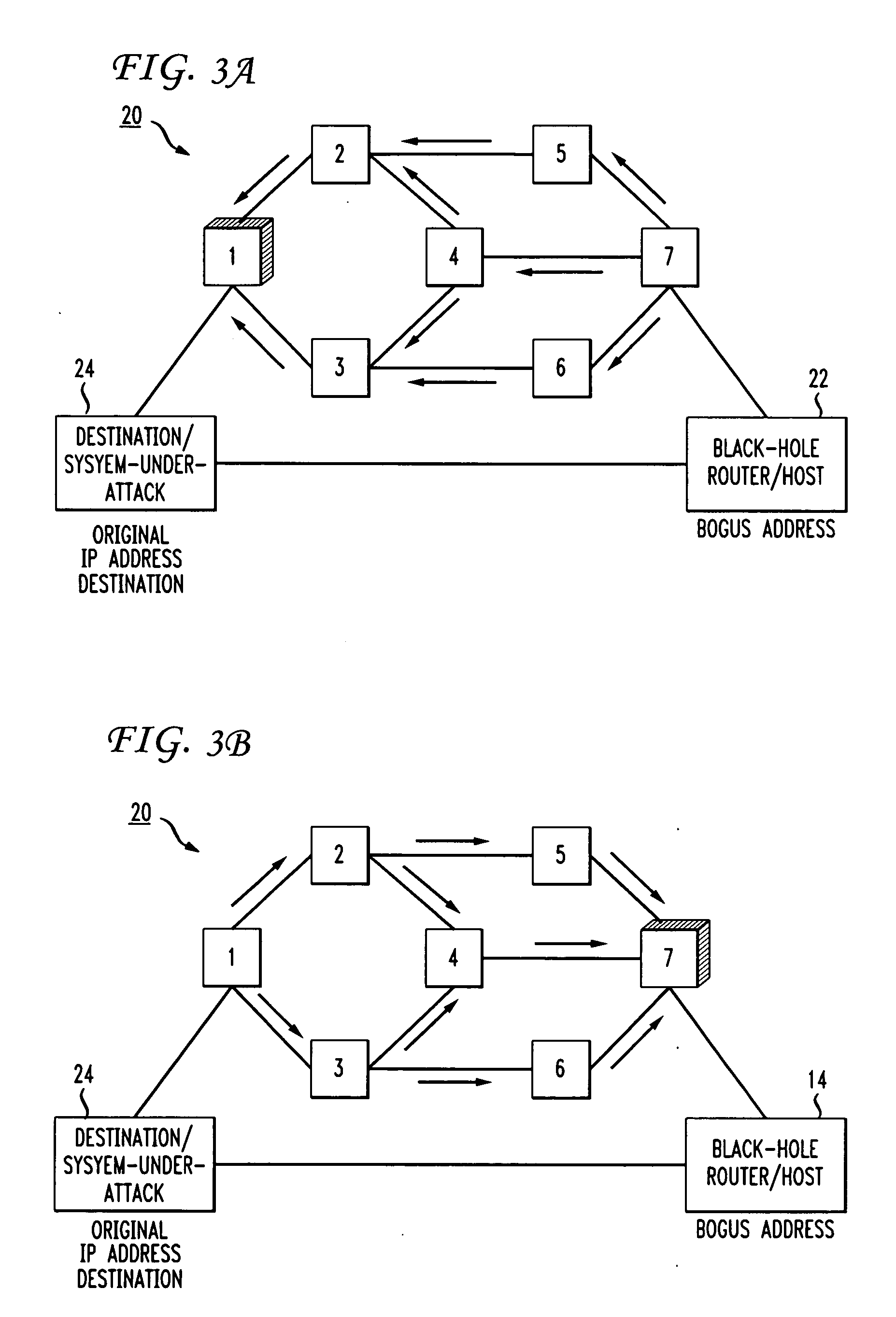
Distributed denial-of-service attack mitigation by selective black-holing in IP networks
ActiveUS20060031575A1Sure easyData switching by path configurationMultiple digital computer combinationsIp addressThe Internet
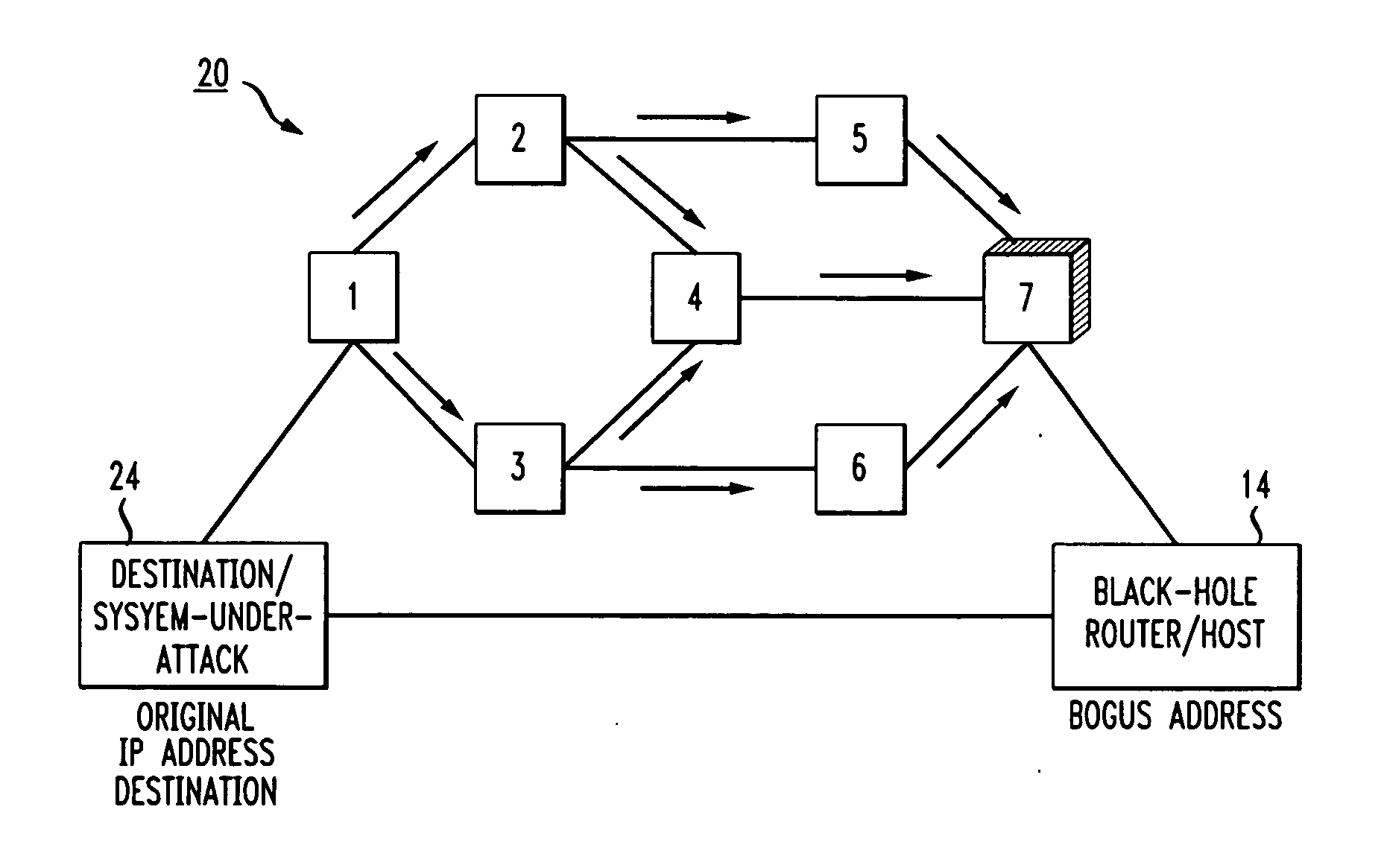
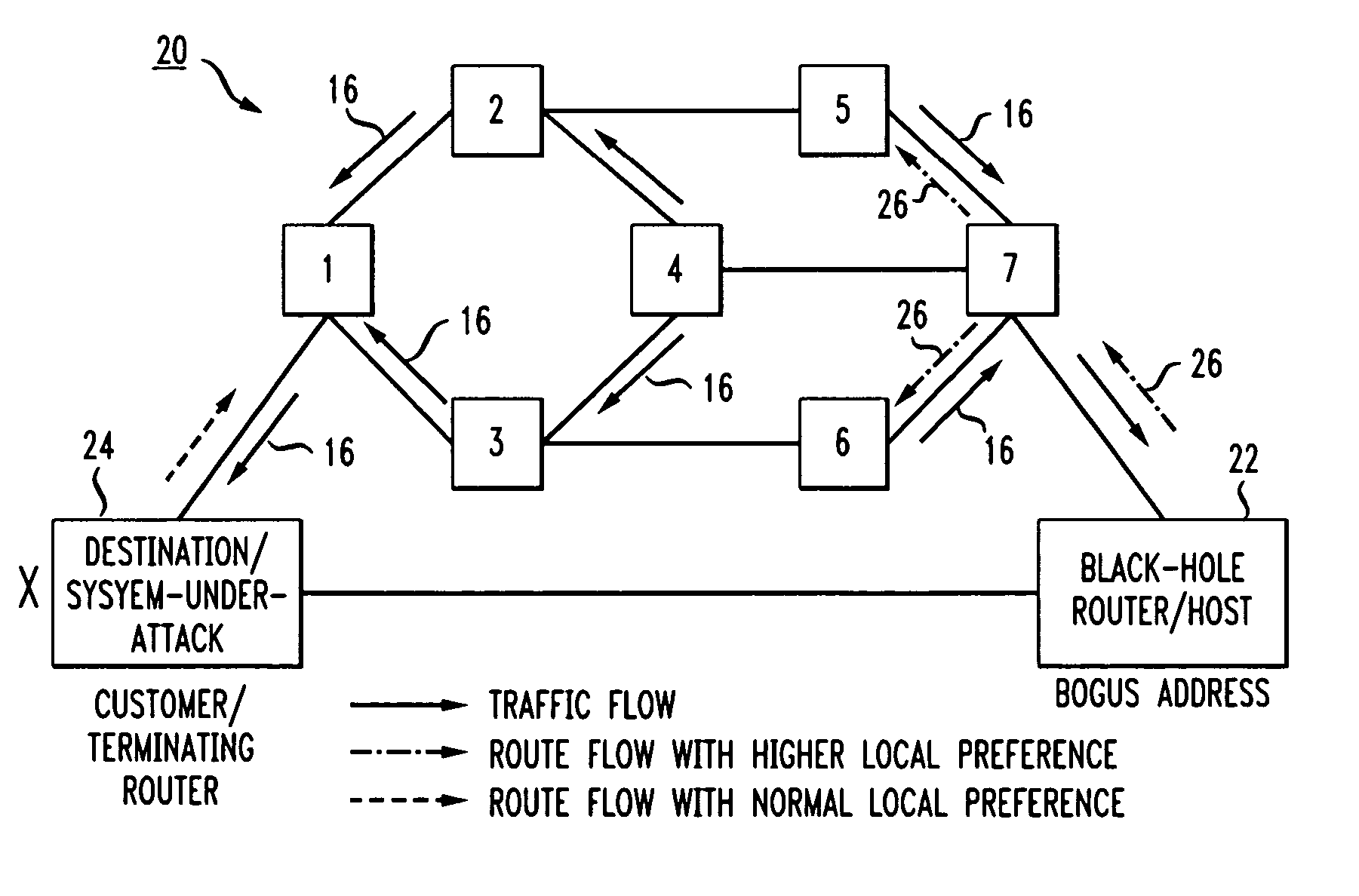
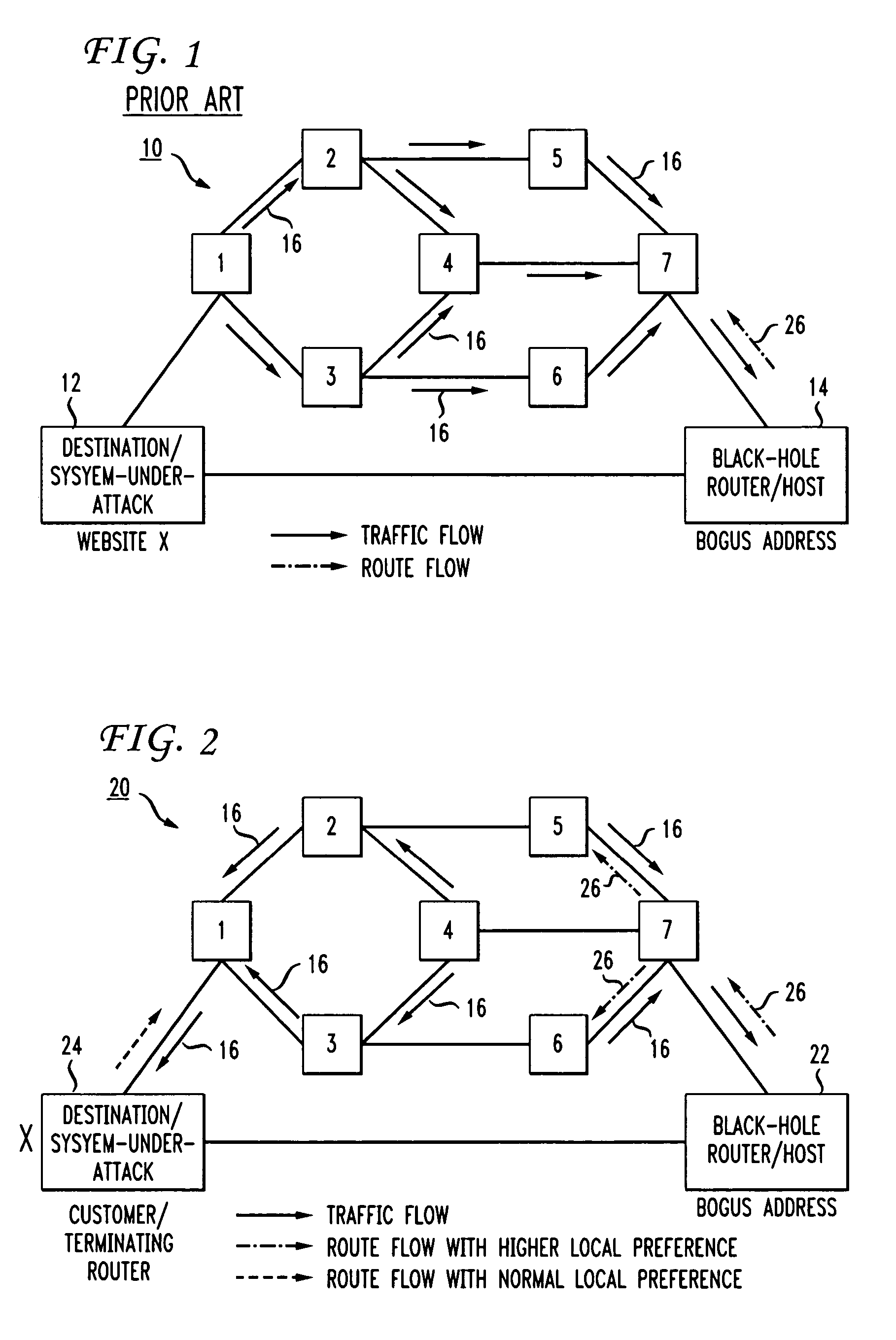
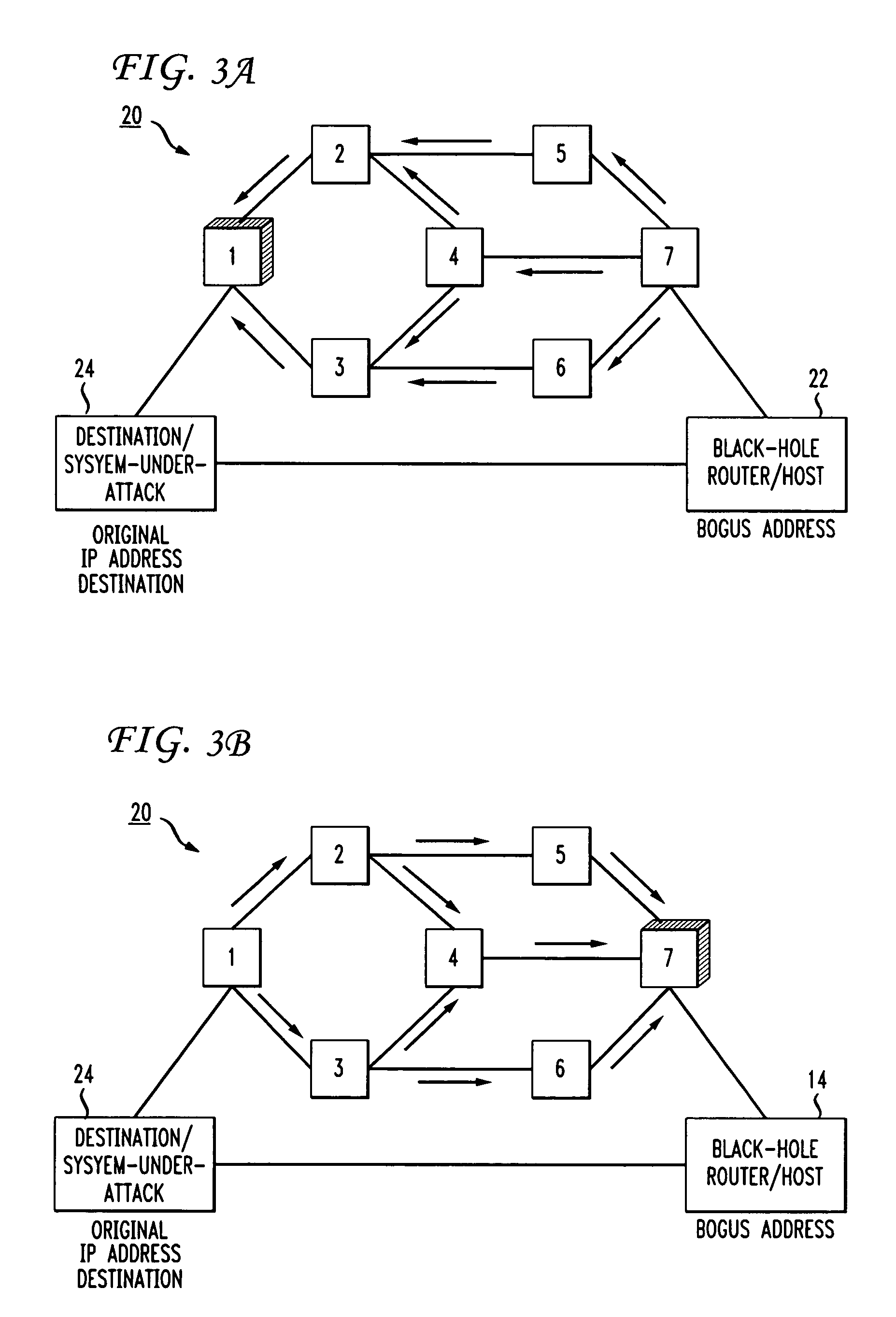
In an IP network during a DDoS attack on a website or other internet entity having an IP address, selective black-holing of attack traffic is performed such that some of the traffic destined for the IP address under attack continues to go to the IP address under attack while other traffic, destined for the same IP address is, rerouted via BGP sessions to a black-hole router. Such a selective black-holing scheme can be used to allow some traffic to continue in route to the IP address under attack, while other traffic is diverted.
