Electric power RPL protocol black hole attack defense method based on cuckoo filter
A black hole attack and cuckoo technology, applied in encryption devices with shift registers/memory, electrical components, digital transmission systems, etc., can solve problems such as inability to defend, and achieve the effect of maintaining security and defending a wide range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further elaborated and illustrated below in conjunction with the accompanying drawings and specific embodiments.
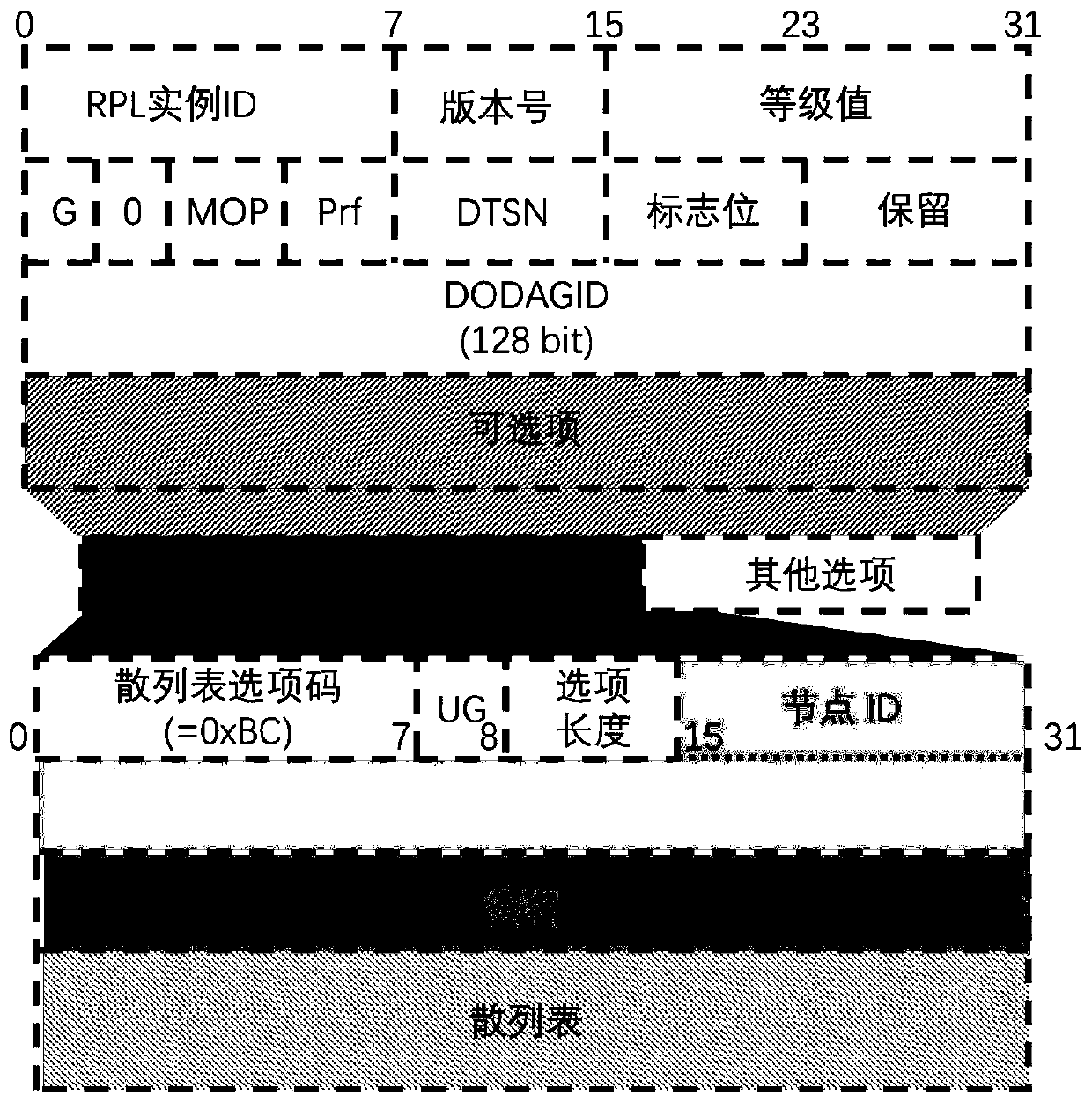
[0017] The smart instrument described in this embodiment is a node, which is a device to be connected before accessing the entire network route. The root node knows which devices are trusted, and the trusted device can access the network route through the improved RPL protocol. like figure 1 Shown is the design diagram of the RPL protocol field, except for the optional items, it is a normal field of the RPL protocol. The present invention mainly adds hash table options in the optional items, including hash table option codes, update flags, node IDs, and message Signatures and hash tables.
