Method for fast uninstalling application programs of mobile terminal devices
A technology of application programs and mobile terminals, applied in the direction of program control devices, program loading/starting, etc., can solve the problems of reducing user experience and wasting mobile phone storage space, and achieve the effect of convenient uninstallation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
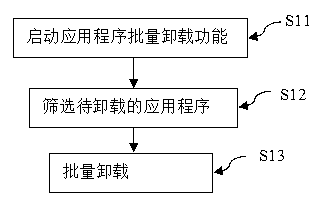
[0014] Such as figure 1 As shown, the operation steps are as follows:
[0015] S11. Receiving an instruction from a user, and starting a batch uninstallation function of application programs;
[0016] S12. Screening applications to be uninstalled to form an uninstallation target list;
[0017] S13. Uninstalling the selected applications in batches: after clicking “Confirm”, calling the operating system command (such as calling the deletePackage() command of the PackageManager in the Android operating system) to uninstall the uninstall target.
[0018] Finally, the desktop exits the bulk uninstall feature mode.
[0019] Wherein, in step S12, the filtering condition is: the time that the application program has not been used for a long time exceeds a set time threshold. The time threshold can be set by the user. The system default setting is 30 days.
Embodiment 2
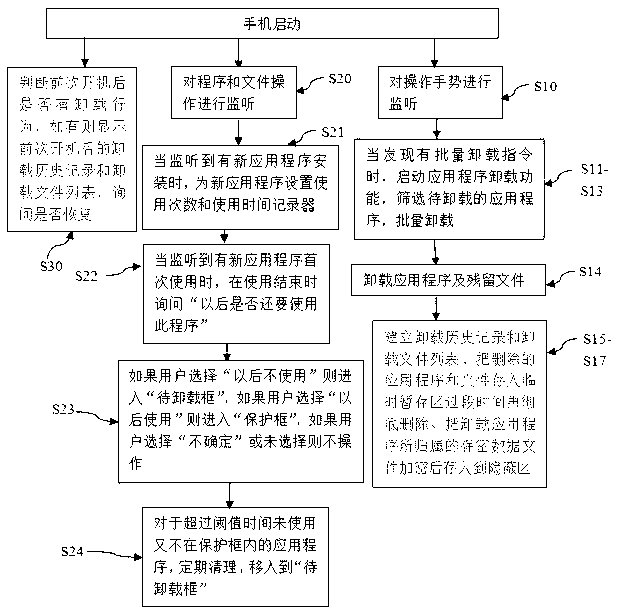
[0021] Compared with Embodiment 1, this embodiment increases the flexibility and convenience of screening. Such as figure 2 As shown, steps S20-S24 are added in this embodiment.
[0022] S20, monitor the program and file operations after the mobile phone is started;
[0023] S21. When it is detected that a new application program is installed, set the usage count and usage time recorder for the new application program;
[0024] S22. When it is detected that a new application program is used for the first time, ask "whether you want to use this program in the future" at the end of the use;
[0025] S23. If the user selects "do not use in the future", enter the "uninstallation box", if the user selects "use in the future", enter the "protection box", if the user selects "not sure" or does not select, do not operate.
[0026] Through the introduction of the above steps, this embodiment can classify and screen the program when it is used for the first time, but does not perfor...
Embodiment 3
[0029] In addition to steps S11-S13 in Embodiment 1 and steps S20-S24 in Embodiment 1, this embodiment also adds further functional steps, such as figure 2 shown. The added steps include: the filtering step in the screening, the aftermath step, the unloading step of residual files, the step of prompting for power-on recovery, the step of storing in the temporary temporary storage area, the step of storing the confidential data files in the hidden area after encryption, etc.
[0030] The filtering step in the filtering (not shown in the figure), is to let the user uncheck or cancel the uninstallation task: in this step, manual filtering is set, that is, the list of targets to be uninstalled is displayed, and a check box is added, and the user can Click the target that you do not want to uninstall, and uncheck the target. For targets unchecked by the user, uncheck them from uninstall targets. Although there is also a ticking operation here, it is different from the prior art,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com