Owner:AT&T INTPROP I L P
Lightweight packet-drop detection for ad hoc networks
InactiveUS20100050258A1Memory loss protectionError detection/correctionComputer networkComputer science
Owner:NYTELL SOFTWARE LLC
Ad Hoc network security trust method based on reference node strategy
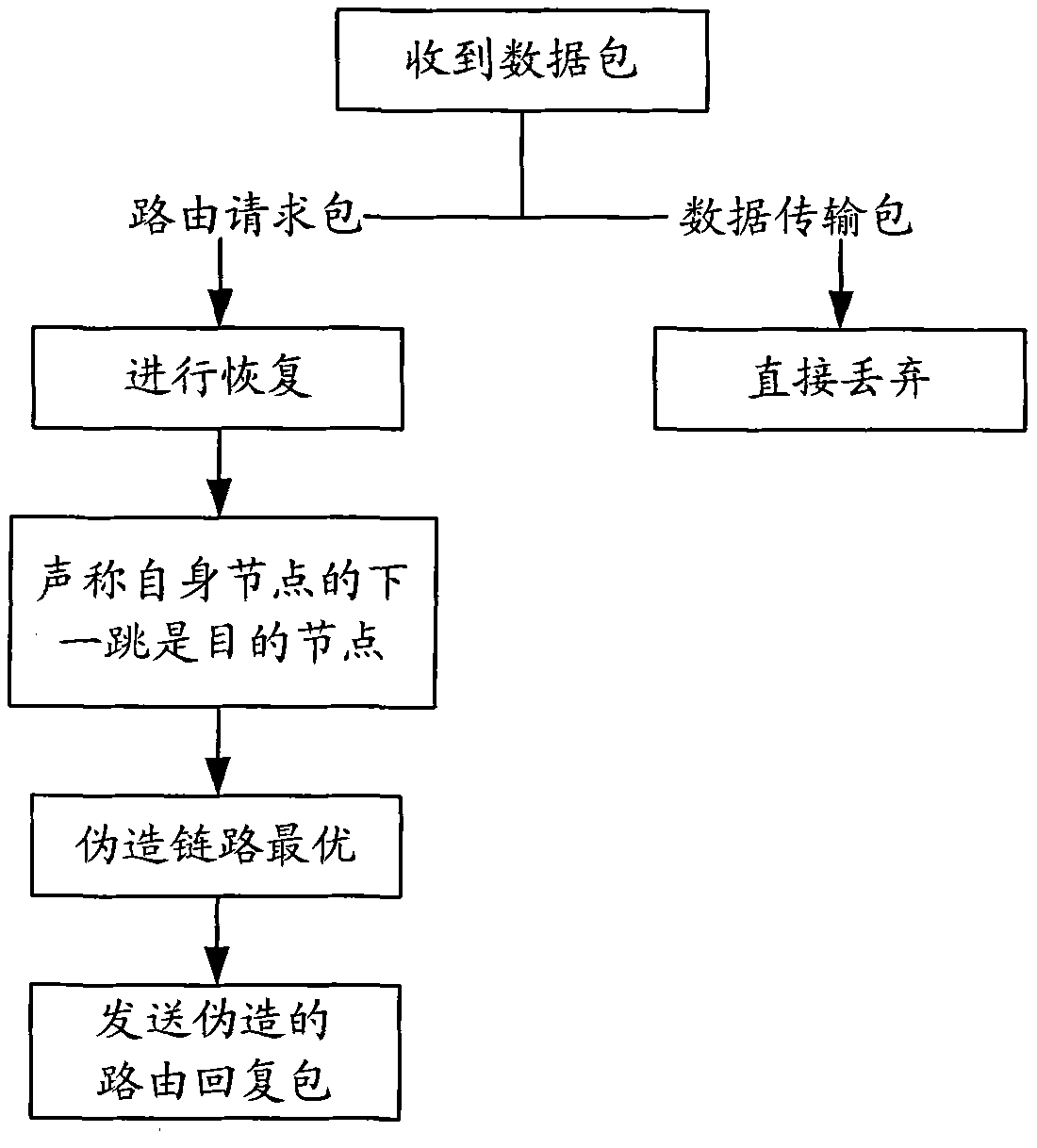
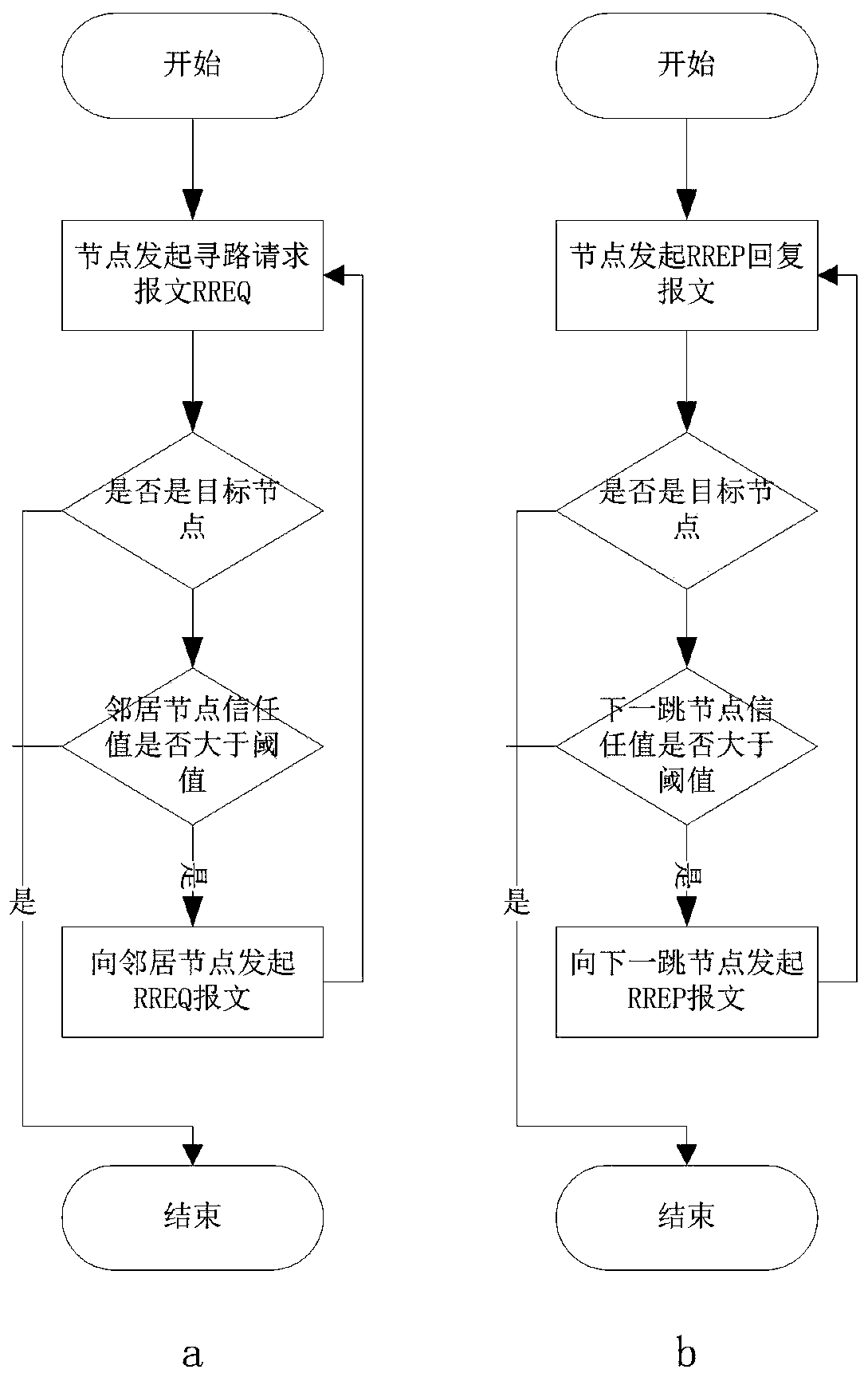
The invention relates to an Ad Hoc network security trust method based on a reference node strategy and belongs to the field of network security. The method specifically comprises the following stepsof computing a trust value of each node through a trust model, sending the trust value to a trust value statistical node, making the trust value statistical node count a weighted trust value of each node, updating a reference node and the trust value statistical node, and lastly, initiating the reference node strategy through the reference node. The method has the advantages that a black hole attack node in the Ad Hoc network can be quickly discovered, and meanwhile, the method has a good defense effect on a way of hybrid of a data message attack and the black hole attack; and the method has strong expandability and adaptability.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
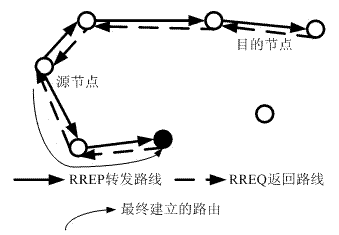
Routing method of wireless ad hoc network
InactiveCN102333314AEfficient identificationAvoid routing black holesSecurity arrangementTelecommunicationsNetwork packet
The invention relates to a routing method of a wireless ad hoc network and belongs to the technical field of networks. According to the routing method, the existing AODV (Ad hoc On-Demand Distance Vector Routing) protocol is improved, and the routing method comprises the following steps of: firstly, sending an explorer packet rather than data after a source node for sending data receives rout response grouping of other intermediate nodes of a non-destination node, requiring the response of a destination node, if the response of the destination node is received, considering that no routing black hole exists on the route, and then sending data; and if the sending node does not receive the response of the destination node, giving up the route and reselecting other routes. In the invention, only by simply modifying the AODV protocol, the purpose of preventing the attack of the conventional route black hole in the wireless ad hoc network can be realized, and the safety of the wireless ad hoc network can be improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
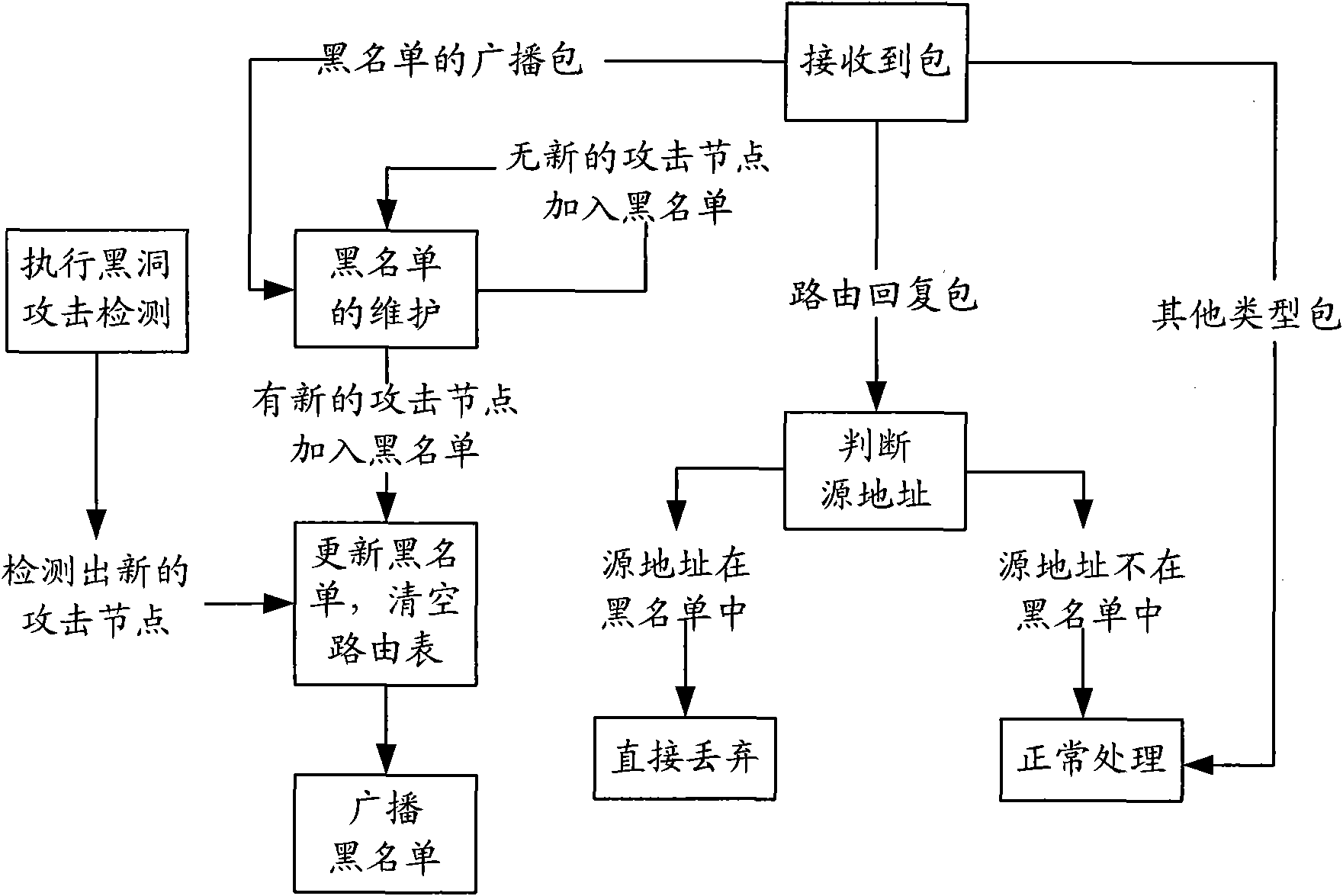
Method for detecting black hole attack in wireless ad hoc network
InactiveCN101895889AReduce lossesNetwork topologiesSecurity arrangementBlack listSelf-organizing network
The invention discloses a method for detecting a black hole attack in a wireless ad hoc network. The method for detecting the black hole attack is respectively carried out at each node of the network independently, and comprises the following steps of: detecting behaviors of neighbor nodes in a one-hop range of a wireless signal effective transmission distance of the node, namely collecting and analyzing the behaviors of the neighbor nodes around the node; performing analysis and statistics on the behaviors of the neighbor nodes, wherein if the statistic data of a certain neighbor node is discovered to be abnormal, the neighbor node is considered to be the black hole attacked node; and once the black hole attacked node is detected, listing the black hole attacked node in a blacklist, broadcasting the black hole attacked node, and isolating the attacked node to reduce the loss due to the black hole attack to the minimum. The invention originally provides a concrete method for detecting the black hole attacked node, and the method can reduce the attack caused loss to the minimum by taking precautionary measures immediately after the black hole attacked node is detected.