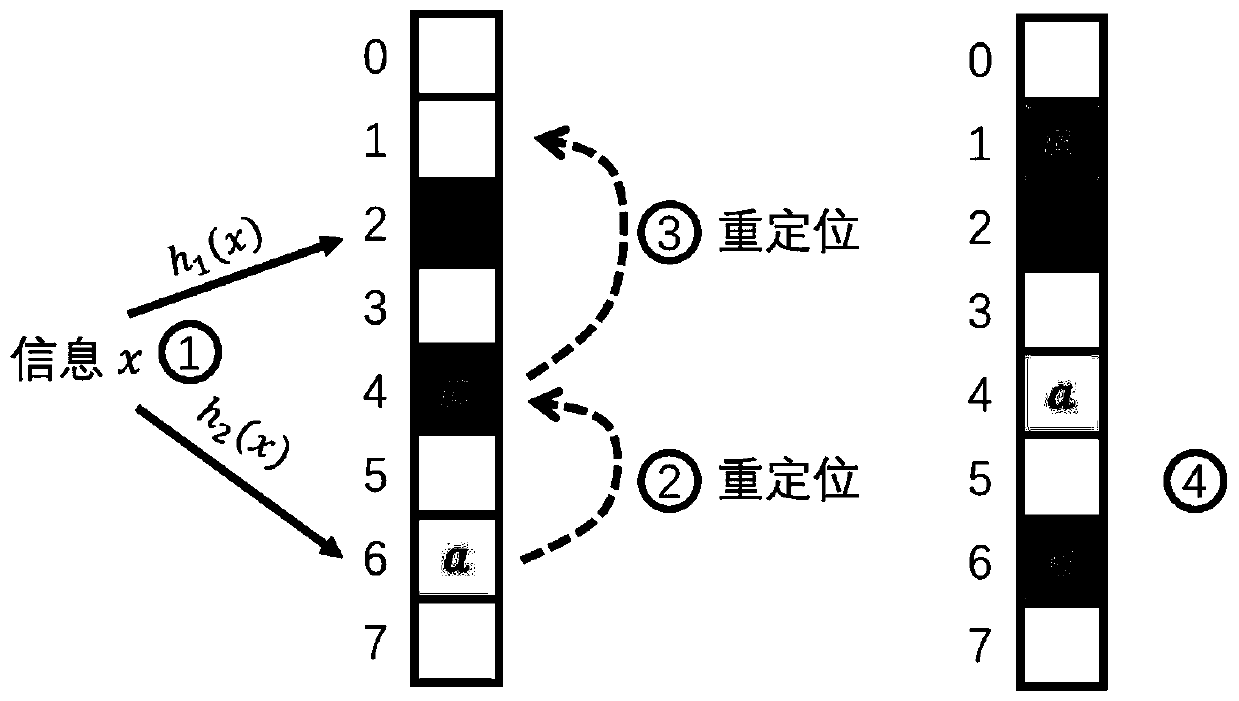
[0018] A kind of power RPL protocol black hole attack defense method based on the cuckoo filter of the present invention, the steps are as follows:
[0019] Step 1: Initialize the DODAG system, establish the information data of the system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com