OLSR protocol black hole attack method for unmanned aerial vehicle ad hoc network
A black hole attack and drone technology, applied in wireless communication, electrical components, security devices, etc., can solve the problems of high mobility drone ad hoc network inapplicability, network damage and other problems, and achieve good scalability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
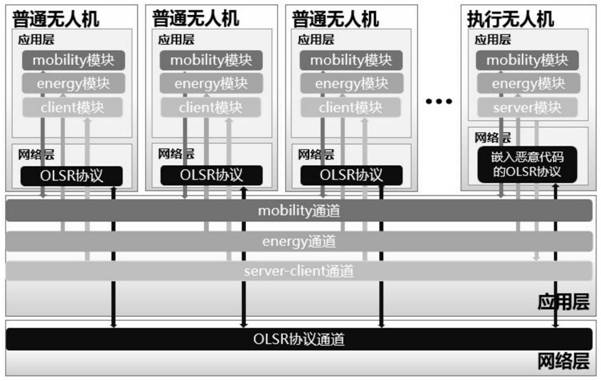
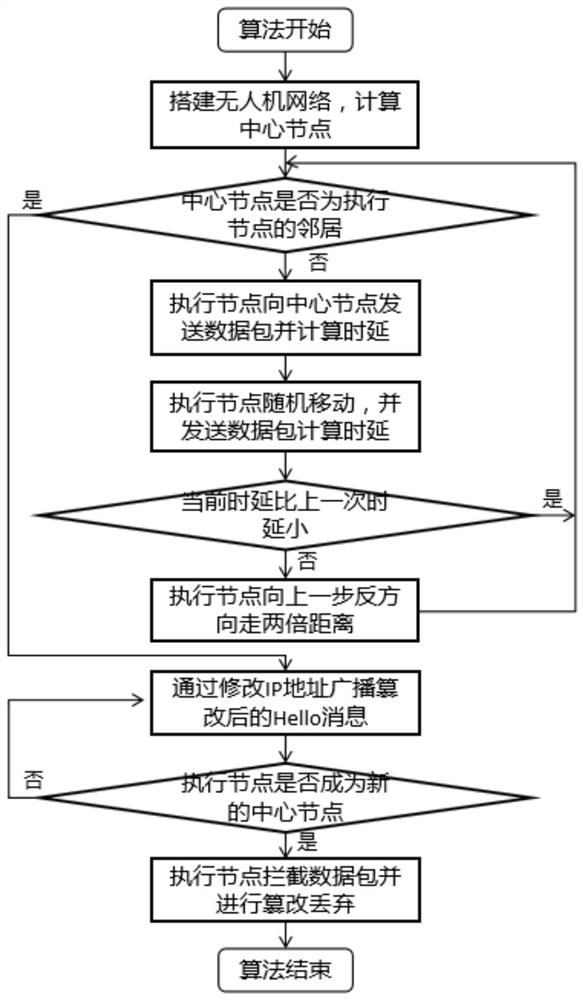
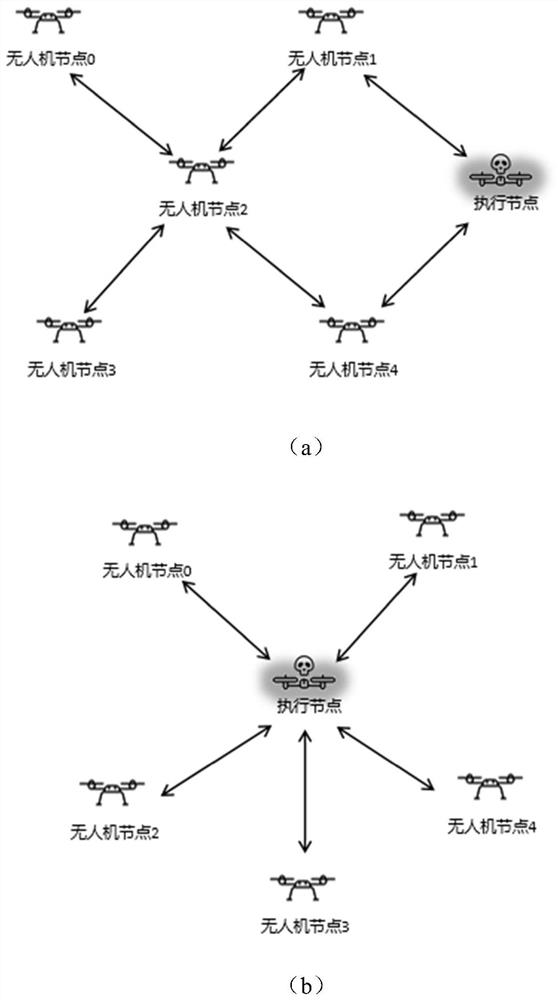
[0045] A black hole attack method of OLSR protocol for UAV Ad Hoc Network, such as figure 1 As shown, it is applied to the UAV ad hoc network system, and the architecture of the UAV ad hoc network system is as follows image 3 As shown, according to the different requirements of collaborative computing and flight control for the communication environment, the UAV network is divided into two parts: the internal communication of the fleet and the external communication of the fleet. The internal communication of the cluster is realized by Adhoc network plus OLSR self-organizing network technology, in which the edge position of the execution node tries to be close to the central node and occupy its position. Include the following steps:
[0046] S1, build the drone ad hoc network, set the execution node to operate the drone ad hoc network, first the execution node needs to calculate and attack the node in the center of the regional network through the routing table information. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com