SAODV optimization method capable of effectively fighting against black hole attacks
A technology of black hole attack and optimization method, which is applied in the field of communication, can solve problems such as inability to effectively resist black hole attacks, achieve the effects of improving reliability and security, improving transmission efficiency, and reducing packet loss rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] A further detailed description of the technical solution of the present invention is given below in conjunction with the accompanying drawings, so that those skilled in the art can understand the solution of the present invention more clearly, but the protection scope of the present invention is not limited thereby.
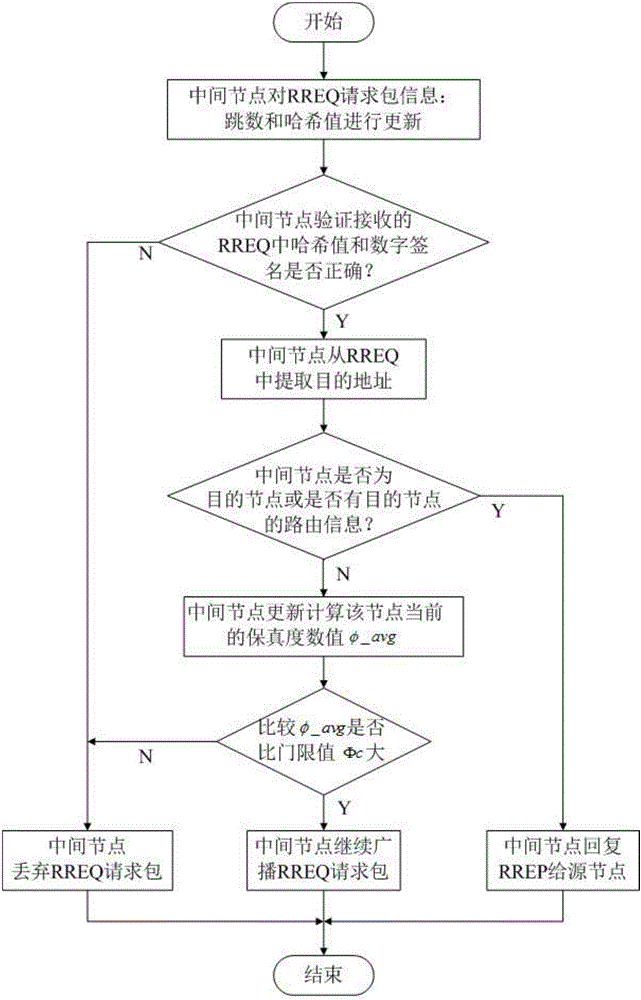
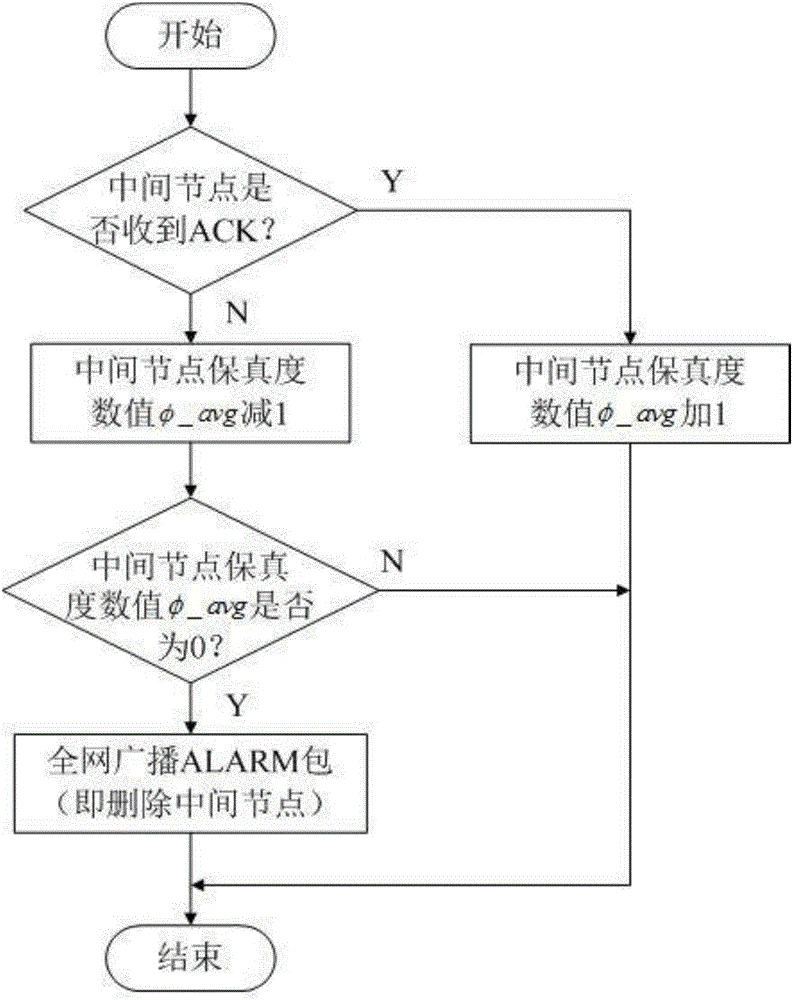
[0044] For ease of understanding, the principle of resisting black hole node attacks of the present invention is briefly given at first: in the Ad-hoc network, when the route selection mode is adopted, the malicious node adds false available channel information to the received route request packet in the route discovery stage, It is a malicious attack that tricks other nodes into establishing a routing connection with it, and then discards the data packets that need to be forwarded, resulting in data packet loss.
[0045] In order to prevent the black hole node from modifying the information contained in the routing request packet, the present invention inn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com