Owner:SHENZHEN ZAXID TECH INDAL
Distributed denial-of-service attack mitigation by selective black-holing in IP networks
ActiveUS7444417B2Sure easyData switching by path configurationMultiple digital computer combinationsIp addressThe Internet
In an IP network during a DDoS attack on a website or other internet entity having an IP address, selective black-holing of attack traffic is performed such that some of the traffic destined for the IP address under attack continues to go to the IP address under attack while other traffic, destined for the same IP address is, rerouted via BGP sessions to a black-hole router. Such a selective black-holing scheme can be used to allow some traffic to continue in route to the IP address under attack, while other traffic is diverted.
Owner:AT&T INTPROP II L P
Black hole attack detection and tracking method based on doubtful degree accumulation
ActiveCN109756515ARealize TrackingContaining Black Hole AttacksTransmissionNetwork packetNetwork control
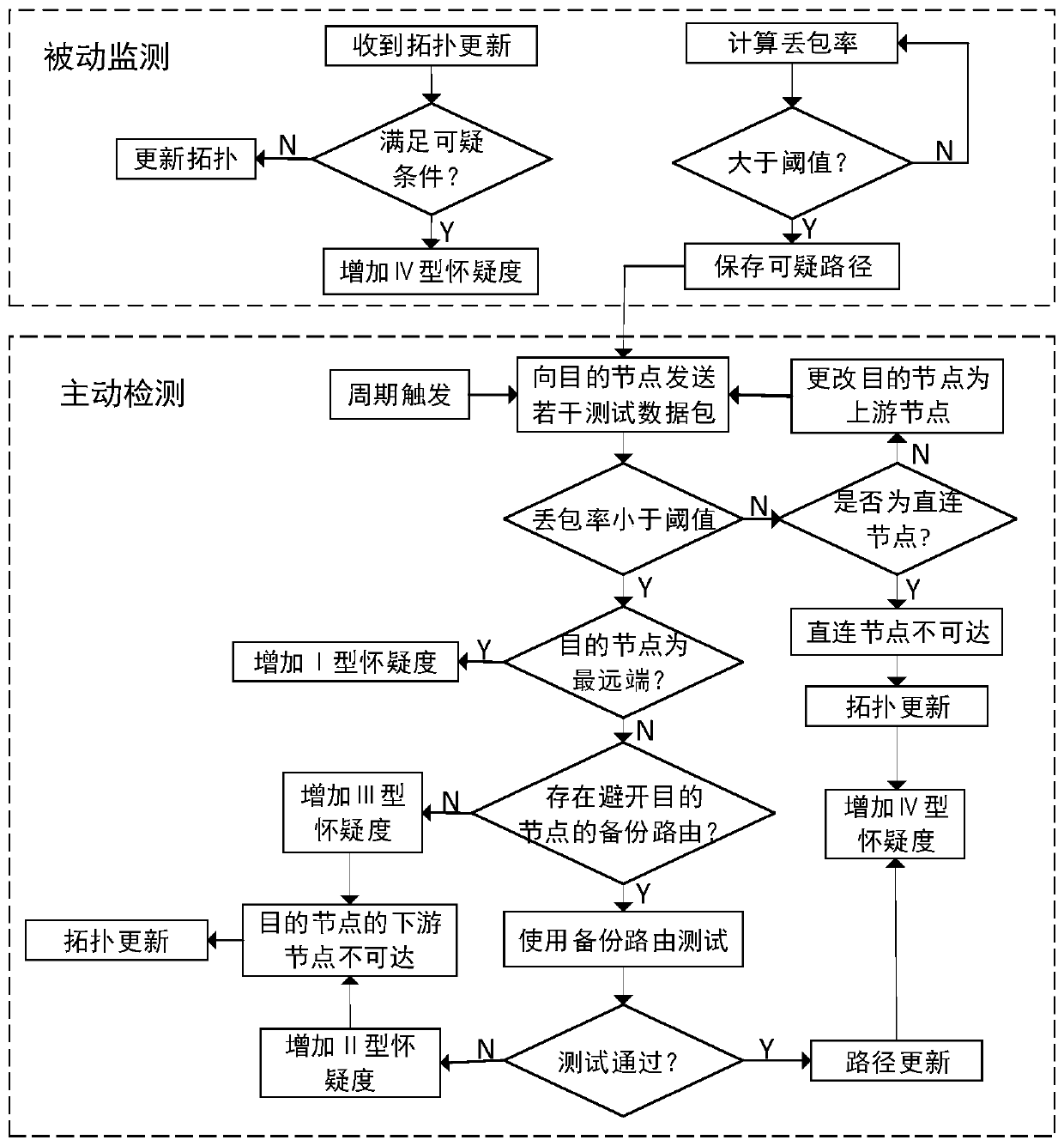
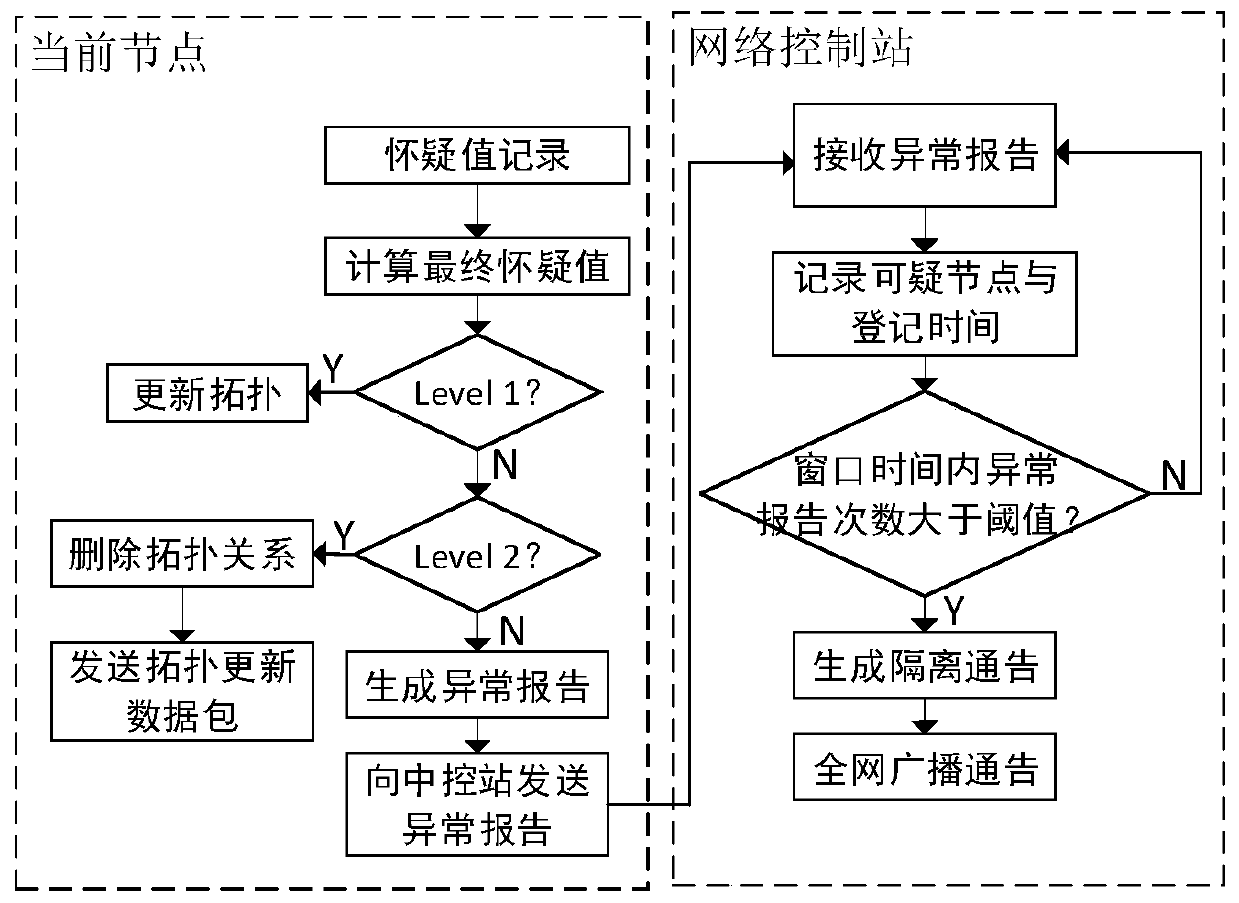
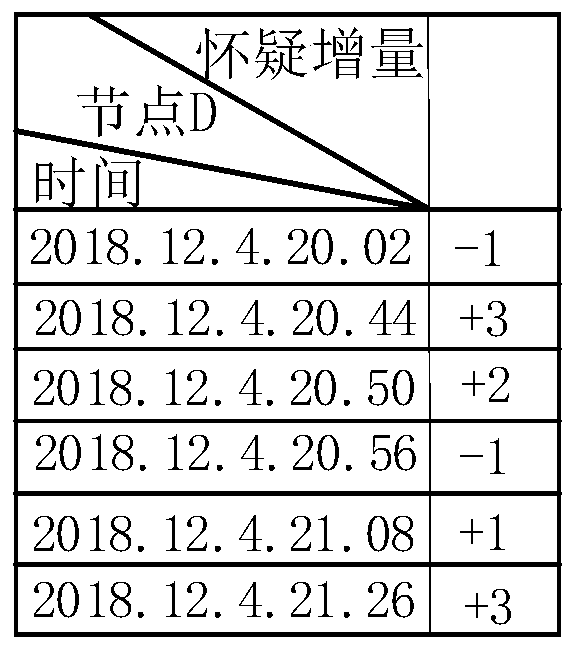
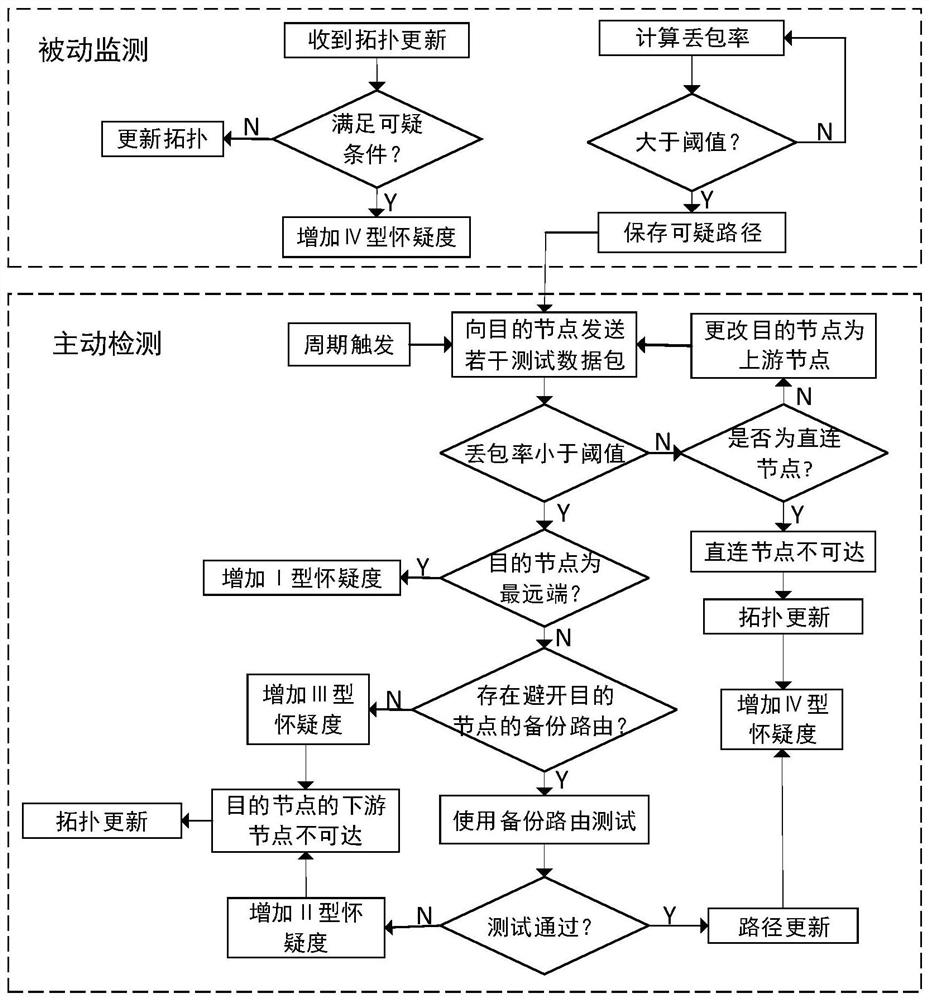
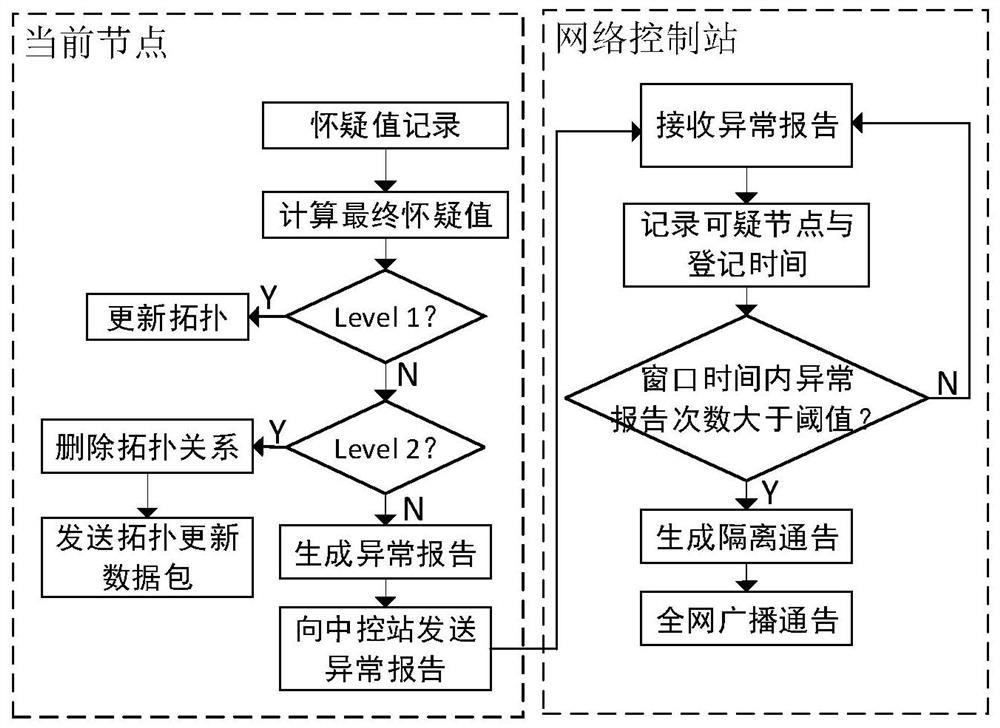
The invention belongs to the field of mobile ad hoc network routing security, and discloses a black hole attack detection and tracking method based on doubtful accumulation. According to the method, in a detection period, a passive monitoring mode is adopted, a node detects whether current topology update meets a suspicious condition, and if a data packet of the topology update meets the suspicious condition, the node adds a IV-type suspicious degree to a reputation registration table corresponding to the suspicious node; The node monitors the packet loss rate in each routing path, and triggers active detection if the packet loss rate exceeds the threshold value; an active detection mode is aodpted to detect suspicious behaviors so as to determine a correspondingly increased doubtful value, and performing weighted calculation on credit changes at different moments according to a forgetting factor so as to obtain a final doubtful value; And according to the final doubtful value of the suspicious node, the network control station determines whether the suspicious node is a malicious node through analysis, and once the suspicious node is confirmed to be the malicious node, the networkcontrol station broadcasts the whole network so as to isolate the malicious node from the whole network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
SAODV optimization method capable of effectively fighting against black hole attacks
InactiveCN106658483AImprove reliabilityImprove securityNetwork topologiesTransmissionHash functionDigital signature
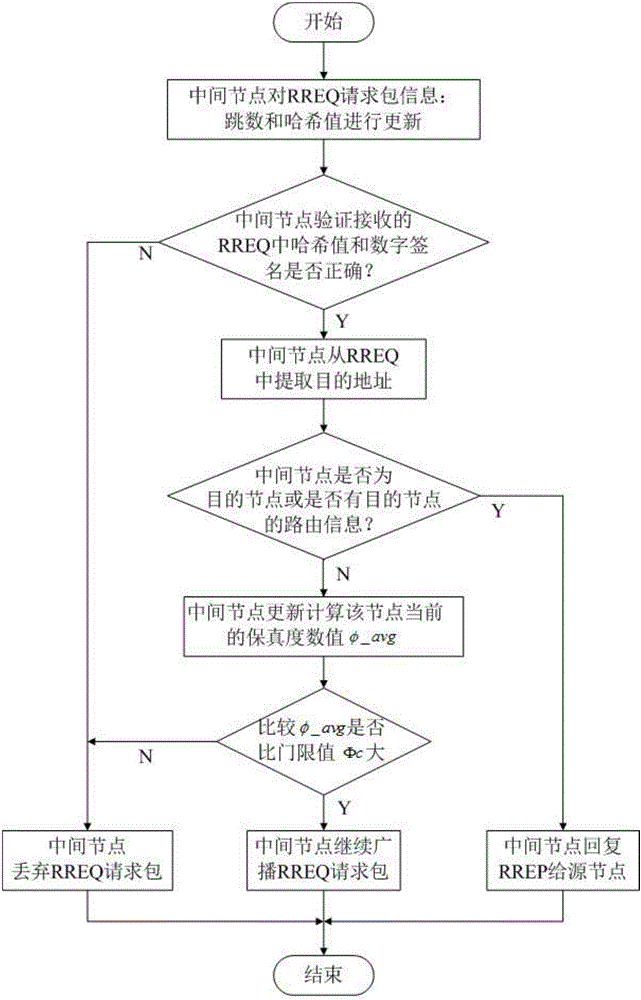
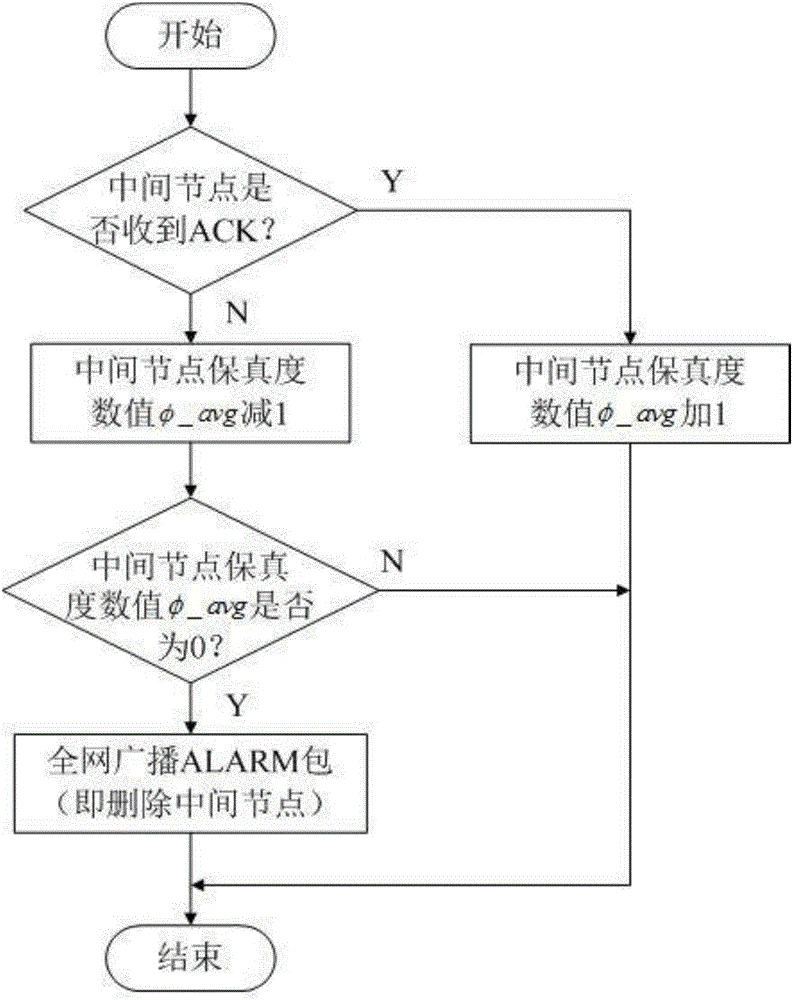
The invention discloses a SAODA optimization method capable of effectively fighting against black hole attacks. The technical schemes are as follows: based on the Hash function and the digital signature of a SAODA protocol, adding the concept of fidelity to the middle nodes to serve as the determination basis for their trustworthiness; during the route establishing and data transmitting stage, conducting dynamic calculation and constant updating to the fidelity of the nodes; and when the fidelity reaches a too small point, determining that the node is a black hole node and abandoning it. The method of the invention solves the problem that black hole attacks could not be solved in the existing SAODV protocol. With the method, the black hole node could be identified, therefore, making the network more reliable and more secure. The method is suitable for the Ad-Hoc network.
