Software vulnerability analytical method based on scene model
A scenario model and software vulnerability technology, applied in the field of network security, can solve the problems of lack of comprehensive use of multiple analysis methods and lack of in-depth testing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
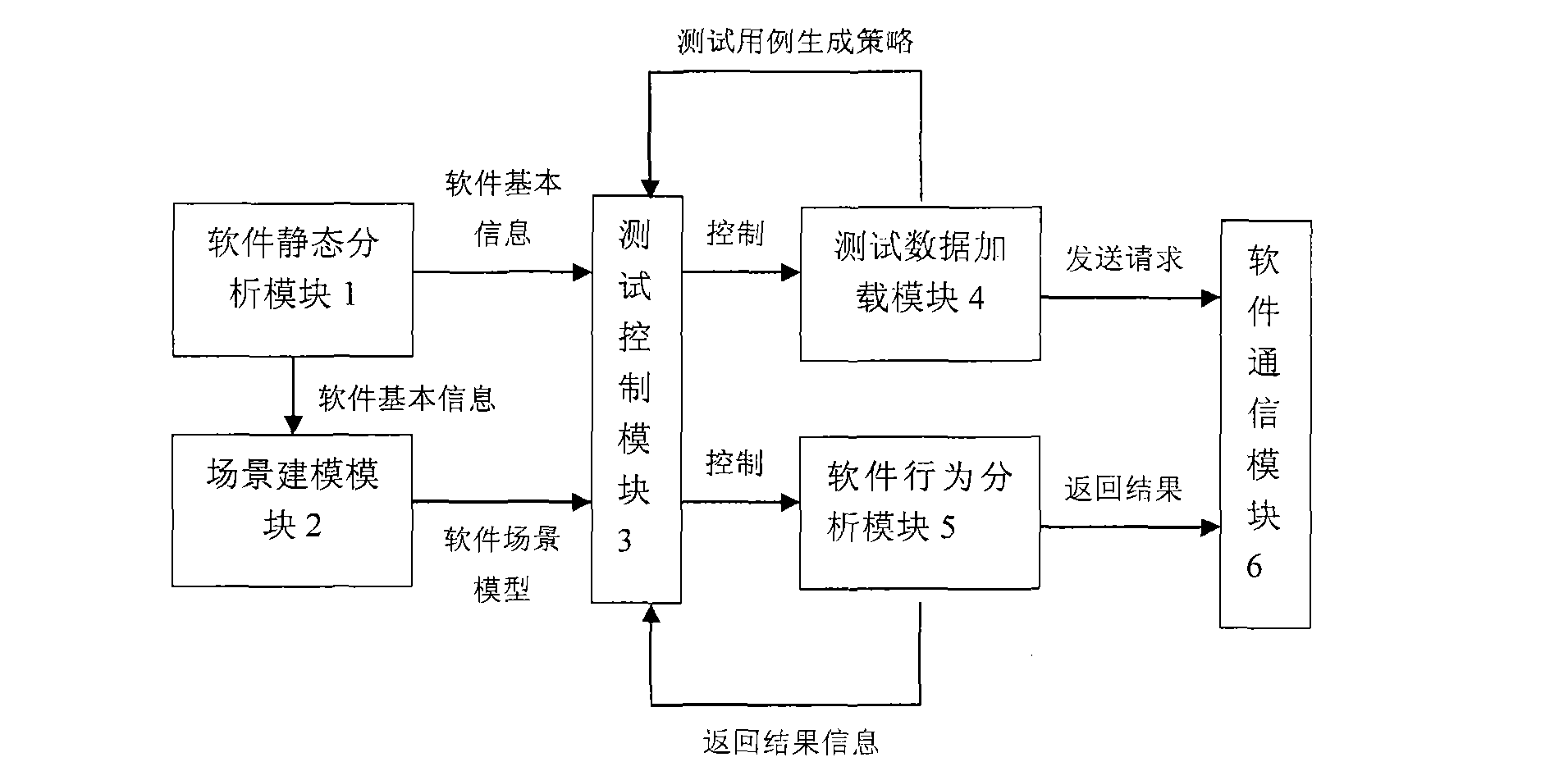
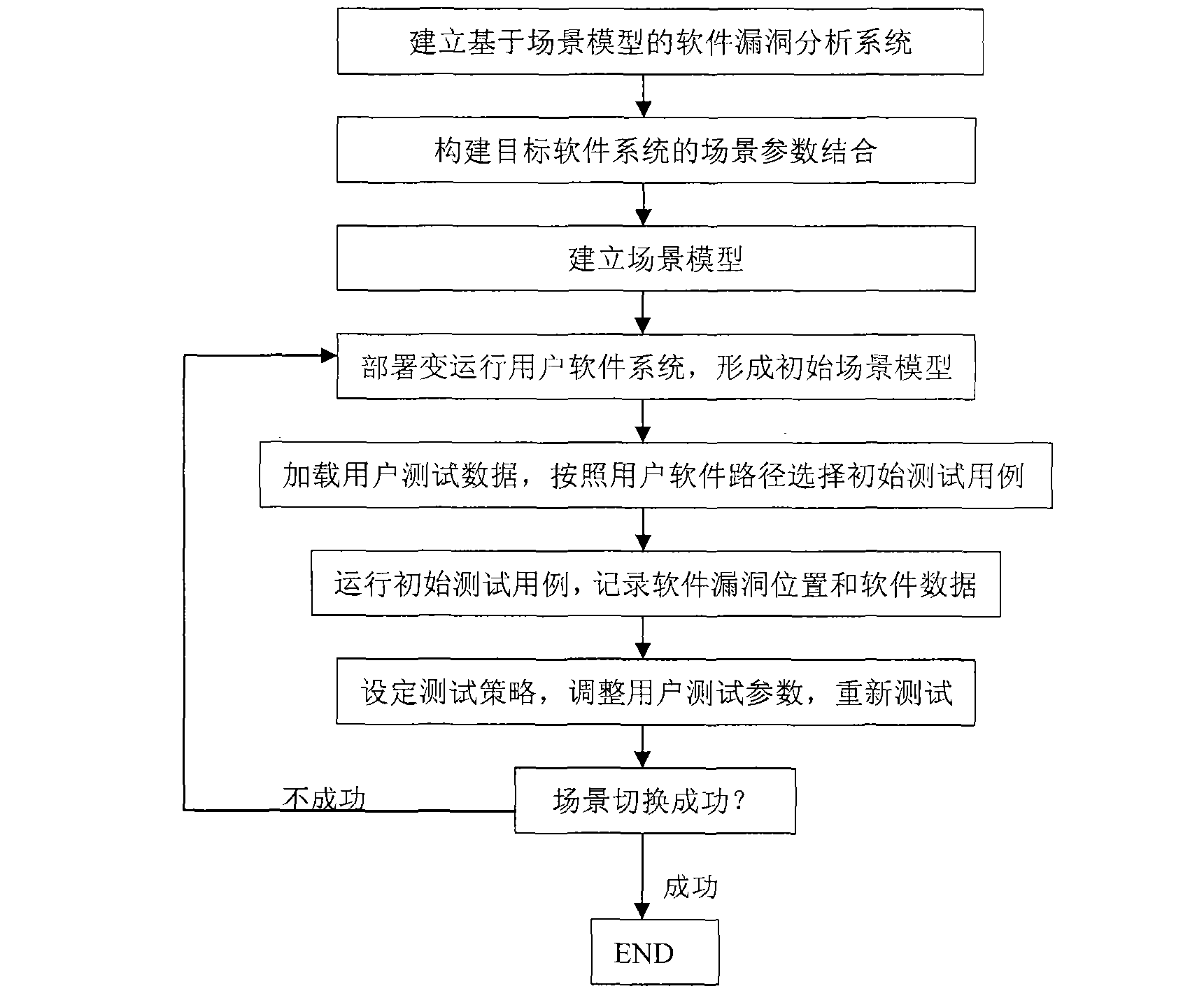
[0061] A scenario-based software vulnerability analysis system includes: a software static analysis module 1, a scenario modeling module 2, a test control module 3, a test data loading module 4, a software operation monitoring module 5, and a software communication module 6.
[0062] (1) Software static analysis module
[0063] The main function of the software static analysis module is to analyze the executable code statements of the software one by one to obtain the execution path of the software, mark the man-machine interface code of the software and the data interface code interacting with other software, and obtain the software development language, operating platform, database, Constituent files, function call parameters, user interface and other information.
[0064] (2) Scene modeling module
[0065] The main function of the scene modeling module is to establish the user state collection of the software according to the composition files and function call parameters ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com