Owner:陕西尚品信息科技有限公司
Data forwarding method with black hole attack detection function
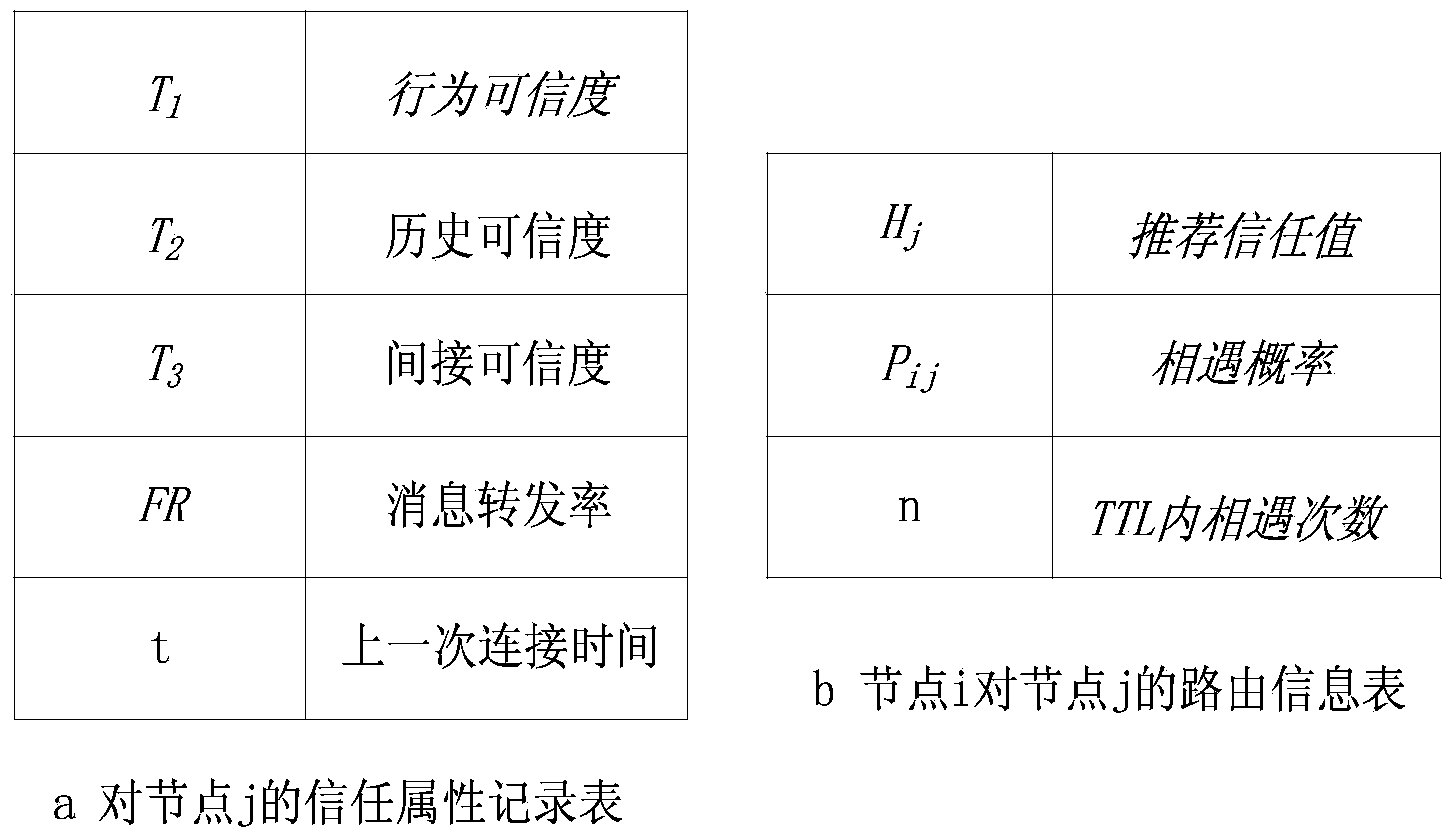
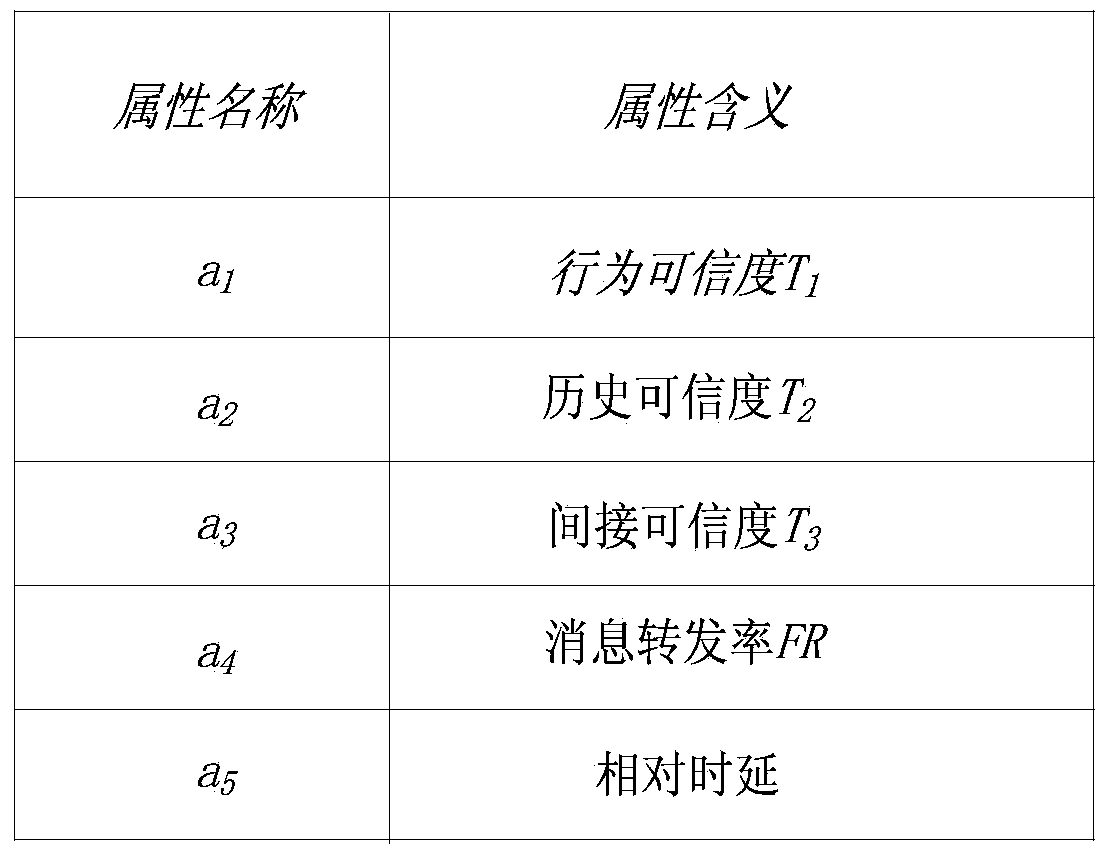
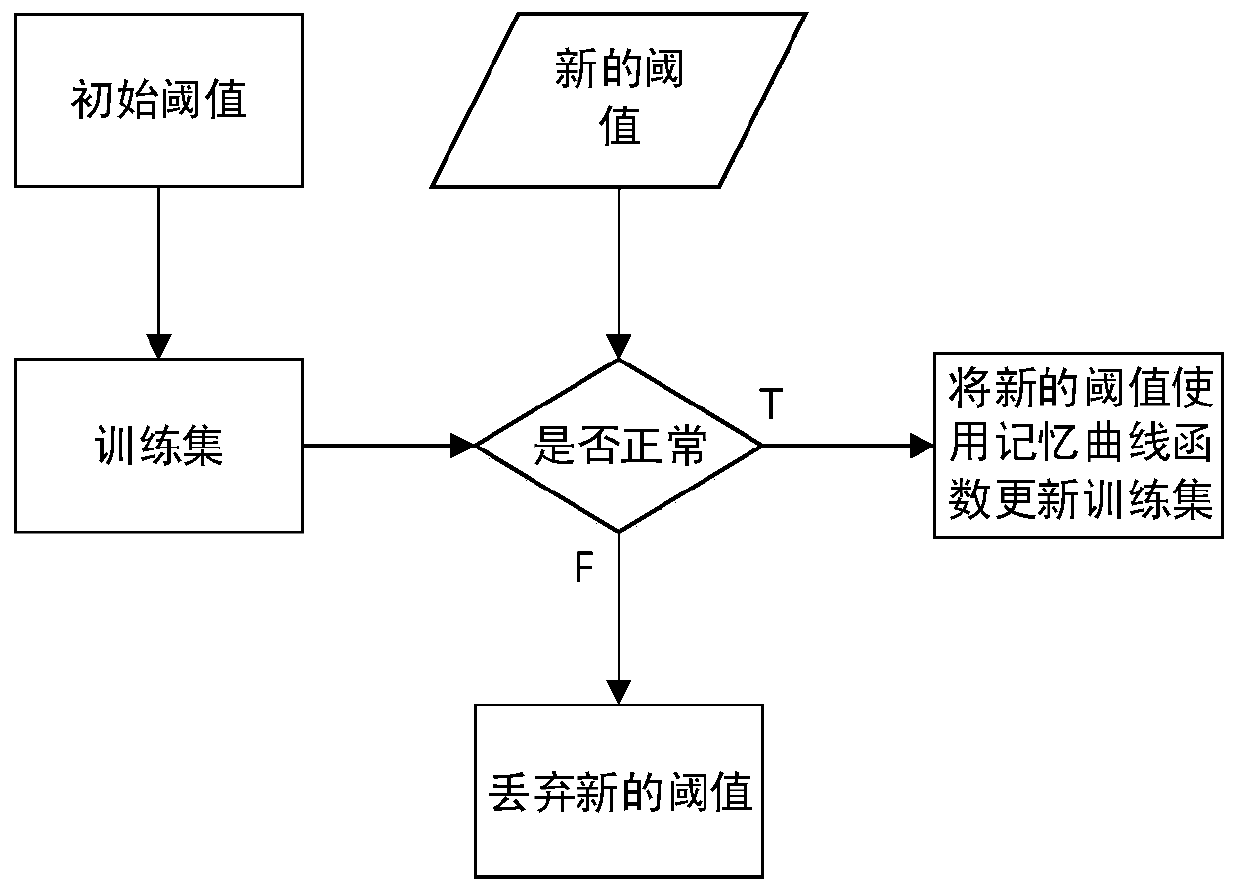
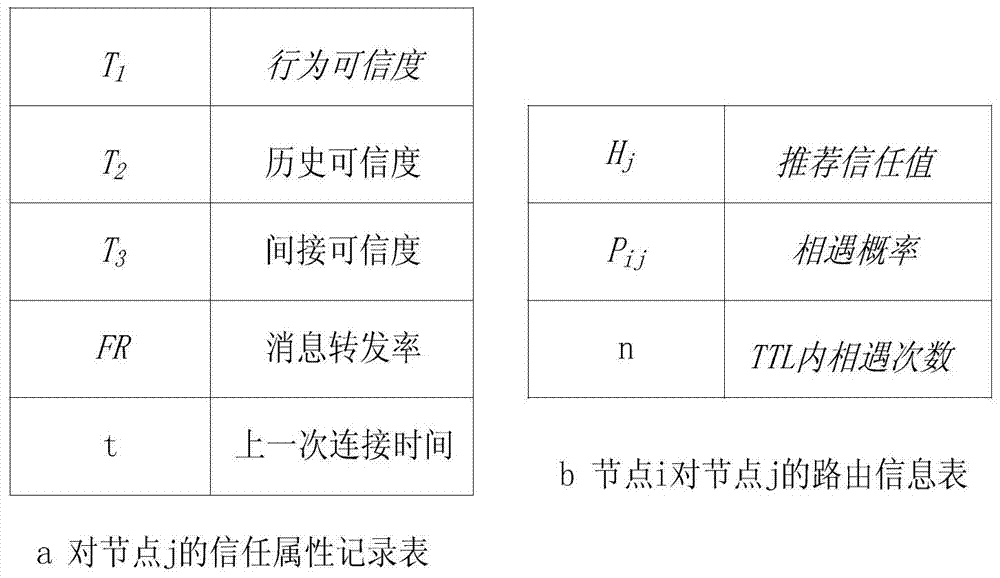
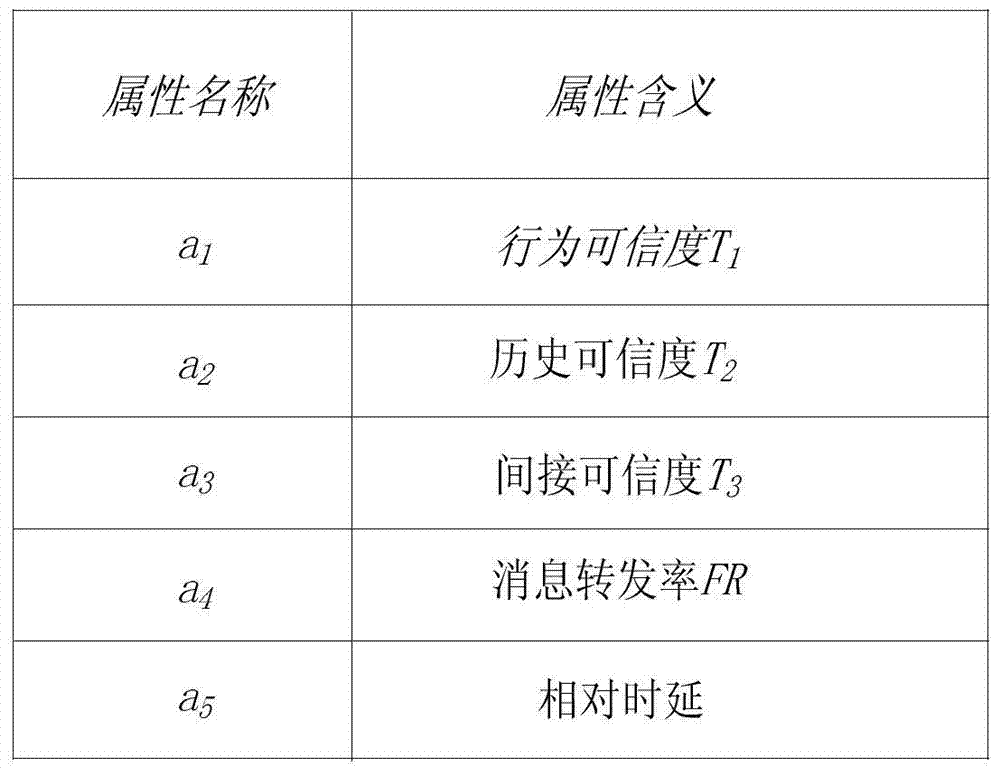
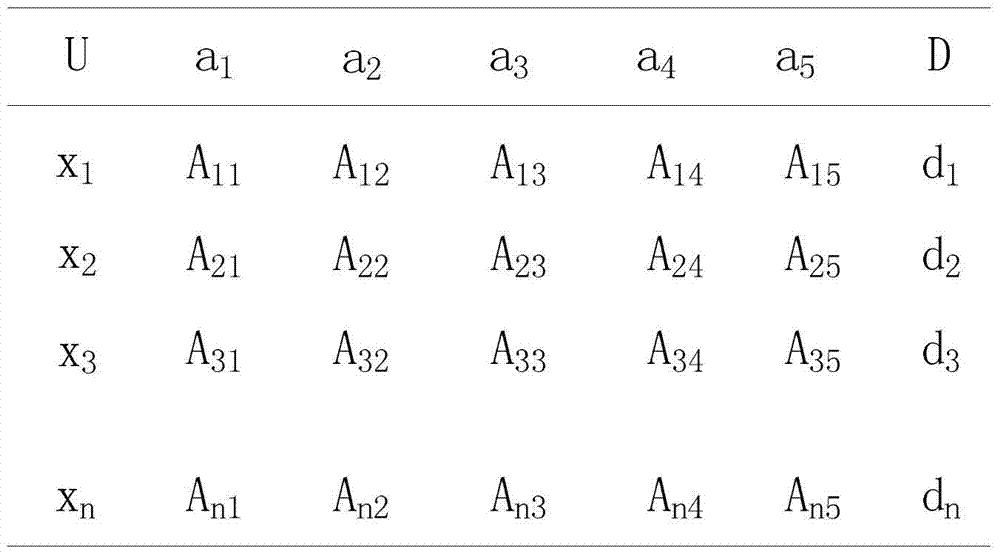
The invention relates to a data forwarding method with a black hole attack detection function and belongs to the technical field of opportunistic network trust management. In order to solve the problems that existing black hole attack detection methods in an opportunistic network only detect attack behaviors of black hole nodes in a certain aspect and lack relatively comprehensive evaluation on the black hole nodes and detection results are affected by certain changes of the network easily, during black hole attack detection, trust conditions of the nodes in all aspects are required to be considered comprehensively, comprehensive judgments are made, and an opportunistic network trust management method for comprehensively judging node credibility according to node experience in the aspects of the accuracy degree of routing information provided by to-be-detected nodes, the reliability of historic behaviors of the nodes, the forwarding capacity of the nodes for messages and the like is further designed. With the adoption of the method, the reliability of the nodes is accurately judged, and detection results cannot be affected by other factors in the network easily, so that the delivery rate of the messages in the network is increased, and the performance of the network is enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
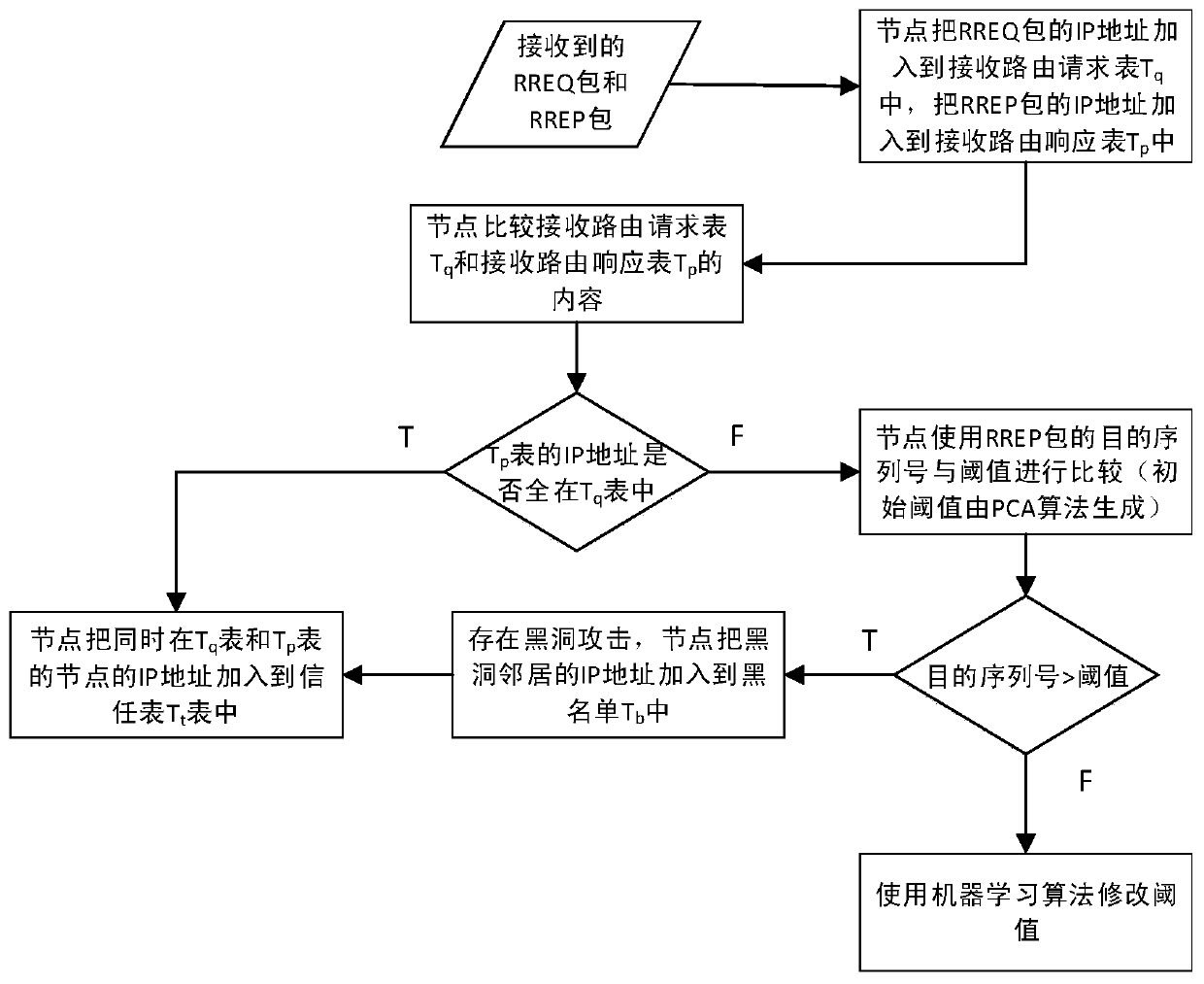
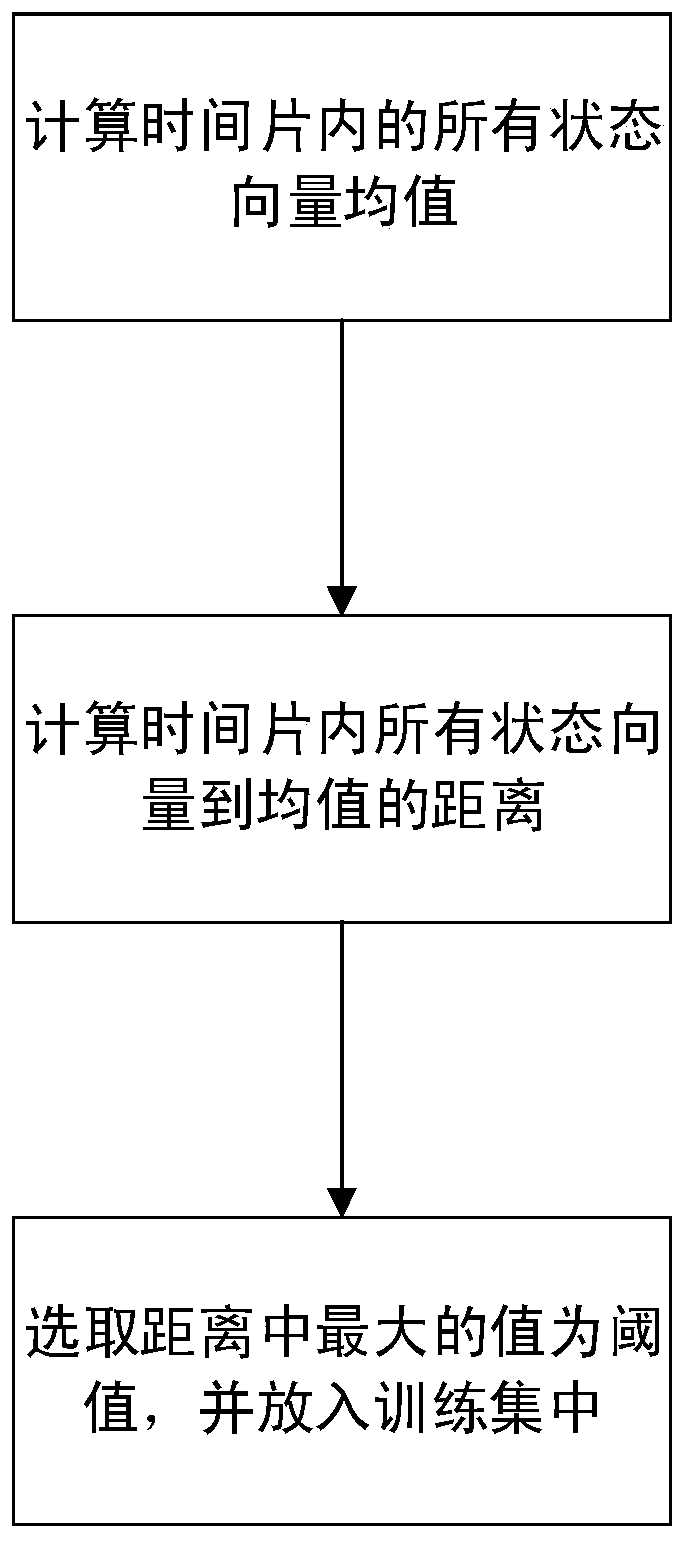
Black hole attack defense method applied to route discovery
ActiveCN106658482AEnsure safetyPrevent leakageNetwork topologiesTransmissionResponse tableThird party
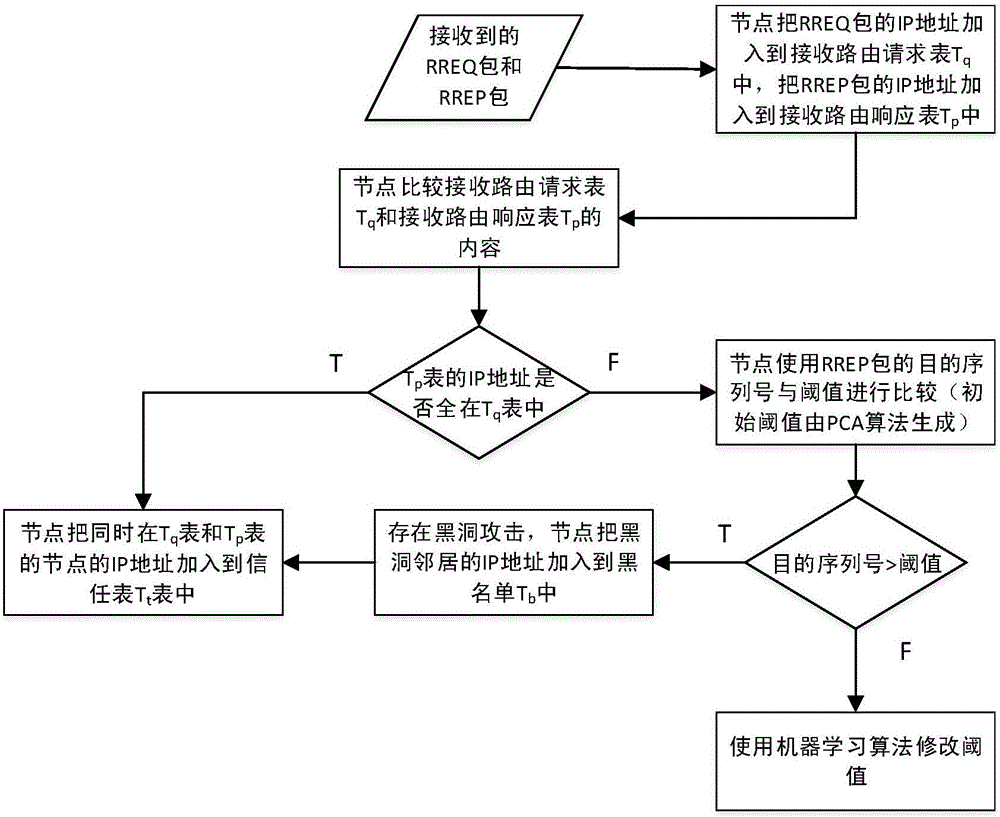
The invention discloses a black hole attack defense method applied to route discovery. The objective of the invention is to solve the problem of incapability of detecting inner attacks and defending against black hole attacks in route discovery in the prior art. According to the method provided by the technical schemes of the invention, each node establishes a receiving route request table and a receiving route response table and compares the content of the receiving route request table and the receiving route response table; whether a suspicious node exists is judged; if a suspicious node exists, a determined threshold value in a training set is compared with the destination sequence number of a received route response packet; if the sequence number is larger than the threshold value, it is determined that a node which sends the route response packet is a black hole node, otherwise, the node which sends the route response packet is determined as a normal node; and in subsequent route discovery, only the data packet of the normal node is forwarded or received, and the data packet of the black hole node is not forwarded or received. According to the black hole attack defense method applied to route discovery of the invention, a third party is not introduced, all procedures are completely completed by nodes in a wireless ad hoc network, and therefore, the security requirements of the routing of the wireless ad hoc network can be satisfied. The method can be applied to defending against black hole attacks in the route discovery of the wireless ad hoc network.
Owner:XIDIAN UNIV
Method for defending black hole attack based on active detection in wireless sensor network
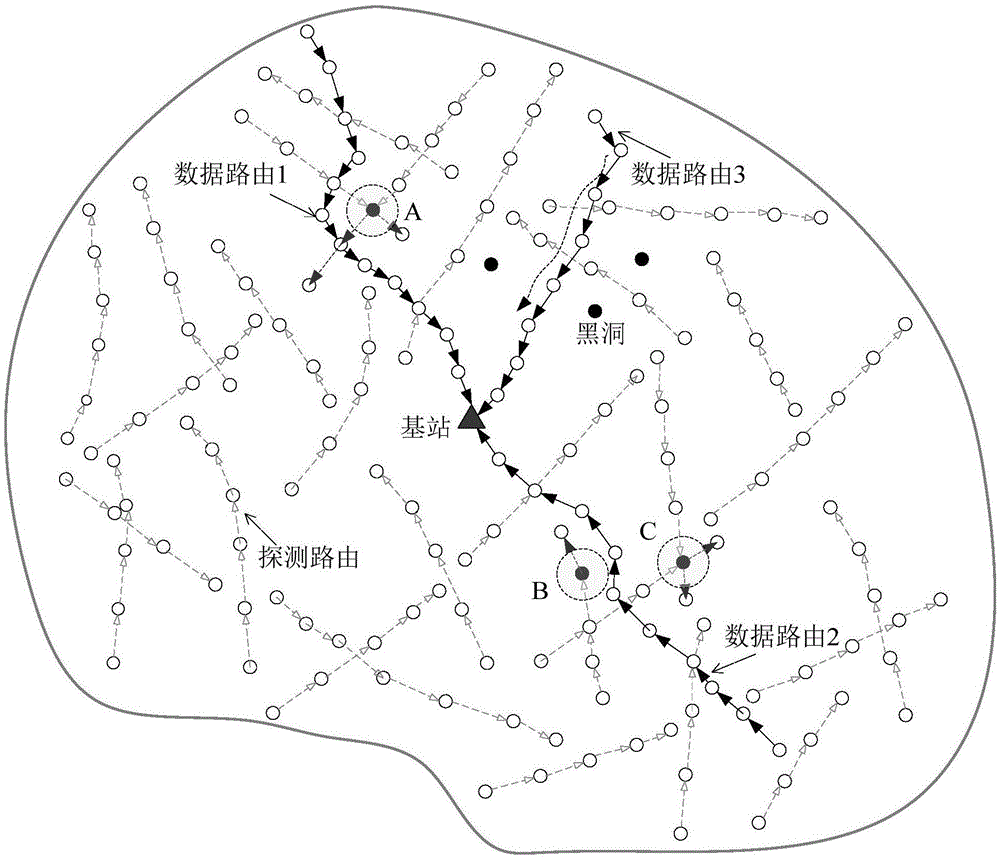
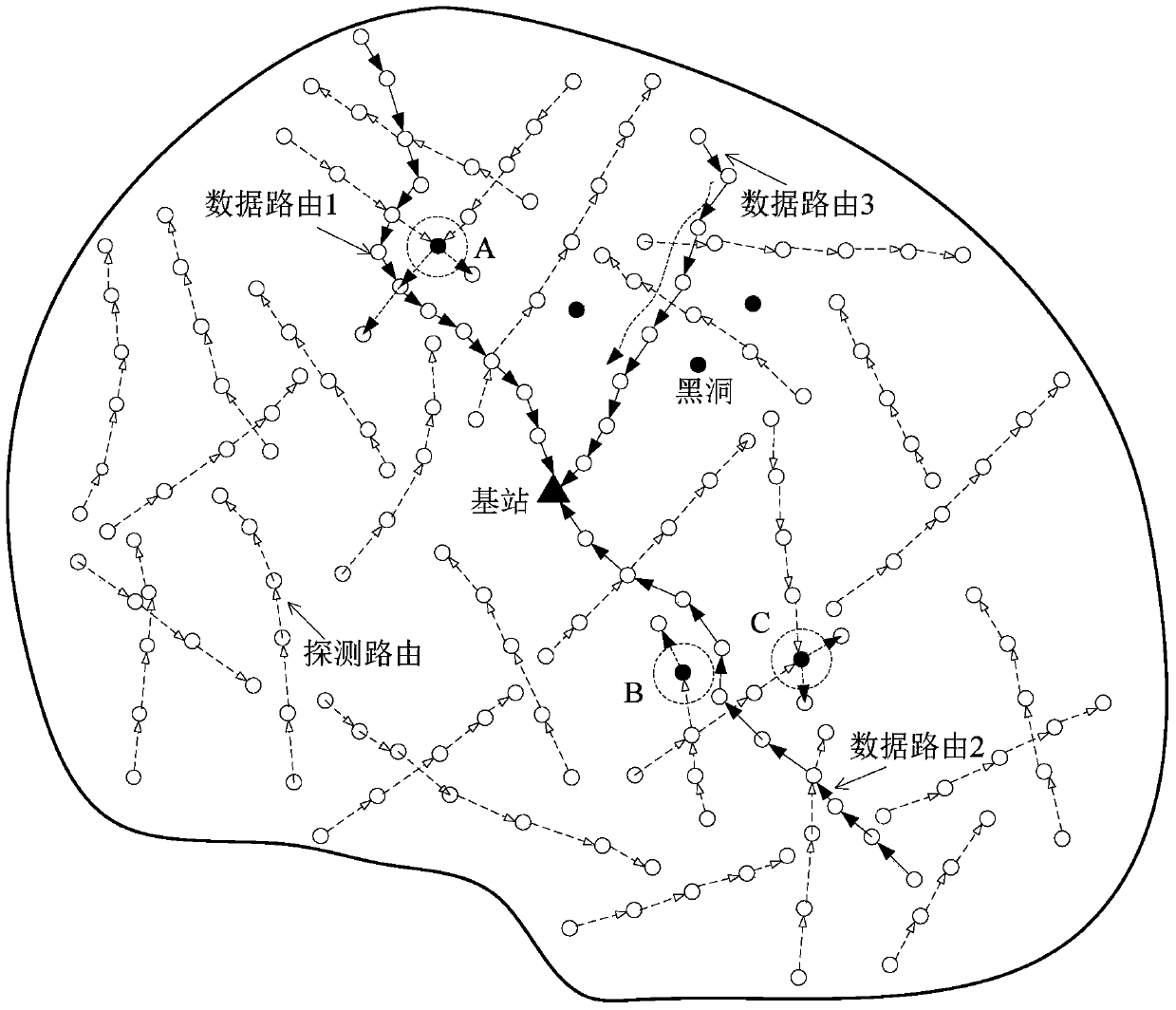
InactiveCN105611536AIdentify and reduce trustIncrease the probability of successfully reaching the base stationTransmissionSecurity arrangementMobile wireless sensor networkWireless mesh network
The invention discloses a method for defending a black hole attack based on active detection in a wireless sensor network. A plurality of detection routes are established in a region in which network energy is abundant and the wireless sensor network is far away from a base station, and an attacker being unaware that the established routes are the detection routes also launches an attack to the detection routes, so that the attacker is exposed, and behavior and position information of the attacker and credibility information of a node can be obtained. After the information is obtained, the region which is under the black hole attack can be avoided when real data routing is performed, so that information of a black hole can be obtained under the condition that sensitive data of a system are unavailable or few data are lost, and data routing security of the wireless sensor network is ensured. Residual energy of a network is fully utilized, and the network service life is not shortened under the condition of enhancing the network security.
Owner:CENT SOUTH UNIV
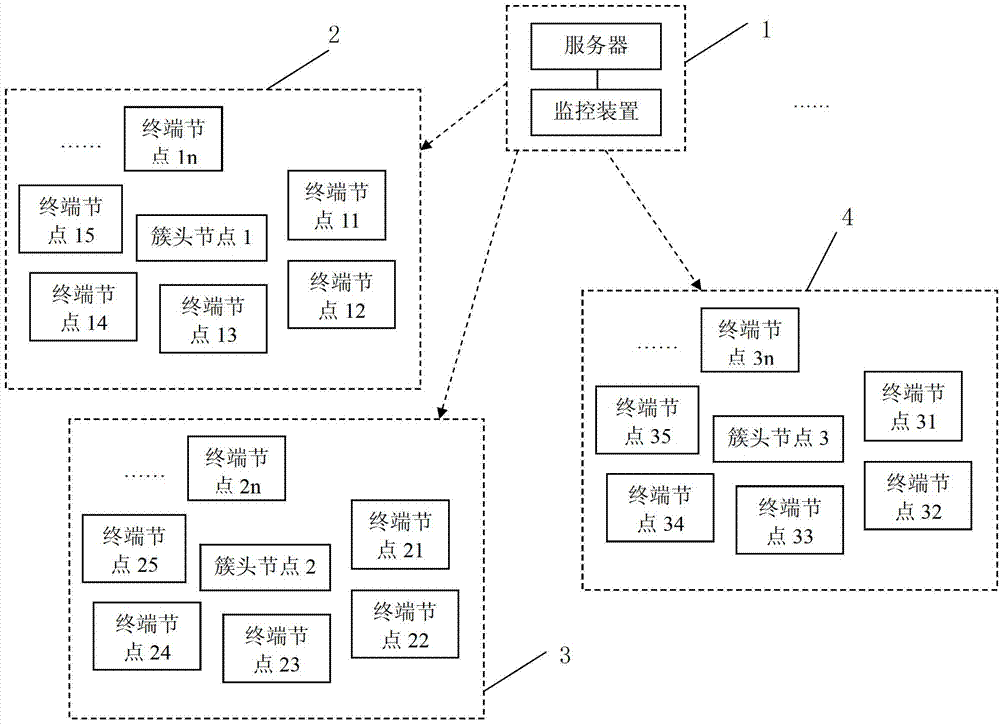
Method for detecting black hole attacks in clustering self-organized networks
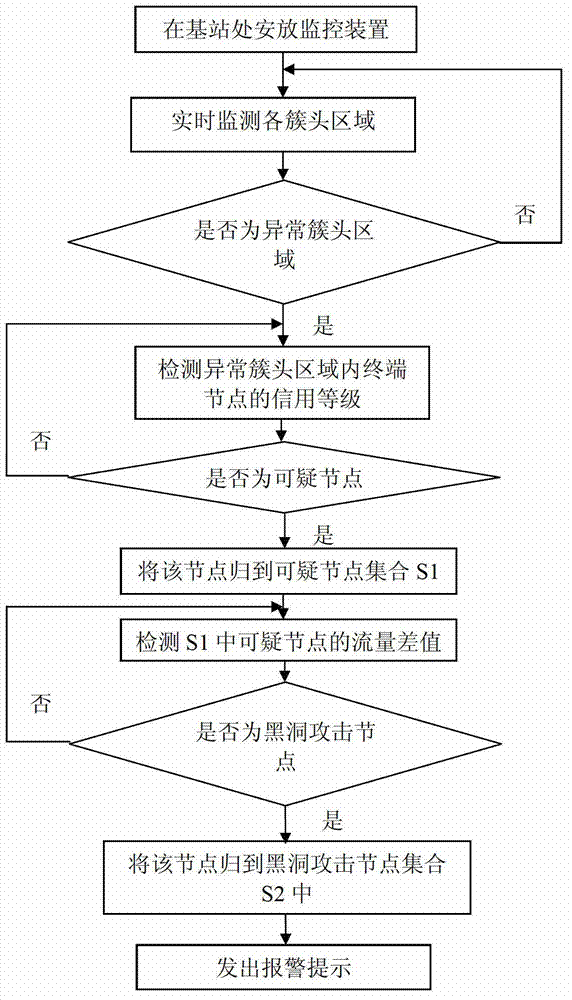
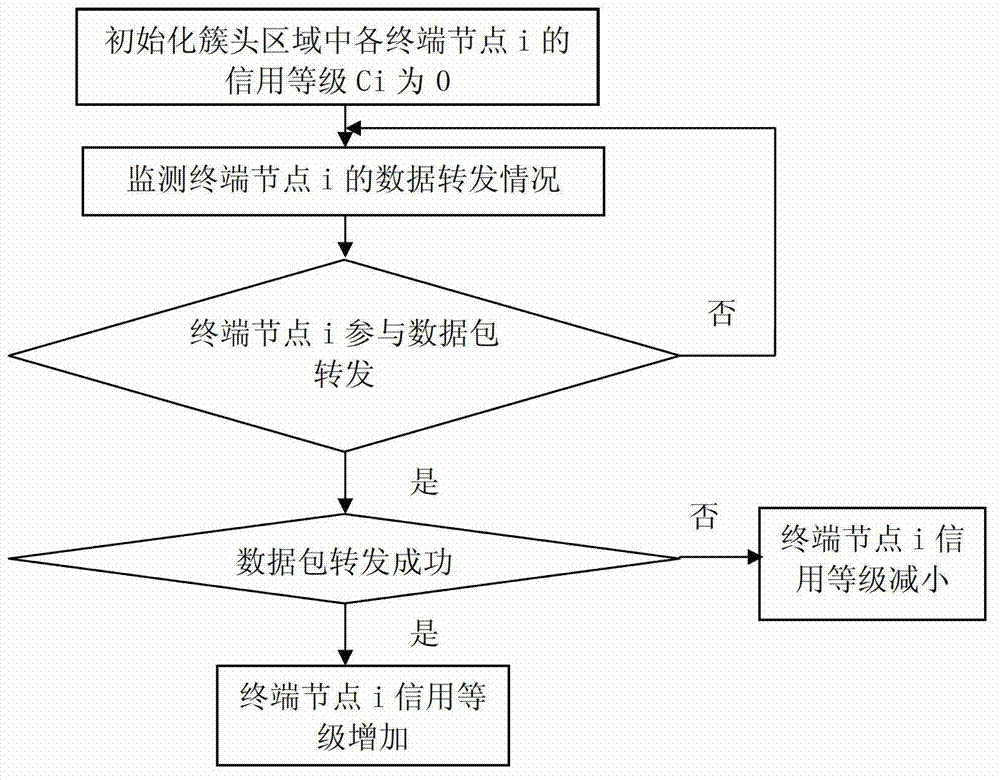
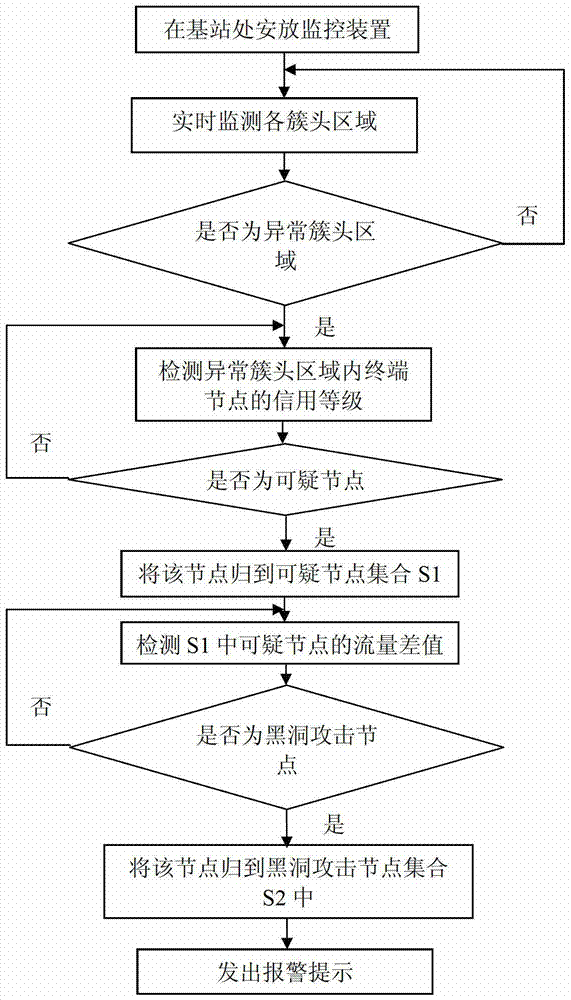
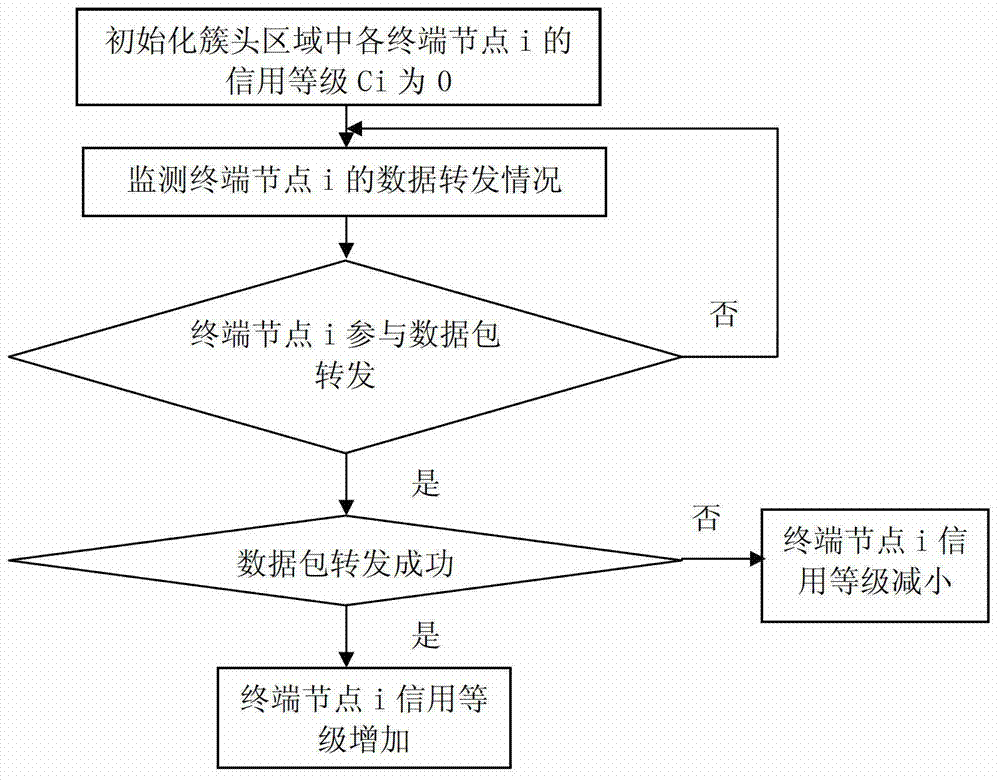
InactiveCN102932794AAvoid attackSolve the problem of attackNetwork topologiesSecurity arrangementSelf-organizing networkBlack hole
The invention relates to a method for detecting black hole attacks in clustering self-organized networks. The method includes that step one, a monitoring device is arranged at a base station; step two, cluster head areas in self-organized networks in an area covered by the base station are monitored in real time; step three, whether abnormal cluster head areas exist in the monitored area is judged, if the abnormal cluster head areas exist, step four is performed, and if not, the step two is repeated; step four, credit rates of terminal nodes in the abnormal cluster head areas are detected, and suspicious nodes are found to form a suspicious node set S1; step five, flow differences of nodes in the S1 are detected, and black hole attack nodes are found to form a black hole attack node set S2; and step six, the monitoring device sends early warning prompts. According to the method, not only a single malicious node attack is solved, the problem that a plurality of single malicious nodes are cooperated to attack can be effectively solved, alarms can be sent, and timely defense and treatment to the black hole attacks are facilitated.
Owner:INST OF INFORMATION ENG CAS
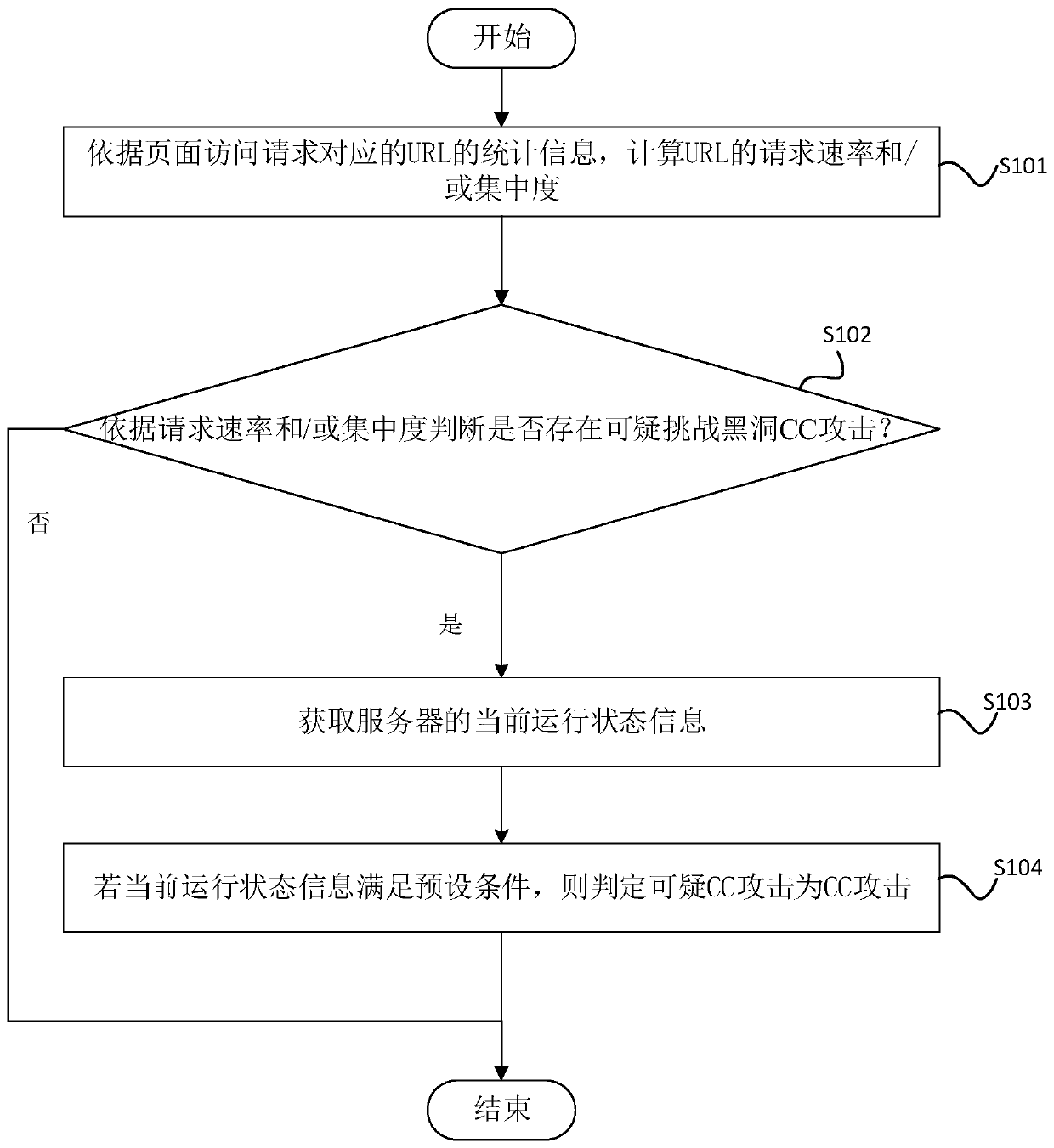
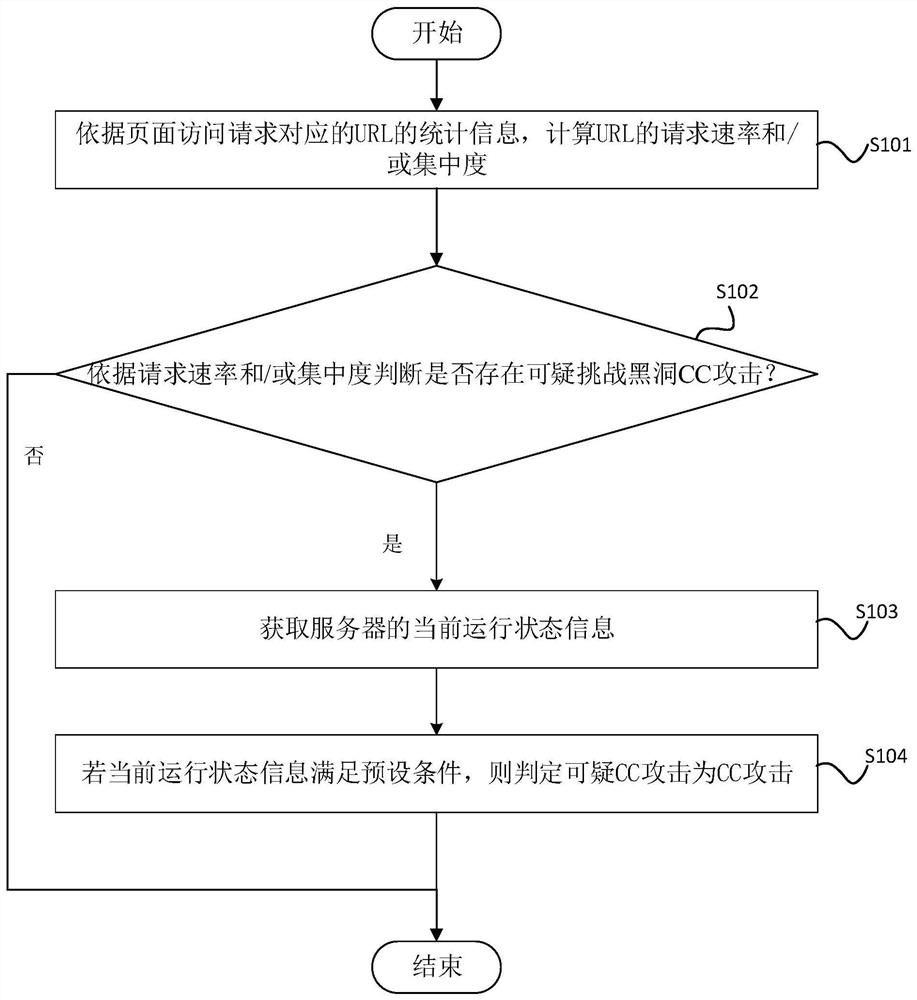
Challenge black hole attack detection method and related device
The invention relates to the field of network security, and provides a challenge black hole attack detection method and a related device, and the method comprises the steps: calculating the request rate and / or concentration degree of a URL according to the statistical information of the URL corresponding to a page access request; judging whether a suspicious challenge black hole CC attack exists or not according to the request rate and / or the concentration degree; if the suspicious CC attack exists, obtaining current running state information of the server; and if the current running state information does not meet the preset condition, judging that the suspicious CC attack is the CC attack. The false alarm rate can be reduced by combining the rate and the concentration degree of the access request and the current running state of the server.
Owner:NEW H3C SECURITY TECH CO LTD
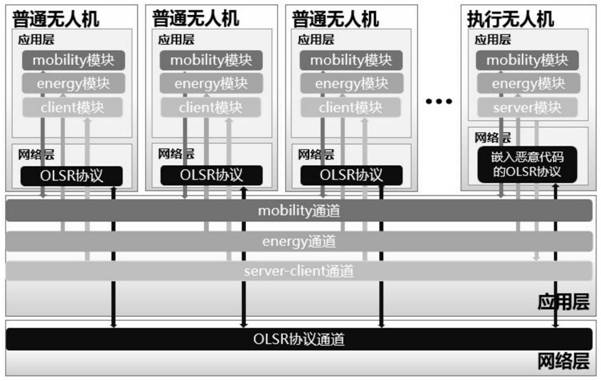
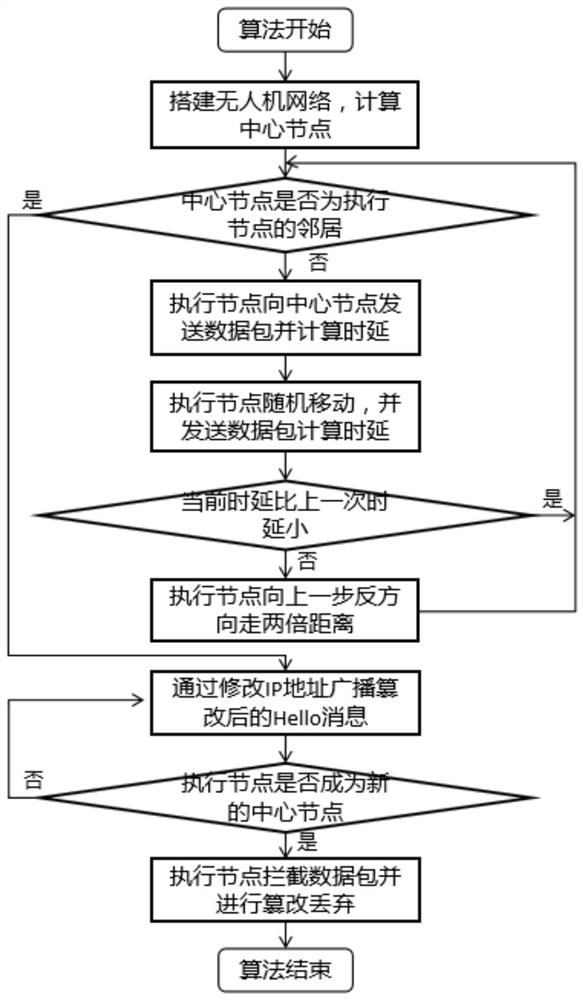
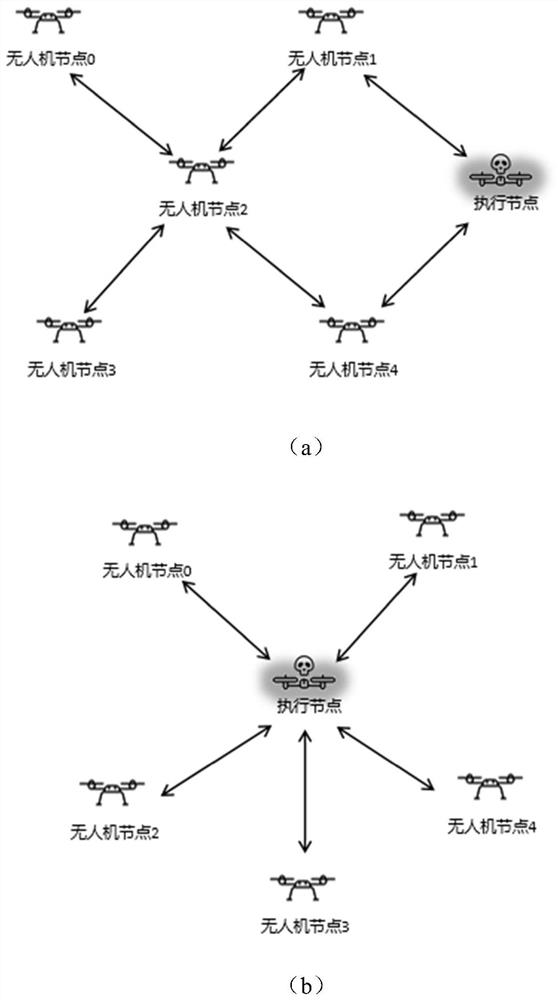
OLSR protocol black hole attack method for unmanned aerial vehicle ad hoc network
InactiveCN111901801AAccelerated destructionDramatic changeSecurity arrangementRouting tableIp address
The invention discloses an OLSR (Optimized Link State Routing) protocol black hole attack method for an unmanned aerial vehicle ad hoc network. The problem that an existing black hole attack method cannot be applied to a high-mobility drone ad hoc network is solved, the formation and the motion trail of the drone are changed, and finally the purpose of obtaining the network control right is achieved. The method comprises the following implementation steps that: an execution node calculates a node in a network center in an area through a routing table; the execution node reaches the transmission range of the central node through the time delay information transmitted by the data packet; the execution node sends a large number of Hello message packets of which the IP addresses are randomly modified to the central node to occupy the position of the central node; and node tampering is executed or the data packet in the network is discarded, and black hole attack is performed on the network. According to the method, the motion trail of the unmanned aerial vehicle ad hoc network can be drastically changed, the attack effect is good, the network is greatly damaged, and the method has obvious advantages in the aspects of changing the formation and the motion trail of the unmanned aerial vehicle, obtaining the control right of the network and the like.
Owner:SOUTHEAST UNIV
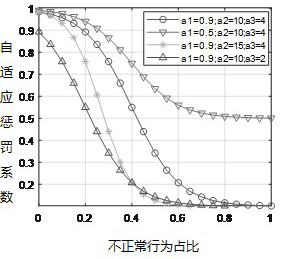
Wireless sensor network security routing protocol based on adaptive trust mechanism
Due to the characteristics of resource limitation and dynamic change of sensor nodes, a wireless sensor network (WSN) faces the problems of safety and energy consumption. The invention provides a wireless sensor network security routing protocol based on a self-adaptive trust mechanism, the protocol only needs to calculate a direct trust value, and an indirect trust value is completed by a base station, so that the energy consumption of the node is reduced. A punishment mechanism is adopted when the nodes calculate the trust values so as to ensure that the trust values of malicious nodes are quickly reduced. Therefore, black hole attacks, selective forwarding attacks, slot attacks and flooding attacks are resisted. A monitoring node is established, and an active security route is selected by a base station and is responsible for resisting wormhole attacks. Therefore, malicious nodes can be quickly identified and isolated.
Owner:CHANGCHUN UNIV OF TECH
CC (Challenge Collapsar) attack defense method of distributed system and distributed system
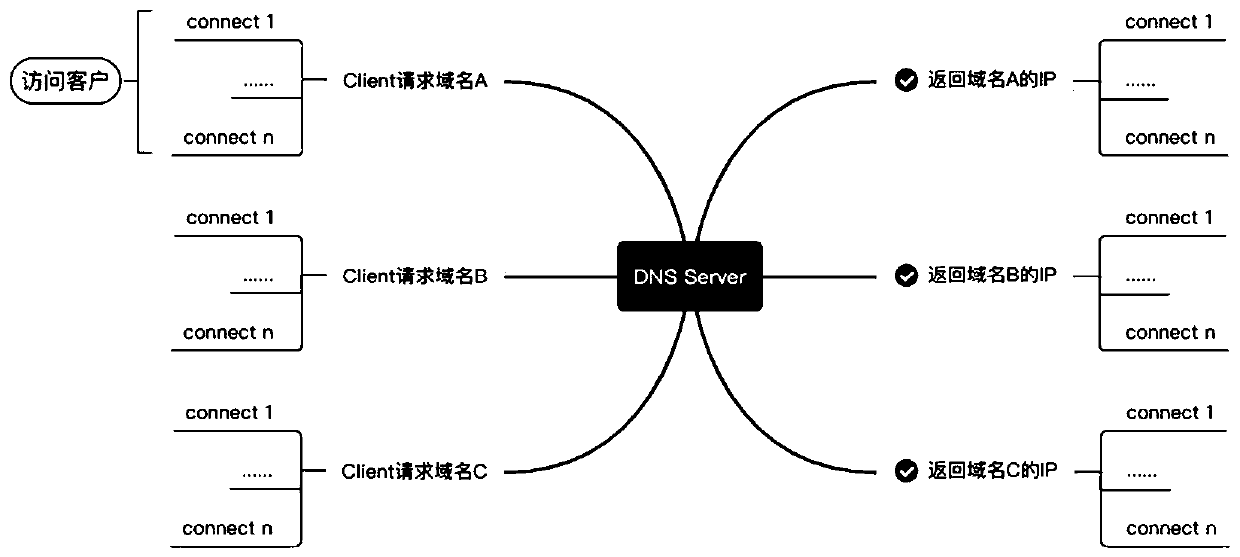
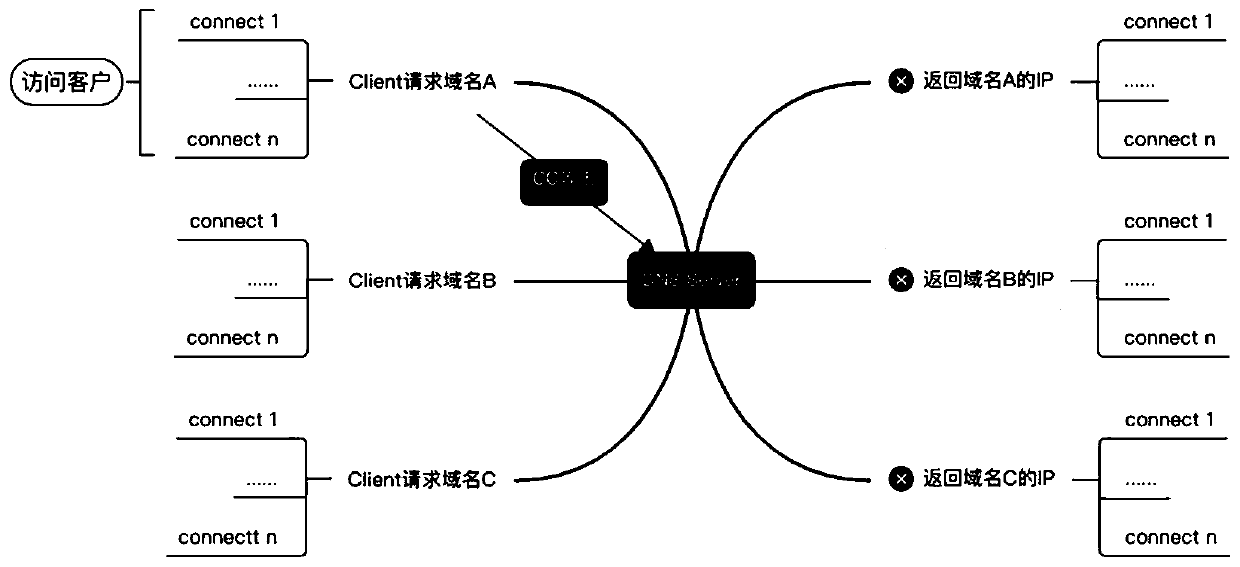
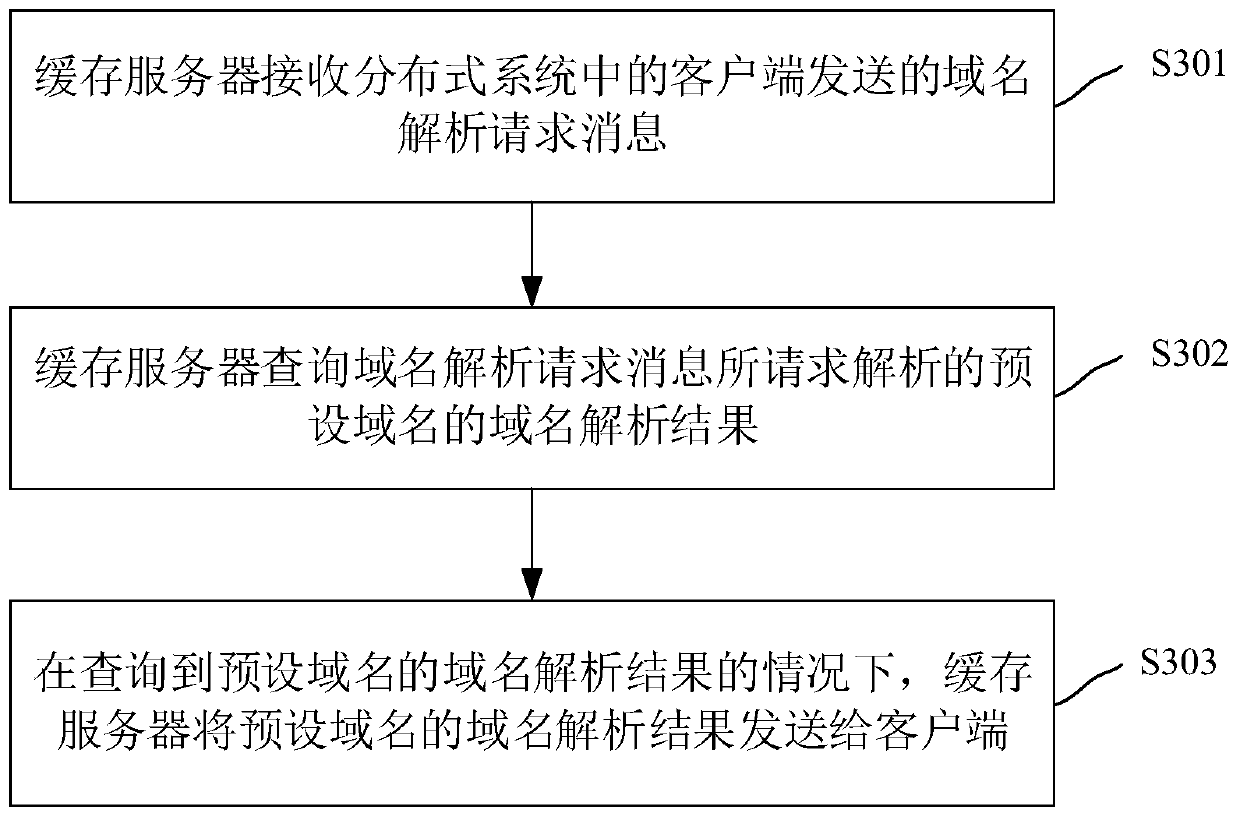
InactiveCN111565195AFix slow responseSolvers the problem of downtimeTransmissionDomain nameCache server
The invention relates to a CC (Challenge Collapsar) attack defense method of a distributed system and the distributed system. The method comprises the steps that a cache server receives a domain nameresolution request message sent by a client in the distributed system; the cache server queries a domain name resolution result of a preset domain name requested to be resolved by the domain name resolution request message; and under the condition that the domain name resolution result of the preset domain name is queried, the cache server sends the domain name resolution result of the preset domain name to the client. Through the method and the device, the problem of slow response or downtime of the DNS server due to CC attack is solved, and CC attack to the DNS server is avoided.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Detection method and related device for challenging black hole attack
ActiveCN110808967BAccurate detectionReduce false alarm rateSecuring communicationInternet privacyAttack
The present disclosure relates to the field of network security, and provides a detection method and related devices for challenging black hole attacks. Rate and / or concentration determine whether there is a suspicious challenge black hole CC attack; if there is a suspicious CC attack, obtain the current operating status information of the server; if the current operating status information does not meet the preset conditions, determine the suspicious CC attack as a CC attack. By combining the rate and concentration of access requests and the current operating status of the server, the false positive rate can be reduced.
Owner:NEW H3C SECURITY TECH CO LTD
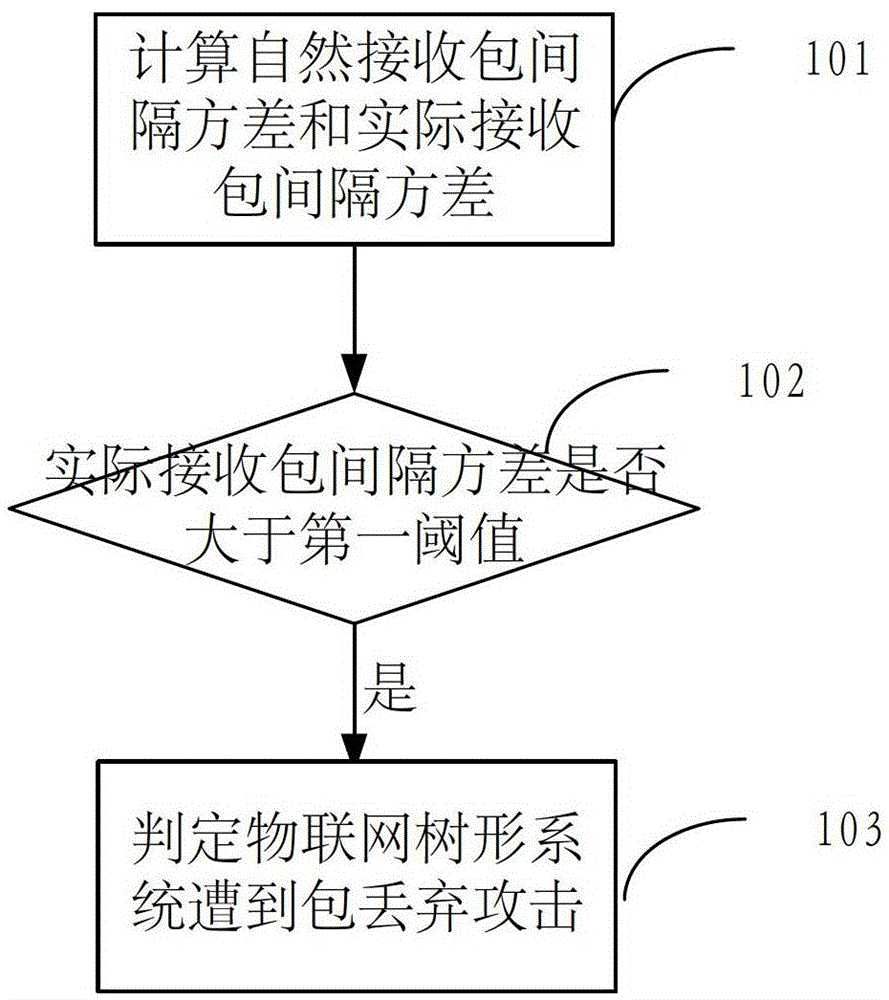
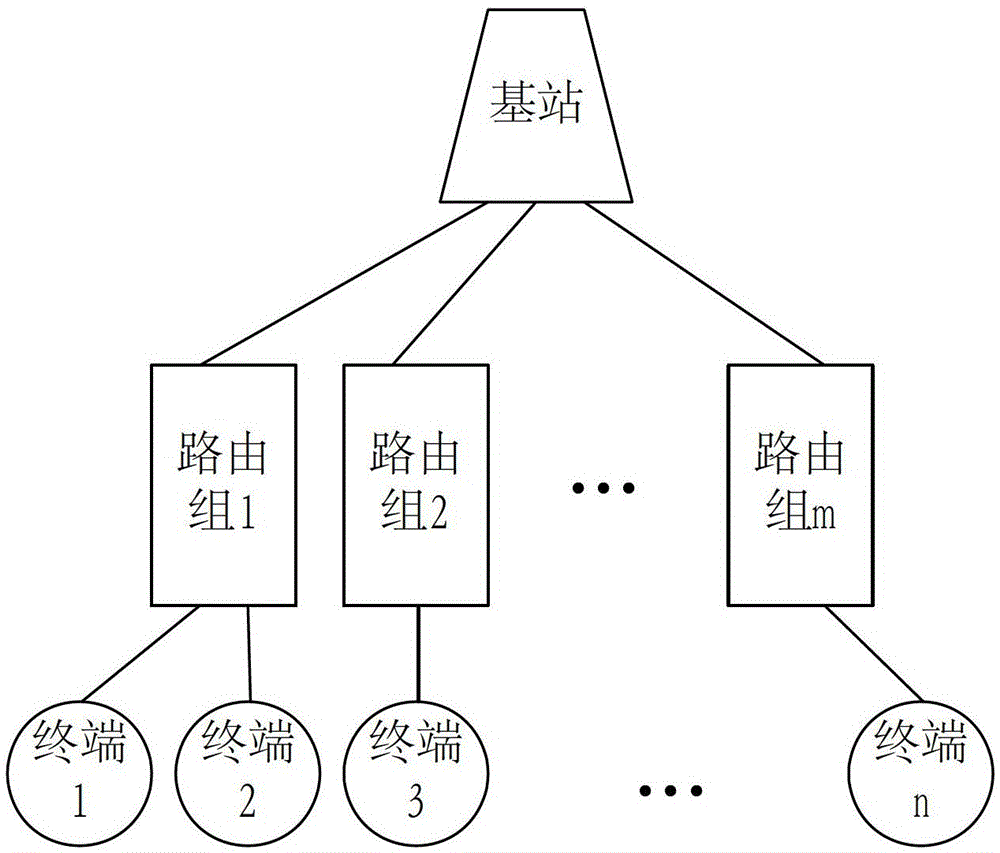
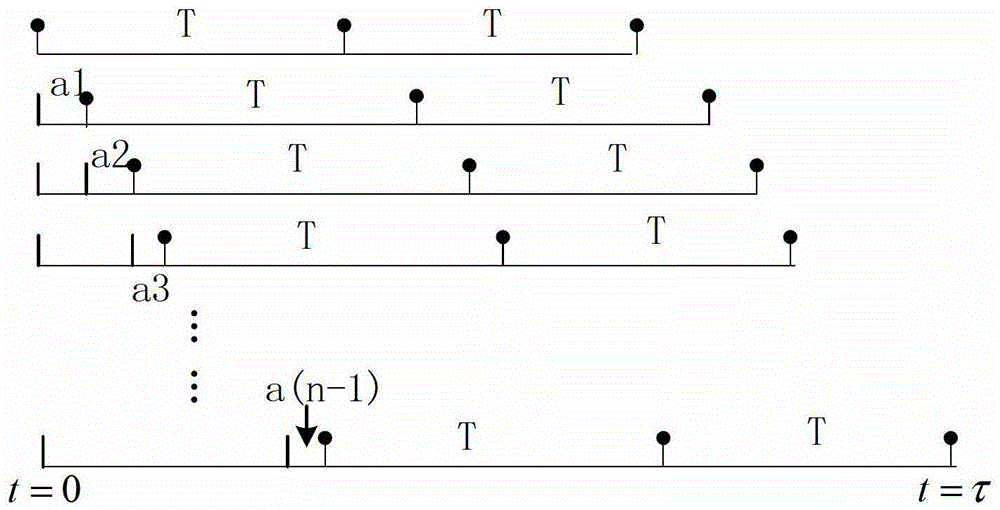
A detection method for Internet of Things packet drop attack and Internet of Things tree system
The invention provides a detection method for a malicious packet dropping attack of the Internet of things. The detection method comprises the following steps of: calculating a natural packet receiving interval variance and calculating an actual packet receiving interval variance; and judging whether the actual packet receiving interval variance is larger than a first threshold obtained according to the natural packet receiving interval variance, if the actual packet receiving interval variance is larger than the first threshold, determining that an Internet of things tree system falls into the malicious packet dropping attack. In a conclusion, according to the Internet of things tree system, the natural packet receiving interval variance obtained when the Internet of things tree system does not fall into the attack and the actual packet receiving interval variance obtained when an information packet is actually received are respectively calculated; and when the actual packet receiving interval variance is larger than the first threshold obtained according to the natural packet receiving interval variance, the Internet of things tree system falls into the malicious packet dropping attack. Therefore, according to the technical scheme of the invention, a routing node and a terminal node do not need to return acknowledgement information, so that communication expense in the Internet of things tree system cannot be extra affected. The invention also provides the Internet of things tree system.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
A method of resisting black hole attack based on active detection in wireless sensor network
InactiveCN105611536BImprove securityExtend your lifeTransmissionSecurity arrangementAttackWireless sensor networking
The invention discloses a method for resisting black hole attacks based on active detection in a wireless sensor network. Multiple detection routes are established in a wireless sensor network with abundant network energy far away from a base station. Since the attacker does not know that this is a detection route, it also An attack on these detection routes will be launched, so that the attacker is exposed, so that the behavior and location information of the attacker, as well as the trust information of the node can be obtained. After obtaining this information, the black hole attack area can be avoided during the real data routing, and the black hole information can be obtained without or little loss of sensitive data in the system, ensuring the data routing security of the wireless sensor network; The remaining energy of the network is fully utilized, and the service life of the network can not be reduced under the condition of improving network security.
Owner:CENT SOUTH UNIV
A black hole attack detection method in clustered self-organizing network
InactiveCN102932794BAvoid attackSolve the problem of attackNetwork topologiesSecurity arrangementSelf-organizing networkPacket drop attack
The invention relates to a method for detecting black hole attacks in a clustered self-organizing network. The method includes the following steps: Step 1: Install a monitoring device at a base station; Step 2: All clusters in the self-organizing network within the coverage of the base station The head area is monitored in real time; step 3: judge whether there is an abnormal cluster head area in the monitored area, if there is, enter step 4, otherwise return to step 2; step 4: detect the credit level of the terminal node in the abnormal cluster head area, Find suspicious nodes to form a set of suspicious nodes S1; step 5: detect the flow difference of nodes in S1, and find out black hole attack nodes to form a set S2 of black hole attack nodes; step 6: the monitoring device issues an early warning prompt. This method can not only solve the attack of a single malicious node, but also effectively solve the problem that multiple malicious nodes cooperate with each other to attack, and can issue an alarm, which is conducive to timely defense and processing of black hole attacks.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Satellite ad hoc network security framework system and black hole attack resisting method thereof
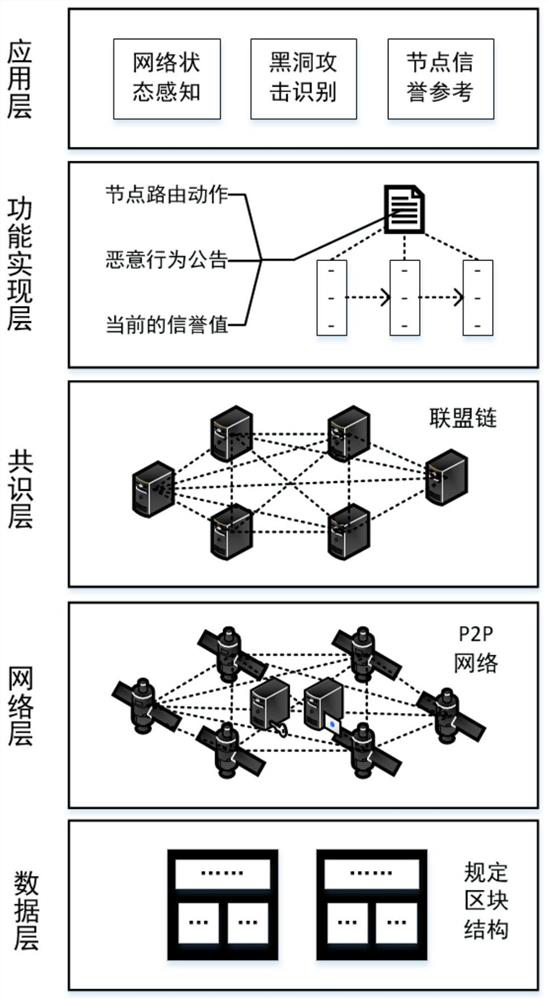
PendingCN114339763AImprove securityOvercoming Vulnerability to Black Hole AttacksUser identity/authority verificationNetwork topologiesAttackSelf-organizing network
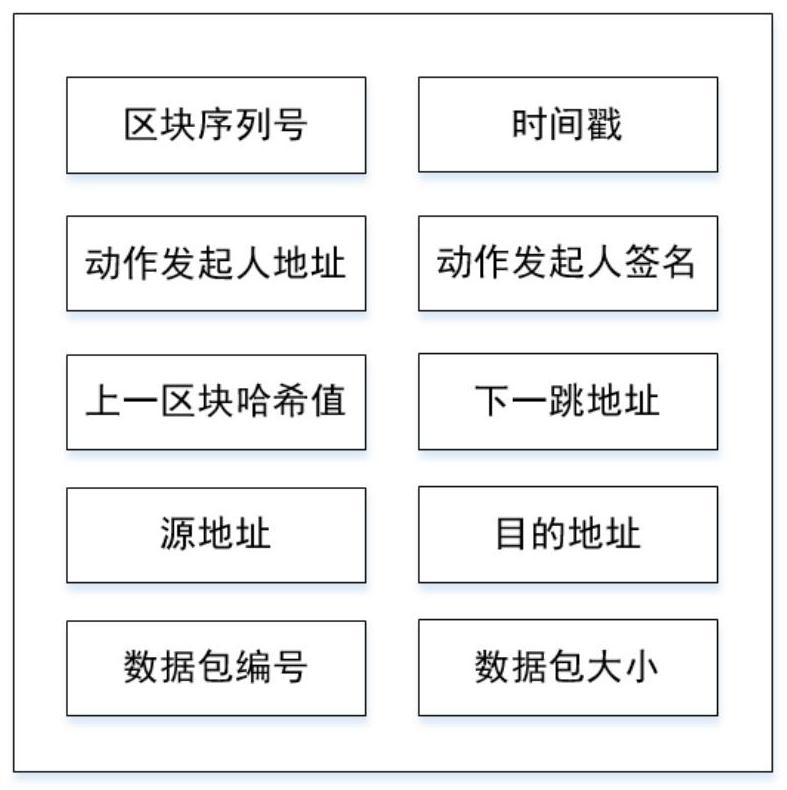
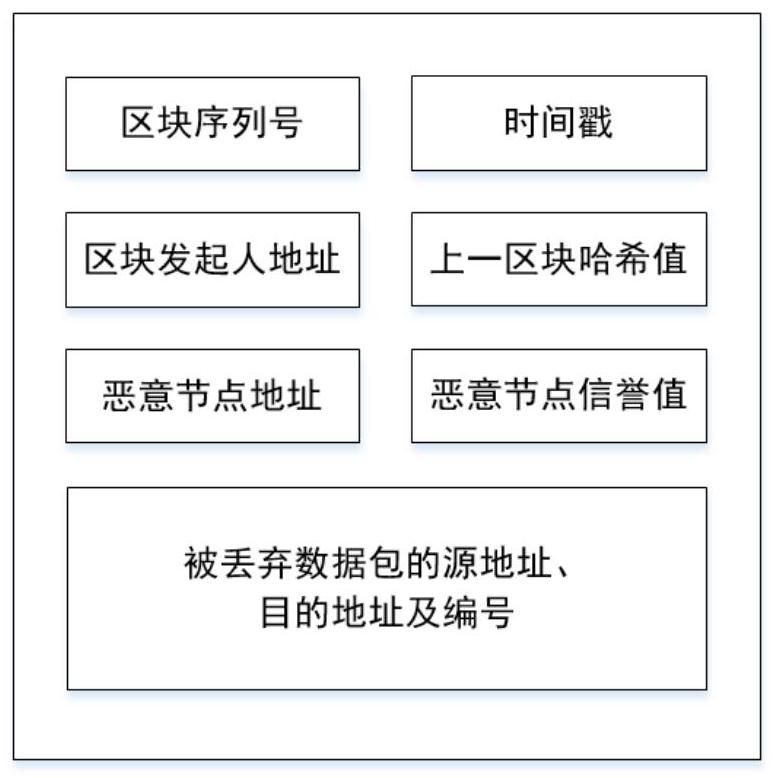
The invention discloses a satellite ad hoc network security framework system based on a block chain technology. The system comprises a data layer, a network layer, a consensus layer, a function implementation layer and an application layer, the data layer stipulates the structure and the content of each block; the satellite nodes of the network layer jointly form a decentralized system structure, and each satellite node is added into the alliance chain system as the identity of an alliance chain member; the consensus layer completes accounting through a right-based consensus mechanism; all satellite nodes in the function implementation layer jointly maintain a block chain account book, routing actions of the satellite nodes in a data plane, announcement of malicious behaviors of the nodes and credible records of current reputation values of all the satellite nodes are achieved according to regulations in an intelligent contract, and the records are stored among all the nodes in a distributed mode; the top layer is an application layer, and the application layer provides network state sensing, black hole attack recognition and reputation reference for satellite nodes of a data plane based on credible records of a bottom layer network, so that network security is guaranteed.
Owner:AEROSPACE DONGFANGHONG SATELLITE
Method and device for identifying unknown cdn nodes in cc attack protection
ActiveCN110636068BAccurate identificationPreventing website inaccessibilitySecuring communicationTransmission protocolContent distribution
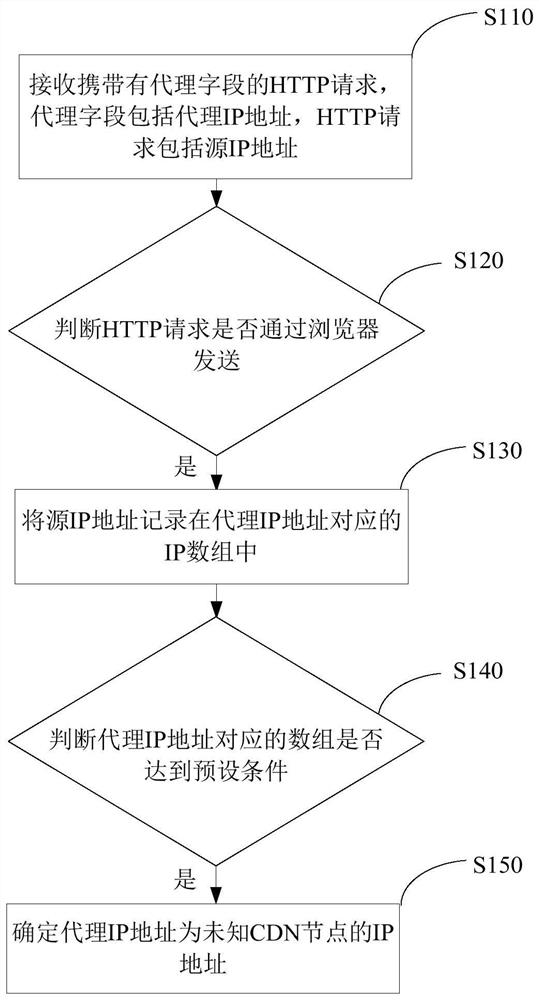
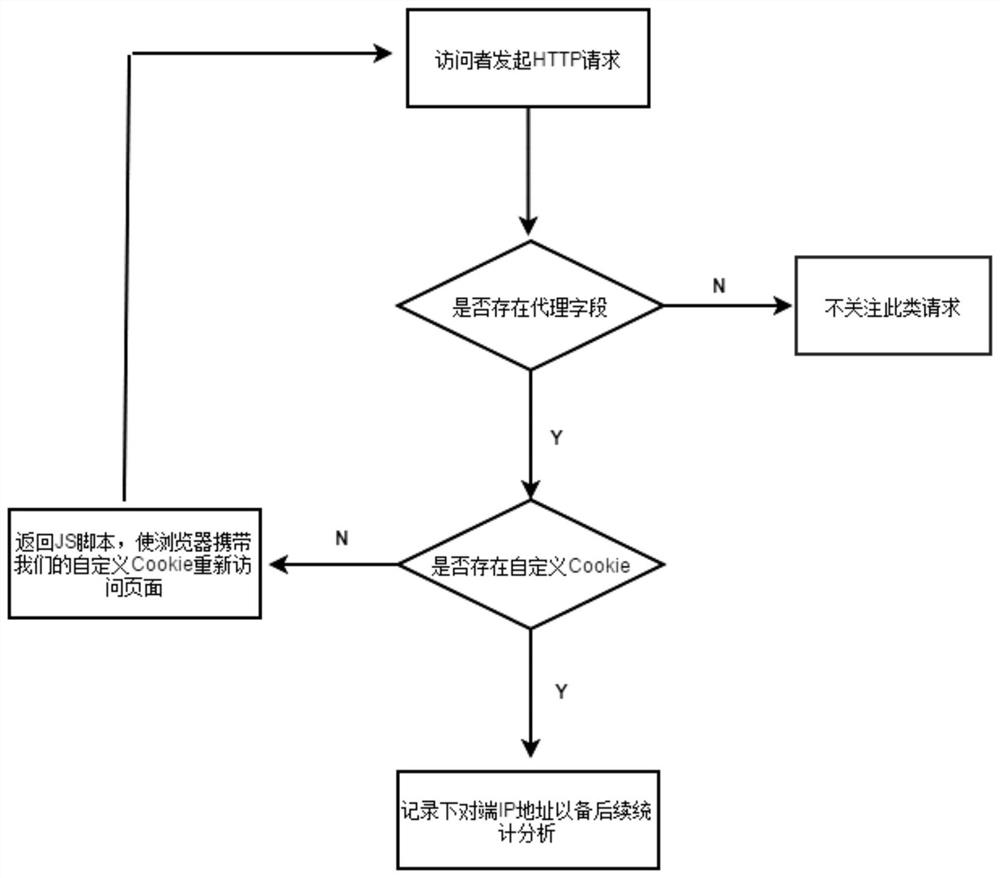
The present application provides a method and device for identifying unknown CDN nodes in CC attack protection, which relate to the field of network technology and include: receiving a hypertext transfer protocol (HTTP) request carrying a proxy field, the proxy field includes a proxy Internet protocol (IP ) address, the HTTP request includes the source IP address; if the HTTP request is sent through a browser, record the source IP address in the IP array corresponding to the proxy IP address; if the array corresponding to the proxy IP address meets the preset condition, determine the proxy IP address as The IP address of the content distribution network (CDN) node is unknown, which solves the technical problem that the CDN node is misjudged as a challenge black hole (CC) attack source and blocks the IP, causing users in some areas to be unable to access the website.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
A security trust method for ad Hoc network based on reference node strategy
The invention relates to an Ad Hoc network security trust method based on a reference node strategy, belonging to the field of network security. The method is specifically as follows: calculate the trust value of each node through the trust model, and send the trust value to the trust value statistics node, the trust value statistics node counts the weighted trust value of each node and updates the reference node, the trust value statistics node, and finally the reference node The node initiates the reference node policy. The invention has the advantages of quickly finding the black hole attack nodes in the Ad Hoc network, and at the same time having a good defense effect against data packet attacks and hybrid black hole attacks; and having strong scalability and adaptability.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Maintaining communication between network nodes that are subjected to a packet attack
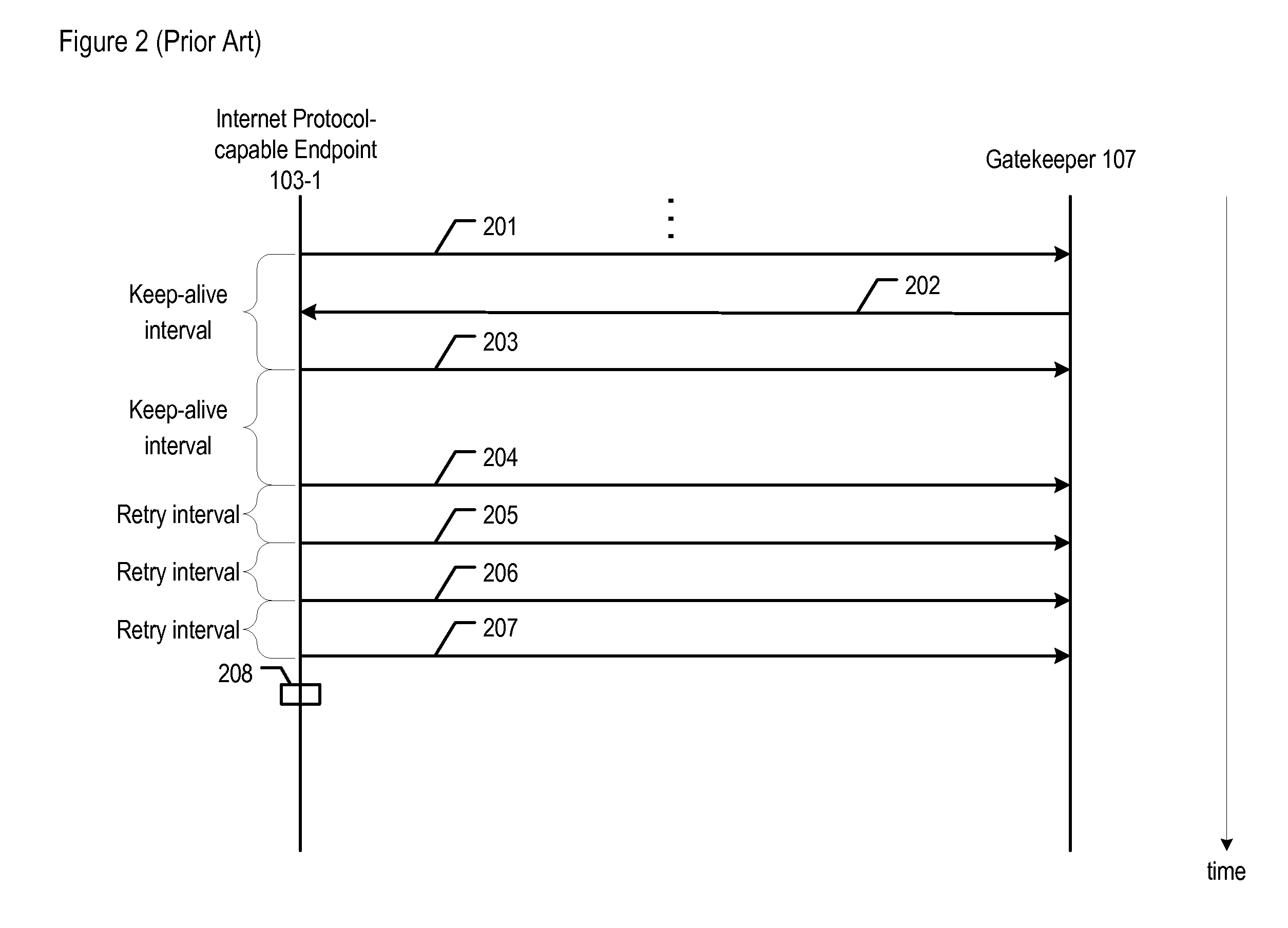
ActiveUS8353030B2Blunt immediate effectSave the processMemory loss protectionError detection/correctionNetwork packetComputer science
A method is disclosed that enables mitigating at least some of the problems caused by a packet attack. When a first Internet Protocol (IP)-capable device is subjected to a packet attack, it indicates periodically to a second IP-capable device that certain communications with the first device are to be suspended. The periodic transmitting of the indication is performed at a slower rate than the keep-alive mechanism that is normally used to detect loss of connectivity. When the second device receives the transmitted indication, it refrains from transmitting keep-alive messages to the first device for a predetermined interval. Meanwhile, the first device also refrains from transmitting keep-alive messages to the second device for a similar interval. In transmitting the suspend indication, the illustrative embodiment seeks to prevent pairs of communicating devices that are experiencing packet attacks from continuing their operation under the erroneous assumption that each device is unavailable.
Owner:AVAYA INC
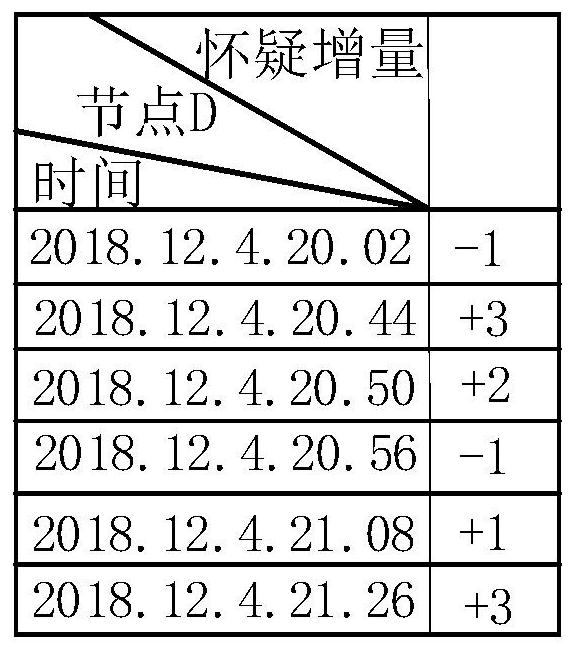
Black hole attack detection and tracking method based on suspicion accumulation
The invention belongs to the field of mobile ad hoc network routing security, and discloses a black hole attack detection and tracking method based on doubtful accumulation. According to the method, in a detection period, a passive monitoring mode is adopted, a node detects whether current topology update meets a suspicious condition, and if a data packet of the topology update meets the suspicious condition, the node adds a IV-type suspicious degree to a reputation registration table corresponding to the suspicious node; The node monitors the packet loss rate in each routing path, and triggers active detection if the packet loss rate exceeds the threshold value; an active detection mode is aodpted to detect suspicious behaviors so as to determine a correspondingly increased doubtful value, and performing weighted calculation on credit changes at different moments according to a forgetting factor so as to obtain a final doubtful value; And according to the final doubtful value of the suspicious node, the network control station determines whether the suspicious node is a malicious node through analysis, and once the suspicious node is confirmed to be the malicious node, the networkcontrol station broadcasts the whole network so as to isolate the malicious node from the whole network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
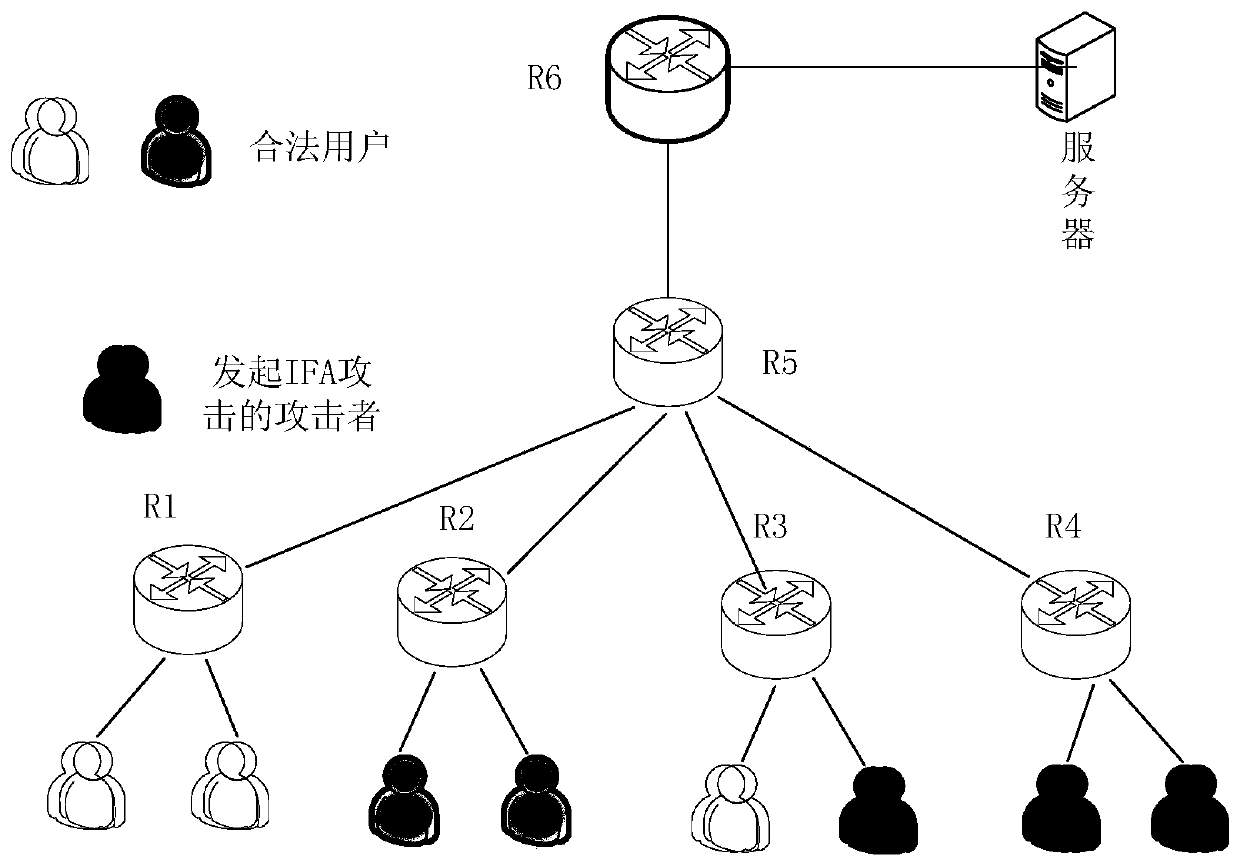
Method and system for detecting interest packet flooding attack in content-centric network
The invention relates to the technical field of network security, and relates to a method and system for detecting an interest packet flooding attack in a content center network. The method comprisesthe following steps: counting a probability distribution model of a content name prefix of an interest packet; calculating an information entropy of a router according to a statistical value; and comparing the information entropy with a given threshold, and then calculating an entropy rate. In the interest packet flooding attack detection scheme designed by the invention, the difference between the entropy rate change of the legal burst stream and the attack stream is considered, the outburst stream of a legitimate user and an attack stream of an attacker are effectively distinguished on the premise of ensuring that the attack is detected as soon as possible, thereby effectively reducing the misjudgment of the legitimate user.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
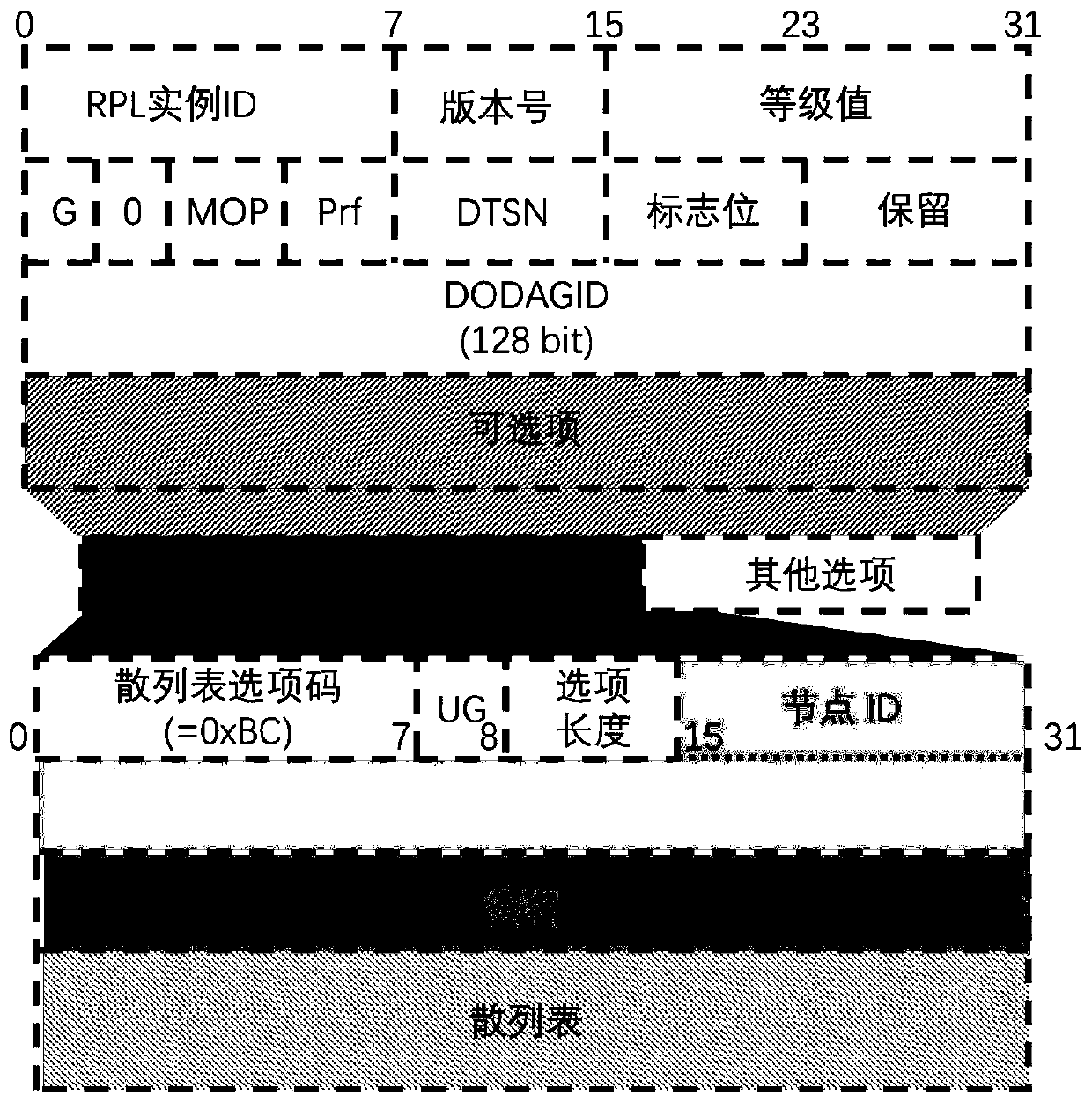
Electric power RPL protocol black hole attack defense method based on cuckoo filter
InactiveCN111049642AMaintain securityWide range of defenseEncryption apparatus with shift registers/memoriesInformation controlAttack
Owner:SHENZHEN POWER SUPPLY BUREAU +1
Black hole attack defense method in route discovery
ActiveCN106658482BSelf-validatingEnsure safetyNetwork topologiesTransmissionThird partyComputer network
The invention discloses a black hole attack defense method in route discovery, which mainly solves the problems that the prior art cannot detect internal attacks and cannot defend black hole attacks in route discovery. The technical solution is: the node establishes and compares the contents of the receiving routing request table and the receiving routing response table to determine whether there is a suspicious node. If there is a suspicious node, the threshold determined in the training set and the purpose of the received routing response packet Sequence numbers are compared: if the destination sequence number is greater than the threshold, it is determined that the node that sent the routing response packet is a black hole node, otherwise it is determined that the node that sent the routing response packet is a normal node; in the subsequent route discovery, only the data of the normal node is forwarded or received packets without forwarding or receiving packets from blackhole nodes. The invention does not introduce a third party, is completely completed by nodes in the wireless ad hoc network, meets the security requirements of the wireless ad hoc network routing, and can be used to defend against black hole attacks in the wireless ad hoc network routing discovery.
Owner:XIDIAN UNIV
A data forwarding method with black hole attack detection
The invention relates to a data forwarding method with a black hole attack detection function and belongs to the technical field of opportunistic network trust management. In order to solve the problems that existing black hole attack detection methods in an opportunistic network only detect attack behaviors of black hole nodes in a certain aspect and lack relatively comprehensive evaluation on the black hole nodes and detection results are affected by certain changes of the network easily, during black hole attack detection, trust conditions of the nodes in all aspects are required to be considered comprehensively, comprehensive judgments are made, and an opportunistic network trust management method for comprehensively judging node credibility according to node experience in the aspects of the accuracy degree of routing information provided by to-be-detected nodes, the reliability of historic behaviors of the nodes, the forwarding capacity of the nodes for messages and the like is further designed. With the adoption of the method, the reliability of the nodes is accurately judged, and detection results cannot be affected by other factors in the network easily, so that the delivery rate of the messages in the network is increased, and the performance of the network is enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com